Добавить любой RSS - источник (включая журнал LiveJournal) в свою ленту друзей вы можете на странице синдикации.
Исходная информация - http://planet.mozilla.org/.
Данный дневник сформирован из открытого RSS-источника по адресу http://planet.mozilla.org/rss20.xml, и дополняется в соответствии с дополнением данного источника. Он может не соответствовать содержимому оригинальной страницы. Трансляция создана автоматически по запросу читателей этой RSS ленты.
По всем вопросам о работе данного сервиса обращаться со страницы контактной информации.
[Обновить трансляцию]
The Firefox Frontier: Enter Our College Essay Contest for a Chance to Win $5,000 |
The world this year’s college graduates will inherit is vastly different than the one they grew up expecting. COVID-19, a changing political climate, and a fluctuating economy all have something … Read more
The post Enter Our College Essay Contest for a Chance to Win $5,000 appeared first on The Firefox Frontier.
https://blog.mozilla.org/firefox/college-essay-contest-pocket-hercampus-announcement/
|
|
Mozilla Open Policy & Advocacy Blog: Defending users’ security in Mauritius |
Yesterday, Mozilla and Google filed a joint submission to the public consultation on amending the Information and Communications Technology (ICT) Act organised by the Government of Mauritius. Our submission states that the proposed changes would disproportionately harm the security of Mauritian users on the internet and should be abandoned. Mozilla believes that individuals’ security and privacy on the internet are fundamental and must not be treated as optional. The proposals under these amendments are fundamentally incompatible with this principle and would fail to achieve their projected outcomes.
Under Section 18(m) of the proposed changes, the ICTA could deploy a “new technical toolset” to intercept, decrypt, archive and then inspect/block https traffic between a local user’s Internet device and internet services, including social media platforms.
In their current form, these measures will place the privacy and security of internet users in Mauritius at grave risk. The blunt and disproportionate action will allow the government to decrypt, read and store anything a user types or posts on the internet, including intercepting their account information, passwords and private messages. While doing little to address the legitimate concerns of content moderation in local languages, it will undermine the trust of the fundamental security infrastructure that currently serves as the basis for the security of at least 80% of websites on the web that use HTTPS, including those that carry out e-commerce and other critical financial transactions.
When similarly dangerous mechanisms have been abused in the past, whether by known-malicious parties, business partners such as a computer or device manufacturer, or a government entity, as browser makers we have taken steps to protect and secure our users and products.
In our joint submission to the on-going public consultation, Google and Mozilla have urged the Authority not to pursue this approach. Operating within international frameworks for cross-border law enforcement cooperation and enhancing communication with industry can provide a more promising path to address the stated concerns raised in the consultation paper. We remain committed to working with the Government of Mauritius to address the underlying concerns in a manner that does not harm the privacy, security and freedom of expression of Mauritians on the internet.
The post Defending users’ security in Mauritius appeared first on Open Policy & Advocacy.
https://blog.mozilla.org/netpolicy/2021/05/12/defending-users-security-in-mauritius/
|
|
Mozilla Privacy Blog: Mozilla files joint amicus brief in support of California net neutrality law |
Yesterday, Mozilla joined a coalition of public interest organizations* in submitting an amicus brief to the Ninth Circuit in support of SB 822, California’s net neutrality law. In this case, telecom and cable companies are arguing that California’s law is preempted by federal law. In February of this year, a federal judge dismissed this challenge and held that California can enforce its law. The telecom industry appealed that decision to the 9th Circuit. We are asking the 9th Circuit to find that California has the authority to protect net neutrality.
“Net neutrality preserves the environment that creates room for new businesses and new ideas to emerge and flourish, and where internet users can choose freely the companies, products, and services that they want to interact with and use. In a marketplace where consumers frequently do not have access to more than one internet service provider (ISP), these rules ensure that data is treated equally across the network by gatekeepers. We are committed to restoring the protections people deserve and will continue to fight for net neutrality,” said Amy Keating, Mozilla’s Chief Legal Officer.
*Mozilla is joined on the amicus brief by Access Now, Public Knowledge, New America’s Open Technology Institute and Free Press.
The post Mozilla files joint amicus brief in support of California net neutrality law appeared first on Open Policy & Advocacy.
|
|
The Firefox Frontier: Peace of mind browser add-ons for Firefox |
The web can be as wonderful as it is overwhelming. Fortunately there are ways you can customize Firefox with add-ons to achieve a more harmonious browsing experience. Here are a … Read more
The post Peace of mind browser add-ons for Firefox appeared first on The Firefox Frontier.
https://blog.mozilla.org/firefox/peace-of-mind-browser-add-ons-for-firefox/
|
|
The Rust Programming Language Blog: The Plan for the Rust 2021 Edition |
|
|
Mozilla Security Blog: Beware of Applications Misusing Root Stores |
We have been alerted about applications that use the root store provided by Mozilla for purposes other than what Mozilla’s root store is curated for. We provide a root store to be used for server authentication (TLS) and for digitally signed and encrypted email (S/MIME). Applications that use Mozilla’s root store for a purpose other than that have a critical security vulnerability. With the goal of improving the security ecosystem on the internet, below we clarify the correct and incorrect use of Mozilla’s root store, and provide tools for correct use.
