[»з песочницы] »мплементаци€ OpenId Connect в ASP.NET Core при помощи IdentityServer4 и oidc-client |
»мплементаци€ OpenId Connect в ASP.NET Core при помощи IdentityServer4 и oidc-client
Ќедавно мне потребовалось разобратьс€, как делаетс€ аутентификаци€ на OpenId Connect на ASP.NET Core. Ќачал с примеров, быстро стало пон€тно, что чтени€ спецификации не избежать, затем пришлось уже перейти к чтению исходников и статей разработчиков. ¬ результате возникло желание собрать в одном месте всЄ, что необходимо дл€ того, чтобы пон€ть, как сделать рабочую реализацию OpenId Connect Implicit Flow на платформе ASP.NET Core, при этом понима€, что ¬ы делаете.
—тать€ про специфику имплементации, поэтому рекомендую воспроизводить решение по предложенному в статье коду, иначе будет трудно уловить контекст. Ѕольшинство значимых замечаний в комментари€х и в тексте статьи содержат ссылки на источники. Ќекоторые термины не имеют общеприн€тых переводов на русский €зык, € оставил их на английском.
Ќемного об OpenId Connect
≈сли ¬ы понимаете OpenId Connect, можете начинать читать со следующей части.
OpenId Connect (не путать с OpenId) Ч протокол аутентификации, построенный на базе протокола авторизации OAuth2.0. ƒело в том, что задачу OAuth2 вход€т вопросы только авторизации пользователей, но не их аутентификации. OpenID Connect также задаЄт стандартный способ получени€ и представлени€ профилей пользователей в качестве набора значений, называемых claims. OpenId Connect описывает UserInfo endpoint, который возвращает эти информацию. “акже он позвол€ет клиентским приложени€м получать информацию о пользователе в форме подписанного JSON Web Token (JWT), что позвол€ет слать меньше запросов на сервер.
Ќачать знакомство с протоколом имеет смысл с официального сайта, затем полезно почитать сайты коммерческих поставщиков облачных решений по аутентификации вроде Connect2id, Auth0 и Stormpath. ќписание всех нужных терминов не привожу, во-первых это была бы стена текста, а во вторых всЄ необходимое есть по этим ссылкам.
≈сли Identity Server ¬ам не знаком, рекомендую начать с чтени€ его прекрасной документации, а также отличных примеров вроде этого.
„то мы хотим получить в итоге
ћы реализуем OpenId Connect Implicit Flow, который рекомендован дл€ JavaScript-приложений, в браузере, в том числе дл€ SPA. ¬ процессе мы чуть глубже, чем это обычно делаетс€ в пошаговых руководствах, обсудим разные значимые настройки. «атем мы посмотрим, как работает наша реализаци€ с точки зрени€ протокола OpenId Connect, а также изучим, как имплементаци€ соотноситс€ с протоколом.
»нструменты
- Ќа стороне сервера воспользуемс€ IdentityServer4
- Ќа стороне клиента будем использовать библиотеку oidc-client
ќсновные авторы обеих библиотек Ч Ѕрок јллен и ƒоминик Ѕрайер.
—ценарии взаимодействи€
” нас будет 3 проекта:
- IdentityServer Ч наш сервер аутентификации OpenId Connect.
- Api Ч наш тестовый веб-сервис.
- Client Ч наше клиентское приложение на JavaScript, основано на коде JavaScriptClient.
—ценарий взаимодействи€ таков: клиентское приложение Client авторизуетс€ при помощи сервера аутентификации IdentityServer и получает access_token (JWT), который затем использует в качестве Bearer-токена дл€ вызова веб-сервиса на сервере Api.
—тандарт OpenId Connect описывает разные варианты пор€дка прохождени€ аутентификации. Ёти варианты на €зыке стандарта называютс€ Flow.
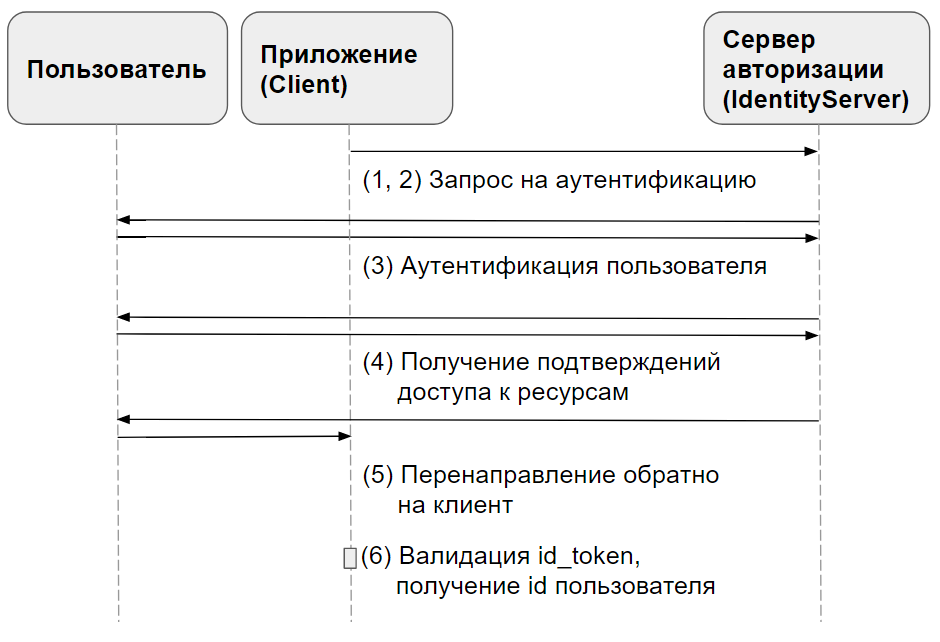
Implicit Flow, который мы рассматриваем в этой статье, включает такие шаги:
- лиент готовит запрос на аутентификацию, содержащий нужные параметры запроса.
