√лубокий анализ антидетектных браузеров: браузерные отпечатки User-Agent |

ѕри посещении сайта через браузер серверу автоматически отправл€етс€ «идентификационный номер» — User Agent (UA). Ёта строка содержит ключевые детали об операционной системе, типе браузера, модели устройства и других параметрах. Ќапример:
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36
Ќа первый взгл€д безобидна€, эта строка €вл€етс€核心овым компонентом систем отслеживани€ пользователей и идентификации автоматизированных инструментов.
I. ¬ли€ние User Agent на управление мультиаккаунтами
1.–иски ассоциации аккаунтов
ѕри входе в несколько аккаунтов с одного устройства все они используют идентичный UA. ѕлатформы фиксируют это совпадение, что ведет к ограничени€м трафика или блокировкам. ѕримеры:
• росc-бордерные e-commerce платформы (например, Amazon) разрешают одному продавцу использовать только основной аккаунт; дл€ мультимагазинов требуютс€ независимые среды .
•—оцсети (например, Facebook) отслеживают активность маркетинговых аккаунтов с повтор€ющимс€ UA, что триггерит систему контрол€ рисков .
2.√лубина технической детекции
—айты анализируют не только UA, но и свыше 27 элементов браузерных отпечатков, включа€:
•Canvas Fingerprinting: аппаратные характеристики при рендеринге изображений.
•WebGL Fingerprinting: данные о драйверах видеокарты.
•ѕараметры окружени€: разрешение экрана, список шрифтов, часовой по€с .
⚠️ ≈сли изменить UA через расширение (например, User-Agent Switcher), но не синхронизировать €дро браузера или шрифты, платформы обнаружат аномалии.
II. ак достичь истинной изол€ции сред?
–ешение BitBrowser: комплексна€ работа с UA и отпечатками
»нструменты вроде BitBrowser создают отдельные виртуальные среды дл€ каждого аккаунта.
1.ƒинамическое соответствие UA и отпечатков
•јвтогенераци€ реалистичных UA, соответствующих реальным устройствам (Windows, macOS, iOS), с синхронизацией версий движка браузера.
ѕример: ѕри выборе Chrome 124 автоматически примен€ютс€ параметры WebKit, шум Canvas и др. .
2.ƒвухуровнева€ изол€ци€
•Ћокальна€ изол€ци€: отдельные cookies, локальное хранилище и кэш дл€ каждого аккаунта.
•—етева€ изол€ци€: прив€зка аккаунтов к статическим резидентным IP по схеме «1 аккаунт + 1 среда + 1 IP» .
3.»митаци€ поведени€ дл€ обхода детекции
•–андомизаци€ временных интервалов (паузы 2–5 секунд после действий).
•≈стественные траектории движени€ курсора дл€ маскировки автоматизации .
III. BitBrowser: профессиональное решение дл€ безопасности мультиаккаунтов
—реди инструментов BitBrowser выдел€етс€ трем€ технологи€ми:
1.ѕолноценна€ подмена отпечатков
• астомизаци€ UA с синхронизацией 32+ параметров (ќ—, разрешение экрана, €зык и т.д.).
•Ѕаза из 100,000+ реальных отпечатков устройств .
2. орпоративна€ безопасность
•End-to-End шифрование: конфигурации хран€тс€ локально (исключение утечек в облако).
•ƒвухфакторна€ аутентификаци€ (2FA): поддержка Google Authenticator .
3.»нструменты автоматизации
•RPA-сценарии: автозаполнение форм, распознавание капчи, scheduled-операции.
• оллабораци€ с ролевым доступом и аудит-логом действий .
«аключение
User Agent — лишь вершина айсберга браузерной идентификации. ѕростые расширени€ дл€ смены UA неэффективны против современных систем детекции. –ешени€ вроде BitBrowser обеспечивают фундаментальную защиту через изол€цию сред, симул€цию поведени€ и шифрование данных.
|
|
√лубокий анализ антидетектных браузеров: Ѕраузерный отпечаток ClientRects |

ѕочему кнопки страницы смещаютс€ на микроскопическую величину между вашими устройствами? —крыта€ сила отпечатка ClientRects
«амечали ли вы микроскопические смещени€ кнопок при открытии одной и той же веб-страницы на разных устройствах? Ёти, казалось бы, незначительные пиксельные вариации лежат в основе браузерного отпечатка ClientRects — одной из самых скрытных техник кросс-сайтового отслеживани€ на сегодн€шний день. »змер€€ точные координаты и размеры элементов веб-страницы (например, ширину кнопки, варьирующуюс€ всего на 0.01px) в сочетании с характеристиками аппаратного рендеринга, этот метод генерирует уникальный идентификатор устройства. ќн может посто€нно св€зывать вашу личность, даже после смены IP-адреса или очистки куки (cookies).
¬ сфере трансграничной электронной коммерции и управлени€ соцсет€ми это создание отпечатков стало причиной массовых блокировок аккаунтов по причине "св€зи устройств" (device association). “радиционные методы противосто€ни€ отслеживанию (такие как отключение JavaScript или режим инкогнито) здесь в основном неэффективны. ¬ этой статье мы разберем механизмы отпечатка ClientRects и способы защиты, раскрыва€, как вмешательство на системном уровне позвол€ет обеспечить по-насто€щему анонимный браузинг.
I. „то такое отпечаток ClientRects?
ClientRects описывает данные макета (позицию, размеры и пр.), предоставл€емые браузерными API, такими как getClientRects() и getBoundingClientRect(). ’от€ на первый взгл€д эти показатели кажутс€ обычными, они микронно различаютс€ на разных устройствах из-за конфигурации аппаратного обеспечени€, операционных систем, движков рендеринга шрифтов и разрешений экранов.
Ќапример:
•–азличные драйверы GPU могут отображать ширину одной и той же кнопки с разницей в 0.01px.
•–асхождени€ в библиотеках шрифтов могут сдвигать высоту текстовых элементов.
огда эти тонкие различи€ комбинируютс€ с параметрами вроде User Agent (UA) и часового по€са, они генерируют уникальные отпечатки устройств дл€ кросс-сайтового отслеживани€.
II. ќтслеживание св€зей: "ћастер-ключ" к у€звимости приватности
—крытность отпечатка ClientRects делает его краеугольным камнем дл€ св€зывани€ аккаунтов:
1.“очна€ идентификаци€ устройства: ƒаже при смене IP или очистке куки, сайты идентифицируют повторно использующеес€ устройство по стабильным паттернам ошибок рендеринга в данных ClientRects.
2. росс-платформенное отслеживание: ¬ электронной коммерции, если одним устройством управл€ет несколько магазинных аккаунтов, платформы могут вы€вить св€зь по посто€нству отпечатка ClientRects, что приводит к блокировкам.
3.ќбход традиционных защит: ќтключение JavaScript или использование VPN не способны полностью заблокировать сбор данных ClientRects, поскольку он эксплуатирует особенности поведени€ движков рендеринга на низком уровне.
III. ќграниченность традиционных мер противодействи€
—уществующие решени€ имеют критические недостатки:
•ќтключение JavaScript: Ќарушает функциональность сайтов, ухудша€ пользовательский опыт.
•–ежим инкогнито: Ѕлокирует только куки; не измен€ет вывод движка рендеринга.
•¬мешательство плагинов (например, Canvas Defender): ƒобавление случайного шума легко фильтруетс€ статистическими модел€ми.
ќсновна€ сложность: дл€ противодействи€ отпечатку ClientRects требуетс€ динамическое подмен€ющее воздействие (спуфинг), не нарушающее отображение страницы.
IV. ќптимальное решение
ѕротиводействие скрытности отпечатка ClientRects требует трехуровневой защиты:
1.ƒинамическое воздействие на рендеринг:
•¬недр€ет контролируемый "шум" в методы getClientRects() (например, колебани€ ширины/высоты в пределах ±0.1px), наруша€ стабильность отпечатка при сохранении визуальной целостности.
•ѕредлагает режимы "‘иксированный", "Ўум" и "ќтключено" дл€ различных сценариев.
2.–еконструкци€ отпечатка на уровне исходного кода:
•»змен€ет логику макета Chromium на уровне исходного кода, встраива€ динамические смещени€ на этапе первичных расчетов координат дл€ систематической фальсификации данных ClientRects.
• астомна€ сборка браузера устран€ет векторы обнаружени€.
3. омплексна€ изол€ци€ окружени€:
•¬ыделенна€ среда дл€ каждого аккаунта: »золирует IP, UA, часовой по€с, шрифты, Canvas-отпечаток и 50+ других параметров.
•јвтоматическа€ синхронизаци€ прокси-IP в соответствии с геолокацией предотвращает св€зывание через утечки IP.
•Ёмул€ци€ ќ— Windows/macOS/Linux дл€ операций корпоративного масштаба.
V. ќтраслевое применение и вызовы будущего
BitBrowser обеспечивает решение в реальных сценари€х:
•ќдно устройство — тыс€чи магазинов: ќтсутствие блокировок на Amazon/eBay/Wildberries и пр. из-за св€зывани€ аккаунтов.
•ѕредотвращение Ad Fraud: 99.7% уникальности отпечатков дл€ пакетного управлени€ рекламными аккаунтами.
•—овместимость с автоматизацией: Ќативна€ поддержка фреймворков Selenium/Puppeteer.
ѕочему BitBrowser?
¬ отличие от традиционных плагинов или режима инкогнито, BitBrowser реконструирует базовую логику рендеринга и изолирует окружени€ на системном уровне, обеспечива€ защиту от отпечатка ClientRects лидирующего в отрасли уровн€ без ущерба дл€ плавности рабочих процессов. [ѕосетите наш сайт], чтобы испытать по-насто€щему "один аккаунт – одно окружение" и исключить св€зывание. ѕолучите 10 посто€нных бесплатных профилей сразу!
|
|
ак продвигатьс€ на Amazon? ƒелимс€ различными методами продвижени€. |

Amazon, будучи мировым гигантом электронной коммерции, €вл€етс€ ключевым оплотом дл€ продавцов, расшир€ющих свой бизнес. ќднако в услови€х жесткой конкуренции на платформе рациональность стратегий продвижени€ и внимание к детал€м напр€мую определ€ют успех или провал. Ќиже представлены оптимизированные методы продвижени€ и ключевые аспекты, помогающие продавцам эффективно привлекать трафик, избега€ рисков.
