A must-have for e-commerce! Facebook multi-account 24-hour efficient traffic diversion! |
As e-commerce competition becomes increasingly fierce, how to quickly seize traffic on overseas social media platforms has become the key to the success or failure of sellers. As a super platform with more than 3 billion users worldwide, Facebook is undoubtedly the core battlefield for merchants to attract traffic. However, many sellers miss the golden period of customer conversion due to problems such as manually operating multiple accounts, frequently switching devices, and delayed replies caused by time differences. How to achieve efficient multi-account management + 24-hour automated operation? Today, I recommend an industry dark horse tool - Bitrowser to help you easily solve the pain points!
Ⅰ. "Traffic Anxiety" of E-commerce Sellers: Why do you need to operate multiple accounts simultaneously?
Avoid risks and disperse traffic entrances
Facebook is extremely sensitive to frequent account operations or multiple accounts logged in by the same IP. It will limit traffic at the least and block accounts at the most. Through multi-account matrix operation, it can not only disperse risks, but also cover user groups in different regions and interests, and enhance brand exposure.
Seize the time difference bonus and reach global customers
Markets such as Europe, the United States, and Southeast Asia have different active hours, and the efficiency of manual posting and replying is extremely low. Multiple accounts publish content regularly + automatic reply to ensure accurate reach to target users around the clock.
Ⅱ. BitBrowser: A "technical artifact" that breaks the operational bottleneck
As a browser tool designed for e-commerce, BitBrowser has become a well-known choice in the industry with the following core functions:
1. Multiple accounts in an independent environment, zero risk of association
By customizing browser fingerprint technology (such as resolution, time zone, language, User-Agent, etc.), an independent virtual operating environment is created for each Facebook account. Even if 100 accounts are logged in at the same time, the system will automatically isolate the data, completely solving the problem of account blocking due to repeated IP or device.
2. One-click synchronous posting, 10 times more efficient
Supports pre-editing of text/video content, batch setting of publishing time, and automatic publishing of all accounts as planned. For example, for the browsing peak of American users at 8 a.m., all accounts can be set in advance to push promotional activities at this time to accurately detonate traffic.
3. Intelligent reply to messages, retain customers 24 hours a day
Built-in automated script function, you can preset the reply words for common questions (such as logistics inquiry, product specifications, etc.). When customers send private messages or comments, the system responds in seconds to avoid customer loss due to time difference. At the same time, it supports keyword-triggered personalized replies to improve user experience.
4. Team collaboration + permission management, more standardized operation
Support multiple people to operate different accounts at the same time, and administrators can set sub-account permissions to avoid accidental deletion, accidental sending and other operational risks. All operation logs are backed up in real time for easy review and optimization.
Ⅲ, practical skills: How to use BitBrowser to create a closed loop of explosive orders?
Strategy 1: Multi-account AB testing
Account A mainly promotes low-priced drainage models, and Account B focuses on high-end products. Through differentiated content, test user preferences and quickly adjust product selection direction.
Strategy 2: Accurate interception of comments
Use the automatic reply function to actively answer questions under popular posts and guide users to the independent website or WhatsApp private domain pool.
Strategy 3: Holiday Marketing Automation
Upload promotional materials such as Black Friday and Christmas in batches 3 days in advance, set the release rhythm in different time periods, and maximize exposure and conversion.
Ⅳ.why choose BitBrowser?