Background on Root Stores: Mozilla provides a root store (curated list of root certificates) to enable Certificate Authorities (CAs) to issue trusted TLS certificates which in turn enables secure browsing and encryption on the internet. The root store provided by Mozilla is intended to be used for server authentication (TLS) and for digitally signed and encrypted email (S/MIME). The root store is built into Firefox and Network Security Services (NSS). The NSS cryptographic library is a set of libraries designed to support cross-platform development of security-enabled client and server applications; it is open source and therefore has become the de-facto standard for many Linux-powered operating systems. While NSS includes Mozilla’s root store by default, it also provides the ability for developers to use their own root store, enabling application developers to provide a list of root certificates that is curated for use cases other than TLS and S/MIME.
Misuse of Root Stores: We have been alerted that some applications are using root stores provided by Mozilla or an operating system (e.g. Linux) for purposes other than what the root store is curated for. An application that uses a root store for a purpose other than what the store was created for has a critical security vulnerability. This is no different than failing to validate a certificate at all.
There are different procedures, controls, and audit criteria for different types of certificates. For example, when a CA issues a certificate for S/MIME, it ensures that the email address in the certificate is controlled by the certificate subscriber. Likewise, when a CA issues a certificate for TLS, it ensures that the domain names in the certificate are controlled by the certificate subscriber. For a CA who has only been evaluated in terms of their issuance of S/MIME certificates there is no indication that they follow the correct procedures for issuance of TLS certificates (i.e. that they properly validate who controls the domain names in the certificate). Similarly, for a CA who has only been evaluated in terms of their issuance of TLS certificates there is no indication that they follow the correct procedures for issuance of Code Signing certificates.
Additionally, some application developers directly parse a file in Mozilla’s source code management system called certdata.txt, in which Mozilla’s root store is maintained in a form that is convenient for NSS to build from. The problem with the scripts that directly parse this file is that some of the certificates in this file are not trusted but rather explicitly distrusted, so scripts that do not take the trust records into account may be trusting root certificates, such as the DigiNotar certificates, which Mozilla explicitly distrusts.
Correctly using Root Stores: Curating a root store is a costly ongoing responsibility, so the Common CA Database (CCADB) Resources tab provides lists of root certificates that are being curated for the purposes of Code Signing, Email (S/MIME), and Server Authentication (SSL/TLS). The Code Signing root certificate list is based on the data that Microsoft maintains in the CCADB for their root store. The Email (S/MIME) and Server Authentication (SSL/TLS) root certificate lists are based on the data that Mozilla maintains in the CCADB for Mozilla’s root store (aka the NSS root store). These lists of certificates may be used for their intended purposes; specifically Code Signing, S/MIME, or TLS. If you choose to use one of these lists, be sure to read the data usage terms and to update the list in your applications frequently.
We recommend that you use the certificate lists provided on the CCADB Resources page rather than directly parsing the certdata.txt file. Application developers who continue to parse the certdata.txt file should use a script that correctly takes the trust records into account.
It is important to note that decisions that a root store operator makes with regards to inclusion or exclusion of CA certificates in its root store are directly tied to the capabilities and behaviors of the software they are distributing. Additionally, a security change could be made wholly or partly in the software instead of the root store. On a best-efforts basis, Mozilla maintains a list of the additional things users of Mozilla’s root store might need to consider.
Application developers must pay attention to which Root Store to use: We strongly encourage application developers to ensure that the list of root certificates that they are using in their applications have been curated for their use case. Additionally, application developers should only use the Mozilla/NSS root store for TLS or S/MIME by using the links provided on the CCADB Resources page that list the certificates in the Mozilla/NSS root store according to the trust bits (key usage) they are curated for.
Choosing to rely on a root store also means understanding and accepting the policies for that root store. Concretely, that means respecting both the trust flags on root certificates and decisions to add or remove root certificates. In particular, Mozilla removes root certificates when they are determined to be no longer trustworthy for TLS or S/MIME. If a removal causes an application to break, then it is either correct on the basis that the root certificate should no longer be used for TLS or S/MIME, or it is a fault in that application not using the root store correctly. Significant root removals are usually announced in Mozilla’s Security Blog (e.g. DigiNotar, CNNIC, WoSign).
Mozilla is committed to maintaining our own root store because doing so is vital to the security of our products and the web in general. It gives us the ability to set policies, determine which CAs meet them, and to take action when a CA fails to do so.
The post Beware of Applications Misusing Root Stores appeared first on Mozilla Security Blog.
https://blog.mozilla.org/security/2021/05/10/beware-of-applications-misusing-root-stores/
|
|
Support.Mozilla.Org: What’s up with SUMO – May 2021 |
Hey SUMO folks,
The second quarter of 2021 is underway and we can’t be more excited about lots of stuff that we’ve been working on in this quarter.
Let’s find out more about them!
Welcome on board!
- Welcome back dbben! Thanks for actively contributing back in the forum.
Community news
- Another reminder to check out Firefox Daily Digest to get daily updates about Firefox. Go check it out and subscribe if you haven’t already.
