Ќастройка двухфакторной аутентификации в домене Astra Linux Directory |
Ќастройка двухфакторной аутентификации в домене Astra Linux Directory
¬ этом посте мы решили рассказать о доменной аутентификации в Linux, с использованием смарт-карт и USB-токенов JaCarta PKI в качестве второго фактора аутентификации. ≈сли о локальной аутентификации через PAM-модуль информации существует довольно много, то вопрос доменной инфраструктуры и аутентификаци€ по Kerberos-билетам в Linux рассмотрен слабо, особенно на русском €зыке. ¬ качестве операционной системы возьмем Astra Linux и на примере Astra Linux Directory (ALD) это и покажем.
¬ыгода такого решени€ очевидна Ц оно позвол€ет отказатьс€ от парольной аутентификации пользовател€, что поможет кардинально снизить вли€ние Ђчеловеческого фактораї на безопасность системы. ѕлюс это даст р€д преимуществ от использовани€ электронных ключей внутри операционной системы, после аутентификации в домене.
ƒомен Astra Linux Directory (ALD) предназначен дл€ организации единого пространства пользователей (домена локальной вычислительной сети) в автоматизированных системах.
ALD использует технологии LDAP, Kerberos5, Samba/CIFS и обеспечивает:
JaCarta PKI Ч это линейка PKI-токенов дл€ строгой аутентификации пользователей в корпоративных системах, безопасного хранени€ ключевых контейнеров программных — «» и цифровых сертификатов российского производител€ Ц компании Ђјладдин –.ƒ.ї.

¬ среде Astra Linux Directory (ALD) электронные ключи JaCarta PKI могут использоватьс€ дл€ двухфакторной аутентификации пользовател€ в домене ALD и отказа от паролей. роме того, с этими же электронными ключами можно выполн€ть различные сценарии внутри ќ—, после аутентификации, такие, как: электронна€ подпись, хранение ключевых контейнеров, доступ к Web-ресурсам, проброс ключа в сессии MS Windows. ƒоступ к VDI сервисам, таким, как VmWare или Citrix.
ѕредполагаетс€, что ALD уже развернут, существует минимум один доменный пользователь, который может аутентифицироватьс€ по паролю, врем€ клиента и сервера совпадают.
ƒл€ обеспечени€ работы со смарт-картой JaCarta PKI на клиенте и сервере установите следующие пакеты: libccid, pcscd, libpcsclite1. ѕосле установки этих об€зательных пакетов установите пакет драйверов IDProtectClient, который можно загрузить с официального сайта Ђјладдин –.ƒ.ї.
ƒл€ обеспечени€ работы со смарт-картой подсистемы Kerberos добавочно к предустановленным пакетам ald/kerberos установите пакет krb5-pkinit на клиенте и сервере.
ƒл€ обеспечени€ возможности выпуска ключей и сертификатов на JaCarta PKI на сервере также установите пакеты libengine-pkcs11-openssl и opensc.
¬ качестве центра сертификации (CA) будет использован OpenSSL.
OpenSSL Ч криптографический пакет с открытым исходным кодом дл€ работы с SSL/TLS. ѕозвол€ет создавать ключи RSA, DH, DSA и сертификаты X.509, подписывать их, формировать CSR и CRT.
¬се настройки в руководстве выполн€ютс€ дл€ тестового домена EXAMPLE.RU. ѕримем, что сервер и клиент принадлежат домену EXAMPLE.RU, им€ сервера Ц kdc, а клиента Ц client. ѕри настройке используйте им€ вашего домена, сервера и клиента. ¬ыполните следующие действи€.
—одержимое файла pkinit_extensions (его следует положить в тот каталог, откуда вы выполн€ете команды):
”бедитесь в том, что установлены пакеты libengine-pkcs11-openssl и opensc. ѕодключите устройство, которое следует подготовить.
ѕроинициализируйте устройство, установите PIN-код пользовател€. ѕомните, что инициализаци€ устройства удалит все данные на JaCarta PKI без возможности восстановлени€.