- лиент шлЄт запрос на аутентификацию на сервер авторизации.
- —ервер авторизации аутентифицирует конечного пользовател€.
- —ервер авторизации получает подтверждение от конечного пользовател€.
- —ервер авторизации посылает конечного пользовател€ обратно на клиент с id_token'ом и, если требуетс€, access_token'ом.
- лиент валидирует id_token и получает Subject Identifier конечного пользовател€.
»мплементаци€
ƒл€ того, чтобы сильно сэкономить на написании станиц, св€занных с логином и логаутом, будем использовать официальный код Quickstart.
«апускать Api и IdentityServer в процессе выполнени€ этого упражнени€ рекомендую через dotnet run Ч IdentityServer пишет массу полезной диагностической информации в процессе своей работы, данна€ информаци€ сразу будет видна в консоли.
ƒл€ простоты предполагаетс€, что все проекты запущены на том же компьютере, на котором работает браузер пользовател€.
ƒавайте приступим к реализации. ƒл€ определЄнности будем предполагать, что ¬ы используете Visual Studio 2017 (15.3). √отовый код решени€ можно посмотреть здесь
—оздайте пустой solution OpenIdConnectSample.
Ѕольша€ часть кода основана на примерах из документации IdentityServer, однако код в данной статье дополнен тем, чего, на мой взгл€д, не хватает в официальной документации, и аннотирован.
–екомендую ознакомитьс€ со всеми официальными примерами, мы же поглубже рассмотрим именно Implicit Flow.
1. IdentityServer
—оздайте solution с пустым проектом, в качестве платформы выберите ASP.NET Core 1.1.
”становите такие NuGet-пакеты
Install-Package Microsoft.AspNetCore.Mvc -Version 1.1.3
Install-Package Microsoft.AspNetCore.StaticFiles -Version 1.1.2
Install-Package IdentityServer4 -Version 1.5.2¬ерсии пакеты здесь значимы, т.к. Install-Package по умолчанию устанавливает последние версии. ’от€ авторы уже сделали порт IdentityServer на Asp.NET Core 2.0 в dev-ветке, на момент написани€ статьи, они ещЄ не портировали Quickstart UI. –азличи€ в коде нашего примера дл€ .NET Core 1.1 и 2.0 невелики.
»змените метод Main Program.cs так, чтобы он выгл€дел следующим образом
public static void Main(string[] args)
{
Console.Title = "IdentityServer";
// https://docs.microsoft.com/en-us/aspnet/core/fundamentals/servers/kestrel?tabs=aspnetcore2x
var host = new WebHostBuilder()
.UseKestrel()
// задаЄм порт, и адрес на котором Kestrel будет слушать
.UseUrls("http://localhost:5000")
// имеет значени€ дл€ UI логина-логаута
.UseContentRoot(Directory.GetCurrentDirectory())
.UseIISIntegration()
.UseStartup()
.Build();
host.Run();
} «атем в Startup.cs
- ƒобавьте пространства имЄн
using System.Security.Claims; using IdentityServer4; using IdentityServer4.Configuration; using IdentityServer4.Models; using IdentityServer4.Test; - ƒобавьте несколько вспомогательных методов, которые содержат настройки IdentityServer, обратите внимание на комментарии. Ёти методы будут в дальнейшем вызваны в
ConfigureServices. –екомендую читать текст методов перед их добавлением в проект Ч с одной стороны это позволит сразу иметь целостную картину происход€щего, с другой стороны лишнего там мало.
Ќастройки информации дл€ клиентских приложений
public static IEnumerable GetIdentityResources()
{
// определ€ет, какие scopes будут доступны IdentityServer
return new List
{
// "sub" claim
new IdentityResources.OpenId(),
// стандартные claims в соответствии с profile scope
// http://openid.net/specs/openid-connect-core-1_0.html#ScopeClaims
new IdentityResources.Profile(),
};
} Ёти настройки добавл€ют поддержку claim sub, это минимальное требование дл€ соответстви€ нашего токена OpenId Connect, а также claim scope profile, включающего описанные стандартом OpenId Connect пол€ профил€ типа имени, пола, даты рождени€ и подобных.
