BitBrowser - How to quickly build a TikTok account matrix and raise accounts in batches! |

TikTok account matrix has become a common strategy for overseas markets. What are its advantages? Will multi-account operation not be blocked? How to build an account matrix at low cost?
Multi-account operation can achieve rapid growth of fans, segment account groups, output content vertically, and reduce the operating risk of a single account.
There are two main methods for building account matrices. The first is to use multiple mobile phones for operation. Such an account environment is the closest to real users, but the cost is too high. If you want to operate a large number of accounts in batches, you need to buy multiple mobile phones, one account corresponds to one mobile phone, and manpower is required to manage the mobile phones one by one, which will also consume too much time and energy.
Don't want to buy a large number of mobile phones? Then you need to use a fingerprint browser to simulate multiple environments on the Internet to operate multiple accounts.
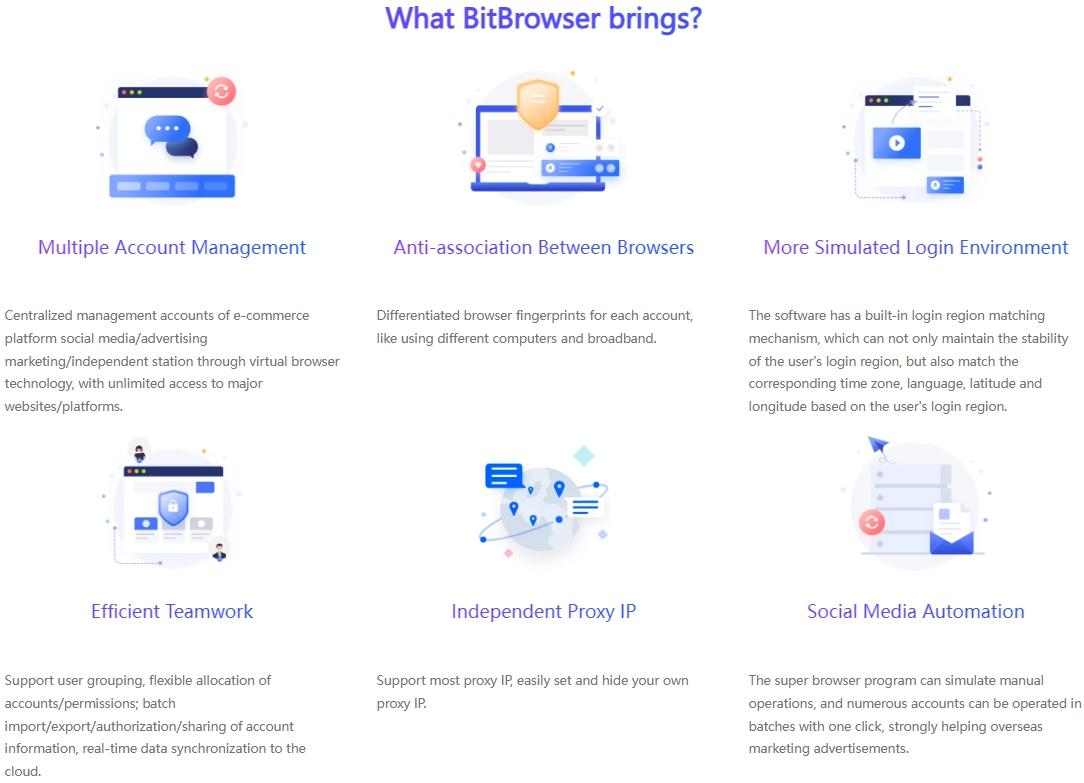
Advantages of using BitBrowser to build accounts
First, the equipment cost and labor cost are low.
You only need to register and download the BitBrowser client to use it. You don’t need to buy a large number of mobile phones. The BitBrowser can generate multiple virtual fingerprint browsers. Each browser can set an independent IP address to facilitate the global operation of enterprises. The independent fingerprint browser environment can effectively isolate the data and prevent being tracked by the website and associated with the account.
The batch import function of the BitBrowser can be used to batch manage multiple accounts, batch import and export cookies, encrypt account data, and automatically fill in account passwords and other information.
In the process of operating multiple accounts, the most difficult and troublesome thing is the account maintenance process. It takes a lot of time to browse, like, and comment on external videos for each account to activate the account.
Such repetitive work can be completely freed by the RPA automation function of the BitBrowser. Through process design, you can set tasks that need to be completed automatically, such as liking every three videos and refreshing a video every 10 seconds.
BitBrowser is suitable for multiple social media accounts. It can not only log in to TikTok, Facebook, YouTube, but also log in to Douyin, Xiaohongshu, Baijiahao, etc.
Using fingerprint browser is the most cost-effective choice in multi-account operation. It is easy to get started, low cost, RPA automation scripts can handle repetitive work, team functions are convenient for asset management, high availability, and can set up other website accounts at the same time.
|
|
Anti-detection browser dedicated proxy IP: the guardian of network privacy and security |

In the vast world of the Internet, privacy and security have always been one of the most concerned issues for users. With the development of network technology, various websites and platforms have strengthened user identification and tracking mechanisms in order to safeguard their own interests. In order to meet this challenge, proxy IP for anti-detection browsers came into being and became an important tool for protecting user privacy and enhancing anonymity.
What is an anti-detection browser?
Anti-detection browsers, as the name suggests, are advanced web browsers that can simulate different browser fingerprints. Browser fingerprints refer to a series of unique information generated by the browser and the operating system, including screen resolution, operating system, browser category and version, installed fonts and plug-ins, etc. Websites usually rely on this information to identify and track users. Anti-detection browsers simulate this information, making it difficult for websites to determine the true identity of the current visitor, thereby effectively preventing tracking and association.
The role of proxy IP
As a "springboard" in the network, the basic principle of proxy IP is that users first access the Internet through a proxy server, so that the record left on the Internet is the IP address of the proxy server, not the user's real IP. This mechanism can not only help users break through IP access restrictions, but also hide the real IP to achieve anonymous access. For users of multi-account operations such as cross-border e-commerce and online marketing, proxy IP is an important tool to circumvent platform audits and prevent account bans.
Advantages of dedicated proxy IP for anti-detection browser
Combining anti-detection browser with dedicated proxy IP can provide users with more comprehensive and powerful privacy protection. On the one hand, anti-detection browser simulates different browser fingerprints, making it difficult for websites to identify the user's true identity; on the other hand, dedicated proxy IP further hides the user's network activity track, making tracking more difficult. This dual protection mechanism greatly improves the anonymity and security of users. Well-known domestic anti-detection browsers include BitBrowser and well-known foreign browsers such as Linken Ball Browser.
In addition, the dedicated proxy IP for anti-detection browser is also highly flexible and scalable. Users can change the proxy IP address at any time according to actual needs, and even simulate different geographical locations and network environments, so as to easily cope with various complex network scenarios.
Application scenarios and challenges
Dedicated proxy IP for anti-detection browser is widely used in cross-border e-commerce, online marketing, data capture and other fields. However, this technology also faces certain challenges. On the one hand, with the continuous upgrading of website identification technology, the effectiveness of anti-detection browsers and proxy IPs may be affected; on the other hand, the abuse of these technologies may also violate relevant laws, regulations and platform policies, bringing unnecessary risks to users.
Therefore, when using anti-detection browser dedicated proxy IP, users need to abide by relevant laws, regulations and platform policies to avoid illegal operations. At the same time, regular updating and checking of proxy IP and browser configurations are also the key to maintaining anti-association effects.
Conclusion
As the guardian of network privacy and security, the anti-detection browser dedicated proxy IP provides users with a powerful protection mechanism. However, its application also needs to be carried out under the premise of legality and compliance. In the future development, with the continuous advancement of technology and the improvement of laws, we have reason to believe that this field will become more mature and reliable.
|
|
Is it too late to enter the TikTok industry now? How can newcomers do TikTok? |

When we turn our attention to the TikTok short video social platform that has set off a global craze, "Is it appropriate to invest in TikTok now?" and "How difficult is it to explore in the TikTok field?" These two key questions, this article will explore in depth from a new perspective to provide a strong reference for your decision-making.
First, let's take a look at the question "Is it too late to join TikTok now?" In fact, now is not too late, but a great time. TikTok is like a solid bridge to promote cross-cultural communication. Its user scale is growing at an impressive rate, and its user loyalty is extremely high, which fully demonstrates that the platform is in a golden stage of rapid development. The platform has launched a series of innovative measures, such as algorithm optimization and upgrades, support plans for creators, etc., with the aim of building a broader display stage for new creators, so that every creator with a dream has the opportunity to shine. Therefore, seizing this opportunity and joining TikTok is undoubtedly a wise choice with huge potential and many opportunities.
However, when it comes to "the difficulty of exploring the TikTok field", we need to look at it dialectically. It is undeniable that the vast stage of TikTok is full of endless possibilities, but it is also accompanied by fierce competition and numerous challenges. In this ocean of creativity, how to stand out and become a unique existence in the eyes of users is a difficult problem that every creator must seriously think about and solve. This requires creators to not only have keen perception and be able to accurately grasp the trend of the times and the preferences of users, but also have the courage to innovate boldly, continue to surpass themselves, and attract and retain audiences with high-quality and creative content. In addition, in-depth understanding and strict compliance with the rules of the platform are also one of the key factors to success.