I. ќсновные методы продвижени€ на Amazon
1. »нтегрированна€ реклама внутри платформы
• “оварные объ€влени€ (Sponsored Products): »спользуйте рекламу с оплатой за клик (CPC) дл€ отображени€ товаров в верхней части страниц результатов поиска, приоритезиру€ показ целевым пользовател€м.
• Ѕрендовые объ€влени€ (Sponsored Brands): ƒемонстрируйте логотипы брендов, несколько товаров и пользовательские заголовки дл€ усилени€ узнаваемости бренда. ѕодходит дл€ усто€вшихс€ брендов.
• ƒемонстрационные объ€влени€ (Sponsored Display): “аргетируйте пользователей на основе их поведени€, охватыва€ трафик внутри и вне Amazon (например, сайты партнеров, приложени€). »деально дл€ ремаркетинга.
2. —рочные акции дл€ стимулировани€ конверсий
• ћолниеносные сделки (Lightning Deals): —верхдисконтные акции длительностью 4-12 часов, привлекающие трафик из раздела "Today's Deals". ѕомогают быстро распродать складские запасы или подн€ть рейтинги.
• упоны (Coupons): Ќастраивайте дисконтные купоны дл€ привлечени€ ценочувствительных пользователей. ќтображаютс€ через метки на страницах результатов поиска дл€ увеличени€ CTR.
3. «аконное получение качественных отзывов
• ѕрограмма Vine: ѕриглашайте верифицированных Amazon обозревателей бесплатно тестировать товары дл€ получени€ доверенных ранних отзывов (доступно только дл€ продавцов с регистрацией бренда).
• »збегайте незаконного стимулировани€ отзывов: —трого запрещен обмен возвратов на отзывы. ¬место этого м€гко стимулируйте обратную св€зь через письма после заказа.
4. ѕривлечение внешнего трафика
• ћаркетинг в соцсет€х: ƒелитесь обучающими материалами по продуктам и информацией о скидках на платформах (Facebook, TikTok), направл€€ пользователей на ссылки Amazon.
• оллаборации с лидерами мнений (KOL): —отрудничайте с инфлюенсерами в нишевых област€х дл€ обзоров продуктов, использу€ доверие их подписчиков дл€ повышени€ конверсий.
5. ќптимизаци€ карточек товара: основа конверсии
• «аголовки включают ключевые слова (например, "наушники дл€ спорта с защитой от ”‘"), изображени€ содержат 6+ реалистичных снимков с разных ракурсов, акцентирующих сценарии использовани€ и детали.
• —труктурированные описани€: »спользуйте маркированные списки дл€ объ€снени€ характеристик, материалов и целевой аудитории, избега€ длинных абзацев.
II. 4 критических ловушки, которых следует избегать
1. ѕревышение бюджета и слепые ставки
• Ќовым продавцам следует начинать с автоматических объ€влений, переключа€сь на ручные кампании после накоплени€ данных дл€ корректировки ставок по высококонверсионным ключевым словам.
• ≈жедневно отслеживайте ACOS (дол€ рекламных расходов в выручке). ѕриостанавливайте и оптимизируйте кампании, если ACOS превышает маржу прибыли товара.
2. »гнорирование политики платформы
• —трого запрещены фиктивные заказы, манипул€ции с рейтингами и стимулирование отзывов. Ќарушени€ гроз€т приостановкой магазина.
• ѕри участии в акци€х убедитесь, что цены соответствуют требовани€м "минимальной цены за 30 дней", чтобы избежать отклонени€ за€вки.
3. –иски ассоциации аккаунтов при внешнем продвижении
• ѕри использовании соцсетей (например, Facebook) дл€ привлечени€ трафика распространена работа с мультиаккаунтами. ќднако платформы строго отслеживают ассоциации аккаунтов. ¬ход в несколько аккаунтов на одном устройстве легко провоцирует блокировки — используйте инструменты анти-обнаружени€ дл€ изол€ции сред.
4. ќтсутствие анализа данных
• ≈женедельно анализируйте "эффективность поисковых запросов" в отчетах по рекламе, добавл€€ негативные ключевые слова (например, низкоконверсионные термины) дл€ сокращени€ бесполезных расходов.
• —равнивайте конверсии внутреннего и внешнего трафика, приоритезиру€ каналы с более высоким ROI.
III. ак повысить эффективность продвижени€ на Amazon?
¬неплатформенное продвижение требует работы с матрицей аккаунтов (например, посты в группах Facebook, коллаборации с KOL), но ручное переключение между аккаунтами может спровоцировать ассоциацию. BitBrowser решает эту задачу комплексно:
• »золированна€ среда дл€ каждого аккаунта: Ќазначает уникальные IP и цифровые отпечатки браузера, исключа€ риски перекрестного входа.
• Ёффективность пакетного управлени€: ќдновременное управление постами и сообщени€ми в нескольких аккаунтах, экономи€ 80% ручного труда.
• Ѕезопасна€ командна€ работа: ѕоддержка уровней разрешений дл€ субаккаунтов, позвол€юща€ параллельные операции между отделами продаж и рекламы.
Ќезависимо от инвестиций в продвижение, соответствие правилам об€зательно. лючева€ ценность BitBrowser — максимальна€ эффективность работы с трафиком через матрицы соцсетей при обеспечении безопасности.
«аключение:
ѕродвижение на Amazon требует двойной стратегии "реклама внутри платформы + внешний трафик", строгого соблюдени€ правил и работы на основе данных. ќсобенно дл€ продавцов, завис€щих от трафика соцсетей, безопасное управление мультиаккаунтами фундаментально дл€ устойчивого роста. »спользование инструментов и фокус на детал€х гарантируют долгосрочную прибыльность в услови€х жесткой конкуренции.
|
|
ѕочему вам необходимо установить пиксель Facebook в своем магазине Shopify? |

Facebook Pixel (Meta Pixel) — это фрагмент кода отслеживани€, встраиваемый на сайт дл€ записи действий пользователей (покупки, добавление в корзину, регистрации и т.д.) и передачи данных в рекламную систему Facebook. ƒл€ владельцев независимых интернет-магазинов его ключевые ценности заключаютс€ в следующем:
1. “очна€ оптимизаци€ рекламы: Ќа основе данных о поведении пользователей автоматически таргетирует аудитории с высокой конверсией, снижа€ цену за приобретение;
2. ћощный ремаркетинг: јвтоматически показывает рекламу пользовател€м, которые не завершили действие (например, добавили товар в корзину, но не оплатили), возвраща€ потенциальные заказы;
3. ѕрин€тие решений на основе данных: јнализирует ROI рекламы, вы€вл€ет высокоэффективные рекламные каналы и предотвращает потерю бюджета.
„етыре шага дл€ установки Shopify Pixel (верси€ 2025 года)
Ўаг 1: —оздание рекламного аккаунта Facebook
• ѕерейдите на https://business.facebook.com/, зарегистрируйтесь с помощью личного аккаунта и подтвердите бизнес-информацию (требуетс€ бизнес-лицензи€ или удостоверение личности законного представител€).
Ўаг 2: √енераци€ кода Pixel
• ¬ Meta Business Suite нажмите 【»сточники данных】→【ѕиксели】→【—оздать новый пиксель】. ѕрисвойте им€ пикселю (рекомендуетс€ указать название магазина + дату) и отметьте "ѕроверка домена" (введите домен вашего магазина Shopify).
Ўаг 3: Ќастройка в панели администратора Shopify
1. ¬ойдите в панель администратора Shopify, перейдите в 【»нтернет-магазин】→【Ќастройки】;
2. ¬ поле "Facebook Pixel ID" вставьте скопированный идентификатор пиксел€;
3. Ќажмите 【—охранить】 дл€ завершени€ базовой интеграции.
Ўаг 4: ѕроверка и настройка событий
• ѕроверка установки: ”становите расширение Chrome "Meta Pixel Helper". ѕосетите страницу вашего магазина; если расширение отображает зеленый значок, настройка прошла успешно;
• ќтслеживание ключевых событий: ¬ ћенеджере событий Facebook активируйте 8 стандартных событий, таких как "Purchase", "AddToCart", и расставьте приоритеты (например, Purchase > AddToCart > Registration > PageView).
—овет по устранению неполадок: ѕри дублировании данных проверьте, не продублирован ли код пиксел€ в коде темы Shopify (theme.liquid) или на странице оформлени€ заказа — при обнаружении удалите дубликаты.
ѕродвинутые методы: ”правление несколькими пиксел€ми и безопасность данных
• ќдин магазин, несколько пикселей: ƒл€ отслеживани€ разных кампаний (например, запуск нового продукта/празднична€ распродажа) добавьте несколько пользовательских кодов пикселей через 【Ќастройки】→【—обыти€ клиентов】 в Shopify. Ќе забудьте вручную удалить код `fbq('track', 'PageView');` по умолчанию во избежание конфликтов;
• ”силение с помощью Conversions API (CAPI): ”становите приложени€ вроде "Omega Facebook Pixel" из магазина приложений Shopify. ѕосле прив€зки Access Token надежность данных повышаетс€ за счет server-to-server соединени€ (особенно важно при ограничени€х конфиденциальности iOS).
«ачем вам нужен BitBrowser?
ѕри управлении несколькими магазинами, рекламными аккаунтами или командной работе традиционные браузеры легко провоцируют срабатывание систем контрол€ риска Facebook, привод€ к ограничени€м рекламных аккаунтов. BitBrowser предлагает профессиональное решение:
1. »золированные браузерные среды: —оздает уникальные цифровые отпечатки браузера (изолированные Cookies, User-Agent, часовой по€с) дл€ каждого магазина/рекламного аккаунта, предотвраща€ ассоциацию и блокировки;
2. јудит командных операций: ѕоддерживает управление правами субаккаунтов (например, сотрудники отдела эксплуатации работают только с пиксел€ми, финансы — только просматривают отчеты) с отслеживаемыми журналами операций;
3. јвтоматизированные скрипты: јвтоматизирует рутинные задачи, такие как проверка работоспособности пикселей и экспорт данных, повыша€ операционную эффективность.