ƒл€ инициализации необходимо воспользоватьс€ утилитой pkcs11-tool.
pkcs11-tool --slot 0 --init-token --so-pin 00000000 --label 'JaCarta PKI' --module /lib64/libASEP11.so,
где:
--slot 0 Ч указывает, в какой виртуальный слот подключено устройство. ак правило, это слот 0, но могут быть и другие значени€ Ц 1,2 и т.д.;
--init-token Ц команда инициализации токена;
--so-pin 00000000 Ц PIN-код администратора JaCarta PKI. ѕо умолчанию имеет значение 00000000;
--label 'JaCarta PKI' Ц метка устройства;
--module /lib64/libASEP11.so Ч указывает путь до библиотеки libASEP11.so. ”станавливаетс€ в рамках пакета idprotectclient см. раздел Ђ”становка драйверов на сервер и клиентї.
ƒл€ задани€ PIN-кода пользовател€ используйте команду:
pkcs11-tool --slot 0 --init-pin --so-pin 00000000 --login --pin 11111111 --module /lib64/libASEP11.so,
где:
--slot 0 Ч указывает, в какой виртуальный слот подключено устройство. ак правило, это слот 0, но могут быть и другие значени€ Ц 1,2 и т.д.;
--init-pin Ц команда установки PIN-кода пользовател€;
--so-pin 00000000 Ц PIN-код администратора JaCarta PKI. ѕо умолчанию имеет значение 00000000;
--login Ц команда логина;
--pin 11111111 Ц задаваемый PIN-код пользовател€;
--module /lib64/libASEP11.so Ч указывает путь до библиотеки libASEP11.so. ”станавливаетс€ в рамках пакета idprotectclient см. раздел Ђ”становка драйверов на сервер и клиентї.
—генерируйте ключи на устройстве, дл€ этого введите следующую команду:
pkcs11-tool --slot 0 --login --pin 11111111 --keypairgen --key-type rsa:2048 --id 42 --label Уtest1 keyФ --module /lib64/libASEP11.so,
где:
--slot 0 Ч указывает, в какой виртуальный слот подключено устройство. ак правило, это слот 0, но могут быть и другие значени€ Ц 1,2 и т.д.;
--login --pin 11111111 Ч указывает, что следует произвести логин под пользователем с PIN-кодом Ђ11111111ї. ≈сли у ¬ашей карты другой PIN-код пользовател€, укажите его;
--keypairgen --key-type rsa:2048 Ч указывает, что должны быть сгенерированы ключи длиной 2048 бит;
--id 42 Ч устанавливает атрибут CKA_ID ключа. CKA_ID может быть любым;
«апомните это значение! ќно необходимо дл€ дальнейших шагов подготовки устройства к работе.
--label Уtest1 keyФ Ч устанавливает атрибут CKA_LABEL ключа. јтрибут может быть любым;
--module /lib64/libASEP11.so Ч указывает путь до библиотеки libASEP11.so. ”станавливаетс€ в рамках пакета idprotectclient см. раздел Ђ”становка драйверов на сервер и клиентї.
—генерируйте запрос на сертификат с помощью утилиты openssl. ƒл€ этого введите следующие команды:
ќбратите внимание на -new -key 0:42, где 0 Ч номер виртуального слота с устройством, 42 Ч атрибут CKA_ID сгенерированных раннее ключей.
»нформацию, которую необходимо указать в запросе, следует задавать в поле "/C=RU/ST=Moscow/L=Moscow/O=Aladdin/OU=dev/CN=test1 (! ¬аш_ѕользователь!)/emailAddress=test1@mail.com".
Ќеобходимо установить переменные окружени€
$ export REALM=EXAMPLE.RU #¬аш домен
$ export CLIENT=test1 #¬аш пользователь
и выпустить сертификат на пользовател€.
$ openssl x509 -CAkey cakey.pem -CA cacert.pem -req -in client.req -extensions client_cert -extfile pkinit_extensions -out client.pem Цdays 365
ƒалее перекодируйте полученный сертификат из PEM в DER.