Compared with traditional VPS or plug-in tools, Bitrowser does not require complex configuration and can create a virtual environment in 30 seconds; the price is only 60% of similar products, and 10 permanent free windows are provided; data encryption technology has passed ISO security certification to protect account privacy. Currently, more than 50,000 sellers have achieved traffic growth through this tool, saving more than 4 hours of operation time per day!
Act now: The battle for traffic is a race against time! Click the official website to register BitBrowser, unlock Facebook's new automatic drainage posture, and let the store orders soar in 7 days!
|
|
How to solve the TikTok "Hot videos list is empty" problem? Try Bit Cloud Phone |
As a popular short video platform in the world, TikTok users often encounter the problem of "Hot videos list is empty", which not only affects the content browsing experience, but also may hinder the account traffic of cross-border operations. This article will analyze the common causes of this problem and provide efficient solutions. At the same time, combined with the functions of Bit Cloud Phone, it will explore how it can become the preferred tool for cross-border practitioners.
Ⅰ. Common reasons for TikTok's "Hot List is Empty"
Network environment restrictions: TikTok has strict restrictions on regional access. If the device IP is identified as an uncommon area, it may trigger platform risk control, resulting in content failure to load.
Account abnormality or association risk: The same device frequently switches accounts or logs in to multiple accounts, which is easy to be judged as "non-real users", thereby limiting functions.
Application cache or version problems: Local cache accumulation or failure to update the application version in time may cause page loading abnormalities.
Device fingerprint is marked: Virtualized environments (such as traditional cloud phones) are easily detected as "non-real devices" by TikTok, resulting in traffic reduction or even account closure.
Ⅱ. Targeted solutions of Bit Cloud Phone
To address the above problems, Bit Cloud Phone, with its core technology advantages, provides a complete set of response strategies:
1. Simulate the real device environment to bypass geographical restrictions
Bit Cloud Phone automatically matches the language, time zone, operator and other parameters corresponding to the IP through real mobile phone chip simulation. For example, when using a US IP, the system will simultaneously generate an English interface, Los Angeles time zone and AT&T operator information to avoid being intercepted by the platform due to "virtualization characteristics". Users only need to configure the Socks5 proxy IP with one click to stably access TikTok's global content and solve the blank list caused by IP problems.
2. Independent management of multiple accounts to avoid associated risks
Traditional mobile phones are prone to triggering risk control when logging in to multiple accounts on the same device, while Bit Cloud Phone supports independent operation of multiple environments. Each environment has independent device fingerprints, IP and storage space, which is equivalent to "one real machine with ten devices". For example, users can operate TikTok accounts in the United States and Southeast Asia at the same time without frequently switching VPNs to avoid account abnormalities due to IP jumping.
3. One-click cache cleanup and quick application update
Bit Cloud Phone provides cloud storage management function. Users can directly clean TikTok cache or uninstall old versions of apps in the cloud, and download the latest version of TikTok through the built-in Google Play Store to ensure application compatibility. In addition, all operations do not occupy local mobile phone memory to avoid loading failures due to insufficient storage.
4. Real device parameters + dynamic risk control confrontation
Unlike ordinary virtual machines, Bit Cloud Phone ensures the authenticity of device fingerprints by simulating 600+ operator information and sensor data (such as gyroscopes and GPS tracks). For example, the system automatically generates corresponding SIM card information based on the proxy IP, and simulates real-person operation intervals (such as sliding speed ±300ms) through the AI behavior engine, effectively avoiding TikTok's "quantum matrix detection" algorithm.
Ⅲ. Why recommend Bit Cloud Phone?
Cost-effective: The hourly billing mode (0.16 yuan/24 hours) supports unlimited creation of environments, saving 90% of hardware costs compared to purchasing multiple real machines.
Easy to operate: supports batch import of environments, synchronizer group control and ADB script customization, such as automatically refreshing TikTok hot pages through scripts to improve operation and maintenance efficiency.
Safety and compliance: provides sub-account permission management function, enterprises can dynamically allocate employee operation permissions to avoid account resource abuse.
IV. Practical operation guide
Create an overseas environment: select "Computing Power B (Overseas Network)" in Bit Cloud Phone, configure Socks5 proxy and detect IP availability.
Install TikTok: Download the latest version through the built-in application market to avoid compatibility issues.
Optimize account behavior: enable the "AI behavior simulation" function, set a random sliding interval, and simulate real user activity.
Regularly change the environment: use the "one-click new machine" function to reset device parameters and keep the account safe.
Summary:
Behind the "blank hot list" problem of TikTok, there is often a game between the device environment and the platform's risk control. Bit Cloud Phone has become a "breakthrough weapon" for cross-border operators with its real device simulation, multi-account isolation and dynamic risk control confrontation capabilities. Whether you are an individual creator or a corporate team, you can achieve efficient and secure global content operations through its flexible function configuration.
Experience Bit Cloud Phone now, click [Official Website Link] to download, new users can also receive 5 yuan experience money, start your TikTok global traffic journey!
|
|
Choose BitBrowser for fingerprint browsers, and look for the only official website: bitbrowser.cn |