Ёто аналогичные предыдущим настройки, но информаци€ предназначаетс€ дл€ API
public static IEnumerable GetApiResources()
{
// claims этих scopes будут включены в access_token
return new List
{
// определ€ем scope "api1" дл€ IdentityServer
new ApiResource("api1", "API 1",
// эти claims войдут в scope api1
new[] {"name", "role" })
};
} —ами клиентские приложени€, нужно чтобы сервер знал о них
public static IEnumerable GetClients()
{
return new List
{
new Client
{
// об€зательный параметр, при помощи client_id сервер различает клиентские приложени€
ClientId = "js",
ClientName = "JavaScript Client",
AllowedGrantTypes = GrantTypes.Implicit,
AllowAccessTokensViaBrowser = true,
// от этой настройки зависит размер токена,
// при false можно получить недостающую информацию через UserInfo endpoint
AlwaysIncludeUserClaimsInIdToken = true,
// белый список адресов на который клиентское приложение может попросить
// перенаправить User Agent, важно дл€ безопасности
RedirectUris = {
// адрес перенаправлени€ после логина
"http://localhost:5003/callback.html",
// адрес перенаправлени€ при автоматическом обновлении access_token через iframe
"http://localhost:5003/callback-silent.html"
},
PostLogoutRedirectUris = { "http://localhost:5003/index.html" },
// адрес клиентского приложени€, просим сервер возвращать нужные CORS-заголовки
AllowedCorsOrigins = { "http://localhost:5003" },
// список scopes, разрешЄнных именно дл€ данного клиентского приложени€
AllowedScopes =
{
IdentityServerConstants.StandardScopes.OpenId,
IdentityServerConstants.StandardScopes.Profile,
"api1"
},
AccessTokenLifetime = 300, // секунд, это значение по умолчанию
IdentityTokenLifetime = 3600, // секунд, это значение по умолчанию
// разрешено ли получение refresh-токенов через указание scope offline_access
AllowOfflineAccess = false,
}
};
} “естовые пользователи, обратите внимание, что bob у нас админ
public static List GetUsers()
{
return new List
{
new TestUser
{
SubjectId = "1",
Username = "alice",
Password = "password",
Claims = new List
{
new Claim("name", "Alice"),
new Claim("website", "https://alice.com"),
new Claim("role", "user"),
}
},
new TestUser
{
SubjectId = "2",
Username = "bob",
Password = "password",
Claims = new List
{
new Claim("name", "Bob"),
new Claim("website", "https://bob.com"),
new Claim("role", "admin"),
}
}
};
} - »змените метод
ConfigureServicesтак
public void ConfigureServices(IServiceCollection services)
{
services.AddMvc();
services.AddIdentityServer(options =>
{
// http://docs.identityserver.io/en/release/reference/options.html#refoptions
options.Endpoints = new EndpointsOptions
{
// в Implicit Flow используетс€ дл€ получени€ токенов
EnableAuthorizeEndpoint = true,
// дл€ получени€ статуса сессии
EnableCheckSessionEndpoint = true,
// дл€ логаута по инициативе пользовател€
EnableEndSessionEndpoint = true,
// дл€ получени€ claims аутентифицированного пользовател€
// http://openid.net/specs/openid-connect-core-1_0.html#UserInfo
EnableUserInfoEndpoint = true,
// используетс€ OpenId Connect дл€ получени€ метаданных
EnableDiscoveryEndpoint = true,
// дл€ получени€ информации о токенах, мы не используем
EnableIntrospectionEndpoint = false,
// нам не нужен т.к. в Implicit Flow access_token получают через authorization_endpoint
EnableTokenEndpoint = false,
// мы не используем refresh и reference tokens
// http://docs.identityserver.io/en/release/topics/reference_tokens.html
EnableTokenRevocationEndpoint = false
};
// IdentitySever использует cookie дл€ хранени€ своей сессии
options.Authentication = new IdentityServer4.Configuration.AuthenticationOptions
{
CookieLifetime = TimeSpan.FromDays(1)
};
})
// тестовый x509-сертификат, IdentityServer использует RS256 дл€ подписи JWT
.AddDeveloperSigningCredential()
// что включать в id_token
.AddInMemoryIdentityResources(GetIdentityResources())
// что включать в access_token
.AddInMemoryApiResources(GetApiResources())
// настройки клиентских приложений
.AddInMemoryClients(GetClients())
// тестовые пользователи
.AddTestUsers(GetUsers());
}¬ этом методе мы указываем настройки IdentityServer, в частности сертификаты, используемые дл€ подписывани€ токенов, настройки scope в смысле OpenId Connect и OAuth2.0, настройки приложений-клиентов, а также настройки пользователей.
“еперь чуть подробнее. AddIdentityServer регистрирует сервис IdentityServer в механизме разрешени€ зависимостей ASP.NET Core, это нужно сделать, чтобы была возможность добавить его как middleware в Configure.
- IdentityServer подписывает токены при помощи RSA SHA 256, поэтому требуетс€ пара приватный-публичный ключ.
AddDeveloperSigningCredentialдобавл€ет тестовые ключи дл€ подписи JWT-токенов, а именно id_token, access_token в нашем случае. ¬ продакшне нужно заменить эти ключи, сделать это можно, например сгенерировав самоподписной сертификат. AddInMemoryIdentityResources. ѕочитать о том, что понимаетс€ под ресурсами можно тут, а зачем они нужны Ч тут.