»деально дл€: јгентств, управл€ющих магазинами нескольких клиентов | Ѕрендов с мультисайтовой структурой | –екламных команд с распределенной работой.
ƒанные — это кислород вашего независимого магазина, а пиксель — кислородна€ трубка: от точного таргетинга аудитории до восстановлени€ потер€нных заказов каждый шаг зависит от его точной обратной св€зи. –азверните свой пиксель, использу€ приведенные выше шаги, и усильте безопасность данных с помощью BitBrowser, чтобы гарантировать, что ваш рекламный бюджет действительно "тратитс€ там, где это необходимо".
|
|
BitBrowser или Dicloak: что лучше дл€ управлени€ несколькими аккаунтами? |
¬ сфере цифрового маркетинга, электронной коммерции, управлени€ социальными медиа и более широких интернет-бизнесов эффективное и безопасное «управление несколькими аккаунтами» уже не €вл€етс€ вариантом, а €вл€етс€ ключом к успеху или неудаче. — развитием технологий детектировани€ св€зи между аккаунтами на крупных платформах традиционные методы управлени€ сталкиваютс€ с неprecedentными вызовами — посто€нные блокировки аккаунтов, низка€ эффективность операций, отсутствие гарантий безопасности данных и другие проблемы. »менно в таком контексте по€вилс€ браузер с антидетекцией, ставший «секретным оружием» цифровых специалистов.
Ќа рынке существует множество браузеров дл€ предотвращени€ св€зи между аккаунтами, среди которых BitBrowser и Dicloak безусловно €вл€ютс€ двум€ наиболее известными продуктами. ќба они направлены на предоставление независимой и чистой среды браузера дл€ безопасного управлени€ несколькими аккаунтами. Ќо сталкива€сь с продуктами с разными функци€ми и разными приоритетами, операторы часто испытывают трудности с выбором. ¬ этой статье мы проведем глубокое сравнение этих двух инструментов, учитыва€ реальные потребности в управлении несколькими аккаунтами, чтобы помочь вам пон€ть, какой из них лучше подходит дл€ использовани€ в коммерческих операци€х.

I. ∆есткие требовани€ к управлению несколькими аккаунтами
ќсновные потребности в управлении несколькими аккаунтами заключаютс€ в «изол€ции» и «эффективности». Ќезависимо от того, речь идет о нескольких рекламных аккаунтах в партнерском маркетинге, управлении несколькими магазинами в кросс-бордерной электронной коммерции, матричной промоции в социальных медиа или необходимости в веб-скреппинге и анализе данных — во всех случа€х требуетс€ имитаци€ среды «нескольких независимых пользователей».
—ложности в основном заключаютс€ в следующих пунктах:
1. —в€зь по отпечатку браузера: ѕлатформы собирают р€д данных о пользователе — операционную систему, шрифты, разрешение экрана, холст Canvas, видеокарту WebGL, аудио, часовой по€с и другие — и создают уникальный «цифровой отпечаток». ≈сли несколько аккаунтов вход€т в систему с использованием одинаковых данных отпечатка, платформа легко может их идентифицировать и заблокировать за св€зь между аккаунтами.
2. ”течка IP-адреса: »спользование одного и того же IP-адреса дл€ нескольких аккаунтов €вл€етс€ наиболее пр€мой причиной блокировки из-за св€зи между аккаунтами.
3. —овместна€ работа в команде и безопасность данных: ѕри работе команды с несколькими аккаунтами ключом к обеспечению эффективности операций и безопасности информации €вл€етс€ безопасное обмен данными аккаунтов, гибкое распределение прав доступа и реальное синхронизаци€ данных.
4. Ёффективность операций: ѕри резком увеличении количества аккаунтов ручна€ смена аккаунтов и повтор€ющиес€ операции значительно трат€т человеческие ресурсы и врем€.
»менно дл€ решени€ этих проблем по€вились такие инструменты дл€ предотвращени€ св€зи между аккаунтами, как BitBrowser. ќн создает независимые профили браузера, предоставл€€ каждому аккаунту уникальную рабочую среду, котора€ не вли€ет на другие аккаунты.
II. „то такое BitBrowser?
BitBrowser — это профессиональный браузер с антидетекцией китайского производства, разработанный дл€ предоставлени€ эффективных и безопасных решений дл€ глобальных потребностей в управлении несколькими аккаунтами. ќн основан на глубоком развитии попул€рных движков Google и Firefox и специализируетс€ на обеспечении 100%-й независимости между окнами браузера «на физическом уровне».
ќсновные возможности BitBrowser:
»митаци€ чистого отпечатка: BitBrowser может имитировать и настраивать более дес€ти параметров отпечатка, включа€ UserAgent, холст Canvas, видеокарту WebGL, часовой по€с Timezone, географические координаты Geo и другие, гарантиру€ каждому окну браузера уникальный цифровой идентификатор.
Ёффективное управление несколькими аккаунтами: ÷ентрализованное управление аккаунтами различных платформ — электронной коммерции, социальных медиа, рекламного маркетинга и других. ѕользователи могут настроить дл€ каждого аккаунта отдельный прокси-IP в соответствии с своими потребност€ми, обеспечива€ чистоту и стабильность сценариев входа в систему.
—овместна€ работа в команде и распределение прав: ѕоддержка группировки пользователей, гибкое распределение аккаунтов и прав доступа, массовое импорт/экспорт, авторизаци€, обмен данными и другие операции. ƒанные синхронизируютс€ в реальном времени в облаке, что значительно повышает эффективность работы команды.
ћощна€ автоматизированна€ экосистема: BitBrowser имеет такие функции, как автоматизаци€ браузера RPA, система синхронизации, LocalAPI и другие, поддерживающие массовые автоматизированные операции с несколькими аккаунтами. ƒл€ международного маркетинга, требующего масштабных и частых операций, это мощный инструмент дл€ повышени€ эффективности.
BitBrowser стремитс€ создать функционально богатую экосистему. ак утверждает разработчик, комбинаци€ «BitBrowser + облачный телефон» предоставл€ет не только защиту от св€зи между аккаунтами на уровне браузера, но и решени€ дл€ мобильных устройств в виде облачных телефонов, обеспечива€ поддержку различных типов операционных потребностей.
III. „то такое Dicloak?
Dicloak — другой браузер с антидетекцией, который завоевал признание части пользователей благодар€ своей простой и удобной интерфейсу и передовым техническим функци€м. ќн акцентует внимание на удобстве использовани€, стрем€сь позволить новичкам или пользовател€м без технического опыта легко управл€ть несколькими аккаунтами.

ќсновные особенности Dicloak:
”добный интерфейс дл€ пользовател€: јкцент на минималистичном дизайне, упрощенные рабочие процессы, использование не требует сложных профессиональных знаний.
Ќастройка параметров отпечатка: ѕредоставление сложной настройки более чем 50 параметров отпечатка, позвол€юща€ пользовател€м проводить детальную настройку.
—овместна€ работа в команде: Ќаличие гибких прав доступа и функций уведомлений дл€ членов команды, удобное безопасное обмен и управление профил€ми в команде.
”правление искусственным интеллектом: ќбъ€вл€етс€ использование »» дл€ автоматизированного сбора данных и просмотра, направленного на повышение эффективности и точности выполнени€ задач.
”сили€ Dicloak по улучшению пользовательского опыта заслуживают признани€. ≈го программа пожизненного бесплатного использовани€ привлекает временных пользователей или пользователей небольшого масштаба.
|
|
–еклама в Facebook или TikTok: что выбрать дл€ арбитража трафика? |

¬ мире арбитража трафика выбор правильной рекламной платформы играет ключевую роль в успехе кампаний. ƒве самые попул€рные платформы на сегодн€ — это Facebook Ads и TikTok Ads. Ќо что выбрать? ƒавайте разберемс€.
јудитори€
•–еклама на Facebook (Facebook Ads):
•Facebook существует давно и охватывает аудиторию разных возрастов, интересов и демографии.
•≈сли ваша целева€ аудитори€ старше 25 лет, Facebook может быть лучшим выбором.
•–еклама в TikTok (TikTok Ads):
•TikTok — это платформа дл€ более молодой аудитории, в основном в возрасте от 13 до 24 лет.
•≈сли ваш продукт ориентирован на молодежь, TikTok — отличный выбор.
Ѕонус: ѕолучите 5 бесплатных виртуальных карт от FlexCard (сервис с виртуальными картами дл€ арбитража трафика и личных покупок) по промокоду Bitbrowser. «арегистрируйтесь по этой ссылке, предоставьте промокод службе поддержки и получите карты бесплатно.
‘орматы рекламы
•–еклама на Facebook (Facebook Ads):
•Facebook предлагает множество форматов рекламы: изображени€, видео, карусели, слайд-шоу и другие.
•Ёти форматы позвол€ют гибко подходить к креативу и адаптировать его под разные цели кампаний.
•–еклама в TikTok (TikTok Ads):
•ќсновной формат рекламы в TikTok — короткие видео. ¬ажно про€вл€ть креативность и создавать запоминающийс€ контент.
•TikTok поддерживает челленджи и хештеги, что позвол€ет рекламе становитьс€ вирусной.
“аргетирование
- •–еклама на Facebook (Facebook Ads):
•” Facebook мощные инструменты таргетировани€, позвол€ющие настраивать рекламу по интересам, поведению, демографии и другим параметрам.
•Ёто дает возможность очень точно охватить нужную аудиторию.
•–еклама в TikTok (TikTok Ads):
•“аргетирование TikTok также впечатл€ет, но оно не такое детализированное, как у Facebook.
•“ем не менее, TikTok активно работает над улучшением своих инструментов таргетировани€, и уже можно настраивать рекламу по интересам, демографии и поведению.