In the digital age, the rise of cross-border e-commerce and social media operations has made multi-account management a rigid demand, but the platform's strict anti-association mechanism also poses challenges to account security. BitBrowser has become a trusted solution for millions of users around the world with its excellent fingerprint protection technology and efficient management functions. This article will deeply analyze the core advantages of this tool and recommend its official website (http://www.bitbrowser.cn) as the only genuine download channel.
1. Core technology: eliminate account association from the root
BitBrowser is deeply developed based on Chrome and Firefox dual-cores. It creates a completely independent browser environment for each account by dynamically simulating device fingerprint information (such as operating system, screen resolution, font, time zone, etc.). This "one account, one fingerprint" mode ensures that even if multiple accounts are logged in on the same device, the risk of being detected by the platform can be avoided. In addition, its unique window synchronization technology supports real-time operation synchronization of multiple windows, greatly improving batch management efficiency. This function has been widely imitated but not surpassed in the industry.
2. Core functions: meet the needs of all business scenarios
Efficient management of multiple accounts
Supports running 2000+ independent accounts on a single computer at the same time. The IP, cookies, and cache data of each account are completely isolated, which is especially suitable for matrix operations of platforms such as Amazon, TikTok, and Facebook.
Team collaboration and permission control
Users can flexibly assign permissions to team members to share and manage browser configuration files, and reduce the risk of internal data leakage through role classification.
RPA automation and plug-in extension
Built-in drag-and-drop automation tools can complete repeated operations such as product listing and form filling in one click; open a large number of plug-in interfaces to support custom development to adapt to different business scenarios.
3. Four major advantages: Why choose Bit?
Safe and stable
Adopting dynamic encryption technology and pure IP matching, the protection level reaches the industry-leading level, and the operation stability is as high as 99.995%.
Convenient operation
The interface is simple and intuitive, and supports one-click generation of configuration files, so novice users can also get started quickly.
Multi-platform compatibility
Covering Windows, Mac systems and mobile terminals, and adapting to the network environment of 150+ countries/regions.
Outstanding cost-effectiveness
Provide 10 basic environments for free for life, and the price of paid packages is only 50%-70% of similar products, and long-term limited-time discount activities (such as 50% discount on June 18).
4. applicable scenarios: Who needs Bit more?
Cross-border e-commerce sellers: manage multi-platform stores to avoid the risk of account suspension;
Social media operators: batch account maintenance, content synchronization release;
Advertising and marketing teams: multi-account delivery testing, optimize ROI;
Data crawling practitioners: break through anti-crawling restrictions and efficiently obtain public information.
5. identify genuine products: beware of piracy risks
Recently, some criminals have forged Bit official websites (such as bit-browser.cn, bitzhiwen.com, etc.), and induced users to download virus-carrying clients through Baidu promotion. Please be sure to download through the only genuine channel http://www.bitbrowser.cn (Chinese official website), and identify the "Beijing Bit Internet Technology Co., Ltd." logo.
Summary:
BitBrowser takes technological innovation as its core and continuously iterates user needs, and has become a benchmark tool in the field of overseas business anti-correlation. Whether it is a start-up team or a large enterprise, it can seize the initiative in global competition through its advantages of security, efficiency and low cost. Visit the official website now to experience it and start your worry-free multi-account operation journey!
|
|
Multilogin Latest Review in 2025: Can it Meet Your Anti-Detection Needs? |