ћетод Configure должен выгл€деть так
public void Configure(IApplicationBuilder app, IHostingEnvironment env, ILoggerFactory loggerFactory)
{
loggerFactory.AddConsole(LogLevel.Debug);
app.UseDeveloperExceptionPage();
// подключаем middleware IdentityServer
app.UseIdentityServer();
// эти 2 строчки нужны, чтобы нормально обрабатывались страницы логина
app.UseStaticFiles();
app.UseMvcWithDefaultRoute();
}
—качайте из официального репозитори€ Starter UI дл€ IdentityServer, затем скопируйте файлы в папку проекта, так чтобы папки совпали по структуре, например wwwroot с wwwroot.
ѕроверьте, что проект компилируетс€.
2. Api
ƒанный проект Ч игрушечный сервер API с ограниченным доступом.
ƒобавьте в solution ещЄ один пустой проект Api, в качестве платформы выберите ASP.NET Core 1.1. “.к. мы не собираемс€ создавать полноценное веб-приложение в данном проекте, а лишь легковесный веб-сервис, отдающий JSON, ограничимс€ лишь MvcCore middleware вместо полного Mvc.
ƒобавьте нужные пакеты, выполнив эти команды в Package Manager Console
Install-Package Microsoft.AspNetCore.Mvc.Core -Version 1.1.3
Install-Package Microsoft.AspNetCore.Mvc.Formatters.Json -Version 1.1.3
Install-Package Microsoft.AspNetCore.Cors -Version 1.1.2
Install-Package IdentityServer4.AccessTokenValidation -Version 1.2.1ЌачнЄм с того, что добавим нужные настройки Kestrel в Program.cs
public static void Main(string[] args)
{
Console.Title = "API";
var host = new WebHostBuilder()
.UseKestrel()
.UseUrls("http://localhost:5001")
.UseContentRoot(Directory.GetCurrentDirectory())
.UseIISIntegration()
.UseStartup()
.Build();
host.Run();
} ¬ Startup.cs потребуетс€ несколько меньше изменений.
ƒл€ ConfigureServices
public void ConfigureServices(IServiceCollection services)
{
services.AddCors(options=>
{
// задаЄм политику CORS, чтобы наше клиентское приложение могло отправить запрос на сервер API
options.AddPolicy("default", policy =>
{
policy.WithOrigins("http://localhost:5003")
.AllowAnyHeader()
.AllowAnyMethod();
});
});
// облегчЄнна€ верси€ MVC Core без движка Razor, DataAnnotations и подобного, сопоставима с Asp.NET 4.5 WebApi
services.AddMvcCore()
// добавл€ем авторизацию, благодар€ этому будут работать атрибуты Authorize
.AddAuthorization(options =>
// политики позвол€ют не работать с Roles magic strings, содержащими перечислени€ ролей через зап€тую
options.AddPolicy("AdminsOnly", policyUser =>
{
policyUser.RequireClaim("role", "admin");
})
)
// добавл€етс€ AddMVC, не добавл€етс€ AddMvcCore, мы же хотим получать результат в JSON
.AddJsonFormatters();
}ј вот так должен выгл€деть Configure
public void Configure(IApplicationBuilder app, IHostingEnvironment env, ILoggerFactory loggerFactory)
{
loggerFactory.AddConsole(LogLevel.Debug);
// добавл€ем middleware дл€ CORS
app.UseCors("default");
// добавл€ем middleware дл€ заполнени€ объекта пользовател€ из OpenId Connect JWT-токенов
app.UseIdentityServerAuthentication(new IdentityServerAuthenticationOptions
{
// наш IdentityServer
Authority = "http://localhost:5000",
// говорим, что нам не требуетс€ HTTPS при общении с IdentityServer, должно быть true на продуктиве
// https://docs.microsoft.com/en-us/aspnet/core/api/microsoft.aspnetcore.builder.openidconnectoptions
RequireHttpsMetadata = false,
// это значение будет сравниватьс€ со значением пол€ aud внутри access_token JWT
ApiName = "api1",
// можно так написать, если мы хотим разделить наш api на отдельные scopes и всЄ же сохранить валидацию scope
// AllowedScopes = { "api1.read", "api1.write" }
// читать JWT-токен и добавл€ть claims оттуда в HttpContext.User даже если не используетс€ атрибут Authorize со схемо…, соответствующей токену
AutomaticAuthenticate = true,
// назначаем этот middleware как используемый дл€ формировани€ authentication challenge
AutomaticChallenge = true,
// требуетс€ дл€ [Authorize], дл€ IdentityServerAuthenticationOptions - значение по умолчанию
RoleClaimType = "role",
});
app.UseMvc();
}ќсталось добавить наш контроллер, он возвращает текущие Claims пользовател€, что удобно дл€ того, чтобы понимать, как middleware аутентификации IdentityServer расшифровал access_token.
ƒобавьте в проект единственный контроллер IdentityController.
Cодержимое файла должно быть таким.
using System.Linq;
using Microsoft.AspNetCore.Mvc;
using Microsoft.AspNetCore.Authorization;
namespace Api.Controllers
{
[Authorize]
public class IdentityController : ControllerBase
{
[HttpGet]
[Route("identity")]
public IActionResult Get()
{
return new JsonResult(from c in User.Claims select new { c.Type, c.Value });
}
[HttpGet]
[Route("superpowers")]
[Authorize(Policy = "AdminsOnly")]
public IActionResult Superpowers()
{
return new JsonResult("Superpowers!");
}
}
}”бедитесь, что проект компилируетс€.