—тоимость
•–еклама на Facebook (Facebook Ads):
•—тоимость рекламы на Facebook может варьироватьс€ в зависимости от аудитории, формата объ€влени€ и конкуренции в вашей нише.
• ак правило, это более дорога€ платформа по сравнению с TikTok, особенно в попул€рных нишах.
•–еклама в TikTok (TikTok Ads):
•TikTok в насто€щее врем€ предлагает более низкие расходы на рекламу, поскольку платформа все еще развиваетс€, и конкуренци€ здесь не така€ высока€, как на Facebook.
•Ёто отлична€ возможность получить больше трафика за меньшие деньги.
Ёффективность
•–еклама на Facebook (Facebook Ads):
•Facebook хорошо подходит дл€ продуктов, которые требуют объ€снени€ и более сложного подхода.
•Ѕлагодар€ разнообразию форматов можно детально презентовать продукт и его преимущества.
•–еклама в TikTok (TikTok Ads):
•TikTok идеален дл€ продуктов, которые можно продвигать через развлекательный контент.
•≈сли ваш продукт визуально привлекателен и легко воспринимаетс€ в видеоформате, TikTok может дать отличные результаты.
јналитика
•–еклама на Facebook (Facebook Ads):
•Facebook предоставл€ет мощные инструменты аналитики, позвол€ющие детально отслеживать результаты рекламных кампаний и корректировать их в реальном времени.
•–еклама в TikTok (TikTok Ads):
•TikTok также предлагает аналитику, но она не столь детализирована, как у Facebook. “ем не менее, основные метрики (показы, клики, конверсии) отслеживать можно.
«аключение
¬ыбор между рекламой на Facebook и рекламой в TikTok зависит от вашей целевой аудитории, бюджета и типа продукта. ≈сли ваша аудитори€ старше и вы готовы инвестировать в более дорогие и детально настраиваемые рекламные кампании, Facebook может стать лучшим выбором. ≈сли ваш продукт ориентирован на молодых людей и вы хотите экспериментировать с креативным видеоконтентом, TikTok — отличный вариант.
¬ идеале, дл€ максимальной эффективности, стоит протестировать обе платформы и определить, кака€ из них обеспечивает больше конверсий при оптимальных бюджетных затратах.
”дачи в арбитраже трафика!
|
|
ќшибка ЂЌевозможно загрузить контентї на Reddit в 2025 году: решени€ |
≈сли вы ищете решени€ дл€ таких сообщений, как "ошибки загрузки контента Reddit" или "проблемы с серверами Reddit",本指南 объ€снит причины и способы устранени€ — включа€ то, как использовать BitBrowser в сочетании с резидентскими прокси дл€ безопасного обхода ограничений Reddit.
„то означает сообщение "ћы столкнулись с ошибкой сервера" на Reddit?
 /img-website.bitbrowser.net/uploads/small_image_0a509370d5.png" target="_blank">https://img-website.bitbrowser.net/uploads/small_image_0a509370d5.png 500w, https://img-website.bitbrowser.net/uploads/medium_image_0a509370d5.png 750w, https://img-website.bitbrowser.net/uploads/large_image_0a509370d5.png 1000w" width="1000" />
/img-website.bitbrowser.net/uploads/small_image_0a509370d5.png" target="_blank">https://img-website.bitbrowser.net/uploads/small_image_0a509370d5.png 500w, https://img-website.bitbrowser.net/uploads/medium_image_0a509370d5.png 750w, https://img-website.bitbrowser.net/uploads/large_image_0a509370d5.png 1000w" width="1000" />Ёто сообщение обычно по€вл€етс€ по следующим причинам:
- —ервера Reddit перегружены или наход€тс€ в режиме технического обслуживани€
- ¬ременные сбои, вызванные пиковым нагрузкой на трафик
- ¬аше сетевое соединение, устройство или браузер не могут корректно загрузить данные
- —еть доставки контента (CDN) Reddit не отвечает
⚠️ ≈сли вы видите сообщение "ћы столкнулись с ошибкой сервера Reddit («аблокировано)", не стоит паниковать. Ёто не об€зательно означает, что ваша учетна€ запись была приостановлена — обычно это временна€ проблема или проблема, св€занна€ с вашим регионом.
"¬ас заблокировала система сетевой безопасности"
ѕример сообщени€:
"¬ас заблокировала система сетевой безопасности. „тобы продолжить, войдите в свою учетную запись Reddit или используйте токен разработчика."
“акие блокировки возникают, когда Reddit сочтает ваше сетевое соединение подозрительным. ¬ 2025 году Reddit усилил свои защитные меры дл€ решени€ следующих ситуаций:
- —пам и автоматизированное сбор данных
- ƒе€тельность через дата-центровые прокси
- јномальные отпечатки браузера
ѕосле блокировки простое обновление страницы не решит проблему.
ѕочему прокси часто вызывают такие блокировки
Reddit поддерживает черный список злоупотребл€ющих IP-адресов. ƒаже платные премиум-прокси часто имеют помеченные общие IP-адреса.
–езультат: даже законные пользователи могут быть заблокированы.
ак безопасно обойти блокировки Reddit
Ќиже приведены действительно эффективные методы в 2025 году:
✅ »спользуйте BitBrowser (браузер дл€ обхода детектировани€) → √енерируйте естественные отпечатки браузера
✅ —очетайте его с резидентскими прокси → ”лучшайте репутацию IP-адреса
✅ чередуйте отпечатки браузера + IP-адреса → »збегайте повторного использовани€ той же комбинации
✅ »збегайте бесплатных прокси и дата-центровых прокси → ¬ысокий риск
👉 — помощью BitBrowser ваши сессии будут имитировать сессии насто€щих пользователей, позвол€€ вам обойти блокировки Reddit без утечки персональных данных.
—ообщение "Reddit заблокировано": „то это на самом деле означает
—ообщение "Reddit заблокировано" не всегда означает приостановление учетной записи. ќно может указывать на:
- Reddit заблокирован вашей страной или провайдером интернет-услуг (ISP)
- онкретный IP-адрес временно добавлен в черный список
- ѕомешение работы брандмауэрами или расширени€ми браузера
- ¬нутренние сбои в самой платформе Reddit
✅ „тобы проверить, попробуйте переключитьс€ на другое сетевое соединение (между Wi-Fi и мобильными данными), используйте BitBrowser + резидентские прокси или проверьте статус на redditstatus.com и Downdetector (сайте дл€ отслеживани€ сбоев).
"ѕроизошла ошибка, попробуйте позже"
Ёто сообщение обычно св€зано с проблемами синхронизации данных Reddit. ќно может по€витьс€ в следующих сценари€х:
- ѕри загрузке определенных сообществ Reddit ( сабреддитов)
- ѕри получении новых постов или комментариев
Ѕыстрые способы устранени€:
- ќбновите страницу
- ѕерезапустите приложение
- ќчистите кэш и куки
- ѕереключитесь на другое сетевое соединение
"ќшибка загрузки контента Reddit"
Ёта проблема часто возникает у пользователей мобильных устройств (iOS/Android). ѕричины включают:
- »збыточную нагрузку на серверы
- Ќестабильное сетевое соединение
–ешени€:
- ѕереустановите приложение Reddit
- ѕереключитесь на мобильную веб-версию
- »спользуйте BitBrowser с стабильными резидентскими прокси дл€ бесперебойного подключени€
Ѕыстрый список дл€ устранени€ неполадок
≈сли Reddit работает некорректно, выполните следующие шаги:
- ќбновите страницу/перезапустите приложение
- ѕопробуйте использовать другой браузер или устройство
- ѕерейдите на redditstatus.com, чтобы проверить статус серверов
- ¬ременно отключите прокси или расширени€ браузера
- ѕереключитесь между Wi-Fi и мобильными данными
- »спользуйте BitBrowser + резидентские прокси
- ѕопробуйте получить доступ к old.reddit.com (лЄгкий интерфейс)
—ейчас ли наблюдаетс€ сбой в работе Reddit?
—бои в работе Reddit обычно временные или региональные.
- ≈сли другие пользователи сталкиваютс€ с той же проблемой → Ёто глобальный сбой Reddit.
- ≈сли только вы сталкиваетесь с проблемой → Ёто локальна€ проблема (устройство, сеть или блокировка IP-адреса).
»тог
—ообщени€ об ошибках Reddit следующего типа:
- "ћы столкнулись с ошибкой сервера"
- "Reddit заблокировано"
- "ѕроизошла ошибка, попробуйте позже"
- "ќшибка загрузки контента Reddit"
…обычно €вл€ютс€ временными проблемами, и их можно устранить.
👉 ƒл€ стабильного и анонимного просмотра BitBrowser + резидентские прокси остаютс€ лучшим решением в 2025 году:
- Ќадежный доступ
- »збегание блокировки
- ѕолна€ защита конфиденциальности
🔥 —пецпредложение: »спользуйте промокод BITBROWSER, чтобы получить скидку 10% при покупке BitBrowser
|
|
ак обойти Cloudflare в 2025 году: проверенные методы автоматизации и парсинга |
Cloudflare — ведущий поставщик веб-инфраструктуры и услуг безопасности, обеспечивающий работу миллионов веб-сайтов по всему миру с помощью быстрых, безопасных и надежных сервисов. ’от€ он защищает сайты от DDoS-атак, ботов и вредоносного трафика, его анти-бот меры также могут блокировать легитимные автоматизированные workflows, такие как веб-скрейпинг и сбор данных.
¬ этом руководстве мы рассмотрим, как работает Cloudflare, почему он блокирует ботов, и проверенные методы дл€ безопасного и эффективного обхода его защитных механизмов в 2025 году.
„то такое Cloudflare?
Cloudflare функционирует как Content Delivery Network (CDN), кэширу€ контент в глобальной сети дл€ повышени€ скорости загрузки сайтов и уменьшени€ задержек. ѕомимо производительности, он предоставл€ет:
- «ащиту от DDoS-атак
- ¬еб-приложение Firewall (WAF)
- ”правление ботами
- DNS-сервисы
- «ащиту от ботов и CAPTCHA
WAF от Cloudflare провер€ет каждый вход€щий запрос и фильтрует вредоносный или автоматизированный трафик. Ёто делает его высокоэффективным в остановке скрейперов и ботов, но также создает проблемы дл€ автоматизированных workflows.