In the previous article, we have evaluated many anti-detection browsers, including adspower, dolphin-anty, etc. In this article, we evaluated Multilogin browser for everyone. This is a product from Estonia. Multilogin browser eliminated its Multilogin 6 version in March 2025 and released its new version Multilogin X, which is known as the "new generation of anti-detection browser". This article analyzes the functions of its upgraded version to confirm whether this so-called new generation of products has advantages in the modern anti-detection browser industry and whether it is worth using?
Ⅰ. What are the advantages of Multilogin X compared to Multilogin 6?
According to official information, the upgrade of Multilogin X is mainly reflected in the following aspects:
1. Interface and access method
New desktop application and web management interface, support mobile access (Multilogin 6 is only for desktop).
Cloud configuration files support multi-device synchronization while retaining local storage to improve speed.
2. API function expansion
Provide four packages: Starter, Solo, Team, and Custom, covering personal to enterprise-level needs.
API endpoints cover all functions, with higher rate limits and more complete documentation (the old version only supports limited APIs).
3. Proxy and Cookie Management
Added the "Multilogin Proxy" service, providing residential IP and traffic reward mechanism.
Supports cookie export and "pre-made cookies" to warm up accounts (the old version has no export function).
4. Team collaboration and efficiency tools
Added AI-driven "Quick Operations" to convert text instructions into automated processes.
Team role permissions are refined (3 new advanced roles are added) and support multi-project management (the old version only has 2 roles).
5. Data security and recovery
Introduced the "Recycle Bin" function to restore accidentally deleted configuration files (deleted in the old version means permanent loss).
Ⅱ. Does Multilogin X have advantages over other fingerprint browsers?
Although Multilogin X has many improvements compared to Multilogin 6, it does not have any advantages over most products on the market. Whether it is API function, web login, proxy traffic, or cloud files, Cookie export, import and preheating functions, as well as multiple window management functions, they are all common fingerprint browser functions. The results of these upgrades will make Multilogin X version closer to modern anti-detection browsers, but these functions are not unique. You can also experience them in well-known anti-detection browsers, such as BitBrowser and Adspower. You can enjoy these functions in the ten permanently free windows of BitBrowser.
Technical level: Multilogin X has innovations in AI commands and proxy services, but BitBrowser free strategy is more universal.
Cost level: Multilogin X pricing is still at the high end of the industry, and the cost-effectiveness is insufficient for small and medium-sized users. BitBrowser free 10 environment can meet basic needs, and there is no additional charge for automation functions.
Market positioning: Suitable for enterprise-level users who need residential IP proxy and team fine management, but for individuals or small teams, BitBrowser is more flexible, and the e-commerce industry can use Huobao e-commerce browser to obtain high-quality proxies.
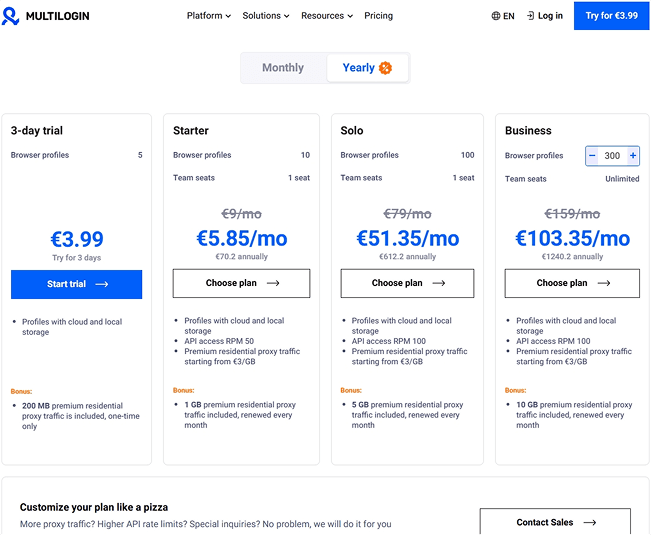
Ⅲ. In the end, should you choose Multilogin X browser?
Although the update from Multilogin 6 to Multilogin X has accelerated the process of Multilogin anti-detection browser entering the modern anti-detection browser, compared with most advanced anti-detection browsers, such as Bitbrowser, it does not have obvious advantages in terms of function, and its price is much higher than other products. The free package of Bitbrowser (10 free windows and one sub-account) costs 9 euros (RMB 70) per month in Multilogin, and it does not support free use. There is only a 4 euro three-day trial package (RMB 30), and the cost of use is much higher than other modern browsers.
Overall, for users in Estonia and nearby areas, Multilogin X's customer service and interface design may be more suitable for local people's language and operating habits, but for users who need higher cost performance, Bitbrowser is undoubtedly a better choice.
|
|
A comprehensive guide to registering and managing multiple Twitter accounts at the same time |