- Advanced Search page is gone from SUMO as per May 4, 2021. The team is currently working to add syntax functionality that will be added to the simple search field. The plan is to have similar functionality to what we have in the advanced search but with minimal UI. Follow our discussion about this in the contributor forum here.
- Firefox 89 is coming soon. We’ve been working on the tagging plan across channels for the upcoming proton launch next month. The idea is that, we want to collect those feedbacks and report to the product team regularly before and after the release. Here’s what we’re going to do for each channel:
- Forum: If you’ve seen any questions related to proton changes, please tag the question with MR1.
- Twitter: Conversocial let us automatically tag conversations with specific keywords related to proton. If you’ve seen other conversations that haven’t been tagged, please add “MR1” tag manually.
- Reddit: Include proton in your post and tag the thread with “Proton” (related thread). We’ll capture top 10 conversations to the product team on a weekly basis.
- Check out the following release notes from Kitsune for the past month:
Community call
- Watch the monthly community call if you haven’t. Learn more about what’s new in April. We talked about various updates including the upcoming proton release in Firefox 89.
- Reminder: Don’t hesitate to join the call in person if you can. We try our best to provide a safe space for everyone to contribute. You’re more than welcome to lurk in the call if you don’t feel comfortable turning on your video or speaking up. If you feel shy to ask questions during the meeting, feel free to add your questions on the contributor forum in advance, or put them in our Matrix channel, so we can address them during the meeting.
Community stats
KB
KB Page views
| Month | Page views | Vs previous month |
| April 2020 | 8,739,284 | -28.03% |
Top 5 KB contributors in the last 90 days:
KB Localization
Top 10 locale based on total page views
| Locale | Apr 2020 page views | Localization progress (per 6 May) |
| de | 10.09% | 99% |
| es | 6.80% | 45% |
| zh-CN | 6.58% | 100% |
| fr | 6.52% | 88% |
| pt-BR | 6.14% | 68% |
| ja | 4.37% | 57% |
| ru | 3.87% | 99% |
| it | 2.48% | 98% |
| pl | 2.31% | 85% |
| id | 0.96% | 2% |
Top 5 localization contributor in the last 90 days:
Forum Support
Forum stats
| Month | Total questions | Answer rate within 72 hrs | Solved rate within 72 hrs | Forum helpfulness |
| Apr 2020 | 3379 | 71.26% | 14.86 | 71.43% |
Top 5 forum contributor in the last 90 days:
Social Support
| Channel | Apr 2020 | |
| Total conv | Conv handled | |
| @firefox | 4,064 | 287 |
| @FirefoxSupport | 303 | 123 |
Top 5 contributors in April 2021
- Christophe Villeneuve
- Md Monirul Alom
- Devin E
- Andrew Truong
- Alex Mayorga
Play Store Support
We don’t have enough data for the Play Store Support yet. However, you can check out the overall Respond Tool metrics here.
Product updates
Firefox desktop
- FX 89 release – June 1st
- MR1/Proton
- Firefox Beta 8(88.0b8) will have final if not near final changes implemented for proton
- Phase 2 of Total Cookie protection – Dynamic First Party Isolation, or dFPI, feature enabled for Private Browsing Mode Users
- Shimming Category 2 – Automatic exceptions UI indicator
- Personalizing New Tab – Customize your new tab experience
Firefox mobile
- Fenix (Fx 89) – June 1st
- Optimized toolbar menus
- Top Site visual improvements
- Sync tabs -> tabs tray
- iOS V34
- Refresh of tabs view
- Adding synced tabs to tabs trey
- Removed tabs search bar
- Tabs Trey refresh
- Nimbus experimentation platform integrated
Other products / Experiments
- Mozilla VPN V2.3 – may 28
- Windows – split tunneling
- IPv6 Captive portal detection
- Firefox for Amazon Fire TV and Echo Show sunset
Shout-outs!
- Thank you Mamoon for taking up VPN questions on the forum!
- Thank you Yoasif for helping us with Proton flair on Reddit!
- Congrats dbben for making into the top contributor list for the forum.
If you know anyone that we should feature here, please contact Kiki and we’ll make sure to add them in our next edition.
Useful links:
- #SUMO Matrix group
- SUMO Discourse
- Contributor forums
- Twitter @SUMO_mozilla and @FirefoxSupport
- SUMO Blog
https://blog.mozilla.org/sumo/2021/05/10/whats-up-with-sumo-may-2021/
|
|
William Lachance: mozregression update May 2021 |
Just wanted to give some quick updates on the state of mozregression.
Anti-virus false positives
One of the persistent issues with mozregression is that it seems to be persistently detected as a virus by many popular anti-virus scanners. The causes for this are somewhat complex, but at root the problem is that mozregression requires fairly broad permissions to do the things it needs to do (install and run copies of Firefox) and thus its behavior is hard to distinguish from a piece of software doing something malicious.
Recently there have been a number of mitigations which seem to be improving this situation:
- :bryce has been submitting copies of mozregression to Microsoft so that Windows Defender (probably the most popular anti-virus software on this platform) doesn’t flag it.
- I recently released mozregression 4.0.17, which upgrades the GUI dependency for pyinstaller to a later version which sets PE checksums correctly on the generated executable (pyinstaller/pyinstaller#5579).