3. Client
Ётот проект фактически не содержит значимой серверной части. ¬есь серверный код Ч это просто настройки веб-сервер Kestrel, с тем чтобы он отдавал статические файлы клиента.
“ак же, как и прошлых 2 раза добавьте в решение пустой проект, назовите его Client.
”становите пакет дл€ работы со статическими файлами.
Install-Package Microsoft.AspNetCore.StaticFiles -Version 1.1.2»змените файл Program.cs
public static void Main(string[] args)
{
var host = new WebHostBuilder()
.UseKestrel()
.UseUrls("http://localhost:5003")
.UseContentRoot(Directory.GetCurrentDirectory())
.UseIISIntegration()
.UseStartup()
.Build();
host.Run();
} ласс Startup должен содержать такой код.
public void ConfigureServices(IServiceCollection services)
{
}
public void Configure(IApplicationBuilder app)
{
app.UseDefaultFiles();
app.UseStaticFiles();
}лиентский код на JavaScript, с другой стороны, и содержит всю логику аутентификации и вызовов Api.
ћы по одному добавим в папку wwwroot проекта следующие файлы.
index.htmlЧ простой HTML-файл с кнопками различных действий и ссылкой на JavaScript-файл приложени€app.jsиoidc-client.js.oidc-client.jsЧ клиентска€ библиотека, реализующа€ OpenId Connectapp.jsЧ настройки oidc-client и обработчики событий кнопокcallback.htmlЧ страница, на которую сервер аутентификации перенаправл€ет клиентское приложение, передава€ параметры, необходимые дл€ завершени€ процедуры входа.callback-silent.htmlЧ страница, аналогична€callback.html, однако именно дл€ случа€, когда происходит "фоновый" повторный логин через iframe. Ёто нужно чтобы продлевать доступ пользовател€ к ресурсам без использовани€refresh_token.
index.html
ƒобавьте новый HTML-файл с таким названием в папку wwwroot проекта.
oidc-client.js
—качайте этот файл отсюда (1.3.0) и добавьте в проект.
app.js
ƒобавьте новый JavaScript-файл с таким названием в папку wwwroot проекта.
ƒобавьте
/// в начале файла дл€ поддержки IntelliSense.
¬ставьте этот код к началу app.js
Oidc.Log.logger = console;
Oidc.Log.level = 4;ѕервой строкой, пользу€сь совместимостью по вызываемым методам, устанавливаем стандартную консоль браузера в качестве стандартного логгера дл€ oidc-client. ¬торой строкой просим выводить все сообщени€. Ёто позволит увидеть больше подробностей, когда мы перейдЄм ко второй части статьи, и будем смотреть, как же наша имплементаци€ работает.
“еперь давайте по част€м добавим остальной код в этот файл.
Ёта часть кода сама€ длинна€, и, пожалуй, сама€ интересна€. ќна содержит настройки библиотеки основного объекта UserManager библиотеки oidc-client, а также его создание. –екомендую ознакомитьс€ с самими настройками и комментари€ми к ним.
var config = {
authority: "http://localhost:5000", // јдрес нашего IdentityServer
client_id: "js", // должен совпадать с указанным на IdentityServer
// јдрес страницы, на которую будет перенаправлен браузер после прохождени€ пользователем аутентификации
// и получени€ от пользовател€ подтверждений - в соответствии с требовани€ми OpenId Connect
redirect_uri: "http://localhost:5003/callback.html",
// Response Type определ€ет набор токенов, получаемых от Authorization Endpoint
// ƒанное сочетание означает, что мы используем Implicit Flow
// http://openid.net/specs/openid-connect-core-1_0.html#Authentication
response_type: "id_token token",
// ѕолучить subject id пользовател€, а также пол€ профил€ в id_token, а также получить access_token дл€ доступа к api1 (см. наcтройки IdentityServer)
scope: "openid profile api1",
// —траница, на которую нужно перенаправить пользовател€ в случае инициированного им логаута
post_logout_redirect_uri: "http://localhost:5003/index.html",
// следить за состо€нием сессии на IdentityServer, по умолчанию true
monitorSession: true,
// интервал в миллисекундах, раз в который нужно провер€ть сессию пользовател€, по умолчанию 2000
checkSessionInterval: 30000,
// отзывает access_token в соответствии со стандартом https://tools.ietf.org/html/rfc7009
revokeAccessTokenOnSignout: true,
// допустима€ погрешность часов на клиенте и серверах, нужна дл€ валидации токенов, по умолчанию 300
// https://github.com/IdentityModel/oidc-client-js/blob/1.3.0/src/JoseUtil.js#L95
clockSkew: 300,
// делать ли запрос к UserInfo endpoint дл€ того, чтоб добавить данные в профиль пользовател€
loadUserInfo: true,
};
var mgr = new Oidc.UserManager(config);ƒавайте теперь добавим обработчики дл€ кнопок и подписку на них.