# openssl x509 -in client.pem -out client.cer -inform PEM -outform DER
«апишите полученный сертификат на токен.
pkcs11-tool --slot 0 --login --pin 11111111 --write-object client.cer --type 'cert' --label 'Certificate' --id 42 --module /lib/libASEP11.so,
где:
--slot 0 Ч указывает, в какой виртуальный слот подключено устройство. ак правило, это слот 0, но могут быть и другие значени€ Ц 1,2 и т.д.;
--login --pin 11111111 Ч указывает, что следует произвести логин под пользователем с PIN-кодом Ђ11111111ї. ≈сли у ¬ашей карты другой PIN-код пользовател€, укажите его;
--write-object ./client.cer Ч указывает, что необходимо записать объект и путь до него;
--type 'cert' Ч указывает, что тип записываемого объекта Ц сертификат;
'cert' --label 'Certificate' Ч устанавливает атрибут CKA_LABEL сертификата. јтрибут может быть любым;
--id 42 Ч устанавливает атрибут CKA_ID сертификата. ƒолжен быть указан тот же CKA_ID, что и дл€ ключей;
--module /lib64/libASEP11.so Ч указывает путь до библиотеки libASEP11.so.
—оздайте на клиенте каталог /etc/krb5/. —копируйте в /etc/krb5/ сертификат CA (cacert.pem) c сервера.
Ќастройте kerberos в /etc/krb5.conf. —екцию [libdefaults] дополните следующими строками.
¬ыполните проверку:
kinit огда по€витс€ строка запроса PIN-кода к карте, введите его.
ƒл€ проверки того, что kerberos-тикет был успешно получен дл€ пользовател€, введите команду klist. ƒл€ удалени€ тикета Ч kdestroy.
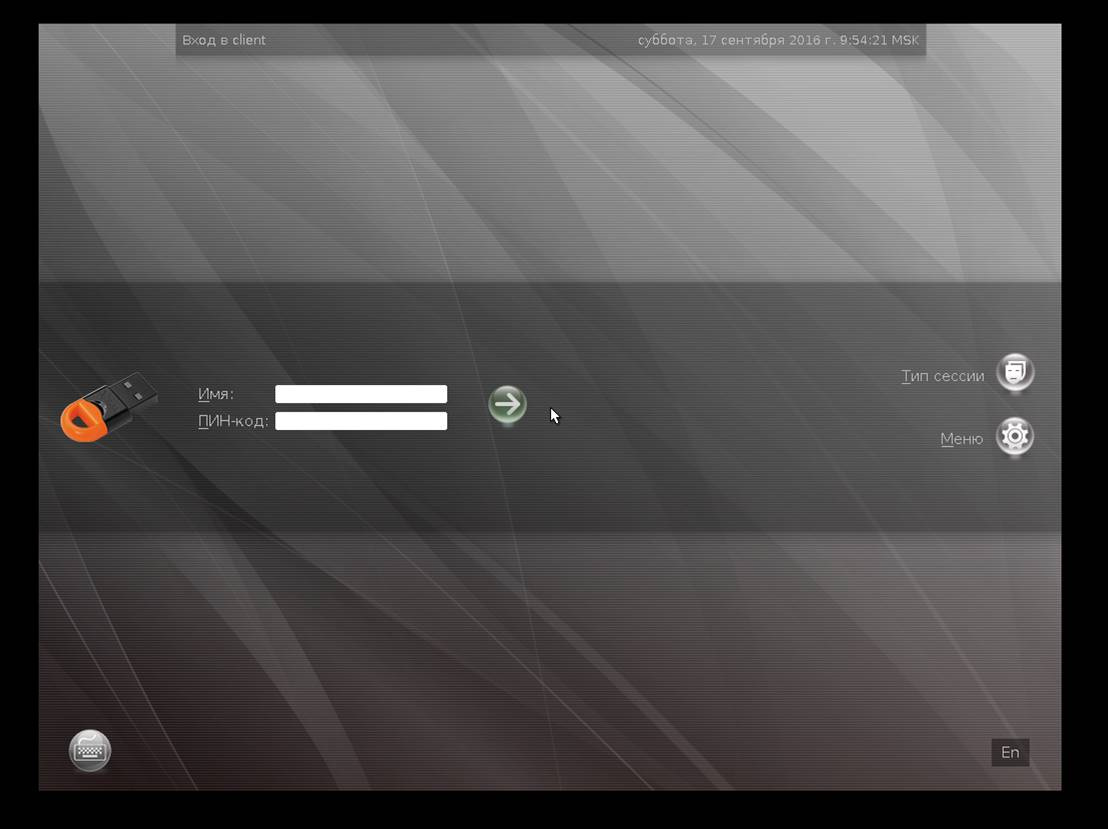
ƒл€ входа в домен по смарт-карте на экране входа в ќ— вместо парол€ введите PIN-код от смарт-карты.