It’s tempting to lament the fact that this is happening, but in a way I can understand it’s hard to reliably detect what kind of software is legitimate and what isn’t. I take the responsibility for distributing this kind of software seriously, and have pretty strict limits on who has access to the mozregression GitHub repository and what pull requests I’ll merge.
CI ported to GitHub Actions
Due to changes in Travis’s policies, we needed to migrate continuous integration for mozregression to GitHub actions. You can see the gory details in bug 1686039. One possibly interesting wrinkle to others: due to Mozilla’s security policy, we can’t use (most) external actions inside our GitHub repository. I thus rewrote the logic for uploading a mozregression release to GitHub for MacOS and Linux GUI builds (Windows builds are still happening via AppVeyor for now) from scratch. Feel free to check the above out if you have a similar need.
MacOS Big Sur
As of version 4.0.17, the mozregression GUI now works on MacOS Big Sur. It is safe to ask community members to install and use it on this platform (though note the caveats due to the bundle being unsigned).
Usage Dashboard
Fulfilling a promise I implied last year, I created a public dataset for mozregression and created an dashboard tracking mozregression use using Observable. There are a few interesting insights and trends there that can be gleaned from our telemetry. I’d be curious if the community can find any more!
https://wrla.ch/blog/2021/05/mozregression-update-may-2021/?utm_source=Mozilla&utm_medium=RSS
|
|
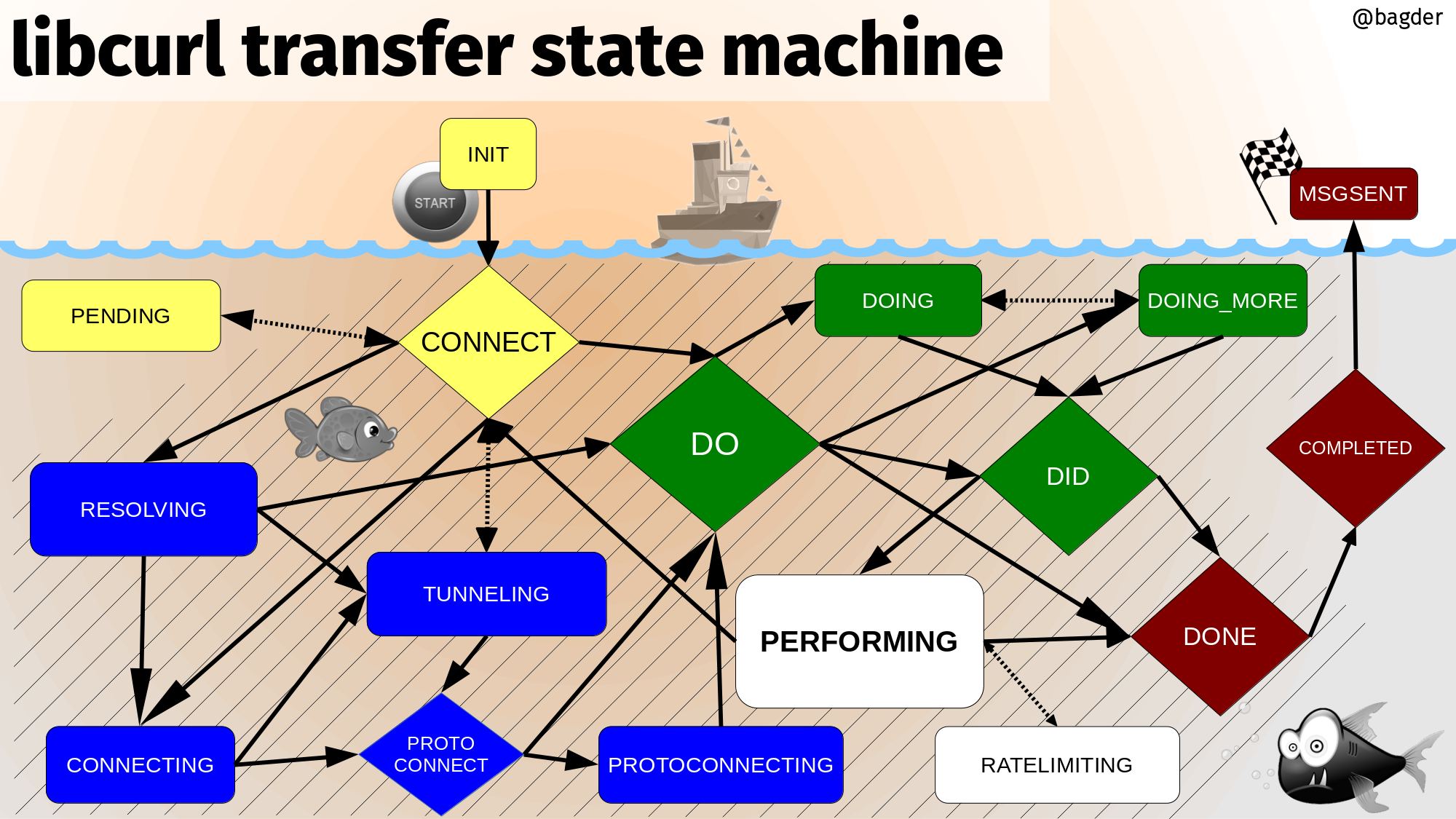
Daniel Stenberg: The libcurl transfer state machine |
I’ve worked hard on making the presentation I ended up calling libcurl under the hood. A part of that presentation is spent on explaining the main libcurl transfer state machine and here I’ll try to document some of what, in a written form. Understanding the main transfer state machine in libcurl could be valuable and interesting for anyone who wants to work on libcurl internals and maybe improve it.