function login() {
// »нициировать логин
mgr.signinRedirect();
}
function displayUser() {
mgr.getUser().then(function (user) {
if (user) {
log("User logged in", user.profile);
}
else {
log("User not logged in");
}
});
}
function api() {
// возвращает все claims пользовател€
requestUrl(mgr, "http://localhost:5001/identity");
}
function getSuperpowers() {
// этот endpoint доступен только админам
requestUrl(mgr, "http://localhost:5001/superpowers");
}
function logout() {
// »нициировать логаут
mgr.signoutRedirect();
}
document.getElementById("login").addEventListener("click", login, false);
document.getElementById("api").addEventListener("click", api, false);
document.getElementById("getSuperpowers").addEventListener("click", getSuperpowers, false);
document.getElementById("logout").addEventListener("click", logout, false);
document.getElementById("getUser").addEventListener("click", displayUser, false);
// отобразить данные о пользователе после загрузки
displayUser();ќсталось добавить пару утилит
function requestUrl(mgr, url) {
mgr.getUser().then(function (user) {
var xhr = new XMLHttpRequest();
xhr.open("GET", url);
xhr.onload = function () {
log(xhr.status, 200 == xhr.status ? JSON.parse(xhr.responseText) : "An error has occured.");
}
// добавл€ем заголовок Authorization с access_token в качестве Bearer - токена.
xhr.setRequestHeader("Authorization", "Bearer " + user.access_token);
xhr.send();
});
}
function log() {
document.getElementById('results').innerText = '';
Array.prototype.forEach.call(arguments, function (msg) {
if (msg instanceof Error) {
msg = "Error: " + msg.message;
}
else if (typeof msg !== 'string') {
msg = JSON.stringify(msg, null, 2);
}
document.getElementById('results').innerHTML += msg + '\r\n';
});
}¬ принципе, на этом можно было бы и заканчивать, но требуетс€ добавить ещЄ две страницы, которые нужны дл€ завершени€ процедуры входа. ƒобавьте страницы с таким кодом в wwwroot.
callback.html
callback-silent.html
√отово!
ак это работает
«апускать проекты рекомендую так: запускаете консоль, переходите в папку проекта, выполн€ете команду dotnet run. Ёто позволит видеть что IdentityServer и другие приложени€ логируют в консоль.
«апустите вначале IdentityServer и Api, а затем и Client.
ќткройте страницу http://localhost:5003/index.html Client.
Ќа этом этапе ¬ы можете захотеть очистить консоль при помощи clear().
“еперь давайте настроим консоль, чтобы на самом деле видеть всю интересную информацию.
Ќапример, дл€ Chrome 60 настройки консоли должны выгл€деть так.
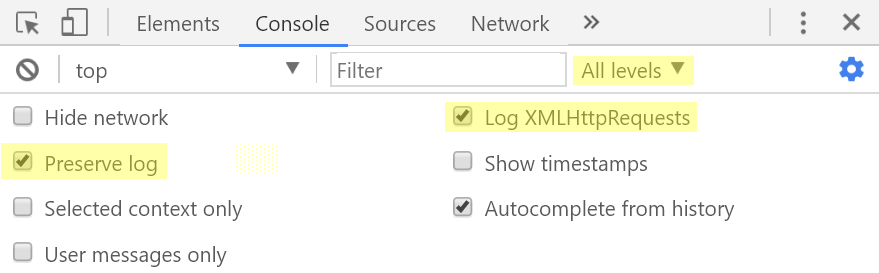
¬о вкладке Network инструментов разработчика ¬ы можете захотеть поставить галочку напротив Preserve log чтобы редиректы не мешали в дальнейшем провер€ть значени€ различных параметров.
ќбновите страницу при помощи CTRL+F5.
Happy path
ѕосмотрим, какие действи€ соответствуют первым двум шагам спецификации.
1. лиент готовит запрос на аутентификацию, содержащий нужные параметры запроса.
2. лиент шлЄт запрос на аутентификацию на сервер авторизации.
ликните на кнопку Login.
¬заимодействие с сервером авторизации начинаетс€ с GET-запроса на адрес
http://localhost:5000/.well-known/openid-configuration
Ётим запросом oidc-client получает метаданные нашего провайдера OpenId Connect (рекомендую открыть этот адрес в другой вкладке), в том числе authorization_endpoint
http://localhost:5000/connect/authorize
ќбратите внимание, что дл€ хранени€ данных о пользователе используетс€ WebStorage. oidc-client позвол€ет указать, какой именно объект будет использоватьс€, по умолчанию это sessionStorage.
¬ этот момент будет послан запрос на аутентификацию на authorization_endpoint с такими параметрами строки запроса
| »м€ | «начение |
|---|---|
| client_id | js |
| redirect_uri | http://localhost:5003/callback.html |
| response_type | id_token token |
| scope | openid profile api1 |
| state | некоторое труднопредсказуемое значение |
| nonce | некоторое труднопредсказуемое значение |
ќбратите внимание, что redirect_uri соответствует адресу, который мы указали дл€ нашего клиента с client_id js в настройках IdentityServer.
“.к. пользователь ещЄ не аутентифицирован, IdentityServer вышлет в качестве ответа редирект на форму логина.
