Microsoft Kaizala - Secure Mobile Chat App |
 The 5 Best Mobile Security Applications for Android and iOS
The 5 Best Mobile Security Applications for Android and iOSDon't recycle or trade in your phone without completely wiping it. You may think that you do not need to stress over safety and security once the phone is not yours, but traces of info on the phone might be sufficient to leave you susceptible. Complete a complete wipe as well as reset the inner memory to factory setups before allowing the phone go.
Our phones are an expansion of our minds these days. Let's begin by taking a min to think concerning all of the points we use our phones for.
With all of that very personal and, sometimes, specialist details kept on our phones, you would certainly think we would certainly be better concerning safeguarding them. Whether it's out of lack of knowledge or not wanting to be interfered, too many individuals are taking safety faster ways that open them up to theft or privacy invasions.
Usage phone locks Making use of phone locks is the initial as well as primary point to maintain your. Many of the malware kinds find the rooted phones attractive as well as can strike any time extra easily when contrasted to unrooted Android gadgets. The most unconfident mobile phones are Android phones. You can make your cell phone personal by calling * 67 and also place your location code alongside the phone number of the individual you desire to call. You may assume that you do not have to worry regarding safety once the phone is not yours, however traces of details on the phone could be sufficient to leave you vulnerable.
What is the best secure messaging app? - NordVPN
Consider it like the lock on your front door. Is it most likely that somebody is going to go through and also take every little thing if you leave it open up? No. Is it way a lot more possible than if you simply transformed the lock? Yup. So why take the threat? If you're a hefty phone user, some phones have a choice of leaving it opened when you're inside your own house.
Establish multi-factor authentication If you have not set up multi-factor verification on every account that supplies it, stop checking out today and also go do it. multi-factor verification requires a code sent to you either by means of text, email, or an authenticator app in enhancement to a password to accessibility whatever program or account it's safeguarding.
Generally, as lots of actions as you can put in between your data as well as an assailant, the far better. Get major regarding encryption Many of the prominent smart devices featured built-in security check out this contrast graph to see just how different phones place for a series of safety issues. If you desire to add one more layer of file encryption on top of what your phone offers, specifically for internet website traffic, it's worth looking right into a high top quality Virtual Private Network (VPN).
Just download from dependable sources We recognize it's appealing to download and install that wonderful brand-new game, yet it deserves it to do your due diligence prior to downloading and install anything since it might come with greater than you prepared for. As a matter of fact, in summer season 2021 Avast scientists began tracking a form of malware that targets "fractured" (read: prohibited) video games.
10 Tips on Securing Your Android Phone
Avast researchers likewise discovered a malware called Bloody, Thief that steals not only cookies, usernames, passwords, as well as monetary info, yet additionally steals video game sessions. : just download from trusted resources as well as do a little research. Keep in mind: Anything you download and install from a questionable source might potentially put spyware on your phone.
Instead of automatically clicking "yes" on every app consent, take a minute to believe whether or not they really require that thing in order to function. As an example, Google Maps most definitely needs to know your area, however does that mind game really require to accessibility to your photos? Most likely not.
Phishing makes use of social design to obtain individuals to either click destructive links that set up malware or to willingly hand over their personal info, like passwords and logins. One method cybercriminals get you is by sending links that appear like they're from a person you know, but actually aren't. Utilize your finest judgment prior to clicking links (on your phone or in your browser) without verifying initially that they came from the person they say they're from.
 8 mobile apps that protect your phone's privacy, because no, you're not doing enough - CNET
8 mobile apps that protect your phone's privacy, because no, you're not doing enough - CNETWhile these 6 things could seem like a hassle, it only takes a couple of days to obtain into new, extra safe and secure practices. Our phones are an expansion of our brains these days.
The 4 Most Secure Phones for Privacy - MakeUseOf
Even setting up a solitary safety app can make the difference in between a risk-free device and a protection minefield. Exactly how do you know which apps are the appropriate ones for you?
The solution supplies customized protection features for PC, Mac, Android, and also i, Phone/i, Pad safeguard your devices where it's required most. Avast supplies both single-platform and also multi-platform options, letting you decide just how much protection you want over all of your devices. While the free variation of Avast blocks infections and spyware in real-time, the Costs version safeguards against ransomware, deceptive websites, password theft, and much more.
The system comes with a protected VPN service that allows for quick and also safe and secure web surfing on mobile devices. Little bit, Protector can likewise remotely locate, secure, as well as clean lost or stolen tools, and the vendor advertises a marginal effect on battery life. In enhancement, the application offers account privacy to confirm whether your e-mail account has been breached.
The application obstructs questionable applications, websites, and documents, in addition to allows users to control access to assigned applications. Kaspersky additionally allows individuals stop spyware checking telephone calls and messages. The application consists of anti-theft tools to shield smart phones and also information as well as uses device finding out to fight brand-new and emerging dangers.
The app shields its customers versus mobile risks like malware, adware, and also phishing before they do any type of harm to the device - secure phone app. Lookout also provides you 24/7 accessibility to ID Restoration Experts and also $1M Identification Theft Insurance coverage to aid recover and also restore your identification in situation your device goes missing or is swiped.
Norton Mobile Protection is a mobile tool security and also virus defense application that safeguards and cleanses devices from malware, infections, and various other threats. The application supplies innovative privacy defense, unsecure Wi-Fi detection, improved anti-theft attributes, important internet security, and also app screening. For customers looking to protect more devices, Norton Safety Deluxe safeguards up to 5 different PCs, Macs, mobile phones, as well as tablets with a single registration.