In order to develop rapidly on TikTok, the following strategies may help you:
Precise positioning and planning strategy: Before entering this field, you must clearly determine your brand or personal image, clarify the theme and style of the content, and develop a long-term and feasible development plan.
In-depth insight into the platform ecology: fully familiar with TikTok's recommendation mechanism, user behavior patterns and the latest policy regulations, laying a solid foundation for accurate positioning and efficient operation.
Create unique and high-quality content: Under the premise of ensuring high-quality content, focus on exploring uniqueness and innovation, so that your work can stand out among many videos.
Strengthen community interaction and communication: actively respond to fans' messages and comments, build close community relationships, and enhance users' sense of participation and dependence on the platform through live broadcasts, participation in challenges, etc.
Flexible response and continuous progress: The market and platform environment are ever-changing. We must maintain keen insight, adjust strategies in time, and constantly learn new skills to better adapt to the ever-changing market needs.
If a novice wants to achieve good results in the TikTok marketing market, it will undoubtedly require multiple attempts and multiple accounts, but multiple TikTok accounts will more easily trigger the platform's risk control mechanism, which may trigger associations and lead to the possibility of account suspension. For details, please refer to: (BitBrowser - How to quickly build a TikTok account matrix and batch raise accounts!).
How to set up a safe network environment for TikTok account?
For the demand of realizing efficient and stable operation of multiple TikTok account systems on a single device, especially for computer users, the introduction of high-end browser isolation solutions such as BitBrowser has undoubtedly opened a new chapter for the sound management and efficient operation of accounts.
BitBrowser, as an account management tool designed for e-commerce, has the key advantage of excellent account isolation and protection functions. It not only provides deeply personalized browser scenes, but also cleverly integrates many innovative technologies to ensure that each account can run safely in a unique digital world.
BitBrowser has created many independent virtual browser environments, each of which can be configured with exclusive user agents, simulated operating systems and even unique font settings according to the specific requirements of users. This highly customized method is like giving each account a unique digital identity, greatly reducing the risk of account association caused by similar browser fingerprints.
TikTok's lack of network connection may be caused by many factors, such as network configuration errors, IP address bans, or server failures. The solution is: first, check the stability of the network connection and try to change the network environment; second, clarify whether the IP address is restricted due to the use of inappropriate proxy or VPN, and adjust or stop using it in time; third, if the problem still exists, you can try to contact TikTok customer service for technical assistance.
In view of the specific needs of e-commerce multi-account operation, BitBrowser is equipped with a powerful proxy IP management function. By assigning a dedicated proxy IP to each account, a complete separation at the IP address level is achieved, which effectively avoids the problem of mutual interference or association between accounts caused by repeated use of IP. This function lays a solid foundation for e-commerce companies to expand their business safely and efficiently on a global scale.
In order to further strengthen the isolation effect between accounts, BitBrowser has also launched an advanced browser fingerprint customization service. Users can customize unique browser fingerprint information for different accounts according to their own needs, and improve the anonymity and security of accounts by prohibiting or modifying the fingerprint data of key Web technologies. This function is like putting an invisible protective armor on the account, allowing the account to be more free in the digital world.
Summary:
TikTok is not only a hot field at the moment, but also a key position for future social and content creation. Although the road ahead is full of challenges, it is these challenges that have created countless success stories. As long as you dare to try and persist in innovation, you will have the opportunity to shine your own dazzling light in this vast sea of stars. With its unique account isolation technology and powerful function settings, BitBrowser provides all-round support and protection for e-commerce companies' multi-account operations on many platforms such as TikTok. By building a safe and independent account ecosystem, it promotes companies to move forward steadily in the global market.
|
|
Intelligent capture of e-commerce data, a marketing method used by e-commerce sellers |
In the current highly digital era, the intelligent crawling of e-commerce data has gradually become a key factor in the development of enterprises. It is no longer limited to simple data acquisition, but with the help of cutting-edge technology and intelligent means, it conducts in-depth exploration, detailed analysis and rapid integration of rich, diverse and complex data in the e-commerce field. These data include detailed product information sets, transaction process records, user preference portraits, market trend forecasts, etc., which provide strong support for e-commerce companies in precise promotion, inventory optimization and regulation, and keen insight into market opportunities.
Key features and difficulties of intelligent crawling of e-commerce data
1. Efficient processing of huge amounts of data
The large-scale data generated by e-commerce platforms every day urgently requires the crawling system to have super parallel processing capabilities and flexible expansion performance to support the real-time acquisition and analysis of PB-level data. The close combination of intelligent algorithms and cloud computing has become an important way to overcome this problem.
For example, large e-commerce platforms like Amazon generate extremely large amounts of data every day. Without strong processing capabilities, it is impossible to capture and analyze key information in a timely and effective manner.
2. Accurate tracking of real-time dynamic data
When faced with fast-updating data such as frequent price fluctuations and continuous changes in inventory, the intelligent crawling system must integrate real-time stream processing technology to ensure the timeliness and accuracy of data and provide the fastest feedback for decision-making.
Taking eBay's limited-time promotion as an example, prices and inventory information change at any time. Only accurate tracking can allow companies to adjust their strategies in a timely manner.
3. Unified analysis of multi-source and differential data
The data types of e-commerce platforms are rich and diverse, covering text, images, videos, structured and unstructured data. Using cutting-edge AI technologies such as natural language processing and image recognition to achieve intelligent analysis and integration of multi-source heterogeneous data has become a highlight in the crawling process.
For example, the product reviews on Shopee have both text and pictures, and unified analysis is needed to fully understand user feedback.
4. Countermeasures for advanced anti-crawling strategies
In view of the increasingly stringent anti-crawling methods of e-commerce platforms, intelligent crawling strategies need to continue to innovate, such as using dynamic proxy pools, simulating real user behavior, and predicting anti-crawling rules through machine learning to ensure the confidentiality and persistence of data collection.
5. Double scrutiny of legal ethics
In the entire data capture process, relevant legal provisions such as data protection laws and privacy policies must be strictly followed, and the industry's ethical standards must be followed to ensure that data collection, use, and storage are legal and compliant, and to fully protect the privacy rights and interests of users.

Implementation methods for intelligent e-commerce data capture
1. Clarify the direction, legality and compliance first
Precisely define the goals and scope of data collection to ensure that data collection behavior complies with various laws and regulations and platform policy regulations.
2. Build an intelligent capture platform
Integrate cutting-edge technologies such as AI, big data, and cloud computing to build an efficient and scalable intelligent capture platform to achieve automatic and intelligent data acquisition and processing.
3. Configure advanced anti-crawling strategies
Combining dynamic proxy, intelligent request scheduling, user behavior simulation and other advanced technical means, cleverly bypass the anti-crawling mechanism of the e-commerce platform to ensure the stability and security of data collection.
4. Data cleaning and integration
The captured raw data is cleaned, deduplicated, formatted, etc. to ensure data quality; through data integration technology, a unified data view is created to lay a solid foundation for subsequent analysis.
5. Intelligent analysis and application
Use data mining, machine learning and other algorithms to conduct in-depth analysis of the integrated data, explore the hidden value behind the data, and provide decision-making basis for e-commerce companies in precision marketing, inventory management, supply chain optimization, etc.
BitBrowser to deal with e-commerce capture difficulties
Even though it is difficult to capture data in the e-commerce industry, the BitBrowser equipped with top-notch hidden technology provides unprecedented powerful assistance for senior developers, enabling them to deal with various situations with ease.
Personalized fingerprint identity management
In the vast world of data collection, the ability to control multiple identities is the core element to success. The BitBrowser can not only build, but also excellently manage a square array composed of many personalized identities, each of which has an independent cookie world, cache space and local data treasure house.
This is undoubtedly a double breakthrough in efficiency and security for implementing complex marketing plans, implementing multi-account planning, or flexibly arranging access rights in teamwork. The smooth switching between identities makes the data collection process both accurate and efficient, greatly optimizes the use of resources, and saves developers a lot of time and energy.
User Agent
Stepping into the mysterious veil of the digital world, BitBrowser uses dynamic imitation of user agent characteristics from all over the world to make it difficult for websites to detect the real explorers behind. This technology seems to have performed a mysterious illusion, making the data acquisition action disappear under the gaze of many eyes, easily avoiding those sophisticated identification mechanisms designed to capture robots. Its powerful concealment function expands the scope of data exploration, allowing developers to break through many constraints and obtain valuable information from a wider range of sources, while ensuring the secrecy and efficiency of the action, and ensuring the continuity and stability of data collection.
Perfect integration of agent network
On the grand stage of data capture, the exquisite integration of agent network is like opening up hidden channels for explorers. The proxy integration system built into BitBrowser makes the flexible change of IP addresses like natural breathing, easily bypassing various obstacles and speed limits set by websites.
For warriors who perform large-scale data crawling tasks, this function is not only a significant improvement in efficiency, but also a strong consolidation of the security line. The deep integration of the proxy network not only increases the scope and depth of data acquisition, but also provides an indestructible protective barrier for every exploration without knowing it, making it impossible for the website to use its countermeasures.
Summary:
The intelligent crawling of e-commerce data is a complex systematic project, which requires companies to have deep technical skills, keen market perception and strict legal and moral self-discipline. By continuously optimizing crawling strategies, improving technical standards, and strengthening compliance management, e-commerce companies can use data resources more efficiently, promote business innovation and development, and achieve data-driven intelligent growth. BitBrowser provides more possibilities for e-commerce sellers to crawl data, making it easier for sellers to deal with the anti-climbing strategies of e-commerce platforms. For the convenience of sellers, Bit Browser will give you 10 permanent free windows when you download and register now, first come first served.
Intelligent capture of e-commerce data, a marketing method used by e-commerce sellers
Time: 2024-08-08 10:54 Author: BitBrowser Click:

In the current highly digital era, the intelligent crawling of e-commerce data has gradually become a key factor in the development of enterprises. It is no longer limited to simple data acquisition, but with the help of cutting-edge technology and intelligent means, it conducts in-depth exploration, detailed analysis and rapid integration of rich, diverse and complex data in the e-commerce field. These data include detailed product information sets, transaction process records, user preference portraits, market trend forecasts, etc., which provide strong support for e-commerce companies in precise promotion, inventory optimization and regulation, and keen insight into market opportunities.
Key features and difficulties of intelligent crawling of e-commerce data
1. Efficient processing of huge amounts of data
The large-scale data generated by e-commerce platforms every day urgently requires the crawling system to have super parallel processing capabilities and flexible expansion performance to support the real-time acquisition and analysis of PB-level data. The close combination of intelligent algorithms and cloud computing has become an important way to overcome this problem.
For example, large e-commerce platforms like Amazon generate extremely large amounts of data every day. Without strong processing capabilities, it is impossible to capture and analyze key information in a timely and effective manner.
2. Accurate tracking of real-time dynamic data
When faced with fast-updating data such as frequent price fluctuations and continuous changes in inventory, the intelligent crawling system must integrate real-time stream processing technology to ensure the timeliness and accuracy of data and provide the fastest feedback for decision-making.
Taking eBay's limited-time promotion as an example, prices and inventory information change at any time. Only accurate tracking can allow companies to adjust their strategies in a timely manner.
3. Unified analysis of multi-source and differential data
The data types of e-commerce platforms are rich and diverse, covering text, images, videos, structured and unstructured data. Using cutting-edge AI technologies such as natural language processing and image recognition to achieve intelligent analysis and integration of multi-source heterogeneous data has become a highlight in the crawling process.
For example, the product reviews on Shopee have both text and pictures, and unified analysis is needed to fully understand user feedback.
4. Countermeasures for advanced anti-crawling strategies
In view of the increasingly stringent anti-crawling methods of e-commerce platforms, intelligent crawling strategies need to continue to innovate, such as using dynamic proxy pools, simulating real user behavior, and predicting anti-crawling rules through machine learning to ensure the confidentiality and persistence of data collection.
5. Double scrutiny of legal ethics
In the entire data capture process, relevant legal provisions such as data protection laws and privacy policies must be strictly followed, and the industry's ethical standards must be followed to ensure that data collection, use, and storage are legal and compliant, and to fully protect the privacy rights and interests of users.