ак работают анти-бот механизмы Cloudflare
јнти-бот система Cloudflare использует несколько уровней дл€ обнаружени€ автоматической активности:
- TLS-отпечатки (TLS Fingerprints) – ѕровер€ет, как клиенты выполн€ют TLS-рукопожати€. Ќебраузерные клиенты часто имеют необычные сигнатуры.
- јнализ HTTP-запросов – ѕровер€ет заголовки, куки и строки user-agent. Ѕоты часто используют стандартные или подозрительные конфигурации.
- JavaScript-отпечатки – «апускает JS в браузере клиента дл€ обнаружени€ ќ—, шрифтов, расширений и других характеристик.
- ѕоведенческий анализ – ќтслеживает похожие на человеческие взаимодействи€, включа€ движени€ мыши, паттерны кликов и врем€ запросов.
Cloudflare использует два основных режима проверки на человечность:
- ¬сегда показывать проверку (Always Show Human Verification) – “ребует CAPTCHA при каждом первом посещении (используетс€ на таких сайтах, как StackOverflow).
- јвтоматическа€ проверка (Automated Human Verification) – ѕровер€ет подозрительный трафик с помощью невидимых JS-тестов, переход€ к CAPTCHA только при необходимости.
ак Cloudflare работает за кулисами
огда вы обращаетесь к сайту, защищенному Cloudflare:
- лиент обмениваетс€ зашифрованными POST-запросами с серверами Cloudflare.
- Cloudflare оценивает отпечатки браузера и системы.
-
”спешна€ проверка устанавливает куки
cf_clearance, предоставл€€ доступ на срок до 15 дней.
јвтоматизированные боты, использующие стандартные HTTP-клиенты, такие как requests, обычно получают ошибку 403 Forbidden. »нструменты дл€ автоматизации браузеров, такие как Playwright, могут достичь шага проверки, но все равно требуют имитации человеческого поведени€ дл€ обхода CAPTCHA.
ѕодходы к обходу Cloudflare
1. ѕр€мой доступ к IP сервера
ѕолный обход Cloudflare включает определение исходного IP сайта с помощью инструментов истории DNS. ќграничени€: большинство серверов принимают запросы только из диапазона IP-адресов Cloudflare, что делает этот метод ненадежным.
2. ќpen-source решени€ (солверы)
Ѕиблиотеки, такие как cloudscraper, cfscrape и humanoid, пытаютс€ решить challenges Cloudflare. Ќедостатки:
- –едко обновл€ютс€
- Ќе справл€ютс€ с частыми обновлени€ми Cloudflare
- ќграниченна€ масштабируемость
3. »нструменты автоматизации с возможност€ми обхода
Ќаиболее эффективный подход — использование профессиональных платформ автоматизации, которые:Bitbrowser
- ќбрабатывают JavaScript-challenges
- ѕодделывают отпечатки браузера
- јвтоматически решают CAPTCHA
- »митируют человеческие взаимодействи€
- –отаруют прокси дл€ разнообрази€ IP
ѕремиум-варианты включают Web Unlocker от Bright Data и Browser API.
–ешени€ на Python дл€ обхода Cloudflare
Camoufox (Open-Source)
јнти-детект браузер на Python, построенный на Playwright. ќбрабатывает Turnstile CAPTCHA и обеспечивает человеко-подобную автоматизацию.
from camoufox.sync_api import Camoufox from playwright.sync_api import TimeoutError with Camoufox(headless=False, humanize=True, window=(1280, 720)) as browser: page = browser.new_page() page.goto("https://www.scrapingcourse.com/cloudflare-challenge") page.mouse.click(210, 290) # Click Turnstile try: page.locator("text=You bypassed the Cloudflare challenge! :D").wait_for() success = True except TimeoutError: success = False browser.close() print("Cloudflare Bypassed:", success)
SeleniumBase
ѕрофессиональный Python toolkit, использующий undetected-chromedriver дл€ автоматического обхода Cloudflare:
from seleniumbase import Driver driver = Driver(uc=True) driver.uc_open_with_reconnect("https://www.scrapingcourse.com/cloudflare-challenge", 4) driver.uc_gui_click_captcha() driver.wait_for_text("You bypassed the Cloudflare challenge! :D", "main") driver.quit()
ћасштабирование обхода Cloudflare
Open-source решени€ ограничены в production из-за:
- ¬ысокого потреблени€ ресурсов в headless-браузерах
- Ќестабильности при обновлени€х
- ќтсутстви€ официальной поддержки
ѕремиум-решени€:
- Web Unlocker – »звлекает HTML из-за анти-бот стен, обрабатывает ограничени€ по частоте запросов, отпечатки и CAPTCHA.
- Browser API – ќблачна€ автоматизаци€ браузеров, интегрируетс€ с Playwright, Puppeteer, Selenium и автоматически мен€ет IP.
»спользование Web Unlocker
import requests BRIGHT_DATA_API_KEY = "<YOUR_API_KEY>" headers = {"Authorization": f"Bearer {BRIGHT_DATA_API_KEY}", "Content-Type": "application/json"} data = {"zone": "web_unlocker", "url": "https://www.scrapingcourse.com/cloudflare-challenge", "format": "raw"} response = requests.post("https://api.brightdata.com/request", json=data, headers=headers) html = response.text print("Cloudflare Bypassed:", "You bypassed the Cloudflare challenge! :D" in html)
»спользование Browser API
from playwright.sync_api import sync_playwright, TimeoutError BRIGHT_DATA_API_CDP_URL = "<YOUR_CDP_URL>" with sync_playwright() as p: browser = p.chromium.connect_over_cdp(BRIGHT_DATA_API_CDP_URL) page = browser.new_page() page.goto("https://www.scrapingcourse.com/cloudflare-challenge") try: page.locator("text=You bypassed the Cloudflare challenge! :D").wait_for() success = True except TimeoutError: success = False browser.close() print("Cloudflare Bypassed:", success)
«аключение
ќбход Cloudflare сложен, но достижим. »нструменты с открытым исходным кодом работают дл€ небольших проектов, в то врем€ как премиум-решени€, такие как Web Unlocker и Browser API, обеспечивают масштабируемость, надежность и поддержку. Ќезависимо от того, используете ли вы автоматизацию на Python или облачные сервисы, понимание защитных механизмов Cloudflare €вл€етс€ ключом к успешному веб-скрейпингу и автоматизации в 2025 году.
|
|
5 лучших сайтов дл€ покупки аккаунтов Discord в 2025 году |
’отите приобрести аккаунт Discord? »зучите этот список проверенных платформ, предлагающих верифицированные, старые и Nitro-аккаунты с быстрой доставкой и защитой покупател€.
Discord давно перерос простую чат-платформу. ≈го широко используют геймеры, создатели контента, бизнес и команды. —тарые или верифицированные аккаунты Discord дают €вные преимущества — они вызывают больше довери€, предоставл€ют доступ к эксклюзивным серверам и позвол€ют обходить некоторые ограничени€ платформы. ƒл€ пользователей, которым нужно управл€ть сообществами, вступать в закрытые группы или быстро развиватьс€, эти аккаунты выдел€ютс€.
 /img-website.bitbrowser.net/uploads/small_image_ff42590d36.png" target="_blank">https://img-website.bitbrowser.net/uploads/small_image_ff42590d36.png 500w, https://img-website.bitbrowser.net/uploads/medium_image_ff42590d36.png 750w, https://img-website.bitbrowser.net/uploads/large_image_ff42590d36.png 1000w" width="1000" />
/img-website.bitbrowser.net/uploads/small_image_ff42590d36.png" target="_blank">https://img-website.bitbrowser.net/uploads/small_image_ff42590d36.png 500w, https://img-website.bitbrowser.net/uploads/medium_image_ff42590d36.png 750w, https://img-website.bitbrowser.net/uploads/large_image_ff42590d36.png 1000w" width="1000" />—оздание нового аккаунта Discord не дает мгновенной репутации, а его раскрутка с нул€ требует много времени и усилий. »менно поэтому многие ищут, как купить аккаунт Discord, или удивл€ютс€, почему другие уже это делают. Ёто позвол€ет сэкономить врем€, избежать ограничений и ускорить рост.
счастью, существуют сторонние маркетплейсы, которые предлагают надежный доступ к аккаунтам Discord. Ёти платформы соедин€ют пользователей с продавцами, у которых есть подход€щие аккаунты, под защитой платформы. ¬ этой статье мы рассмотрим 6 лучших сайтов, чтобы купить аккаунты Discord по конкурентным ценам с гарантией безопасных и легальных сделок.
1. Xyliase Shop – ѕремиальные верифицированные токены Discord
¬еб-сайт: shop.xyliase.com
 /img-website.bitbrowser.net/uploads/small_image_25156e4af5.png" target="_blank">https://img-website.bitbrowser.net/uploads/small_image_25156e4af5.png 500w, https://img-website.bitbrowser.net/uploads/medium_image_25156e4af5.png 750w, https://img-website.bitbrowser.net/uploads/large_image_25156e4af5.png 1000w" width="1000" />
/img-website.bitbrowser.net/uploads/small_image_25156e4af5.png" target="_blank">https://img-website.bitbrowser.net/uploads/small_image_25156e4af5.png 500w, https://img-website.bitbrowser.net/uploads/medium_image_25156e4af5.png 750w, https://img-website.bitbrowser.net/uploads/large_image_25156e4af5.png 1000w" width="1000" />Xyliase Shop выдел€етс€ как ведуща€ платформа дл€ покупки полностью верифицированных токен-аккаунтов Discord. Whether you're a developer, marketer, or community manager, Xyliase предлагает высококачественные, старые аккаунты с пользовательскими именами и аватарами. лючевые особенности:
- ѕолностью верифицированные токены: ѕодтверждены email и телефоном дл€ полного доступа.
- —тарые аккаунты: ќт новых до возрастом 24 мес€ца.