Ќа этом настройка окончена. ƒа, к сожалению, система сама не помен€ет и не подстроит login окно под смарт-карту, и оно будет стандартным, но если приложить немного секретных усилий, можно добитьс€ красивого результата.
¬ыгода такого решени€ очевидна Ц оно позвол€ет отказатьс€ от парольной аутентификации пользовател€, что поможет кардинально снизить вли€ние Ђчеловеческого фактораї на безопасность системы. ѕлюс это даст р€д преимуществ от использовани€ электронных ключей внутри операционной системы, после аутентификации в домене.
Ќемного вводных об Astra Linux Directory (ALD) и JaCarta PKI
ƒомен Astra Linux Directory (ALD) предназначен дл€ организации единого пространства пользователей (домена локальной вычислительной сети) в автоматизированных системах.
ALD использует технологии LDAP, Kerberos5, Samba/CIFS и обеспечивает:
- централизованное хранение и управление учетными запис€ми пользователей и групп;
- сквозную аутентификацию пользователей в домене с использованием протокола Kerberos5;
- функционирование глобального хранилища домашних директорий, доступных по Samba/CIFS;
- автоматическую настройку файлов конфигурации UNIX, LDAP, Kerberos, Samba, PAM;
- поддержку соответстви€ Ѕƒ LDAP и Kerberos;
- создание резервных копий Ѕƒ LDAP и Kerberos с возможностью восстановлени€;
- интеграцию в домен вход€щих в дистрибутив —”Ѕƒ, серверов электронной почты, Web-серверов, серверов печати и другие возможности.
JaCarta PKI Ч это линейка PKI-токенов дл€ строгой аутентификации пользователей в корпоративных системах, безопасного хранени€ ключевых контейнеров программных — «» и цифровых сертификатов российского производител€ Ц компании Ђјладдин –.ƒ.ї.

¬ среде Astra Linux Directory (ALD) электронные ключи JaCarta PKI могут использоватьс€ дл€ двухфакторной аутентификации пользовател€ в домене ALD и отказа от паролей. роме того, с этими же электронными ключами можно выполн€ть различные сценарии внутри ќ—, после аутентификации, такие, как: электронна€ подпись, хранение ключевых контейнеров, доступ к Web-ресурсам, проброс ключа в сессии MS Windows. ƒоступ к VDI сервисам, таким, как VmWare или Citrix.
ѕроцесс настройки
ѕример демо-зоны
- —ервер Ч Astra Linux Smolensk SE 1.5 4.2.0-23-generic, x86_64, с установленными пакетами:
- JaCarta IDProtect 6.37;
- libccid;
- pcscd;
- libpcsclite1;
- krb5-pkinit;
- libengine-pkcs11-openssl;
- opensc.
- JaCarta IDProtect 6.37;
- лиент Ч Astra Linux Smolensk SE 1.5 4.2.0-23-generic, x86_64, с установленными пакетами:
- JaCarta IDProtect 6.37;
- libccid;
- pcscd;
- libpcsclite1;
- krb5-pkinit.
- JaCarta IDProtect 6.37;
ѕредполагаетс€, что ALD уже развернут, существует минимум один доменный пользователь, который может аутентифицироватьс€ по паролю, врем€ клиента и сервера совпадают.
”становка драйверов на сервер и клиент
ƒл€ обеспечени€ работы со смарт-картой JaCarta PKI на клиенте и сервере установите следующие пакеты: libccid, pcscd, libpcsclite1. ѕосле установки этих об€зательных пакетов установите пакет драйверов IDProtectClient, который можно загрузить с официального сайта Ђјладдин –.ƒ.ї.
ƒл€ обеспечени€ работы со смарт-картой подсистемы Kerberos добавочно к предустановленным пакетам ald/kerberos установите пакет krb5-pkinit на клиенте и сервере.