Implementation methods for intelligent e-commerce data capture
1. Clarify the direction, legality and compliance first
Precisely define the goals and scope of data collection to ensure that data collection behavior complies with various laws and regulations and platform policy regulations.
2. Build an intelligent capture platform
Integrate cutting-edge technologies such as AI, big data, and cloud computing to build an efficient and scalable intelligent capture platform to achieve automatic and intelligent data acquisition and processing.
3. Configure advanced anti-crawling strategies
Combining dynamic proxy, intelligent request scheduling, user behavior simulation and other advanced technical means, cleverly bypass the anti-crawling mechanism of the e-commerce platform to ensure the stability and security of data collection.
4. Data cleaning and integration
The captured raw data is cleaned, deduplicated, formatted, etc. to ensure data quality; through data integration technology, a unified data view is created to lay a solid foundation for subsequent analysis.
5. Intelligent analysis and application
Use data mining, machine learning and other algorithms to conduct in-depth analysis of the integrated data, explore the hidden value behind the data, and provide decision-making basis for e-commerce companies in precision marketing, inventory management, supply chain optimization, etc.

BitBrowser to deal with e-commerce capture difficulties
Even though it is difficult to capture data in the e-commerce industry, the BitBrowser equipped with top-notch hidden technology provides unprecedented powerful assistance for senior developers, enabling them to deal with various situations with ease.
Personalized fingerprint identity management
In the vast world of data collection, the ability to control multiple identities is the core element to success. The BitBrowser can not only build, but also excellently manage a square array composed of many personalized identities, each of which has an independent cookie world, cache space and local data treasure house.
This is undoubtedly a double breakthrough in efficiency and security for implementing complex marketing plans, implementing multi-account planning, or flexibly arranging access rights in teamwork. The smooth switching between identities makes the data collection process both accurate and efficient, greatly optimizes the use of resources, and saves developers a lot of time and energy.
User Agent
Stepping into the mysterious veil of the digital world, BitBrowser uses dynamic imitation of user agent characteristics from all over the world to make it difficult for websites to detect the real explorers behind. This technology seems to have performed a mysterious illusion, making the data acquisition action disappear under the gaze of many eyes, easily avoiding those sophisticated identification mechanisms designed to capture robots. Its powerful concealment function expands the scope of data exploration, allowing developers to break through many constraints and obtain valuable information from a wider range of sources, while ensuring the secrecy and efficiency of the action, and ensuring the continuity and stability of data collection.
Perfect integration of agent network
On the grand stage of data capture, the exquisite integration of agent network is like opening up hidden channels for explorers. The proxy integration system built into BitBrowser makes the flexible change of IP addresses like natural breathing, easily bypassing various obstacles and speed limits set by websites.
For warriors who perform large-scale data crawling tasks, this function is not only a significant improvement in efficiency, but also a strong consolidation of the security line. The deep integration of the proxy network not only increases the scope and depth of data acquisition, but also provides an indestructible protective barrier for every exploration without knowing it, making it impossible for the website to use its countermeasures.
Summary:
The intelligent crawling of e-commerce data is a complex systematic project, which requires companies to have deep technical skills, keen market perception and strict legal and moral self-discipline. By continuously optimizing crawling strategies, improving technical standards, and strengthening compliance management, e-commerce companies can use data resources more efficiently, promote business innovation and development, and achieve data-driven intelligent growth. BitBrowser provides more possibilities for e-commerce sellers to crawl data, making it easier for sellers to deal with the anti-climbing strategies of e-commerce platforms. For the convenience of sellers, Bit Browser will give you 10 permanent free windows when you download and register now, first come first served.
|
|
How do foreign traders use Facebook for marketing promotion? |

Facebook has a huge number of users and is a hot commodity in the eyes of B2B companies. If you don't make good use of this traffic, it's like missing out on 100 million.
However, some B2B companies still don't know how to effectively promote on Facebook?
So today I will take you to learn how to effectively promote on Facebook and quickly maintain multiple accounts.
1. Techniques of Facebook Marketing and Promotion
When conducting marketing and promotion on Facebook, you should first complete the formulation of marketing strategies and the establishment of accounts to ensure the exposure of companies and brands on the entire network and help companies accurately locate target audiences.
1. Create a professional Facebook page
You need to create a professional Facebook page to showcase your products or services.
Make sure the page design is clear, concise, and contains information about your business. In this way, potential customers can establish brand awareness of B2B companies and increase exposure.
2. Provide valuable content
Publish high-quality and valuable content on Facebook to attract potential customers.
Creating explosive content can help shorten the sales cycle, convert viewers into customers, and attract customers to send inquiries.
In order to have better exposure, B2B companies should plan the theme and frequency of Facebook posts according to their own situation.
Posting content: You can share industry news, customer cases, product updates, etc. to ensure that the content is relevant to your target audience and maintain a consistent brand image.
Posting frequency: Maintain a posting frequency of 3-6 times a week to increase potential user stickiness.
3. Data analysis and active interaction
Pay close attention to Facebook data analysis tools to understand your audience, their interests and behaviors.
And maintain active interaction with potential customers, collect their feedback and suggestions in a timely manner, and then adjust market strategies and product offerings.
4. Facebook advertising and advertising optimization
Facebook advertising is an effective and low-cost way to promote social media marketing.
Ads can be targeted to users based on specific information such as location, demographics, behavior, interests, etc.
B2B companies can measure the cost of Facebook advertising campaigns based on cost per click.
2. Rapid maintenance of multiple Facebook accounts
Facing Facebook's strict platform rules, accounts are likely to be banned during operation due to violations of regulations;
If there is only one account, it may affect the operation of the business, so companies will operate multiple accounts to disperse risks.
At the same time, the operation of multiple accounts can also help companies expand brand exposure, attract more user attention, and improve conversion rates.
In addition, the data of the account will inevitably be very low in the early operation. At this time, multiple accounts can be used to browse, like, comment on works and other operations to increase the weight of the account, which is helpful for the early development of the account.
Users can manage multiple Facebook accounts by using BitBrowser.
BitBrowser has the fingerprint information required for platform detection and can modify basic fingerprint information: UA, time zone, language, etc.;
You can also adjust the underlying fingerprint browser to support the modification of hardware fingerprint information such as Canvas, WebGL, Audio, etc., and add the proxy IP to generate a separate isolation environment (equivalent to a new device and a new browser), so that multiple accounts on the same device can be independently accessed.
Each FB account can generate a dedicated browsing environment (set a fixed IP).
At the same time, the RPA automation function of BitBrowser can help enterprises to automatically maintain accounts.
Those who operate Facebook batch accounts know the pain of manual operation. Using the automatic account maintenance function of Bit Browser can help save a lot of manpower and time.
You only need to set the time and the process to be operated. When the time comes, RPA will automatically like, comment on the video content, browse the web, etc.
And e-commerce friends can also use this function to interact with collections and add to cart, which is really cool!
|
|
Youtube multiple accounts safe sharing, solution sharing |

As the world's leading video sharing and social media giant, YouTube has a very large user base and a rich and diverse content ecosystem. It has long broken through the boundaries of simple video sharing and transformed into a global interactive platform, where hundreds of millions of users upload, browse and share videos every day. For this reason, many companies regard YouTube as an excellent place to carry out marketing and promotion, hoping to reach potential customers around the world, spread brand information, and promote business conversion.
Due to the wide and diverse global audiences, it is difficult for a single account to cover all target groups in an all-round way. Therefore, the multi-account operation strategy came into being, which allows companies to carry out more accurate content positioning and interactive management for different markets and audiences. The use of multi-account strategies on YouTube has the following core goals for companies:
Diversified content marketing: Publish a variety of content through different accounts to attract and retain a wider target audience.
Enhance brand influence: With the help of multi-account layout, expand user coverage, thereby significantly improving brand awareness.
Data-driven optimization: Based on the data analysis results of each account's performance, continuously optimize content strategies and improve marketing efficiency.
In the past, companies usually used multiple browsers, incognito mode or virtual machines to achieve multiple openings of YouTube accounts, but these methods have obvious shortcomings:
Complicated operation: Frequent switching of windows and browsers is required, and management efficiency is very low.
High risk of association: The same device and IP address are prone to account association problems, which in turn increases the possibility of account bans.
Serious resource loss: When the virtual machine is running, it will occupy a large amount of system resources, affecting the overall performance of the device.
In contrast, fingerprint browsers bring better solutions to companies. It allows users to log in to multiple YouTube accounts on the same device at the same time, and ensures that each browser instance has an independent identity by generating and managing unique browser fingerprint information (such as WebGL, Canvas, screen resolution, plug-in configuration, font style, etc.), which is a key factor for websites to identify users.
Using fingerprint browser to manage multiple YouTube accounts can effectively solve the following key problems:
Prevent account association and ban: Provide independent fingerprint environment and proxy IP to ensure the independence of account operation and reduce the risk of ban due to shared IP.
Efficient and convenient management: Support the safe operation of multi-platform accounts, create multiple browser environments to manage multiple accounts, and realize the automation and rapid development of business processes.
Enhance security: Each account runs in an independent browser window to achieve data isolation and improve security and privacy protection.
Optimize team collaboration: Team members can jointly manage multiple accounts without logging in separately on each member's device, achieving seamless collaboration and non-interference in account management.
Here, we strongly recommend BitBrowser, which focuses on ensuring the safe operation of multi-platform accounts and helping enterprises achieve business automation and rapid growth. It not only protects your accounts on global social media, cross-border e-commerce and other platforms from association detection and ban, but also supports matrix operations on multiple platforms such as TikTok, Instagram, YouTube, Facebook, etc. With the help of BitBrowser, enterprises can easily achieve efficient management of multiple YouTube accounts and enhance brand influence and marketing effects. Whether it is automatic collection, mass messaging, or comment area management, the functions of BitBrowser can help companies stand out in the fierce market competition.
|
|
Twitter (X) account maintenance strategy, durable account development plan |
Twitter (X) Twitter, as a social media giant with great influence in the world, has a huge user base and has become an important platform for brands and individuals to expand global markets and implement marketing strategies. However, Twitter (X) Twitter has strict supervision on multi-account operations. As long as any abnormal behavior is found, the account may face the serious consequence of being banned. Therefore, on the basis of following the platform regulations, how to safely and efficiently cultivate high-powered and mature Twitter (X) Twitter accounts has become the key to the multi-account operation strategy.