- ћгновенна€ доставка: Ѕез ожидани€; получайте токены сразу.
- –еалистичные имена и аватары: —озданы реальными людьми и собраны из крупных сообществ Discord.
- »деально дл€ автоматизации: ќтлично подход€т дл€ запуска ботов, маркетинговых кампаний или управлени€ серверами.
Ѕлагодар€ репутации надежности и удовлетворенности клиентов, Xyliase Shop — лучший выбор дл€ тех, кто ищет премиальные аккаунты Discord. ”знайте больше здесь.
2. PlaySwap – Ўирокий выбор и надежна€ гаранти€
¬еб-сайт: playswap
«а годы PlaySwap утвердила свою репутацию в торговле аккаунтами Discord. ќни поддерживают стабильное качество за счет строгого процесса проверки аккаунтов перед listing, гарантиру€, что покупатели получают рабочие аккаунты. лючевые особенности:
- –азнообразный выбор аккаунтов: ¬ерифицированные, старые, Nitro или аккаунты с бейджами.
- ѕоддержка в live-чате 24/7: ћгновенна€ помощь при проблемах или вопросах о заказе.
- ѕрозрачна€ политика гарантии: ѕомогает пользовател€м чувствовать себ€ в безопасности.
- Ѕыстра€ доставка: ѕолучите свой аккаунт быстро и безопасно.
- ¬строенна€ система сообщений: ѕомогает сторонам быстро св€зыватьс€ при необходимости.
- ѕубличные отзывы и показатели выполнени€ заказов: ƒают больше уверенности перед покупкой.
Ѕлагодар€ удобному интерфейсу, продвинутым функци€м и высокому уровню безопасности, PlaySwap — первоклассный вариант дл€ тех, кто хочет купить аккаунт Discord без больших затрат времени или риска.
3. Eldorado – ѕроверенный маркетплейс дл€ геймеров
¬еб-сайт: eldorado
Eldorado — известный маркетплейс, где геймеры торгуют аккаунтами, внутриигровыми предметами и валютами. ’от€ торговл€ аккаунтами Discord — новое направление, сильна€ репутаци€ Eldorado делает его надежным选项. ќсобенности:
- ‘ильтры по цене и доставке: Ѕыстро находите аккаунты по вашим needs.
- ƒоверие сообщества: ”сто€вша€с€ в игровых сообществах.
- ѕолитика гарантии на аккаунты: ¬ключена защита покупател€.
- ”добный процесс оформлени€ заказа: ѕростой и безопасный процесс покупки.
¬рем€ доставки зависит от продавца, но Eldorado предлагает прозрачность и множество选项, что делает его solid выбором дл€ покупки аккаунтов Discord.
4. G2G – рупный маркетплейс с защитой покупателей
¬еб-сайт: g2g
G2G — попул€рный цифровой маркетплейс дл€ игровых аккаунтов, предметов, валюты и аккаунтов Discord. ѕокупатели могут фильтровать listings по цене, скорости доставки и репутации продавца.
- ќткрытый маркетплейс: ћножество продавцов с конкурентными选项.
- —труктурированна€ система отзывов: ѕрозрачные рейтинги продавцов.
- ѕолитика защиты покупателей: —нижает риски при сделках.
ƒл€ тех, кто хочет гибкость и множество选项 продавцов, G2G — надежна€ платформа дл€ покупки аккаунтов Discord.
5. PlayerUp – ћаркетплейс в форумном стиле
¬еб-сайт: playerup
PlayerUp работает как маркетплейс в стиле форума, где покупатели могут просматривать аккаунты и вести переговоры напр€мую с продавцами.
- ѕр€мые переговоры: Ќастраивайте предложени€ и обсуждайте детали аккаунта.
- ”слуги посредника: ќплата удерживаетс€, пока покупатель не подтвердит доставку.
- Ѕольша€ пользовательска€ база: ѕопул€рен, несмотр€ на менее современный интерфейс.
PlayerUp остаетс€ фаворитом среди пользователей, prioritizing защиту покупател€ и гибкость переговоров.
6. Z2U – ƒоступные и безопасные选项
¬еб-сайт: z2u
Z2U предлагает широкий ассортимент игровых и Discord-аккаунтов, включа€ верифицированные, старые, токен-аккаунты, аккаунты с бейджами и Nitro-аккаунты.
- „етка€ категоризаци€: Ћегко фильтруйте аккаунты по типу и назначению.
- ѕриверженность безопасности: «ащищенные транзакции дл€ вашего спокойстви€.
- ƒоступные选项: онкурентные цены дл€ покупателей.
ƒаже с учетом комиссий, Z2U — solid выбор дл€ тех, кто ищет straightforward опыт покупки.
«аключительные мысли
ѕокупка аккаунта Discord может сэкономить врем€ и быстрее открыть функции, если вы покупаете у проверенного источника. —реди перечисленных платформ Xyliase Shop выдел€етс€ как лучший вариант благодар€ strict стандартам качества и политике, ориентированной на покупател€.
Ќезависимо от выбора платформы, всегда сравнивайте listings, изучайте отзывы о продавцах и понимайте политику сайта перед покупкой. ѕравильный выбор может упростить ваш опыт использовани€ Discord и помочь вам развиватьс€ быстрее и безопаснее.
|
|
Ѕесплатное руководство по использованию GPT5 |

Ќедавно многие спрашивают, есть ли действительно бесплатный способ использовани€ GPT5? ак опытный пользователь AI-инструментов, после многочисленных тестов € нашел надежное решение — Copilot от Microsoft. ќн не только бесплатно интегрирует ключевые функции GPT5, но и обеспечивает довольно плавный опыт использовани€. ќднако пользователи из ита€ часто сталкиваютс€ с проблемой ограничени€ аккаунта при пр€мом использовании. ѕосле более чем двух мес€цев практики € обнаружил, что браузер BitBrowser позвол€ет идеально решить эту задачу. Ќиже подробно поделюсь полным методом настройки и опытом использовани€.
I. ѕочему многие все еще выбирают Chatgpt?
GPT5 как последн€€ верси€ €зыковой модели от OpenAI действительно внесла революционные изменени€ по сравнению с предыдущими верси€ми. ≈го возможности были проверены в различных сценари€х, и наиболее заметные преимущества про€вл€ютс€ в следующих четырех аспектах:
1. «начительное улучшение качества генерации контента
Ѕудь то написание технической документации, маркетинговых текстов или научных отчетов, генерируемый контент становитс€ более точным и профессиональным. ќсобенно при работе с задачами в специализированных област€х он способен предоставл€ть глубинные выводы, а не просто поверхностные комментарии. ќднажды € попросил его разработать сложный технический проект, и результат оказалс€ удивительно подробным и точным.
2. ”силенна€ способность понимани€ контекста
ѕри длительных диалогах GPT5 лучше воспринимает общую структуру темы. Ќапример, при обсуждении сложного плана проекта он запоминает все ранее упом€нутые ключевые моменты и продолжает углубленный анализ на их основе, без необходимости повторного напоминани€ о предыдущих обсуждени€х.
3. Ѕолее полна€ поддержка мультимодальности
ѕомимо текстового взаимодействи€ теперь поддерживаютс€ задачи, св€занные с изображени€ми. «агрузка фотографий продукции дл€ создани€ описательных текстов или анализ технических деталей на изображени€х — эти функции значительно помогают в повседневной работе и творческих проектах. я протестировал его на анализе схемы механизма, и описание оказалось весьма профессиональным.
4. ”силенные возможности логического рассуждени€
ѕри решении сложных задач GPT5 демонстрирует более сильные способности логического анализа. Ѕудь то обработка данных, сравнение вариантов решений или вы€вление проблем, он предлагает более систематизированные и структурированные решени€.
’от€ доступ к GPT5 на официальном сайте OpenAI требует платной подписки, благодар€ Microsoft Copilot мы можем бесплатно опробовать эти ключевые функции — это и есть основна€ причина, по которой € насто€тельно рекомендую его попробовать.
II. ”никальные преимущества Copilot
Ќа рынке существует множество AI-инструментов, но Copilot имеет несколько уникальных преимуществ, которые трудно заменить, и они особенно заметны при практическом использовании:
1. ѕолностью бесплатное использование
Ќет необходимости в дополнительной платной подписке или беспокойства о лимитах использовани€. ѕо сравнению с другими платными AI-инструментами Copilot имеет абсолютное преимущество в плане стоимости.
2. √лубока€ интеграци€ с пакетом Office
≈го можно напр€мую запускать в Word, Excel и PPT. “ака€ глубока€ интеграци€ значительно повышает производительность, особенно при работе с документами Office, так как нет необходимости переключатьс€ между разными приложени€ми.
3. ѕростой процесс регистрации
ƒостаточно иметь аккаунт Microsoft дл€ немедленного использовани€, что избавл€ет от сложного процесса регистрации и верификации. ќсобенно удобно дл€ пользователей, уже имеющих аккаунты Outlook или Office.
4. Ѕезопасность благодар€ официальному происхождению
–азработка Microsoft гарантирует строгие меры по обеспечению безопасности данных и защиты конфиденциальности. ѕо сравнению с некоторыми сторонними инструментами, использование Copilot дл€ обработки чувствительных данных вызывает больше уверенности.
¬ практической работе € заметил, что удобство использовани€ Copilot превзошло все ожидани€. Ќапример, при написании технической документации его можно сразу использовать дл€ улучшени€ формулировок, а при создании презентаций — дл€ быстрого формировани€ структуры контента. “акой бесперебойный опыт работы гораздо эффективнее, чем переключение между несколькими программами.
¬ажное примечание: ќсновной барьер дл€ использовани€ Copilot
»з-за географических ограничений Microsoft пользователи из некоторых регионов часто сталкиваютс€ с проблемой блокировки аккаунта как "из ограниченного региона", что приводит к приостановке сервиса. онкретно это про€вл€етс€ в невозможности отправки команд после входа в систему или пр€мом уведомлении "Ётот сервис не поддерживаетс€ в вашем регионе". я тоже сталкивалс€ с этой проблемой вначале, и позже решил ее с помощью технических средств.