ƒл€ обеспечени€ возможности выпуска ключей и сертификатов на JaCarta PKI на сервере также установите пакеты libengine-pkcs11-openssl и opensc.
”становка и настройка центра сертификации на сервере
¬ качестве центра сертификации (CA) будет использован OpenSSL.
OpenSSL Ч криптографический пакет с открытым исходным кодом дл€ работы с SSL/TLS. ѕозвол€ет создавать ключи RSA, DH, DSA и сертификаты X.509, подписывать их, формировать CSR и CRT.
¬се настройки в руководстве выполн€ютс€ дл€ тестового домена EXAMPLE.RU. ѕримем, что сервер и клиент принадлежат домену EXAMPLE.RU, им€ сервера Ц kdc, а клиента Ц client. ѕри настройке используйте им€ вашего домена, сервера и клиента. ¬ыполните следующие действи€.
- —оздайте каталог CA командой mkdir /etc/ssl/CA и перейдите в него. ¬ этом каталоге будут размещатьс€ сгенерированные ключи и сертификаты.
- —оздайте ключ и сертификат CA:
$ openssl genrsa -out cakey.pem 2048
$ openssl req -key cakey.pem -new -x509 Цdays 365 -out cacert.pem
¬ диалоге заполните необходимую информацию о вашем центре сертификации. ¬ Common name указать EXAMPLE.RU.
- —оздайте ключ и сертификат KDC:
$ openssl genrsa -out kdckey.pem 2048
$ openssl req -new -out kdc.req -key kdckey.pem
¬ диалоге заполните необходимую информацию о вашем сервере. ¬ Common name указать kdc.
- ”становите переменные среды. ѕеременные среды устанавливаютс€ в рамках сессии и не устанавливаютс€ дл€ других сессий и не сохран€ютс€ после закрыти€ сессии.
export REALM=EXAMPLE.RU Ч ¬аш домен
export CLIENT=kdc Ч ¬ашего сервер
- «агрузите файл pkinit_extensions Ч http://dms.aladdin-rd.ru/970c5538-afbf-4a26-a7ef-d76550cbc435
—одержимое файла pkinit_extensions (его следует положить в тот каталог, откуда вы выполн€ете команды):
[ kdc_cert ]
basicConstraints=CA:FALSE
# Here are some examples of the usage of nsCertType. If it is omitted
keyUsage = nonRepudiation, digitalSignature, keyEncipherment, keyAgreement
#Pkinit EKU
extendedKeyUsage = 1.3.6.1.5.2.3.5
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid,issuer
# Copy subject details
issuerAltName=issuer:copy
# Add id-pkinit-san (pkinit subjectAlternativeName)
subjectAltName=otherName:1.3.6.1.5.2.2;SEQUENCE:kdc_princ_name
[kdc_princ_name]
realm = EXP:0, GeneralString:${ENV::REALM}
principal_name = EXP:1, SEQUENCE:kdc_principal_seq
[kdc_principal_seq]
name_type = EXP:0, INTEGER:1
name_string = EXP:1, SEQUENCE:kdc_principals
[kdc_principals]
princ1 = GeneralString:krbtgt
princ2 = GeneralString:${ENV::REALM}
[ client_cert ]
# These extensions are added when 'ca' signs a request.
basicConstraints=CA:FALSE
keyUsage = digitalSignature, keyEncipherment, keyAgreement
extendedKeyUsage = 1.3.6.1.5.2.3.4
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid,issuer
subjectAltName=otherName:1.3.6.1.5.2.2;SEQUENCE:princ_name
# Copy subject details
issuerAltName=issuer:copy
[princ_name]
realm = EXP:0, GeneralString:${ENV::REALM}
principal_name = EXP:1, SEQUENCE:principal_seq
[principal_seq]
name_type = EXP:0, INTEGER:1
name_string = EXP:1, SEQUENCE:principals
[principals]
princ1 = GeneralString:${ENV::CLIENT} - ¬ыпустите сертификат KDC:
$ openssl x509 -req -in kdc.req -CAkey cakey.pem -CA cacert.pem -out kdc.pem -extfile pkinit_extensions -extensions kdc_cert ЦCAcreateserial Цdays 365
- ‘айлы kdc.pem, kdckey.pem, cacert.pem перенесите в /var/lib/krb5kdc/
- —оздайте резервную копию файла /etc/krb5kdc/kdc.conf. ќтредактируйте /etc/krb5kdc/kdc.conf, дополнив секцию [kdcdefaults] следующими запис€ми:
pkinit_identity = FILE:/var/lib/krb5kdc/kdc.pem,/var/lib/krb5kdc/kdckey.pem
pkinit_anchors = FILE:/var/lib/krb5kdc/cacert.pem
ѕерва€ запись задает ключи и сертификат сервера, а втора€ указывает на корневой сертификат центра сертификации.