How to cultivate Twitter (X) durable account?
Twitter (X) , with its advanced algorithms and monitoring system, can accurately detect abnormalities in login behavior and operation mode, such as multiple accounts logged in under the same IP address, or multiple accounts posting very similar content in a short period of time. These situations can easily be judged by the system as a connection between accounts, which may lead to temporary restrictions or permanent bans on accounts.
In order to effectively avoid the security alerts triggered by multi-account operations, the key is to cut off the direct connection between accounts. The following methods can be taken:
First, realize the differentiated use of IP addresses. It is necessary to ensure that each Twitter (X) account is logged in and operated through an independent IP address to prevent multiple accounts from sharing the same IP address, thereby reducing the risk of account being blocked due to IP association.
The second is to configure the device fingerprint independently. Set a unique device fingerprint for each account, and key information such as operating system, browser type and version, plug-in, font, etc. must be different. In addition to IP address, device fingerprint is also an important aspect of Twitter (X) monitoring.
The fingerprint browser provides a complete solution for multi-account operation. It can properly manage the device fingerprint of each account, so that each login presents a different user environment, which can greatly reduce the risk of account association and detection.
The specific strategy of using fingerprint browser to carry out Twitter (X) multi-account cultivation is as follows:
The first is to create an independent browsing session environment. Create an independent browsing environment for each Twitter (X) account to ensure that information such as browser settings, cache, cookies, etc. can be isolated from each other to avoid information crossover between accounts.
The second is to set personalized device fingerprints. For each account, adjust its device fingerprint, such as operating system type, browser type, screen resolution, etc., so that each account appears to be from a different physical device on Twitter (X).
Finally, do a good job of automated operation management. Use the automated function of the fingerprint browser to reasonably arrange the operation time and content release rhythm of each account to avoid too mechanical operation mode, so as to simulate the behavior habits of real users.
In addition, if you want to improve the account weight, you must also pay attention to the quality and uniqueness of the content, and there must be no duplication or plagiarism of content. In the initial registration stage of a new account, avoid frequent interactions, but gradually increase the number of likes, comments and reposts to simulate the natural growth process of normal user behavior. At the same time, the growth of the number of followers and fans should also be gradual to avoid a sharp increase in the short term.
Here, I recommend an excellent fingerprint browser to everyone - BitBrowser. BitBrowser focuses on the safe operation of multi-platform accounts, and can provide comprehensive solutions for business automation operations and rapid account growth. It can not only effectively avoid association detection and ban risks, but also meet the account operation needs of global social media, cross-border e-commerce and other platforms.
|
|
What is Super Browser? What can it be used for? |

Super browser is a browser customized for e-commerce business, with multi-opening and anti-association functions, designed to optimize store access speed and improve the security of multi-store management. Its core purpose is to improve the operating experience of e-commerce sellers, improve operational efficiency, and provide a secure store management platform.
What is a super browser?
Taking Bit Super Browser as an example, it can create an independent and secure environment for each e-commerce account. Since cross-border e-commerce platforms such as Amazon, Shopee, eBay and Wish prohibit a single seller from opening multiple stores, but due to business expansion needs, sellers often have to adopt a multi-store strategy to increase product exposure. However, this strategy must avoid the platform's detection mechanism. Super browser is the key to solving this problem. It allows each store account to log in with an independent IP address and computer environment, thereby avoiding the platform from discovering that the same seller is operating multiple stores, effectively preventing account association and store closure risks.
The main functions of super browser include:
Multi-account management: For e-commerce operators, managing multiple accounts is normal. Super browsers provide convenient multi-account management functions, allowing users to log in to multiple e-commerce platform accounts at the same time and maintain the independence between accounts, which is particularly important for cross-border e-commerce operations.
Automated operation: Through automation functions, super browsers can simplify repetitive tasks in daily operations, such as data entry and order processing. Automated operations such as automatic form filling, batch product uploading, and scheduled task execution can significantly improve work efficiency.
Privacy protection: Super browsers also pay attention to the privacy and security of users and provide a series of privacy protection measures. These measures include preventing data leakage, blocking trackers, clearing browsing history, etc., to protect merchants' business secrets and customer personal information. Some super browsers use virtual browser technology to assign a unique ID and configuration information to each browser, support independent modification of key privacy parameters such as IP and Canvas fingerprints, ensure that each browser environment is independent of each other, and further ensure the security isolation of accounts.
|
|
Twitter (X) account maintenance strategy, durable account development plan |
Twitter (X) Twitter, as a social media giant with great influence in the world, has a huge user base and has become an important platform for brands and individuals to expand global markets and implement marketing strategies. However, Twitter (X) Twitter has strict supervision on multi-account operations. As long as any abnormal behavior is found, the account may face the serious consequence of being banned. Therefore, on the basis of following the platform regulations, how to safely and efficiently cultivate high-powered and mature Twitter (X) Twitter accounts has become the key to the multi-account operation strategy.

How to cultivate Twitter (X) durable account?
Twitter (X) , with its advanced algorithms and monitoring system, can accurately detect abnormalities in login behavior and operation mode, such as multiple accounts logged in under the same IP address, or multiple accounts posting very similar content in a short period of time. These situations can easily be judged by the system as a connection between accounts, which may lead to temporary restrictions or permanent bans on accounts.
In order to effectively avoid the security alerts triggered by multi-account operations, the key is to cut off the direct connection between accounts. The following methods can be taken:
First, realize the differentiated use of IP addresses. It is necessary to ensure that each Twitter (X) account is logged in and operated through an independent IP address to prevent multiple accounts from sharing the same IP address, thereby reducing the risk of account being blocked due to IP association.
The second is to configure the device fingerprint independently. Set a unique device fingerprint for each account, and key information such as operating system, browser type and version, plug-in, font, etc. must be different. In addition to IP address, device fingerprint is also an important aspect of Twitter (X) monitoring.
The fingerprint browser provides a complete solution for multi-account operation. It can properly manage the device fingerprint of each account, so that each login presents a different user environment, which can greatly reduce the risk of account association and detection.
The specific strategy of using fingerprint browser to carry out Twitter (X) multi-account cultivation is as follows:
The first is to create an independent browsing session environment. Create an independent browsing environment for each Twitter (X) account to ensure that information such as browser settings, cache, cookies, etc. can be isolated from each other to avoid information crossover between accounts.
The second is to set personalized device fingerprints. For each account, adjust its device fingerprint, such as operating system type, browser type, screen resolution, etc., so that each account appears to be from a different physical device on Twitter (X).
Finally, do a good job of automated operation management. Use the automated function of the fingerprint browser to reasonably arrange the operation time and content release rhythm of each account to avoid too mechanical operation mode, so as to simulate the behavior habits of real users.
In addition, if you want to improve the account weight, you must also pay attention to the quality and uniqueness of the content, and there must be no duplication or plagiarism of content. In the initial registration stage of a new account, avoid frequent interactions, but gradually increase the number of likes, comments and reposts to simulate the natural growth process of normal user behavior. At the same time, the growth of the number of followers and fans should also be gradual to avoid a sharp increase in the short term.
Here, I recommend an excellent fingerprint browser to everyone - BitBrowser. BitBrowser focuses on the safe operation of multi-platform accounts, and can provide comprehensive solutions for business automation operations and rapid account growth. It can not only effectively avoid association detection and ban risks, but also meet the account operation needs of global social media, cross-border e-commerce and other platforms.
|
|
A computer can easily set up the network environment of the matrix account, and there is no need to worry about IP association. It's a good city. |

How to build the network environment of matrix accounts
Most cross-border enterprises will adopt the configuration method of "proxy IP + fingerprint browser" when operating multiple stores or doing matrix accounts. This configuration can generate multiple isolated windows in the browser, each window is equipped with a single IP, so that the accounts are effectively independent and achieve the effect of preventing IP association.
This method is simple and easy to operate, and will not affect the local browser to access domestic websites. It is very friendly to novices, so today we will take a detailed look at what is the Bit Fingerprint Browser and what functions the Bit Fingerprint Browser provides for cross-border enterprises.
Bit Fingerprint Browser is a powerful anti-association browser designed to provide users with better privacy protection and work efficiency. In addition to common browser functions, it also has a series of special functions that enable users to better manage accounts, customize fingerprints, customize IPs, open multiple browsers, etc.
Bit Fingerprint Browser can be used in business areas: cross-border advertising and e-commerce, advertising verification, media and music platforms, e-commerce platforms, payment platforms, data capture, account anti-association, cross-border overseas, etc.
1. Account management: batch management of accounts
The account management function enables users to easily import, export and create tasks in batches. Whether it is an individual user or an enterprise user, the batch operation function provided by BitFingerprint Browser will greatly improve efficiency when managing a large number of accounts.
2. Browser fingerprint: the key to privacy protection
Each browser window sets independent fingerprint information, including time zone, default language, User Agent, font, resolution, etc. Users can choose to use the fingerprint information provided by the system, or customize it according to their needs to enhance privacy protection capabilities.
3. Automated operation: improve work efficiency
BitFingerprint Browser provides automated operation functions to help users liberate manpower and improve work efficiency. Through automated operations, users can automatically perform a series of tasks, such as form filling, data crawling, etc., reducing repetitive work and allowing users to focus on more important matters.
4. Custom IP: a wider range of application scenarios
BitFingerprint Browser supports the import of custom proxy IP functions, allowing users to use various proxy IP services in the browser. This provides users with a wider range of application scenarios, such as visiting websites in specific regions, bypassing regional restrictions, etc.
5. Browser plug-in support: personalized customization function
BitBrowser Fingerprint Browser supports various browser plug-ins, such as OilMonkey, Translate, Adblock Plus, etc. Users can choose appropriate plug-ins according to their needs to achieve personalized customization functions and improve the usability and scalability of the browser.
6. Automated API interface: rich expansion functions
Bitfingerprint Browser provides an automated API script interface, which supports enterprises or individual users to call the interface for secondary script development, providing users with more convenient expansion services.
|
|
How to restore Facebook trust and unblock Facebook advertising account? |