«атем браузер перенаправлен на http://localhost:5000/account/login.
3. —ервер авторизации аутентифицирует конечного пользовател€.
4. —ервер авторизации получает подтверждение от конечного пользовател€.
5. —ервер авторизации посылает конечного пользовател€ обратно на клиент с id token'ом и, если требуетс€, access token'ом.
¬водим bob в качестве логина и password в качестве парол€, отправл€ем форму.
Ќас вначале вновь перенаправл€ют на authorization_endpoint, а оттуда на страницу подтверждени€ в соответствии с OpenId Connect разрешени€ получени€ relying party (в данном случае нашим js-клиентом) доступа к различным scopes.
—о всем соглашаемс€, отправл€ем форму. јналогично форме аутентификации, в ответ на отправку формы нас перенаправл€ют на authorization_endpoint, данные на authorization_endpoint передаютс€ при помощи cookie.
ќттуда браузер перенаправлен уже на адрес, который был указан в качестве redirect_uri в изначальном запросе на аутентификацию.
ѕри использовании Implicit Flow параметры передаютс€ после #. Ёто нужно дл€ того, чтобы эти значени€ были доступны нашему приложению на JavaScript, но при этом не отправл€лись на веб-сервер.
| »м€ | «начение |
|---|---|
| id_token | “окен с данными о пользователе дл€ клиента |
| access_token | “окен с нужными данными дл€ доступа к API |
| token_type | “ип access_token, в нашем случае Bearer |
| expires_in | ¬рем€ действи€ access_token |
| scope | scopes на которые пользователь дал разрешение через пробел |
6. лиент валидирует id token и получает Subject Identifier конечного пользовател€.
oidc-client провер€ет вначале наличие сохранЄнного на клиенте state, затем свер€ет nonce с полученным из id_token. ≈сли всЄ сходитс€, происходит проверка самих токенов на валидность (например, провер€етс€ подпись и наличие sub claim в id_token). Ќа этом этапе происходит чтение чтение содержимого id_token о объект профил€ пользовател€ библиотеки oidc-client на стороне клиента.
≈сли ¬ы захотите расшифровать id_token (проще всего его скопировать из вкладки Network инструментов разработчика), то увидите, что payload содержит что-то подобное
{
"nbf": 1505143180,
"exp": 1505146780,
"iss": "http://localhost:5000",
"aud": "js",
"nonce": "2bd3ed0b260e407e8edd0d03a32f150c",
"iat": 1505143180,
"at_hash": "UAeZEg7xr23ToH2R2aUGOA",
"sid": "053b5d83fd8d3ce3b13d3b175d5317f2",
"sub": "2",
"auth_time": 1505143180,
"idp": "local",
"name": "Bob",
"website": "https://bob.com",
"amr": [
"pwd"
]
}at_hash, который затем используетс€ дл€ валидации в соответствии со стандартом.
ƒл€ access_token в нашем случае payload будет выгл€деть, в том числе в соответствии с настройками, чуть иначе.
{
"nbf": 1505143180,
"exp": 1505143480,
"iss": "http://localhost:5000",
"aud": [
"http://localhost:5000/resources",
"api1"
],
"client_id": "js",
"sub": "2",
"auth_time": 1505143180,
"idp": "local",
"name": "Bob",
"role": "admin",
"scope": [
"openid",
"profile",
"api1"
],
"amr": [
"pwd"
]
}≈сли ¬ы не умеете дл€ себ€ объ€сн€ть все их отличи€, сейчас Ч прекрасный момент устранить этот пробел. Ќачать можно отсюда, или с повторного прочтени€ кода настроек IdentityServer.
¬ случае когда проверка завершаетс€ успехом, происходит чтение claims из id_token в объект профил€ на стороне клиента.
«атем, но только если указана настройка loadUserInfo, происходит обращение к UserInfo Endpoint. ѕри этом при обращении UserInfo Endpoint дл€ получени€ claims профил€ пользовател€ в заголовке Authorization в качестве Bearer-токена используетс€ access_token, а полученные claims будут добавлены в JavaScript-объект профил€ на стороне клиента.
loadUserInfo имеет смысл использовать если ¬ы хотите уменьшить размер access_token, если ¬ы хотите избежать дополнительного HTTP-запроса, может иметь смысл от этой опции отказатьс€.
¬ызываем метод API
Ќажмите кнопку "Call API".
ѕроизойдЄт ajax-запрос на адрес http://localhost:5001/identity.
ј именно, вначале будет OPTIONS-запрос согласно требовани€ми CORS т.к. мы осуществл€ем запрос ресурса с другого домена и используем заголовки, не вход€щие в список "безопасных" (Authorization, например).
«атем будет отправлен, собственно, сам GET-запрос. ќбратите внимание, что в заголовке запроса Authorization будет указано значение Bearer <значение access_token>.
IdentityServer middleware на стороне сервера проверит токен. ¬нутри кода IdentityServer middleware проверка токенов фактически осуществл€етс€ стандартным Asp.Net Core JwtBearerMiddleware.
ѕользователь будет считатьс€ авторизованным, поэтому сервер вернЄт нам ответ с кодом 200.