- ƒл€ прин€ти€ изменений выполните:
/etc/init.d/krb5-admin-server restart
/etc/init.d/krb5-kdc restart
ѕодготовка смарт-карты. ¬ыпуск ключей и сертификата пользовател€
”бедитесь в том, что установлены пакеты libengine-pkcs11-openssl и opensc. ѕодключите устройство, которое следует подготовить.
ѕроинициализируйте устройство, установите PIN-код пользовател€. ѕомните, что инициализаци€ устройства удалит все данные на JaCarta PKI без возможности восстановлени€.
ƒл€ инициализации необходимо воспользоватьс€ утилитой pkcs11-tool.
pkcs11-tool --slot 0 --init-token --so-pin 00000000 --label 'JaCarta PKI' --module /lib64/libASEP11.so,
где:
--slot 0 Ч указывает, в какой виртуальный слот подключено устройство. ак правило, это слот 0, но могут быть и другие значени€ Ц 1,2 и т.д.;
--init-token Ц команда инициализации токена;
--so-pin 00000000 Ц PIN-код администратора JaCarta PKI. ѕо умолчанию имеет значение 00000000;
--label 'JaCarta PKI' Ц метка устройства;
--module /lib64/libASEP11.so Ч указывает путь до библиотеки libASEP11.so. ”станавливаетс€ в рамках пакета idprotectclient см. раздел Ђ”становка драйверов на сервер и клиентї.
ƒл€ задани€ PIN-кода пользовател€ используйте команду:
pkcs11-tool --slot 0 --init-pin --so-pin 00000000 --login --pin 11111111 --module /lib64/libASEP11.so,
где:
--slot 0 Ч указывает, в какой виртуальный слот подключено устройство. ак правило, это слот 0, но могут быть и другие значени€ Ц 1,2 и т.д.;
--init-pin Ц команда установки PIN-кода пользовател€;
--so-pin 00000000 Ц PIN-код администратора JaCarta PKI. ѕо умолчанию имеет значение 00000000;
--login Ц команда логина;
--pin 11111111 Ц задаваемый PIN-код пользовател€;
--module /lib64/libASEP11.so Ч указывает путь до библиотеки libASEP11.so. ”станавливаетс€ в рамках пакета idprotectclient см. раздел Ђ”становка драйверов на сервер и клиентї.
—генерируйте ключи на устройстве, дл€ этого введите следующую команду:
pkcs11-tool --slot 0 --login --pin 11111111 --keypairgen --key-type rsa:2048 --id 42 --label Уtest1 keyФ --module /lib64/libASEP11.so,
где:
--slot 0 Ч указывает, в какой виртуальный слот подключено устройство. ак правило, это слот 0, но могут быть и другие значени€ Ц 1,2 и т.д.;
--login --pin 11111111 Ч указывает, что следует произвести логин под пользователем с PIN-кодом Ђ11111111ї. ≈сли у ¬ашей карты другой PIN-код пользовател€, укажите его;
--keypairgen --key-type rsa:2048 Ч указывает, что должны быть сгенерированы ключи длиной 2048 бит;
--id 42 Ч устанавливает атрибут CKA_ID ключа. CKA_ID может быть любым;
«апомните это значение! ќно необходимо дл€ дальнейших шагов подготовки устройства к работе.
--label Уtest1 keyФ Ч устанавливает атрибут CKA_LABEL ключа. јтрибут может быть любым;
--module /lib64/libASEP11.so Ч указывает путь до библиотеки libASEP11.so. ”станавливаетс€ в рамках пакета idprotectclient см. раздел Ђ”становка драйверов на сервер и клиентї.