We profile the top vendors in the flexibility monitoring area, their crucial abilities, as well as our Base Line for every. Dan is a tech writer who blogs about Cybersecurity for Solutions Testimonial. He graduated from Fitchburg State University with a Bachelor's in Professional Writing. You can reach him at Latest articles by Daniel Hein (see all).
 Smart security system app - SecureConnect
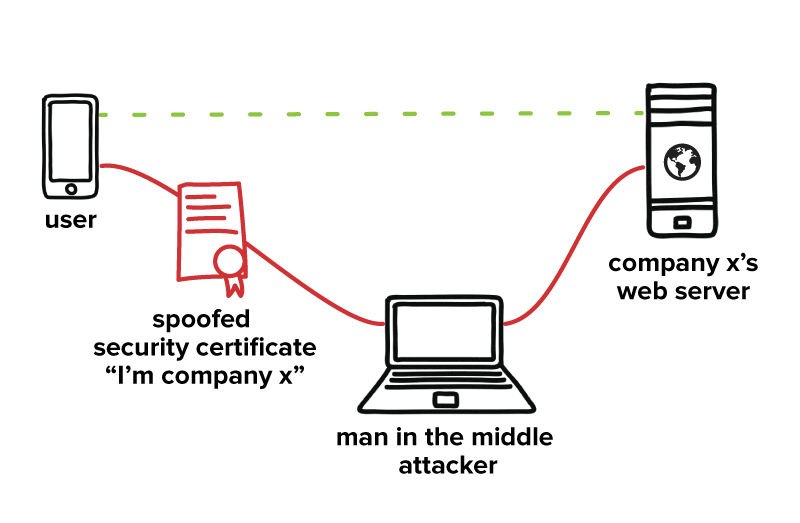
Smart security system app - SecureConnect A network hazard is triggered when the gadget is attached to a rogue gain access to factor. A sharp informs you that there might be a concern with a Wi-Fi network that you may be inclined to trust, so you can disconnect and also take various other preventive activities. An assailant uses a rogue access point that can make use of a tool vulnerability to link to a previously recognized Wi-Fi network.
Making Secure Voice Calls on Phone - Safe Online
g., a home cordless network showing as offered at an unanticipated area), or the tool will automatically link to one. If an enemy installs a rogue access factor, the attacker has the ability to run numerous kinds of susceptability scanners, and instead of needing to be physically inside the organization, can attack remotelyperhaps from a function area, nearby structure, parking area, or with a high-gain antenna, also from a number of miles away.
Stressed regarding your personal privacy when you're making use of applications on your cell phone or tablet computer? Right here's what you can do to protect your privacy prior to and also after you mount applications on your tool.
Prior to You Set up an Application Before you install an app, below's what you can do to far better secure your privacy: To minimize the threat of installing potentially damaging applications, download and install apps only from main app shops, such as your device's producer or operating system application shop. Additionally, study the designer before setting up an application.
Is the plan obscure regarding exactly how the app will share your data? If it is, or if you're not comfy with how your information might be shared, you may intend to discover another application. To get to details like your place or contacts or to obtain access to features like your camera and also microphone, apps require your authorization.
5 Must Have Android Security Apps To Protect Your ... - Gtricks
Pay close attention to the consents the app demands. For instance, does it really require to access your area or pictures to do its job? Your Privacy on Apps You Already Have If an application is currently on your phone or tablet computer, there are still some things you can do to safeguard your personal privacy: Most likely to your setups to evaluate the permissions to make certain the application doesn't have accessibility to info or features it does not require.
Take into consideration removing applications that need a lot of consents some applications demand lots of authorizations that aren't needed for the application's function. If an application requires accessibility to your place information to work, assume about limiting the access to just when the application is in usage.
If you aren't okay keeping that, use your e-mail address and an one-of-a-kind password to authorize in. Applications with obsolete software program might go to risk of being hacked. Shield your gadget from malware by installing application updates as quickly as they're launched. To avoid unnecessary information collection, if you're not utilizing an app, erase it.
With RingLeader CrowdVoice free international calling mobile app you can securely talk, message, meet, or hold a conference in one app? For only $15 per month, add three dedicated phone numbers in the US, Canada, or Mexico! Have a local presence from anywhere in the world. Sit on a beach in Spain and receive phone calls from your California office. encrypted phone number
Tokenization is an additional method of protecting payments that utilizes randomly generated tricks. Methods of protection, such as encryption as well as tokenization, only go as much as the tool they are utilized on and also the person who employs them.
ChatMail - Encrypted Communications

A person could succumb the act by giving their bank card details to a website they think to be trustworthy, but that is really set up merely as a system. Not upgrading your phone even more endangers the security of your mobile pay application. Every software application update includes sophisticated safety and security procedures made to protect you and also the contents of your phone.
Losing your phone is commonly the contemporary age's matching of losing your budget. If your phone finishes up in the incorrect hands, a huge selection of valuable info can be disseminated or exploited.
Nonetheless, a lot of smart devices have integrated protection protections of their own. Two-factor authentication is one the primary resources of this defense. With two-factor authentication, users can input a PIN alongside a fingerprint, face scan, or iris check. Some other kinds of two-factor, or multi-factor, authentication allow users to address a concern about themselves or offer an e-mail address or telephone number connected with the account.
More precautions to be taken consist of downloading and install tracking apps, securing your phone from another location, and also downloading apps that get rid of information if a phone is lost. The application "Find My Phone", for instance, is a valuable means to assist know where your phone has actually wound up when it's missing. An attribute located especially within Find My Phone might be even much more essential.
| Комментировать | « Пред. запись — К дневнику — След. запись » | Страницы: [1] [Новые] |