Logout
ќтправл€етс€ GET-запрос на end_session_endpoint
| »м€ | «начение |
|---|---|
| id_token_hint | —одержит значение id_token |
| post_logout_redirect_uri | URI, на который клиент хочет, чтобы провайдер аутентификации |
¬ ответ нас перенаправл€ют на страницу, содержащую данные о логауте дл€ пользовател€.
ѕровер€ем работу ролей
Ќа самом деле политики позвол€ют задавать любые услови€ предоставлени€ доступа, но € остановилс€ на примере реализации безопасности через роли. –олевую модель же реализуем через политики и токены, потому что это во-первых просто и нагл€дно, а во-вторых это наиболее часто используемый способ задани€ разрешений.
ѕопробуйте зайти вначале под пользователем alice и нажать кнопку Get Superpowers!, затем зайдите под пользователем bob и проделайте то же самое.
ƒругие варианты развити€ событий
ѕользователь жмЄт do not allow
Ќажмите Logout и залогиньтесь ещЄ раз, на этот раз используйте данные
Username: alice
Password: password
Ќа странице подтверждени€ http://localhost:5000/consent нажмите No, Do Not Allow.
¬ы попадЄте на страницу завершени€ логина клиентского приложени€ http://localhost:5003/callback.html.
ѕо причине того, что страница подтверждени€ пользователем передаЄт фрагмент URL #error=access_denied, выполнение signinRedirectCallback пойдЄт по другому пути, и промис в результате будет иметь статус rejected.
Ќа странице callback.html будет дл€ промиса выполнен catch-обработчик, он выведет текст ошибки в консоль.
ѕользователь не даЄт разрешени€ на профиль
—копируйте закодированный id_token из одноимЄнного параметра URL ответа и убедитесь, что теперь в него не вход€т claims, которые вход€т в стандартный scope profile.
Claims, которые вход€т в стандартный scope profile можно посмотреть тут.
ѕри этом вызвать API получитс€.
ѕользователь на даЄт разрешение на api1
¬ токене теперь нет claim api1
"scope": [
"openid",
"profile"
],ѕри попытке вызвать Api нам теперь возвращают 401 (Unathorized).
access_token устаревает
ƒождитесь устаревани€ access_token, нажмите кнопку Call API.
API будет вызван! Ёто вызвано тем, что IdentityServer использует middleware Asp.Net Core, который использует пон€тие ClockSkew. Ёто нужно дл€ того, чтобы всЄ в целом работало в случае если часы на клиенте и разных серверах несколько неточны, например, не возникали ситуации вроде токена, который был выпущен на период целиком в будущем. «начение ClockSkew по умолчанию 5 минут.
“еперь подождите 5 минут и убедитесь, что вызов API теперь возвращает 401 (Unathorized).
«амечание ¬ клиентском приложении может быть полезно €вно обрабатывать ответы с кодом 401, например пытатьс€ обновить access_token.
access_token обновл€етс€
ƒавайте теперь добавим в app.js в объект config код, так чтобы получилось
var config = {
// ...
// если true, клиент попытаетс€ обновить access_token перед его истечением, по умолчанию false
automaticSilentRenew: true,
// эта страница используетс€ дл€ "фонового" обновлени€ токена пользовател€ через iframe
silent_redirect_uri: 'http://localhost:5003/callback-silent.html',
// за столько секунд до истечени€ oidc-client постараетс€ обновить access_token
accessTokenExpiringNotificationTime: 60,
// ...
} ѕри помощи консоли браузера убедитесь что теперь происходит автоматическое обновление access_token. Ќажмите кнопку Call API чтобы убедитьс€, что всЄ работает.
id_token устаревает
≈сли access_token предназначаетс€ дл€ ресурса API и ресурс об€зан проверить его валидность, в том числе не устарел ли токен, при обращении к нему, то id_token предназначен именно дл€ самого клиентского приложени€. ѕоэтому и проверка должна проводитьс€ на клиенте js-клиенте. ’орошо описано тут.
«аключение
≈сли ¬ы следовали инструкци€м, на данный момент ¬ы:
- —воими руками сделали рабочую реализацию OpenId Connect Implicit Flow при помощи IdentityServer и oidc-client на платформе ASP.NET Core 1.1.
- ќзнакомились с различными параметрами, позвол€ющими настроить части имплементации дл€ ¬аших нужд.
- », главное, несколько подразобрались, как имплементаци€ соотноситс€ со стандартом, причЄм до того, как выучили стандарт наизусть.
ѕолезные ссылки
- ’ороший туториал.
- ќфициальные примеры IdentityServer4
- ќфициальные примеры oidc-client.
- “ут можно почитать про политики авторизации в ASP.NET Core. «аодно стоит прочитать и это.
- ¬ этой статье описано как использовать атрибут Authorize со списками ролей совместно с IdentityServer.
- «десь описано почему в стандарте OpenId Connect 2 токена Ч
id_tokenиaccess_tokenвместо одного. - ¬ процессе подготовки этой статьи вышла эта стать€ по реализации OpenId Connect в ASP.NET Core.
| омментировать | « ѕред. запись — дневнику — —лед. запись » | —траницы: [1] [Ќовые] |