In 2024, Facebook's ban has not been lifted, and in some areas it has even become more serious. Of course, there are some countermeasures to resolve this, thereby reducing the risk of permanent account loss. Here, we have carefully prepared a guide for you, which will explain in detail the reasons for the ban and the key and effective methods to restore your account to normal operation.
What caused the problem with your Facebook advertising account?
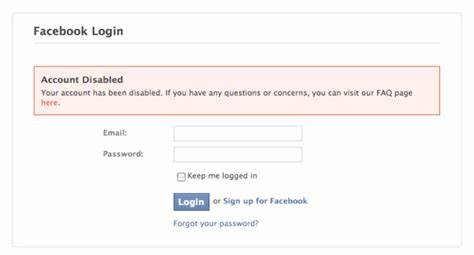
1) Non-fixed IP access:
The IP address of each login is changing, which may trigger Facebook's security alarm and misjudge it as abnormal activity, and then impose security restrictions or bans on the account. Therefore, it is recommended to adopt a stable and reliable access strategy to reduce unnecessary IP changes.
2) Improper cross-device login operation:
In the absence of appropriate account isolation measures, frequently changing computers or using the same device to log in to multiple Facebook accounts may violate its single user principle and trigger system monitoring and account blocking risks. To ensure account security, you should carefully manage cross-device logins and use professional tools such as BitBrowser to maintain the independence of fingerprint information such as cookies to avoid account association risks.
3) Violation of platform policy red line:
Facebook is extremely strict about content management. Any advertisement that touches on prohibited content will immediately face severe penalties such as account restrictions or closure. This type of blocking only affects advertisements, and the account itself will not be blocked. This is usually caused by what Facebook considers to be suspicious behavior. You can familiarize yourself with the restrictions in Facebook's official policies to avoid restrictions.
4) Illegal commercial marketing content:
Facebook strictly prohibits the use of images of celebrities and public figures in creativity, and does not allow misleading information (such as claiming that the offer can cure diseases 100%). As in the case of rule violations, the ban may target the advertising content of this account rather than the entire account. To unlock and restart the account, the illegal advertising content must be resolved and deleted.
5) Payment information inconsistency problem:
This type of blocking occurs when Facebook detects errors and suspicious activities related to bank cards or payment data. To solve this problem, you need to ensure that the GEO of the campaign matches the location of the card and verify that the balance is positive. Of course, you can also try to link other bank cards.
6) Risk of missing identity verification:
To prevent account abuse, Facebook requires users to bind their mobile phone numbers to verify their identities. Accounts that are not bound to mobile phone numbers may increase the risk of being restricted due to unknown identities. Timely completion of mobile phone number binding will help improve account security.
7) Imbalanced social interaction:
Adding a large number of friends in a short period of time may be regarded as abnormal behavior, resulting in the account being temporarily locked by the system. It is recommended that users reasonably control the speed of adding friends according to natural social habits to maintain a healthy balance of social interaction.
8) Control of content release rhythm:
If a new account is eager to post a large number of pictures and videos in the early stage, it may trigger the system review mechanism and be regarded as abnormally active. It is recommended that new accounts gradually increase the amount of content released to maintain a natural growth trend and avoid risks caused by excessive promotion.
9) Product compliance challenges:
Facebook is highly vigilant against counterfeit brands and materials with high content similarity. Its advanced detection mechanism can quickly identify potential risks. At the same time, if a newly established independent station lacks good user experience and reputation accumulation, it may also affect Facebook's trust assessment. Therefore, ensuring product originality and independent station quality is the key to improving account trust.

How to unblock a blocked Facebook account?
Method 1.
If some functions of your account are temporarily unavailable, you don't need to appeal, just wait. If it is not restored after about a week, try to unblock it again.
Method 2.
If your phone is already linked to your Facebook account, you only need to unblock it through the phone verification code (provided that you really have no serious violations)
Method 3.
Remove or change any elements that violate the rules in the campaign, delete all illegal content in the ad account you use, and there is a chance to restore the account.
Method 4.
Check your payment method and bank card, verify the accuracy of the data, correct any errors, and verify your account again. There is also a possibility of restoring the ad account.
Method 5.
You select several well-known and closely connected friends from your friends, and then send them a security code. Then, contact them to get the verification code they received from Facebook, use this verification code to unlock your account, and follow the prompts given by the system to achieve unblocking. For individual users, if you can submit relevant information seriously, the probability of successful unblocking is more than 90%.
Method 6.
Restart the campaign and wait 2-3 days, which will help if your ad account is frozen.
Method 7.
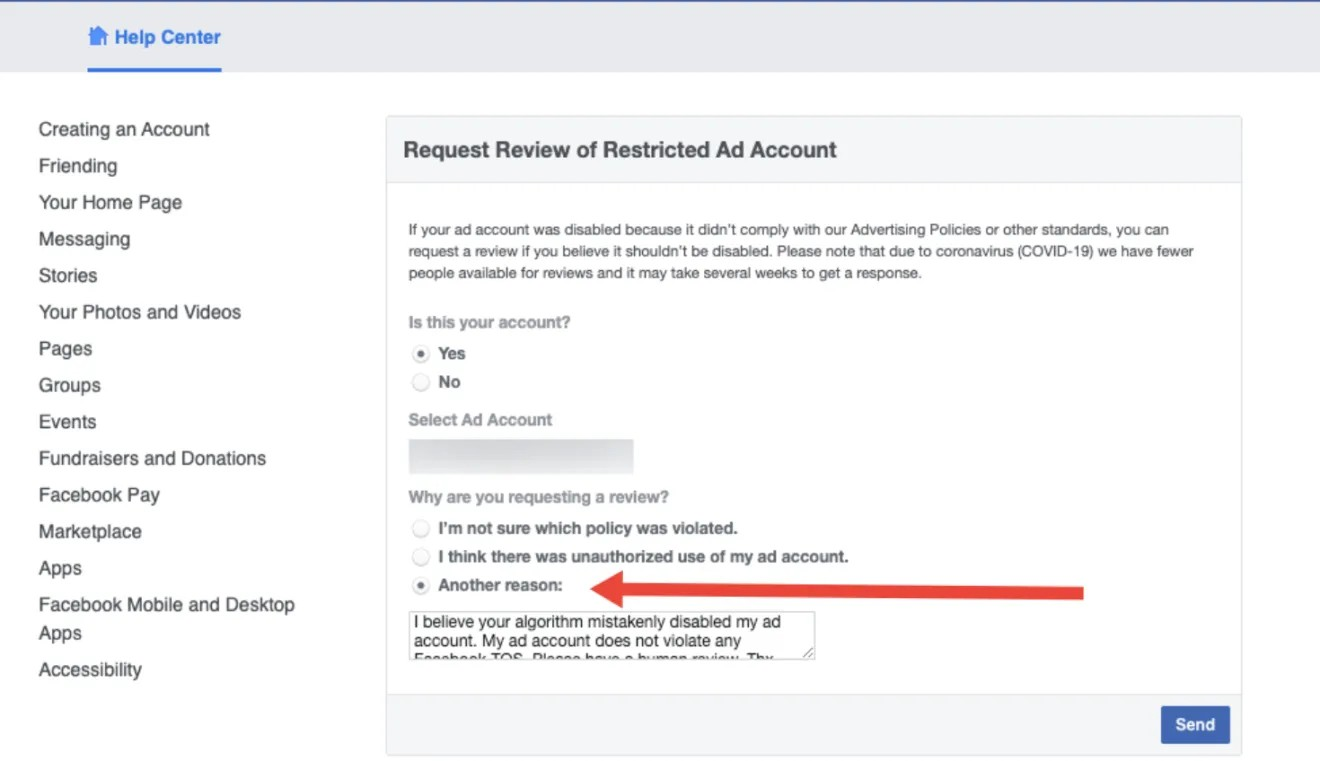
If none of the above methods can help you, and your account has no other violations, you can contact Facebook support. Sometimes, Facebook accounts may not have such a button, or the account has been completely blocked. In this case, you can write to support from another account and attach a link to the blocked profile, and upload the ID card photo of the account application in the attachment to clearly indicate that the account is indeed operated by yourself. The next step is to wait patiently for the administrator to reply and clearly explain the reason for your appeal. Once it is confirmed that the violation is locked, your account will be unblocked soon. If you don’t know how to explain to the administrator, don’t worry. There is a detailed email content writing tutorial at the end of the article to help you explain that this is a wrong ban.
In the process of using Facebook advertising accounts, it is very important to understand how to unblock the blocked accounts, but it is also essential to learn how to protect the accounts that are still in operation. It is the best solution to plan ahead and avoid problems before the accounts have problems. Follow the editor to see how to safely operate multiple Facebook accounts.
Prevent Facebook Advertising Account Blocking through BitBrowser:
In the process of multi-account marketing on social media, everyone must pay great attention to account security issues, especially to prevent Facebook accounts from being blocked. Especially for social media practitioners, they often operate multiple Faceboo accounts. However, this multi-account operation model hides huge risks and is extremely easy to trigger Facebook account blocking strategies.
In order to minimize the possibility of Facebook being blocked, BitBrowser is undoubtedly your best choice for multi-account management. Traditional browsers have obvious shortcomings when dealing with multi-account management. Because they are easy to leave browser fingerprint information, once Facebook finds that multiple accounts are logged in from the same device, it may be identified as a violation, and then restrict or even block the account.
BitBrowser Fingerprint Browser is unique. It can create a unique browsing environment for each social media account. With the help of advanced browser fingerprint technology, it can cleverly simulate different devices and network scenarios. Even if you log in to multiple accounts such as Instagram, Facebook, Amazon, etc. on the same device, the operation of each account seems to be performed on completely different computers and locations.
In addition to effectively avoiding account association, BitBrowser also has the following outstanding functions and significant advantages:
RPA Automation: This free and practical function can automatically complete repetitive operations such as following, liking and commenting, which can significantly increase the speed of Facebook's fan growth. At the same time, it can also maintain the randomness of human behavior and cleverly circumvent Facebook's automated detection mechanism.
Window Group Control: When you need to post the same content on multiple accounts or perform unified operations, the window group control function can greatly improve your work efficiency.
Guarantee account security: The global setting function of BitBrowser can be described as a "solid fortress" of multi-layer security protection, such as providing email remote login reminders, and being able to fill in the account's 2FA key when creating an environment, providing strong protection for account security.
How to explain to Facebook administrators that this was a wrongful ban?
1. Greet Facebook employees.
A polite opening statement shows that you are committed to a constructive attitude to solve the problem.
2. Describe the situation.
Next, inform the other party that your account has been blocked, clearly indicate the name or ID of the account, and express your view that the ban is unfair.
3. Provide useful information about yourself.
You can show that you are an entrepreneur or a representative of a small business that only promotes legal goods and services.
4. Prove the wrong nature of the ban.
Emphasis that you did not break any rules.
5. Provide alternatives.
Depending on the type of ban, you can point out that the mistake has been discovered and corrected. Or, you can request a review of your profile and ask why the ban was caused.
6. Don't forget to add a call to action.
At the end of the message, you should ask support to help unlock the account. You can also add that you will be extra careful in the future to avoid similar problems.
7. Express gratitude.
The letter ends on a positive note and shows a willingness to engage in constructive dialogue. You can also express your hope for a prompt response.
Some suggestions on the content of the email:
① The letter should be concise and clear.
Ideally, keep it to two or three paragraphs.
② Be polite.
Aggression, profanity, and insults are absolutely unacceptable, otherwise you may not be able to wait for the unlock.
③ Provide proof.
As evidence of the problem or that the violation has been corrected, relevant screenshots should be attached. For example, you have removed the banned elements from the creative.
④ Write a personalized message yourself instead of using a template. .
The other options in the ticket are templates, in which you need to fill in the information. However, the support team is not very enthusiastic about reviewing such templates. The "another" option allows you to write a unique letter.
⑤ Business style.
It is important to maintain a formal business communication style and abandon all emotions.
⑥ Express genuine surprise and confusion.
You can create a situation, for example, you are an honest marketer who has been promoting legitimate goods or services, but was suddenly blocked for no reason.
⑦ Communicate in English.
English-speaking support staff usually respond faster.
When sending emails to Facebook management, an important principle is to make them believe that you are a potential customer who is ready to invest a lot of money in advertising on Facebook, and Facebook has no benefit in losing you.
Summary:
I believe everyone has already understood how to unblock a blocked Facebook account. By correcting the illegal content of the blocked account and sending email feedback to Facebook management, I believe everyone's account problems can be solved. At the same time, it is also essential to avoid the blocking of Facebook accounts in advance. BitBrowser is a tool specially designed for Facebook marketers. It can not only protect the security of marketers' social media accounts, but also increase sales. Download BitBrowser now and get 10 permanent free windows immediately. Click to download BitBrowser to get a more convenient solution.
|
|
What is VPN Global Mode? How to configure and enable it? |