Background
The state is kept in easy handle in the struct field called mstate. The source file for this state machine is called multi.c.
An easy handle is always in exactly one of these states for as long as it exists.
This transfer state machine is designed to work for all protocols libcurl supports, but basically no protocol will transition through all states. As you can see in the drawing, there are many different possible transitions from a lot of the states.
libcurl transfer state machine
(click the image for a larger version)
Start
A transfer starts up there above the surface in the INIT state. That’s a yellow box next to the little start button. Basically the boat shows how it goes from INIT to the right over to MSGSENT with it’s finish flag, but the real path is all done under the surface.
The yellow boxes (states) are the ones that exist before or when a connection is setup. The striped background is for all states that has a single and specific connectdata struct associated with the transfer.
CONNECT
If there’s a connection limit, either in total or per host etc, the transfer can get sent to the PENDING state to wait for conditions to change. If not, the state probably moves on to one of the blue ones to resolve host name and connect to the server etc. If a connection could be reused, it can shortcut immediately over to the green DO state.
The green states are all about setting up the connection to a state of fully connected, authenticated and logged in. Ready to send the first request.
DO
The green DO states are all about sending the request with one or more commands so that the file transfer can begin. There are several such states to properly support all protocols but also for historical reasons. We could probably remove a state there by some clever reorgs if we wanted.
PERFORMING
When a request has been issued and the transfer starts, it transitions over to PERFORMING. In the white states data is flowing. Potentially a lot. Potentially in both or either direction. If during the transfer curl finds out that the transfer is faster than allowed, it will move into RATELIMITING until it has cooled down a bit.
DONE
All the post-transfer states are red in the picture. The DONE is the first of them and after having done what it needs to round up the transfer, it disassociates with the connection and moves to COMPLETED. There’s no stripes behind that state. Disassociate here means that the connection is returned back to the connection pool for later reuse, or in the worst case if deemed that it can’t be reused or if the application has instructed it so, closed.
As you’ll note, there’s no disconnect anywhere in the state machine. This is simply because the disconnect is not really a part of the transfer at all.
COMPLETED
This is the end of the road. In this state a message will be created and put in the outgoing queue for the application to read, and then as a final last step it moves over to MSGSENT where nothing more happens.
A typical handle remains in this state until the transfer is reused and restarted, in which it will be set back to the INIT state again and the journey begins again. Possibly with other transfer parameters and URL this time. Or perhaps not.
State machines within each state
What this state diagram and explanation doesn’t show is of course that in each of these states, there can be protocol specific handling and each of those functions might in themselves of course have their own state machines to control what to do and how to handle the protocol details.
Each protocol in libcurl has its own “protocol handler” and most of the protocol specific stuff in libcurl is then done by calls from the generic parts to the protocol specific parts with calls like protocol_handler->proto_connect() that calls the protocol specific connection procedure.
This allows the generic state machine described in this blog post to not really know the protocol specifics and yet all the currently support 26 transfer protocols can be supported.
libcurl under the hood – the video
Here’s the full video of libcurl under the hood.
If you want to skip directly to the state machine diagram and the following explanation, go here.
Credits
Image by doria150 from Pixabay
https://daniel.haxx.se/blog/2021/05/10/the-libcurl-transfer-state-machine/
|
|
Karl Dubost: Browser Wish List - Tabs and bookmarks are the same thing |
My browser is my like an office room with desk and shelves, where the information is accessible. Information is stacked, accessible, sometimes open and browsable at glance and some deep on the shelves. But how would I want to have access it in the browser.
Currently we bury the information of tabs and bookmarks in a big bind of context without giving any help for managing apart of having to go through the list of pages one by one. No wonder why people feel overwhelmed and try to limit the number of tabs they have opened. Because big numbers rely on external tools (Tree Style Tabs, Sidebery, Containers, etc) which do not go far enough to manage the tabs.

Some contexts
It started with a message from Glandium sharing an article from Joseph Chee Chang with the title: When the Tab Comes Due. Tabs! Love Tabs. Reading the PDF brought some strong nodding.
Tabs should better reflect users’ complex task structures.
One potential design space is to bootstrap such mental model repre-sentations with minimal user effort by identifying their intentionsusing their navigation patterns. For example, a set of tabs openedfrom a search engine query is likely to support the same information needs; or, a set of tabs opened from a top-10 list article arelikely competing options under the same category. Capturing andorganizing tabs using such structures has the potential of betterorienting users and providing better support for task progressionand resumption.
Allow users to externalize their thoughts and synthesize information across tabs.