|
|
What can a virtual browser do? |

1. Secure browser environment
2. Privacy protection
3. Function customization
Summary:
|
|
What is the principle of fingerprint cloud phone? |

What are the advantages of Bit Fingerprint Cloud Phone?
|
|
Why do most fingerprint browsers use the Chrome kernel? |

Why are most fingerprint browsers Chrome kernels?
1: Functional advantages of the Chrome kernel
2. Functional requirements of fingerprint browsers
|
|
Using BitBrowser to Automatically Login to Web Pages with Cookies |

1. The core role and mechanism of Cookie
2. The application of Cookie in automatic login
3. Automatic login in BitBrowser
4. Security and privacy protection
Summary:
|
|
What determines the cost of promoting a website? And how to reduce the cost |
Next, what are the key factors that affect the cost of website promotion?

Solutions to reduce the cost of website promotion:

1. Clear goals and strategies
2. Accurately locate the target audience
3. Optimize keyword selection
4. Focus on content marketing
5. Reasonable planning of advertising budget
6. Utilize free promotion channels
7. Monitor and analyze data
What is SEO optimization browser?
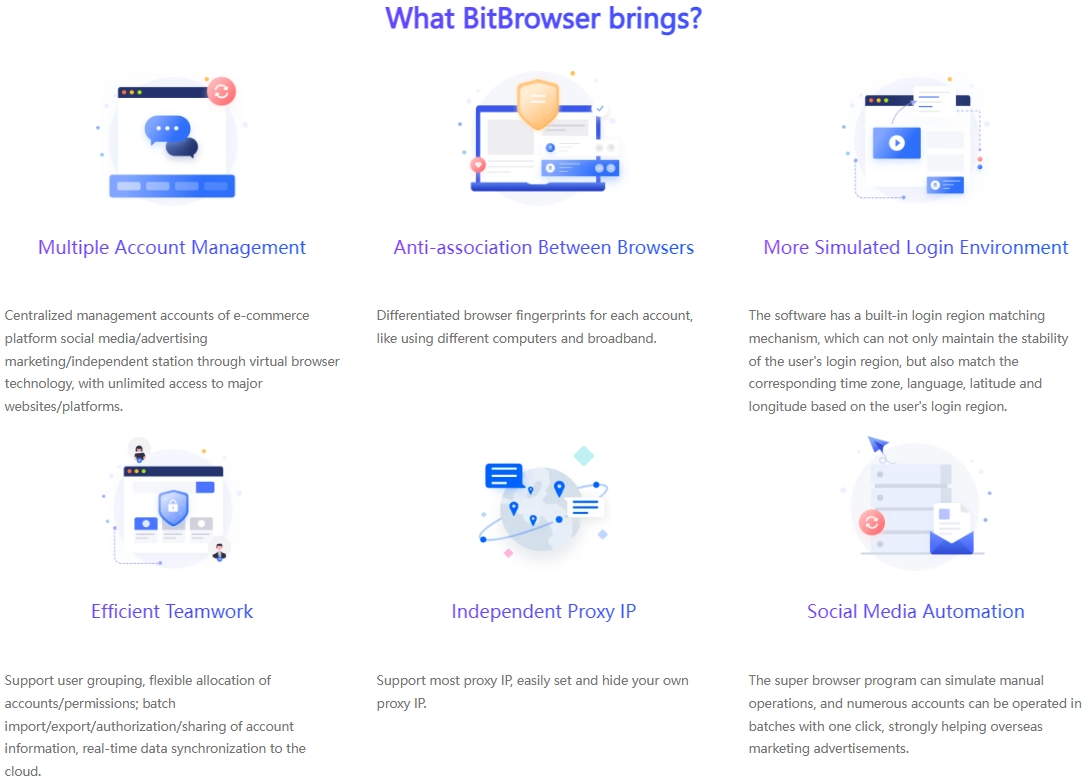
Summary:
|
|
Multi-account browser helps you solve the problem of IP association of multiple Shopee stores |

|
|
How to use multi-account browser to achieve multi-account maintenance in cross-border e-commerce |

|
|
What browsers can be used for multiple openings? How many accounts can be logged in? |

Core Advantage Analysis:
Recommended choice: BitBrowser
|
|
In-depth analysis of TikTok's risk control mechanism and prevention using fingerprint browser |

Exploring TikTok's risk control mechanism
Fingerprint browser: a powerful new tool to avoid risk control
Application strategy
Notes
|
|
Analysis of reasons for Tinder account ban |

Overview of Tinder Platform
Analysis of Tinder's Account Ban Policy
The role of BitBrowser
|
|
How to open multiple browsers without affecting each other? |

|
|
Will using a pure proxy IP network with a fingerprint browser prevent association? |

Privacy protection and account security have become the focus of many users. Especially in the fields of multi-account management, cross-border e-commerce, social media operations, etc., how to effectively prevent the association between accounts has become an urgent problem to be solved. The combination of pure proxy IP network and fingerprint browser is an effective anti-association strategy.
Pure proxy IP network: building a secure access channel
Fingerprint browser: simulate real user environment
The anti-association effect of combined use
|
|
Can a proxy IP-specific fingerprint browser hide local user privacy? |
Can a proxy IP-specific fingerprint browser hide local user privacy?