III. ќграничени€ Microsoft дл€ аккаунтов Copilot
Microsoft определ€ет регион пользовател€ по нескольким параметрам, и эти механизмы весьма строги:
1. –аспознавание отпечатка браузера
¬ключа€ UserAgent, разрешение устройства, системные шрифты, настройки часового по€са и €зыка — эти данные полностью раскрывают реальное окружение устройства. ƒаже при использовании прокси, если отпечаток браузера не соответствует требовани€м, его легко распознать.
2. ѕроверка географического положени€ по IP-адресу
≈сли IP-адрес указывает на расположение в итае или €вл€етс€ общедоступным IP-адресом дата-центра, включаетс€ механизм ограничений. —истема проверки IP-адресов Microsoft весьма точна и способна распознать большинство прокси-IP.
3. јнализ шаблона поведени€ аккаунта
¬ анализ также включаютс€ такие характеристики поведени€, как врем€ входа в систему, частота использовани€, привычки操作 — аномальные шаблоны поведени€ аккаунта также запускают безопасные механизмы.
ак только система определ€ет, что устройство находитс€ в китайской среде, сервис Copilot приостанавливаетс€, и это ограничение, как правило, посто€нное — даже при входе в систему с другого устройства его трудно сн€ть. я тоже сталкивалс€ с этой проблемой вначале, и позже нашел эффективное решение.
IV. “ехническое решение с BitBrowser
BitBrowser — это профессиональный браузер с измен€емым отпечатком, его ключева€ технологи€ заключаетс€ в создании независимого окружени€ браузера и полном изменении отпечатка браузера, что позвол€ет избежать распознавани€ реального региона пользовател€ платформой.
ќсновные принципы технологии:
1. —оздание независимого окружени€ отпечатка
ƒл€ каждого пользовател€ создаетс€ полностью независимое окружение отпечатка, включа€ изменение UserAgent на версии, широко используемые за рубежом, а также настройку разрешени€, шрифтов, часового по€са в соответствии с стандартными параметрами устройств из-за границы.
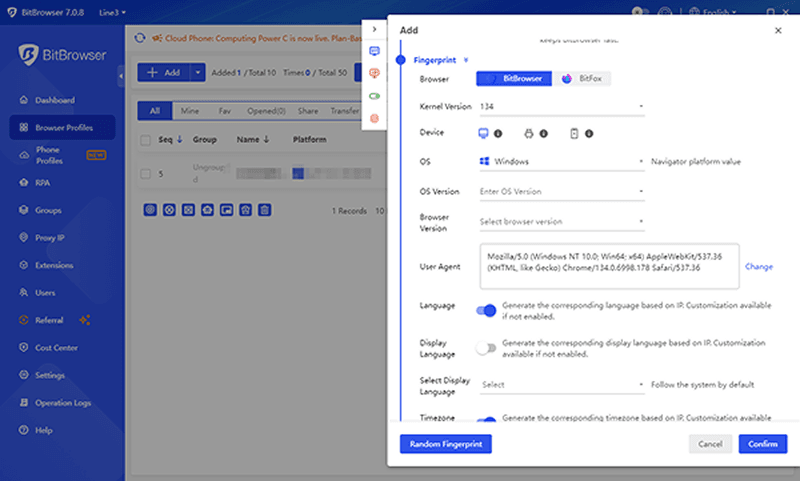
2. “очное соответствие IP-адреса
ѕоддерживаетс€ прив€зка стабильных жилых IP-адресов за рубежом, что гарантирует полное соответствие отпечатка браузера и географического положени€ IP-адреса, избежа€ распознавани€ из-за несоответстви€ данных.
3. ћеханизм изол€ции нескольких окружений
ѕоддерживаетс€ создание нескольких независимых окружений браузера, которые полностью изолированы друг от друга — даже если возникают проблемы с одним окружением, это не вли€ет на использование других.
4. »митаци€ шаблона поведени€
—пособен имитировать реальный шаблон поведени€ пользовател€, включа€ перемещение мыши, прокрутку и другие действи€, что делает весь процесс использовани€ более естественным и реалистичным.
ѕодробные шаги настройки:
1. —тади€ подготовки окружени€
—начала скачайте и установите BitBrowser — рекомендуетс€ получать последнюю версию с официального сайта. ѕосле установки произведите базовые настройки, чтобы обеспечить стабильную работу программного обеспечени€.
2. —оздание профил€ настроек
—оздайте новый профиль настроек браузера, ключевые параметры включают: установку часового по€са в целевой регион (например, западноамериканский часовой по€с), €зык — английский, разрешение — в соответствии с распространенными характеристиками устройств за рубежом.

3. Ќастройка прокси-сети
Ќастройте стабильный прокси с жилыми IP-адресами за рубежом — рекомендуетс€ выбирать услуги известных провайдеров. ѕротестируйте чистоту и стабильность IP-адреса, чтобы обеспечить его длительное использование.
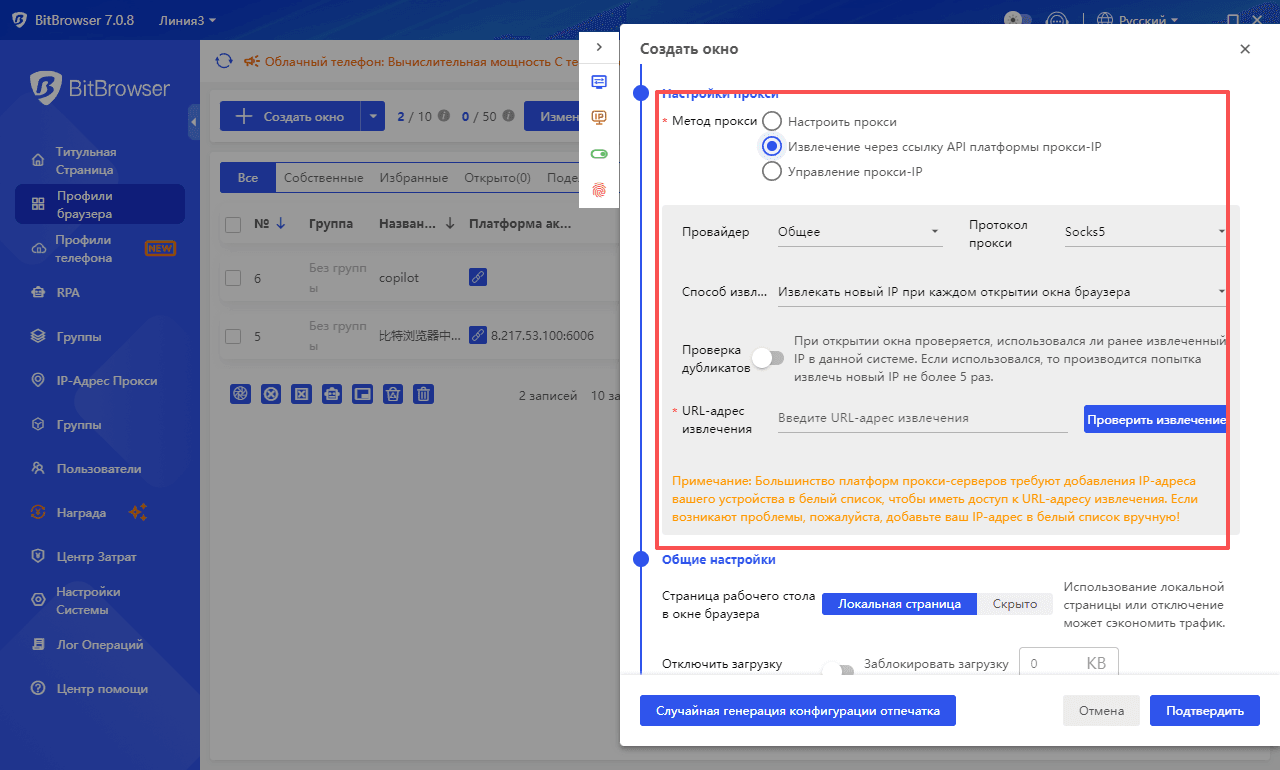
4. “естирование и проверка окружени€
¬ новом окружении браузера посетите сайт дл€ проверки IP-адреса, чтобы убедитьс€, что все данные отпечатка соответствуют целевому региону. ѕерейдите к следующему шагу только после подтверждени€ корректности настроек.
5. Ќастройка доступа к Copilot
¬ проверенном окружении посетите официальный сайт Copilot и войдите в систему с подготовленным аккаунтом Microsoft. –екомендуетс€ провести тестирование функций при первом использовании.
V. лючевые моменты дл€ длительного стабильного использовани€
ƒл€ обеспечени€ длительного стабильного использовани€ Copilot ниже приведены важные рекомендации и советы по использованию:
—тратеги€ резервного копировани€ нескольких окружений
–екомендуетс€ создать 2-3 независимых окружени€ браузера дл€ чередующего использовани€, чтобы избежать чрезмерной зависимости от одного окружени€. “аким образом, даже если возникают проблемы с одним окружением, можно немедленно переключитьс€ на резервное.
√аранти€ качества IP-адреса
¬ыберите надежных провайдеров иностранных IP-адресов, отдава€ предпочтение жилым IP-адресам вместо IP-адресов дата-центров. –егул€рно провер€йте качество и стабильность IP-адреса, своевременно замен€€ проблемные адреса.
—оветы по управлению аккаунтом
Ќе рекомендуетс€ прив€зывать китайские номера телефонов к аккаунтам Microsoft — новые зарегистрированные аккаунты имеют более высокий процент успешного использовани€. –екомендуетс€ создать отдельный аккаунт Microsoft专门 дл€ использовани€ Copilot.
ќптимизаци€ привычек использовани€
»збегайте частого переключени€ окружений входа в систему, поддержива€ относительно посто€нный шаблон использовани€. ѕри работе обращайте внимание на естественность действий, избега€ слишком механизированных паттернов操作.
–егул€рна€ проверка и обслуживание
–егул€рно провер€йте правильность данных отпечатка окружени€ браузера, своевременно обновл€€ настройки. —ледите за изменени€ми политик Microsoft, регулиру€ стратегию использовани€ в соответствии с актуальной ситуацией.