VPN (Virtual Private Network) global mode means that all network connections are made through VPN, thus realizing global network proxy. VPN global mode means that when the user's device is connected to the Internet, all network traffic (including browsers, applications, system services, etc.) will be routed through the VPN server, rather than just for specific applications or websites. In most cases, we also need to use VPN with fingerprint browser to ensure stable and efficient network access speed.
How VPN global mode works:
When the user enables VPN global mode, the user's device will establish an encrypted connection to the VPN server. All network requests sent from this device will first be sent to the VPN server, which will then access the target website or resource on behalf of the VPN server and return the response data to the user's device. During this process, the user's real IP address will be hidden and all transmitted data will be encrypted.
How to configure and enable VPN global mode?
Step 1: Install and configure the VPN software
After downloading and installing the selected VPN software, open the program and follow the guided steps to set it up. During this process, you may need to enter your login credentials (user name and password) to connect to the VPN server. Different VPN software may require you to select additional configurations such as server location and protocol.
Step 2: Configure global proxy
After successfully connecting to the VPN server, you need to configure the global proxy to ensure that all network traffic is transmitted through the VPN. In most VPN software, you can find the global proxy settings in the "Settings" or "Options" menu. Here, you can specify the proxy type (such as HTTP, HTTPS, SOCKS, etc.) and the proxy server address and port.
Step 3: Verify the proxy settings
After the configuration is completed, if your real IP address is hidden and the displayed IP address matches the VPN server location, it means that the proxy setting has been successful. You can also use the BitBrowser to detect it. Launch the BitBrowser window and click Network Detection. If it is green, the detection is successful.
Step 5: Confirm the effect of the global proxy
Finally, you need to confirm the effect of the global proxy settings by visiting different websites or using other applications. Make sure all network activities are conducted through the VPN to protect your privacy and security.
When we use global VPN, it is best to use BitBrowser. Some virtual private networks may have multiple people on the same line, which can easily lead to your account being associated with other people's accounts. Therefore, you need to use BitBrowser with proxy IP to separate it. Use BitBrowser to simulate the time zone, language and other browser fingerprint information corresponding to the IP. In this way, the platform detects that you are in a completely independent new device, which can avoid the association of accounts and protect the security of accounts.
In this article, we introduce how to use VPN global proxy and use BitBrowser when using VPN. As an independent fingerprint browser that is well-known at home and abroad, BitBrowser supports deep simulation of more than 30 browser fingerprints to avoid account risks when using VPN. After configuring the VPN global mode and using Bit Fingerprint Browser, you can get the best network access browsing experience.
|
|
Why do most fingerprint browsers use the Chrome kernel? |

As an e-commerce seller or social media operator, you must have used or heard of fingerprint browsers. As a multi-account social media marketing and e-commerce seller store security protection tool, fingerprint browsers play a key role in it. Most of the fingerprint browsers used may be of different brands, but have you noticed that most of these fingerprint browsers are Chrome kernels, or support two kernels, Chrome kernel and Firefox kernel, like BitFingerBrowser. What is the reason why these fingerprint browsers all choose Chrome kernel?
Why are most fingerprint browsers Chrome kernels?
This is due to a variety of reasons. One is due to the functional advantages of the Chrome kernel, and the other is the functional requirements of the fingerprint browser itself. These reasons and functions together lead to the need for fingerprint browsers to use the Chrome kernel.
1: Functional advantages of the Chrome kernel
The core of the Chrome kernel is the Blink engine, which is a browser rendering engine created by Google with great effort, derived from a branch of the Webkit engine. Its original intention was to fully improve the browser's running speed, stability and security.
The reason why the Chrome kernel is so popular is mainly due to its outstanding speed and extraordinary flexibility. The engine has been deeply optimized to quickly render web content and give users a smooth browsing experience. At the same time, it has strong compatibility and can accurately present various websites and web applications, ensuring that users can enjoy consistent and high-quality browsing effects on different platforms.
And the Chrome kernel actively accepts Web standards and HTML5 technology, providing a solid backing for the smooth operation and interaction of websites and web applications. It also fully supports JavaScript, a key core technology of modern web applications, to ensure that all kinds of dynamic web page content can be loaded and presented smoothly. With its speed, stability, security and flexibility, the Chrome kernel has become the core choice of modern web browsers, so most fingerprint browsers will give priority to the Chrome kernel when designing.
2. Functional requirements of fingerprint browsers
Everyone knows that one of the functions of fingerprint browsers is to disguise real fingerprint information, protect your browser information security, and avoid being tracked and identified by the network. Chrome browsers are used by many people, so it is easier for you to present an invisible effect in the crowd. If you are using a niche kernel browser, even if the fingerprint browser simulates a new identity information for you, you will stand out like a crane among chickens, with a very obvious identification information, which greatly increases the possibility of being identified. However, this situation can be avoided by using Chrome browsers. Browsers with Chrome kernels account for more than 50% of the world, which greatly avoids being identified due to kernel reasons. With the browser fingerprint information simulated by the fingerprint browser, it is easier to play a safe and anti-tracking effect.
The other is that many users of fingerprint browsers have the need to open multiple browsers. Bit Fingerprint Browser itself supports multiple browsers. Cookie information and browser fingerprint information are independent, and a separate IP can be added to each multiple window. Multiple information will not be associated, and account security is guaranteed. However, there are many requirements for browser extensions for multiple browsers. Now the mainstream extension resource library in the world is based on supporting Google kernel. Bit Fingerprint Browser can directly import extensions from Google Store using Google kernel, which is convenient for users to use. If there is no required extension in Google Store, Google Browser's own extensibility interface is also convenient for customizing exclusive extensions for fingerprint browser users. You only need to contact the exclusive personnel through Bit Browser script customization to customize it.
I believe that through this article you have roughly understood why fingerprint browsers need to use Chorme kernel, but some fingerprint browsers provide more than one kernel. Why is this? For example, Bit Fingerprint Browser provides two kernels, Google kernel and Firefox kernel. This situation is mostly based on customer needs. The reasons for different fingerprint browsers are slightly different. I hope this article can help you.
|
|
Which browsers can support Chrome and Firefox dual core? |
Chorme kernel and Fierfox kernel are the kernels of internationally renowned browsers Google Chrome and Firefox. Among them, Google Chrome is the most popular browser overseas for its ease of use and plasticity of supporting multiple plug-in extensions, while Firefox has higher privacy and confidentiality. These two browsers have their own advantages and are used by the vast majority of people in the global browser market.

Is there a browser that combines the advantages of the two browsers and supports both browser kernels?
Yes, BitBrowser Fingerprint Browser is such a browser. In BitBrowser Fingerprint Browser, you can experience the kernel performance of both browsers at the same time, and the extension plasticity and access security of BitBrowser Fingerprint Browser are top browser qualities. It is a relatively comprehensive browser. BitBrowser Fingerprint Browser can help you achieve the goal of batch registration of accounts in the fields of e-commerce platforms, social platforms, web crawlers, retail price comparison, security and privacy protection, and advertising alliances. Whether you are an e-commerce seller, social media marketer, web crawler developer, or anyone who needs to register accounts in batches, BitBrowser Fingerprint Browser can provide you with practical help.
What are the advantages of BitBrowser Fingerprint Browser?
Physical isolation: By simulating the hardware and software fingerprint information of a computer or mobile device, each browser file cookie, local storage and other cache files are deleted, and the browser profile is completely isolated to prevent network accounts from being associated due to the same browser fingerprint.
Rich customization functions: BitBrowser Fingerprint Browser provides a wealth of customization functions, and users can customize the browser environment according to their needs, including browser fingerprints, IP addresses, proxy settings, etc. This enables users to create a unique browsing experience based on different usage scenarios, improving the level of personalized services.
Data encryption and transmission: The highest level of data encryption technology is used to ensure that sensitive information such as user login credentials and transaction data is not stolen or tampered with during transmission
Extension support: BitBrowser Browser greatly improves the user's browsing experience and operating efficiency by integrating rich extension functions. Whether it is a cross-border e-commerce seller who needs to manage multiple store accounts at the same time, or a social media operator who needs to frequently switch between different platform accounts, BitBrowser Browser can meet these needs through its powerful extension center. Users can add the required extensions from the official extension center or Chrome App Store in just a few simple steps to achieve multiple functions such as multi-account management, advertising optimization, and data synchronization.
A browser like BitBrowser Browser that supports two kernels solves the user's difficulty in making choices. You can switch to the browser kernel you need. Compared with browsers with a single kernel, there are significant improvements in privacy protection, security and expansion flexibility. Now, using BitBrowser Fingerprint Browser will also come with 10 permanently free window experiences. Whether it is e-commerce platforms, social platforms, web crawlers, retail price comparisons, security and privacy protection, advertising alliances and other fields, you can try BitBrowser Fingerprint Browser.
|
|
What are the criteria for selecting a fingerprint browser? Recommendations for mainstream fingerprint browsers |