More directly, a recent survey showed thataround half of their participants (49.4%, N=89) use spreadsheets togather evidence and take notes across multiple online informationsources to compare options (e.g., products or destinations) to helpthem make decisions. However, current browsers treat tabs asindividual silos and provide little support for cross-referencing andcollecting information between webpages. Using external tools,such as word documents and spreadsheets, creates a disconnectin users’ workspace, and can incur high cognitive and interactioncosts when trying to copy and paste information to synthesize themin a separate document
Sketch
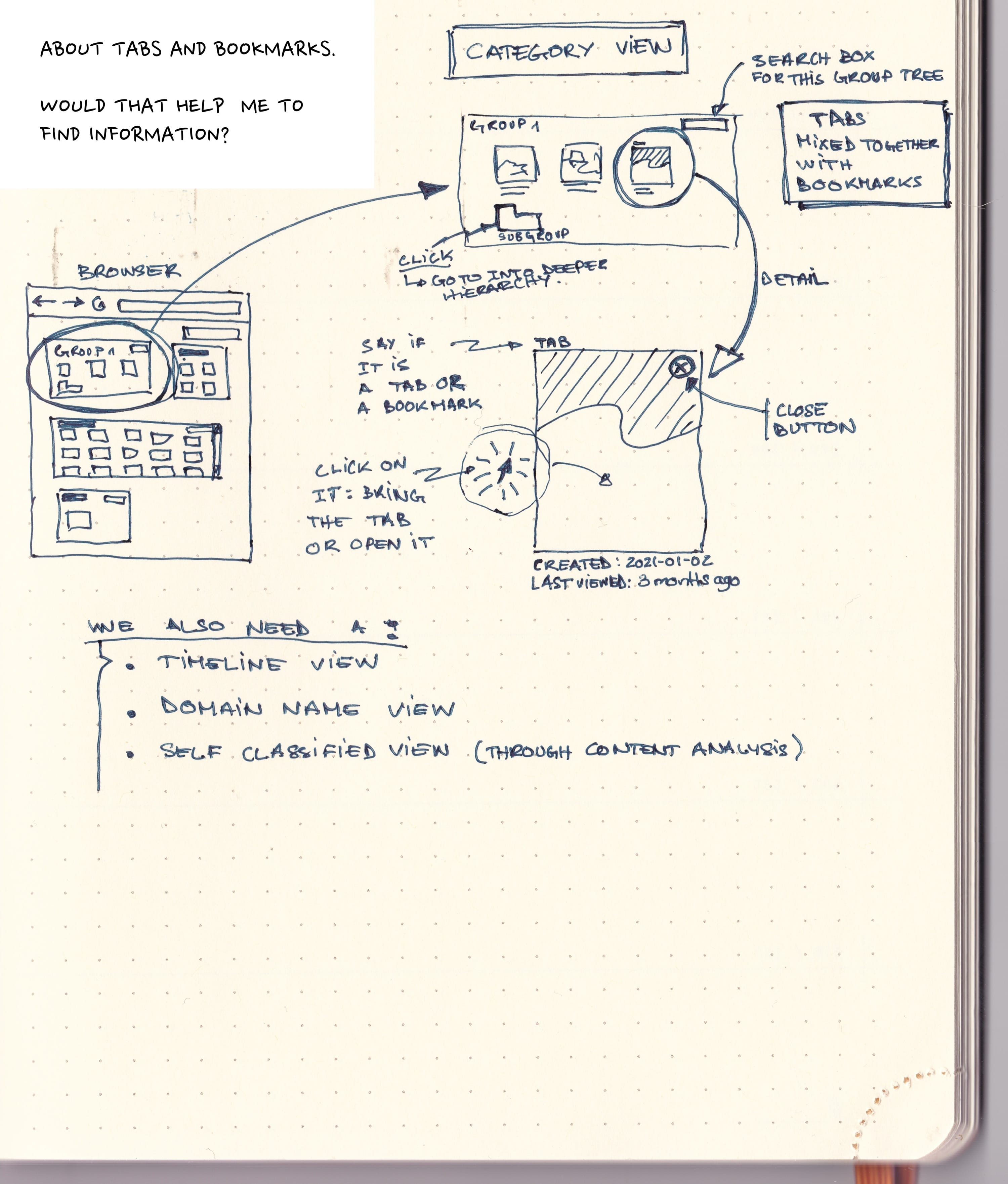
The article made me think about tabs and bookmarks, in our browsers UIs, these are separated. Probably it should not be. A bookmark is just a closed context, and a tab is just an opened context. But they are basically the same. The UI to access them is completely different, the information to filter them is also totally different. Why?
So I was thinking how could both world be mixed together.
- Make the bookmarks more visual though thumbnails.
- Make the tabs manageable through trees and categories and gives them the concept of dates (created and last opened) and show these dates.
- Add on top of this full text search on the full set (or subcategory) of tabs/bookmarks (we need a new name).
- Search "Gardening" for tabs opened in between February 2021 and May 2021.
- Search "Curry" for tabs in my Thailand category
- Give the notion of views
- By tree (the sketch below)
- By timeline (Year, month, days). Think photo management software. Sure I opened this tab after this date, during this trip, etc.
- By geolocation (tabs opened when I was at home or in this cafe) Sometimes we memorize the information through the external context we where in.
- By labels or keywords that you may have added.