With the popularity of network applications, personal privacy protection has become an increasingly important topic. Proxy IP and fingerprint browser, as two common network security tools, are widely used to protect user privacy and enhance network security. So, can the fingerprint browser used in combination with the proxy IP really effectively hide the privacy of local users?
Can a proxy IP-specific fingerprint browser hide local user privacy?

With the popularity of network applications, personal privacy protection has become an increasingly important topic. Proxy IP and fingerprint browser, as two common network security tools, are widely used to protect user privacy and enhance network security. So, can the fingerprint browser used in combination with the proxy IP really effectively hide the privacy of local users?
|
|
Overseas social media matrix anti-association strategy: proxy IP unlimited browser |

In this digital age filled with massive data, social media is not only a tool for people to communicate in daily life, but also an important platform for personal image building and business expansion. However, with the continuous development of social networks, the problem of account association is like a crisis lurking in the dark, silently eroding the privacy and security of users. Next, this article will lead you to deeply explore the root cause of the easy association of overseas social media matrices, and unveil the mystery and practical skills of proxy IP unlimited browser as a privacy defender.
1. Unveiling the mystery of overseas social media matrix association

2. Proxy IP Unlimited Browser Protects Your Security

3. Proxy IP Unlimited Browser Usage Guidelines
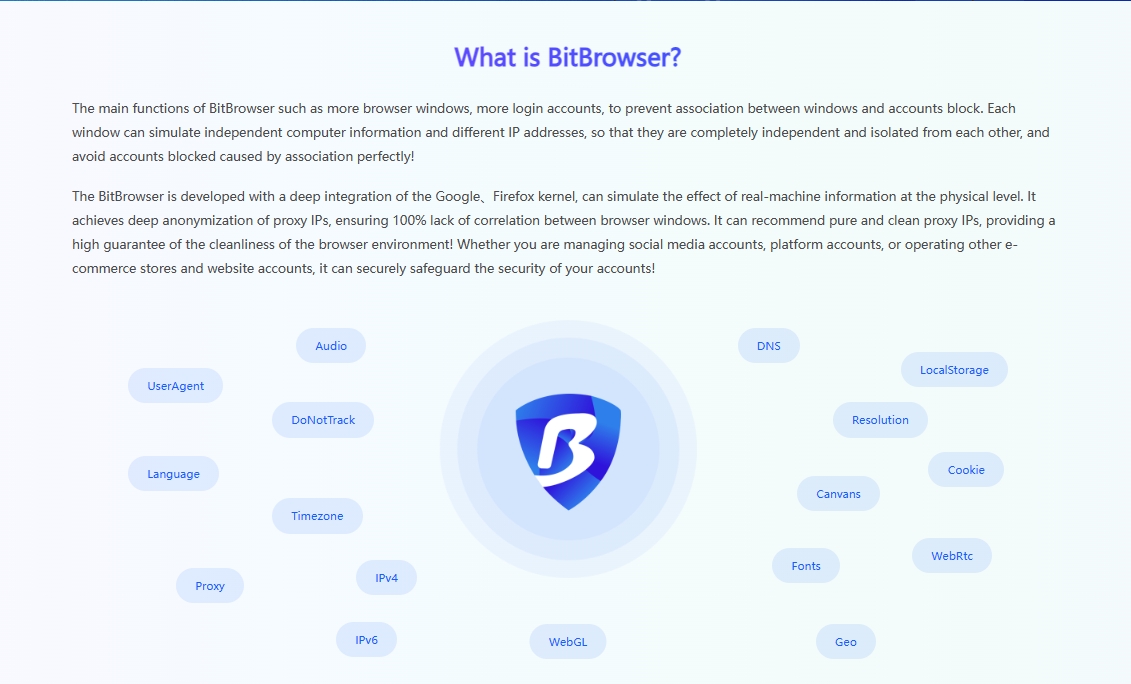
4, reasonable use of proxy IP with proxy IP unlimited browser
Summary:
|
|
Can a proxy IP-specific fingerprint browser hide local user privacy? |

With the popularity of network applications, personal privacy protection has become an increasingly important topic. Proxy IP and fingerprint browser, as two common network security tools, are widely used to protect user privacy and enhance network security. So, can the fingerprint browser used in combination with the proxy IP really effectively hide the privacy of local users?
|
|