With the advent of browser fingerprint recognition technology, personal security and privacy are increasingly being violated. How to protect personal privacy and identity on the Internet from being violated has attracted more and more attention. Among them, fingerprint browsers are popular among e-commerce multi-store and multi-account social media operators because of their anti-association and security and privacy effects. However, with the development of various fingerprint browsers, the types, styles and functions of fingerprint browsers are becoming more and more different. Choosing a suitable one among many fingerprint browsers has become a difficult problem for many e-commerce sellers and social media operators. So what are the standards for choosing fingerprint browsers? Which fingerprint browsers are better to use?
What are the standards for choosing fingerprint browsers?
1. Security
Privacy protection: Choose a fingerprint browser that can effectively hide the user's identity and online activities, and ensure that it has the ability to bypass high-security websites and networks to check browser fingerprints. This includes using advanced anti-fingerprint technology to confuse or change the browser's fingerprint information, such as IP address, operating system characteristics, browser settings and version, to protect the user's privacy and security.
Data encryption: The browser should use strong encryption technology to protect the user's data transmission and storage security and prevent data leakage and theft.
Anti-crawler technology: It has powerful anti-crawler technology to deal with malicious crawler attacks and protect user data and website security.
2. Compatibility
Operating system support: The fingerprint browser should be able to support multiple operating systems, such as Windows, Mac, Linux, etc., to meet the needs of different users.
Device compatibility: Ensure stable operation on different types of devices, such as desktops, laptops, tablets, etc.
Web application integration: The fingerprint browser should be able to seamlessly integrate with various web applications, providing flexibility and versatility in use.
3. Ease of use
Friendly interface: The interface design of the fingerprint browser should be intuitive, concise, and easy for users to understand and operate.
Function operation: Provide clear navigation and intuitive controls, allowing users to easily configure IP addresses, fingerprint obfuscation, multi-opening functions, etc.
Extra functions: If the fingerprint browser can provide some additional functions, such as multi-account management, scheduled tasks, team collaboration, etc., it will further enhance the user experience.
Recommended mainstream fingerprint browsers:
Bitbrowser:
A browser that enhances privacy protection, by simulating different browser fingerprints, effectively preventing users from being tracked online. It supports independent management of multiple accounts and is suitable for e-commerce, social media marketing, SEO optimization and other fields. It provides a variety of package options to meet different needs. Its anti-association technology ensures account security, and the RPA automation function improves work efficiency. Bit Fingerprint Browser is a powerful assistant for protecting privacy and improving network security.
BitBrowser's pricing strategy is flexible and diverse to meet the needs of different user groups. Specifically, its pricing plans include:
Permanent free version: provides a basic configuration of 10 environments, suitable for individuals or small-scale users to conduct initial trials and experiences.
Paid version: Depending on the number of windows and employees required by the user, the price ranges from 50 yuan/month to higher. For example, the package price for 50 windows and 2 employees is 50 yuan/month; the package price for 100 windows and 4 employees is 75 yuan/month; the package price for 200 windows and 8 employees is 125 yuan/month. For users who need more configurations, Bit Browser also provides higher-level packages that can support up to 300,000+ windows. Please contact the Bit Browser team for specific prices.
Adspower:
Cross-border e-commerce and marketing tool, providing multi-account security management and browser fingerprint configuration. Support RPA automation to improve efficiency; team collaboration function to promote team collaboration.
Adspower prices vary according to different versions and functions, mainly including free version, basic version, professional version and customized version.
Free version: provides limited functional experience, suitable for individual users to try initially, without paying any fees.
Basic version (Base version): provides basic configuration environment and management functions, suitable for small-scale use. The monthly fee is about US$9/month (about RMB 54/month), and the annual fee is more favorable, about US$76/year (about RMB 456/year), which is only about RMB 38 per month.
Professional version (Pro version): provides richer configuration environment and management functions, suitable for large-scale use. The monthly fee is about 20 US dollars/month (about 250 RMB/month), and the annual fee is about 420 US dollars/year (about 2520 RMB/year), which is only about 210 RMB per month.
Customized version: customized according to the actual needs of users, providing personalized function configuration, the price needs to be negotiated according to specific needs.
Morelogin:
Morelogin is a powerful anti-detection browser designed for users who need to manage multiple user configurations and maintain anonymity.
The price of Morelogin varies according to user needs and the selected package. Generally speaking, its price is more flexible and provides a variety of options to meet the needs of different users. Specifically, Morelogin provides packages such as basic version and professional version. The basic version is usually cheaper and suitable for individual users or small teams; while the professional version provides more advanced functions and configuration options, suitable for enterprise-level users who need to manage a large number of accounts. For specific price information, users are advised to visit the Morelogin official website directly or contact its customer service department to obtain the most accurate price information.
|
|
What is the use of browser data capture? How to use fingerprint browser data capture? |

Web scraping is a key technology in the field of Internet data collection. It has been emerging since the birth of the World Wide Web, but it has only attracted widespread public attention in recent years, fully demonstrating its extraordinary value. In short, web scraping is an automated process whose goal is to systematically collect data from public resources on the Internet. The effectiveness of this process depends on three core criteria: whether the data exists, whether it is accessible online, and whether it is public.
1. How Web Scraping Works
The essence of web scraping can be regarded as a highly intelligent "copy and paste" action, but its efficiency, scalability and cost-effectiveness far exceed traditional methods. During operation, an automated script will traverse a series of URLs in sequence, download the web page content one by one, and temporarily store it in the local system. Then, the script will use search algorithms to filter out the required information from the collected data, and finally organize the information and output it to a specific file or database.
Although there are differences in different implementation methods, the core concept of web scraping remains consistent. Some methods focus on fine-grained management of URL lists, in-depth browsing of multiple pages, and complete preservation of HTML code; while others prefer to parse HTML directly during data crawling to reduce memory usage. Regardless of which method is used, web crawlers are like tireless explorers, searching for valuable information in the vast ocean of the Internet.
It is worth noting that web crawlers are essentially no different from ordinary Internet users when browsing websites, and some crawlers even load pages through browsers. However, in order to improve efficiency and save computing resources, most modern crawlers choose to send HTTP requests directly to websites, receive and process response content, without rendering any content on the screen.
2. Difficulties and solutions for web crawling
A major challenge facing web crawling is the complexity and variability of the HTML format. HTML was originally designed to display content in browsers, not to facilitate data analysis. Therefore, the data collected by crawlers often contains a lot of redundant and useless information. To solve this problem, parser tools came into being. Parsers can convert unstructured HTML data into a structured format, making it easier for humans or software to understand and process.
To further protect the identity of the crawler from being revealed, BitBrowser provides the function of masking IP addresses. It uses proxy servers and VPNs to rotate IPs, ensuring that different IP addresses are used each time the crawler is crawled, thereby increasing anonymity and security. BitBrowser can make it impossible for websites to accurately read the fingerprint information of the crawler, further enhancing the anti-detection effect.
3. Application scenarios of web crawling
The application fields of web crawling are extremely wide, covering almost all fields that need to be data-driven. The following are several representative application scenarios:
1. Dynamic pricing: E-commerce giants and travel ticketing platforms use web crawlers to continuously monitor the product prices of competitors, thereby implementing dynamic pricing strategies. By adjusting prices in real time, these companies can gain an advantage in the fierce market competition.
2. Professional data collection: Social media platforms are an important source of corporate information. By crawling data on social media, companies can conduct potential customer analysis, employee turnover monitoring, and competitor product performance evaluation.
3. Alternative data collection: With the advent of the big data era, alternative data has gradually become an important basis for corporate decision-making. Web crawling technology enables companies to quickly collect data from multiple sources, providing strong support for investment decisions, market forecasts, etc.
4. Geographically sensitive data acquisition: For companies that need to obtain data in specific regions, residential IP proxies have become an indispensable tool. By simulating the network environment of real users, companies can bypass geographical restrictions and obtain more accurate and comprehensive data.
Summary:
As an efficient and flexible way of data collection, web crawling is gradually changing the operating model and decision-making method of companies. With the continuous advancement of technology and the continuous expansion of application scenarios, the future of web scraping will surely be brighter and more glorious.
|
|
Essential software for affiliate marketing, BitBrowser |

Roaming freely with advertisers in the vast world of the Internet, accurately targeting the target audience. However, with the rapid evolution of technology and the continuous strengthening of supervision, the operation of advertising alliance marketing faces unprecedented severe challenges, especially in multi-account management and strict compliance with platform rules.
Multi-platform multi-account management
The brilliant achievements of advertising alliance marketing are often due to the carefully planned multi-platform and multi-account layout strategy. The core goal of this strategy is to maximize the advertising effect by dispersing risks and optimizing resource allocation. However, in the complex network ecological environment, how to ensure the independence and concealment of accounts and cleverly avoid the platform's security monitoring mechanism has become a difficult problem that marketers need to overcome.
Fingerprint browser debuts
Against this background, fingerprint browsers came out and quickly became a capable general in advertising alliance marketing. This type of browser carefully simulates multiple completely independent browsing environments, covering each account with a mysterious "invisible coat", successfully concealing the user's true identity and operation trajectory. They can not only effectively isolate sensitive information such as Cookies, caches, and browsing history, but also greatly reduce the risk of association between accounts with unique browser fingerprint technology, effectively ensuring the stability and security of multi-account operations.
Comprehensive strategy upgrade
Carefully select anti-detection tools: Professional fingerprint browsers such as BitBrowser, with their powerful isolation technology and flexible and diverse configuration options, build a solid fortress for advertising alliance marketing.
Personalized environment customization: Tailor a unique browser environment and configuration file for each advertising account to ensure that they are independent and do not interfere with each other in the digital world.
Clever use of proxy IP: Assign a dedicated proxy IP address to each account, realistically simulate the geographic location and behavior patterns of real users, and significantly improve the authenticity and credibility of the account.
Dynamic adjustment and real-time update: Closely follow the trend of technological development, regularly update browser settings and anti-detection strategies, and calmly respond to continuously upgraded monitoring methods.
Fine advertising delivery planning: Reasonably arrange the time nodes and frequency of advertising delivery to avoid risk exposure caused by excessive concentration, and carefully optimize advertising content to fully improve conversion rate.
Strengthen data security protection: On the basis of effectively isolating browsing data, further strengthen data encryption and access control to ensure that user information and marketing data are foolproof.
Summary:
BitBrowser, as a leader in the industry, has injected a steady stream of new vitality into advertising alliance marketing with its outstanding multi-account management level, flexible and convenient automated operation functions and indestructible security protection strength. Whether you are a master of global social media marketing or an elite leader in the field of cross-border e-commerce, BitBrowser can be your most reliable partner, leading you to steadily move forward on the road of compliance and efficiency. Download now to experience it for yourself and open a new chapter of your advertising alliance marketing!
|
|
Using BitBrowser to Automatically Login to Web Pages with Cookies |