- By automatic classification of content. Machine Learning is all the rage, why not using the capabilities that OS provides more and more for running Machine learning to classify the content or even embark one.
Comments
If you have more questions, things I may have missed, different take on them. Feel free to comment…. Be mindful.
Otsukare!
|
|
Daniel Stenberg: curl up 2021 |
curl up 2021 happened today.
We had five presentations done, all prerecorded and made available before the event. At the Sunday afternoon we gathered to discuss the presentations and everything around those topics.
The presentations
- The state of curl 2021 – Daniel Stenberg
- curl security 2021 – Daniel Stenberg
- libcurl under the hood – Daniel Stenberg
- Interfacing rust – Stefan Eissing
- Curl profiling – Jim Fuller.
Discussions
We were not very many who actually joined the meeting, and out of the people in the meeting a majority decided to be spectators only and remained muted with their cameras off.
It turned out as a two hour long mostly casual talk among me, Stefan Eissing and Emil Engler about the presentations and related topics. Toward the end, Kamil Dudka appeared.
The three of us get to talk about roadmap items, tests, security, writing code that interfaces modules written in rust and what more details in the libcurl internals that could use further descriptions and documentation.
The video
The agenda in the video is roughly following the agenda order in the 2021 wiki page and the discussion topics mentioned there.
Sponsored
Thanks to wolfSSL for sponsoring the video meeting account used!
|
|
Patrick Cloke: A new maintainer for django-allauth-2fa |
I’m excited to announce the django-allauth-2fa project has a new maintainer! It can now be found under the valohai organization on GitHub, who have already contributed quite a bit to the package.
This project lets you easily add two-factor authentication to a Django project using django-allauth.
As a bit …
https://patrick.cloke.us/posts/2021/05/07/django-allauth-2fa-transfer/
|
|
Daniel Stenberg: curl pictures |
“Memes” or other fun images involving curl. Please send or direct me to other ones you think belong in this collection! Kept here solely to boost my ego.
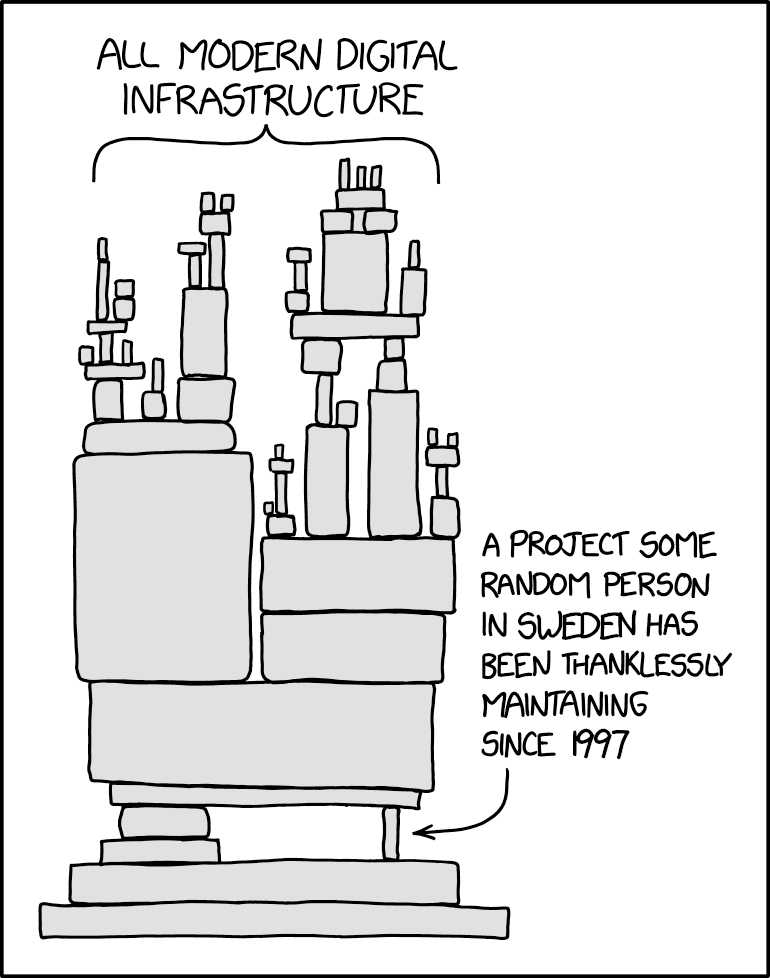
All modern digital infrastructure
This is the famous xkcd strip number 2347, modified to say Sweden and 1997 by @tsjost. I’ve seen this picture taking some “extra rounds” in various places, somehow also being claimed to be xkcd 2347 when people haven’t paid attention to the “patch” in the text.
Entire web infrastructure
Image by @matthiasendler
Car contract

This photo of a rental car contract with an error message on the printed paper was given to me by a good person I’ve unfortunately lost track of.
The developer dice
Thanks to Cassidy. (For purchase here.)
Don’t use -X
Remember that using curl -X is very often just the wrong thing to do. Jonas Forsberg helps us remember:
The curl
In an email from NASA that I received and shared, the person asked about details for “the curl”.
Image by eichkat3r at mastodon.
You’re sure this is safe?