—генерируйте запрос на сертификат с помощью утилиты openssl. ƒл€ этого введите следующие команды:
#openssl
OpenSSL> engine dynamic -pre SO_PATH:/usr/lib/ssl/engines/engine_pkcs11.so -pre ID:pkcs11 -pre LIST_ADD:1 -pre LOAD -pre MODULE_PATH:/lib64/libASEP11.so
OpenSSL> req -engine pkcs11 -new -key 0:42 -keyform engine -out client.req -subj "/C=RU/ST=Moscow/L=Moscow/O=Aladdin/OU=dev/CN=test1 (!¬аш_ѕользователь!)/emailAddress=test1@mail.com"
OpenSSL>quit. ќбратите внимание на -new -key 0:42, где 0 Ч номер виртуального слота с устройством, 42 Ч атрибут CKA_ID сгенерированных раннее ключей.
»нформацию, которую необходимо указать в запросе, следует задавать в поле "/C=RU/ST=Moscow/L=Moscow/O=Aladdin/OU=dev/CN=test1 (! ¬аш_ѕользователь!)/emailAddress=test1@mail.com".
Ќеобходимо установить переменные окружени€
$ export REALM=EXAMPLE.RU #¬аш домен
$ export CLIENT=test1 #¬аш пользователь
и выпустить сертификат на пользовател€.
$ openssl x509 -CAkey cakey.pem -CA cacert.pem -req -in client.req -extensions client_cert -extfile pkinit_extensions -out client.pem Цdays 365
ƒалее перекодируйте полученный сертификат из PEM в DER.
# openssl x509 -in client.pem -out client.cer -inform PEM -outform DER
«апишите полученный сертификат на токен.
pkcs11-tool --slot 0 --login --pin 11111111 --write-object client.cer --type 'cert' --label 'Certificate' --id 42 --module /lib/libASEP11.so,
где:
--slot 0 Ч указывает, в какой виртуальный слот подключено устройство. ак правило, это слот 0, но могут быть и другие значени€ Ц 1,2 и т.д.;
--login --pin 11111111 Ч указывает, что следует произвести логин под пользователем с PIN-кодом Ђ11111111ї. ≈сли у ¬ашей карты другой PIN-код пользовател€, укажите его;
--write-object ./client.cer Ч указывает, что необходимо записать объект и путь до него;
--type 'cert' Ч указывает, что тип записываемого объекта Ц сертификат;
'cert' --label 'Certificate' Ч устанавливает атрибут CKA_LABEL сертификата. јтрибут может быть любым;
--id 42 Ч устанавливает атрибут CKA_ID сертификата. ƒолжен быть указан тот же CKA_ID, что и дл€ ключей;
--module /lib64/libASEP11.so Ч указывает путь до библиотеки libASEP11.so.
Ќастройка клиента. ѕроверка работоспособности
—оздайте на клиенте каталог /etc/krb5/. —копируйте в /etc/krb5/ сертификат CA (cacert.pem) c сервера.
Ќастройте kerberos в /etc/krb5.conf. —екцию [libdefaults] дополните следующими строками.
[libdefaults]
default_realm = EXAMPLE.RU
pkinit_anchors = FILE:/etc/krb5/cacert.pem
# дл€ аутентификации по токену
pkinit_identities = PKCS11:/lib64/libASEP11.so¬ыполните проверку:
kinit огда по€витс€ строка запроса PIN-кода к карте, введите его.
ƒл€ проверки того, что kerberos-тикет был успешно получен дл€ пользовател€, введите команду klist. ƒл€ удалени€ тикета Ч kdestroy.
ƒл€ входа в домен по смарт-карте на экране входа в ќ— вместо парол€ введите PIN-код от смарт-карты.
Ќа этом настройка окончена. ƒа, к сожалению, система сама не помен€ет и не подстроит login окно под смарт-карту, и оно будет стандартным, но если приложить немного секретных усилий, можно добитьс€ красивого результата.

| омментировать | « ѕред. запись — дневнику — —лед. запись » | —траницы: [1] [Ќовые] |