In the digital age, Cookie is like a shining pearl in the Internet ecology, and its importance cannot be underestimated. As a small text file generated by the website and stored on the user's device, Cookie shoulders the important mission of carrying the user's browsing history and personalized settings, enabling the website to intelligently identify and remember the user's login status and preferences. This article will deeply analyze how to cleverly use Cookie technology in the environment of advanced fingerprint browsers to create a seamless and secure automatic login experience.
1. The core role and mechanism of Cookie
Cookie is like a solid bridge for information exchange between websites and browsers. When a user logs in to a website for the first time and successfully verifies his identity, the server will generate a unique session ID and send it to the browser for storage with the help of the Set-Cookie instruction in the HTTP response. From then on, every time the browser sends a request to the website, it will automatically carry this cookie. The server confirms the user's login status by verifying the session ID in the cookie, and then provides users with a personalized service experience.
2. The application of Cookie in automatic login
1. Simplified login process: After the user completes the first login and successfully verifies, the server will encapsulate the login credentials (such as session ID) in the cookie and send it to the browser. After that, as long as the cookie is still valid, the user will be able to log in automatically when visiting the website again, without having to repeatedly enter the username and password.
2. Advantages of fingerprint browsers: For users who need to manage multiple platforms and accounts, traditional browsers may increase the risk of account association due to cookie sharing. Fingerprint browsers (such as BitBrowser) create independent browser environments for each account to ensure that data such as cookies, caches, and plug-ins are isolated from each other, effectively preventing cross-account data leakage.
3. Automatic login in BitBrowser
BitBrowser provides users with an excellent solution for efficient management of multiple accounts with its powerful isolation technology and convenient operation interface. When creating a new browser window, users only need to select the corresponding platform and enter the account information (if there is a cookie field, enter it as well). Once the settings are completed, the next time the window is opened, the system will automatically load the saved cookies to achieve one-click login, greatly improving work efficiency and user experience.
4. Security and privacy protection
BitBrowser not only pays great attention to user experience, but also puts the security and privacy of user accounts in a crucial position. Through advanced anti-detection technology and personalized privacy settings, it effectively prevents websites from tracking user behavior through cookies and reduces the risk of account bans. At the same time, it also provides comprehensive technical support and rich resource channels to help users' business develop steadily.
Summary:
For users who pursue efficient and secure multi-account management experience, BitBrowser is undoubtedly an ideal choice. It brings unprecedented convenience and security to users with its unique cookie processing mechanism and powerful privacy protection function. Download and experience it now, and start a new chapter of your multi-platform multi-account management!
|
|
How to protect your multiple social media accounts in a safe environment with Multi-Account Explorer |

With the development of Internet social networking, more and more companies are increasing their visibility through social media marketing. Most social media marketers will quickly open up the market by opening multiple social media accounts to obtain traffic for the company, but using multiple social media accounts will undoubtedly increase the risk. When using multiple accounts on Facebook, X, Instagram and other social media, your browser fingerprint will be detected. If multiple accounts are found to be under the same browser information, they will be associated, and there will be a risk of being blocked.
How to prevent association and use multiple social media accounts?
You can use a multi-account browser, such as BitBrowser. Unlike most browsers on the market, Multi-account Browser can provide a secure browser fingerprint environment for each user's account. BitBrowser completely simulates the real machine system through independent user agents (including browser type, version and operating system information), screen resolution, browser plug-in information, time zone settings, font list and language settings, etc., to create a dedicated browser environment for each account to prevent association and account blocking.
BitBrowser also supports browser automation and group control functions, providing a convenient solution for social media marketers:
BitBrowser's group control function allows users to synchronize all mouse and keyboard events to multiple controlled windows through a master browser window, achieving multiple goals at one stroke. This function can greatly improve the operating efficiency of multiple windows, especially for users who need to handle multiple tasks and accounts at the same time, which can significantly save time and human resources.
BitDoden Account Browser's automation function helps users achieve a series of repetitive browser operations, such as automatic login, form filling, button clicking, etc., through built-in automation scripts or third-party tools. This function can significantly reduce manual operations and improve work efficiency.
Summary:
In summary, BitBrowser provides a convenient and secure solution for social media marketers. By using BitBrowser, multiple accounts of social media marketers are not related to each other, ensuring the normal marketing use of accounts.
|
|
Reasons for Tinder social platform bans, and how to prevent and unblock accounts |

Tinder is a dating app with extremely high popularity worldwide. It helps people build romantic emotional bonds with advanced technology. It was born in 2012 and attracts attention with its simple style and innovative design. Sean Rad, Jonathan Badeen and Justin Mateen are the founders of Tinder.
Why has Tinder achieved such remarkable success?
This is mainly due to its excellent strategic marketing, localization strategy and continuous improvement. In the dating app market, various niches are emerging one after another, and Tinder is able to stand out as a versatile platform. It provides users with a rich variety of dating options and experiences while keeping the process simple and pleasant. For many independent website owners and cross-border marketers, Tinder has become an indispensable and important tool in promotion work. However, novices who are new to the world of Tinder often fall into the trouble of "instant ban", which makes people feel lost. To help you get out of this dilemma, here is a detailed Tinder anti-association guide to help you get started smoothly!

What caused your Tinder account to be blocked?
Like other social giants, Tinder strictly controls the ecological environment of the community, and any violations will be severely punished. Coupled with the particularity of the mainland network environment, Tinder's association detection mechanism is extremely strict, and its degree is no less than Tinder. Common account minefields mainly cover:
Violation of terms and agreements or community guidelines: If a user violates the terms and agreements or community guidelines, his account will be automatically blocked by the server. Sometimes, blocked users cannot restore their accounts because they have been permanently banned from using the application. In order to avoid trouble during use, you'd better read the relevant guidelines of the application carefully.
Similar registration information: If personal information is repeated or shared with others, the system will identify it as impersonation and ban it mercilessly.
Improper use of chat language: During the chat process, if a user uses inappropriate language, such as swear words, racist comments, and homophobic remarks, other end users can report it. Tinder is committed to creating a safe and healthy environment for everyone looking for a match.
Device fingerprint overlap: Tinder strictly investigates the situation of multiple accounts on one device, and its device identification technology is designed to ensure the independence of each account. If your device has logged into other accounts before, it is very likely to trigger an association warning, resulting in the account being blocked.
IP address abnormality: It is absolutely not allowed to have one IP corresponding to multiple accounts, and frequent changes or sharing of IPs are also very dangerous. The platform will regard such behavior as an abuse of resources and impose penalties.
How to unblock a blocked Tinder account? The latest solution.
Tinder's official policy clearly states that blocking an account is usually the final decision, but this is not without room for maneuver. It has to be said that Tinder is quite firm in its attitude towards blocking accounts. The official statement of their blocking decision is irrevocable, but as long as you file an appeal, there is still a slight possibility of unblocking. If you get a message saying you've violated the Terms of Use when you're logging into the app or website, that means your account has been blocked.
If you subscribed to Tinder Gold or Tinder Plus and subscribed through your Apple ID or Google Play Store account, cancel your subscription here to prevent further charges.
If you signed up for Tinder Gold or Tinder Plus using the credit card option or on the Tinder website, your subscription will be automatically canceled.
Can I appeal a ban on Tinder?
Yes, it's the only official way to get unblocked.
Yes, it's the only official way to get unblocked. Although Tinder claims that they don't offer appeals for bans, you can actually submit a request here. Select "Account login issues," then "Can't log in, my account is blocked." Enter your information and explain why you think you should not have been blocked. After that, they may be able to unblock your account.
For example, if it's because of a misunderstanding by other users, you can try to explain: "I know that a matched user is unhappy with me, but I think it's a misunderstanding. Can you check and help me get my account unblocked?"
If you don't know why you were blocked, ask the other party to review your account. You can say: "I don't think I violated any rules. This must be a mistake. Can you check my activities and find out what the problem is?"
Finally, end your description with honest and concise words, don't do it too much. If you are lucky enough and meet a kind reviewer, they may help you get your account unblocked.
How to prevent Tinder account blocking? 2024 version
Personalize registration information: Make sure each account has a unique name (use English name), age, location and photo. When registering a new account, never use old photos or similar information, and once the registration is completed, never change it easily.
Optimize the network environment: In order to prevent the association between accounts, you need to carefully plan the network environment. Use BitBrowser and proxy IP to create an independent virtual environment for each account, effectively avoiding the risk of device blocking. At the same time, remember to clean the browser cache regularly to keep the network environment pure.
Smart matching strategy: When a new account logs in for the first time, you should wait for half an hour to stabilize the system. When matching, do not be too eager, control the rhythm, and avoid frequent operations to attract attention. In addition, follow the habits of real users and add friends and groups moderately.
Content security specifications: Strictly abide by the rules of the platform and stay away from sensitive words and topics. When communicating with customers, guide the other party to provide contact information to reduce your own exposure risk.
Reasons for the ban of Tinder social platform, and how to prevent bans and unbans
BitBrowser Your Protection of Multiple Tinder Accounts
In daily social and professional activities, managing multiple Tinder accounts has become a necessary task for many people, but this work is often accompanied by considerable challenges, especially how to ensure the independence of accounts, prevent mutual associations, and avoid the risk of account bans.
Given the complexity and potential risks of multi-account management, it is particularly important to seek a management strategy that is both efficient and secure. At this time, fingerprint browsers become an ideal solution. Such tools use advanced technology to simulate different browser environments and device features, and tailor independent browser profiles for each account, so that the login activities of each account seem to occur in completely independent physical devices and network environments.
BitBrowser optimizes multi-account management
As an advanced fingerprint browser designed for multi-account management, BitBrowser greatly simplifies the anti-association management process of Tinder accounts, allowing users to easily manage multiple accounts without worrying about risks.
Account isolation technology: BitBrowser generates unique browser profiles, simulates different operating systems, browser versions and cookie records, etc., to create a completely isolated login environment for each Tinder account, effectively preventing mutual interference and association between accounts.
Window synchronization function: In order to improve operational efficiency, BitBrowser also provides a window synchronization feature, allowing users to synchronize operations between different browser windows, such as batch editing content or executing unified instructions, which greatly saves time and energy.
Automated workflow: With the help of RPA (Robotic Process Automation) technology, BitBrowser can automatically perform a series of tedious account management tasks, including but not limited to automatic login, content publishing, interaction (likes, comments), etc., greatly reducing the user's workload.
By adopting BitBrowser, users can not only achieve efficient and secure management of Tinder multiple accounts, but also significantly improve work efficiency while protecting account security. Both individual and corporate users can benefit greatly from it and enjoy a smoother and worry-free social media management experience.
Summary:
Mastering the above anti-blocking and unblocking tips, you have taken the first step towards success. But please remember that the security journey begins with registration and continues in daily use. Always maintain a high degree of vigilance and carefully maintain the security of your account, so that you can bravely move forward in this vast blue ocean of social networking and reap a lot of rewards. Once an account encounters an accident, it will not only lose customer resources, but it is also likely to have an adverse impact on your brand image and long-term development. By adopting BitBrowser, users can not only achieve efficient and secure management of Tinder multiple accounts, but also significantly improve work efficiency while protecting account security. Both individual and corporate users can benefit greatly from it and enjoy a smoother and worry-free social media management experience.
|
|