Piping curl output straight into a shell is a much debated practice…
Picture by Tim Chase.
curl, reinvented by…
Remember the powershell curl alias?
Picture by Shashimal Senarath.
Billboard
This is an old classic:
Related
|
|
The Firefox Frontier: Detroit’s digital divide reminds us how far America has to go for internet equity |
by Biba Adams The need for equitable broadband internet access has been a problem since the term “digital divide” was first coined in the mid-1990s, but these conversations are getting … Read more
The post Detroit’s digital divide reminds us how far America has to go for internet equity appeared first on The Firefox Frontier.
https://blog.mozilla.org/firefox/digital-divide-detroit-broadband-internet-access-2021/
|
|
The Rust Programming Language Blog: Announcing Rust 1.52.0 |
The Rust team is happy to announce a new version of Rust, 1.52.0. Rust is a programming language that is empowering everyone to build reliable and efficient software.
If you have a previous version of Rust installed via rustup, getting Rust 1.52.0 is as easy as:
rustup update stable
If you don't have it already, you can get rustup
from the appropriate page on our website, and check out the
detailed release notes for 1.52.0 on GitHub.
What's in 1.52.0 stable
The most significant change in this release is not to the language or standard libraries, but rather an enhancement to tooling support for Clippy.
Previously, running cargo check followed by cargo clippy wouldn't actually
run Clippy: the build caching in Cargo didn't differentiate between the two. In
1.52, however, this has been fixed, which means that users will get the expected
behavior independent of the order in which they run the two commands.
Stabilized APIs
The following methods were stabilized.
Arguments::as_strchar::MAXchar::REPLACEMENT_CHARACTERchar::UNICODE_VERSIONchar::decode_utf16char::from_digitchar::from_u32_uncheckedchar::from_u32slice::partition_pointstr::rsplit_oncestr::split_once
The following previously stable APIs are now const.
char::len_utf8char::len_utf16char::to_ascii_uppercasechar::to_ascii_lowercasechar::eq_ignore_ascii_caseu8::to_ascii_uppercaseu8::to_ascii_lowercaseu8::eq_ignore_ascii_case
Other changes
There are other changes in the Rust 1.52.0 release: check out what changed in Rust, Cargo, and Clippy.
Contributors to 1.52.0
Many people came together to create Rust 1.52.0. We couldn't have done it without all of you. Thanks!
|
|
The Firefox Frontier: Mozilla Explains: What are deceptive design patterns? |
Deceptive design patterns are tricks used by websites and apps to get you to do things you might not otherwise do, like buy things, sign up for services or switch … Read more
The post Mozilla Explains: What are deceptive design patterns? appeared first on The Firefox Frontier.
|
|
Data@Mozilla: Announcing Mozilla Rally |
We wrote recently about how difficult it is to understand the data companies collect from you, and what they’re doing with it. These companies determine how your data is used and who benefits. Cutting people out of decisions about their data is an inequity that harms not only individuals, but also society and the internet. We believe that you should determine who benefits from your data. Today, we’re taking a step in that direction with the alpha release of Mozilla Rally. Rally is now available for desktop Firefox users age 19 and older in the USA.
Rally is aimed at rebuilding your equity in your data. We allow you to choose how to contribute your data and for what purpose. We’re building a community to help understand some of the biggest problems of the internet, and we want you to join us.
How Rally Works
When you join Rally, you have the opportunity to participate in data crowdsourcing projects — we call them “studies” — focused on understanding and finding solutions for social problems caused by the data economy. You will always see a simple explanation of a study’s purpose, the data it collects, how the data will be used, and who will have access to your data. All your data is stored in Mozilla’s restricted servers, and access to the analysis environment is tightly controlled. For those who really want to dig deep, you can read our detailed disclosures and even inspect our code.
Our First Study
Major tech and ad companies track you and others like you online. They can even predict what you’re likely to do next. This information isn’t available to you. Our first study seeks to remedy this imbalance by exploring the time we spend online. We will publish our findings to give you a first look at the data you help create as part of our Rally community.
This first study also creates a foundation for communities to share data in equitable ways. Rally aims to improve our collective understanding of the value of personal data, so we will share public reports and updates with our community at key milestones.
Change starts with exploration
We started Rally as an innovation program, building on earlier experiments with trusted research institutions. In the coming months, we are exploring new products and public interest projects that return equity to communities. We are data optimists and want to change the way the data economy works for both people and day-to-day business. We are committed to putting our users first every step of the way, and building a community together.
Join us at rally.mozilla.org. You can also follow us on Twitter.
https://blog.mozilla.org/data/2021/05/05/announcing-mozilla-rally/
|
|
Daniel Stenberg: Every base is base 10 |
This image originally comes from cowbirdsinlove.com but sadly it seems the page that once showed it is no longer there. I saved it from that site already back in 2015, but I cannot recall the exact URL it used. The image is still available at https://cowbirdsinlove.com/comics/base10[1].png.
Since I consider this picture such an iconic classic and masterpiece, I decided I better host it here in a small attempt to preserve it for everyone to enjoy.
Because, you know, every base is base 10.
Update: the original page on archive.org.
https://daniel.haxx.se/blog/2021/05/04/every-base-is-base-10/
|
|