VI. „асто задаваемые вопросы и ответы
¬опрос: ƒействительно ли Copilot соответствует возможност€м GPT-5?
ќтвет: ¬ насто€щее врем€ Copilot интегрировал возможности GPT-4, а также передовые модели, которые Microsoft и OpenAI посто€нно обновл€ют. ’от€ GPT-5 еще не было официально выпущено, производительность Copilot в области сложного рассуждени€, генерации кода и мультимодального взаимодействи€ уже демонстрирует современный передовой уровень AI. Ёто один из лучших бесплатных способов опробовать возможности следующего поколени€ AI-технологий.
¬опрос: BitBrowser бесплатный? “ребуетс€ ли оплата за использование?
ќтвет: BitBrowser имеет бесплатную и платную версии. ≈сли вы используете Copilot лишь иногда, функции бесплатной версии полностью достаточны — она поддерживает создание 2-3 независимых окружений, что в основном удовлетвор€ет потребности индивидуальных пользователей. ≈сли вы используете его часто или нуждаетесь в создании большего количества окружений (например, дл€ корпоративных пользователей), можно рассмотреть платную версию — она открывает дополнительные расширенные функции, такие как массовое управление окружени€ми, более точна€ настройка отпечатка и т.д.
¬опрос: ѕри использовании Copilot и BitBrowser не будут ли раскрыты введенные данные?
ќтвет: Ќет. Ѕезопасность обеспечиваетс€ по двум направлени€м: во-первых, Copilot следует политике конфиденциальности Microsoft — введенные пользователем данные используютс€ только дл€ генерации ответов и не будут раскрыты или повторно использованы; во-вторых, BitBrowser как профессиональный браузер с измен€емым отпечатком не хранит данные о просмотрах и информации об аккаунтах пользователей — все данные сохран€ютс€ только на локальном устройстве пользовател€, поэтому нет риска "раскрыти€ данных при загрузке".
¬опрос: ак BitBrowser предотвращает блокировку аккаунта Copilot?
ќтвет: BitBrowser создает взаимно независимые профили настроек браузера, обеспечива€, чтобы каждый аккаунт Copilot работал в уникальном, высококачественно имитированном "виртуальном компьютере" в регионе без ограничений. ќн изолирует отпечаток китайской локальной среды, фиксирует IP-адрес и имитирует настройки часового по€са и €зыка целевого региона, исключа€ из causes, по которым сервис Copilot может определить "пользовател€ из ита€", что гарантирует длительное стабильное использование аккаунта.
¬опрос: ѕри использовании Copilot необходимо посто€нно поддерживать соответствие IP-адреса и отпечатка браузера?
ќтвет: ƒа, соответствие — это ключ к стабильному использованию. ак только Copilot обнаружит частые или резкие изменени€ в вашем окружении доступа (IP-адрес, часовой по€с, €зык и т.д.), это может запустить безопасные механизмы. ѕоэтому использование BitBrowser и настройка фиксированного чистого иностранного IP-адреса дл€ профил€ Copilot крайне важны — это обеспечит Copilot надежную "идентичность" дл€ доступа, котора€ не измен€етс€ в течение длительного периода.
»тог:
— помощью технического решени€ BitBrowser мы можем эффективно решить проблему географических ограничений Copilot и обеспечить длительное стабильное бесплатное использование. я использую этот метод уже более трех мес€цев, и Copilot демонстрирует сильные возможности как при обработке технической документации, так и при помощи в написании кода или поддержке научных исследований. ¬ практическом применении Copilot не только повышает производительность, но и, что более важно, предлагает новые подходы к решению сложных задач. ќсобенно ценным он становитс€ при разработке технических решений и создании контента. –екомендую новичкам последовательно выполн€ть шаги руководства, не спешить с процессом. ѕри возникновении проблем во врем€ настройки можно попробовать несколько вариантов решени€, чтобы найти наиболее подход€щий шаблон использовани€. Ќадеюсь, что это подробное руководство поможет больше пользовател€м опробовать AI-ассистент уровн€ GPT5 и действительно повысить эффективность работы и обучени€.
|
|
ак эффективно управл€ть несколькими аккаунтами Google Drive на одном компьютере? |

¬ повседневной работе многие люди используют несколько аккаунтов Google Drive дл€ рабочих или личных нужд. ќднако, как эффективно управл€ть ими на одном компьютере и избежать беспор€дка, возникающего при посто€нном переключении между ними, всегда был сложным вопросом. ¬ этой статье представлены несколько практических методов, которые помогут вам легко использовать несколько аккаунтов параллельно и поддерживать пор€док в рабочих файлах.
ћетод 1: ƒесктопное приложение Google Drive
ќфициальное десктопное приложение Google Drive делает синхронизацию файлов очень удобной. ¬ы можете работать с файлами напр€мую в папках компьютера, так же как и с локальным хранилищем. Ёто приложение поддерживает вход в до четырех разных аккаунтов Google.
ѕреимущества:
—инхронизаци€ файлов: —инхронизирует файлы облачного диска напр€мую с локальным устройством, обеспечива€ удобный доступ к ним без подключени€ к интернету и управление ими.
»нтуитивно пон€тна€ работа: ќперации выполн€ютс€ в файловом менеджере компьютера, что соответствует привычкам пользователей.
ќграничени€:
ќграничение по количеству аккаунтов: ѕоддерживает вход не более чем в четыре аккаунта, что недостаточно дл€ пользователей, которым нужно управл€ть большим количеством аккаунтов.
≈диный вид: ‘айлы из всех аккаунтов отображаютс€ в виде папок, что легко приводит к путанице. ¬озможно, вам придетс€ потратить врем€, чтобы определить, к какому аккаунту относитс€ кажда€ папка.
ћетод 2: ”правление несколькими аккаунтами в браузере
Ёто самый распространенный и простой метод. Ќе требуетс€ установка программного обеспечени€ — вам只需 войти в несколько аккаунтов Google в браузере и переключатьс€ между профил€ми дл€ доступа к разным аккаунтам Google Drive.
ѕреимущества:
ќтсутствие необходимости в установке: Ќе требуетс€ дополнительное программное обеспечение, можно начать использовать сразу после открыти€ браузера.
Ѕыстрое переключение: ѕереключение между аккаунтами осуществл€етс€ кликом по аватару в браузере.
ќграничени€:
«ависимость от браузера: ¬ течение всей работы браузер должен оставатьс€ открытым, отсутствует опыт использовани€ десктопного приложени€.
Ѕеспор€док с вкладками: Google Drive каждого аккаунта открываетс€ в новой вкладке браузера. ѕри частом переключении браузер заполн€етс€ большим количеством вкладок, что затрудн€ет управление.
Ќизкое качество пользовательского опыта: ѕоскольку все операции выполн€ютс€ в браузере, при работе с большим количеством файлов опыт использовани€ значительно хуже, чем при работе с десктопным приложением.
ћетод 3: BitBrowser — профессиональный выбор дл€ управлени€ несколькими аккаунтами
ƒл€ решени€ проблем, возникающих при использовании вышеупом€нутых методов, по€вились специализированные инструменты. Ќапример, BitBrowser — это инструмент дл€ создани€ отпечатков браузера, который эффективно решает задачу управлени€ несколькими аккаунтами. —оздава€ независимые среды браузера, он позвол€ет каждому аккаунту Google Drive работать в отдельном изолированном окне.
ќсновные преимущества BitBrowser:
ѕолна€ изол€ци€: аждый аккаунт имеет уникальный отпечаток браузера и собственную рабочую среду. јккаунты не вли€ют друг на друга, что эффективно избежает рисков ассоциации.
Ќеограниченное количество аккаунтов: ¬ы можете создавать любое количество профилей браузера по мере необходимости. ¬ каждый профиль можно войти под одним аккаунтом Google Drive, что облегчает управление большим количеством аккаунтов.
ѕрофессиональна€ безопасность: ак специализированный инструмент дл€ работы с отпечатками браузера, он обеспечивает более высокий уровень защиты ваших аккаунтов и гарантирует безопасность данных.
”правление аккаунтами Google Drive с помощью BitBrowser также очень просто. ¬ам只需 создать отдельный профиль браузера дл€ каждого аккаунта, а затем войти в Google Drive в соответствующем профиле. Ётот метод не только решает проблему беспор€дочного управлени€ несколькими аккаунтами, но и делает вашу рабочую среду более организованной и эффективной.
»тог:
¬ыбор правильного инструмента — ключ к эффективному управлению несколькими аккаунтами Google Drive. ≈сли вам нужно управл€ть небольшим количеством аккаунтов, десктопное приложение Google Drive может удовлетворить ваши потребности; если вы предпочитаете легковесный вариант, переключение между несколькими аккаунтами в браузере также подойдет.
ќднако, если вам нужно управл€ть большим количеством аккаунтов или у вас есть высокие требовани€ к безопасности аккаунтов и эффективности работы, профессиональный инструмент вроде BitBrowser безусловно €вл€етс€ более разумным выбором. Ќезависима€ изолированна€ среда и возможность управлени€ неограниченным количеством аккаунтов помогут вам полностью избежать проблем с переключением между несколькими аккаунтами и сосредоточитьс€ на работе.
|
|
BitBrowser: ѕолучите бесплатные ваучеры на 5$и$10... |

|
|
Ёмул€ци€ ввода браузера: основна€ технологи€, лежаща€ в основе обнаружени€ антибраузеров |
|
|
TikTok:¬ход в браузер с отпечатками отпечатков |

|
|
ƒостижение успеха в электронной коммерции с помощью резидентных прокси-серверов |

¬ стремительно развивающемс€ мире электронной коммерции компании посто€нно ищут способы оптимизировать операции, опередить конкурентов и улучшить свою прибыль. ќдин из самых ценных инструментов дл€ достижени€ этих целей — резидентские прокси (живые прокси). ќни предлагают непревзойденные преимущества дл€ бизнеса в сфере электронной коммерции: от предотвращени€ блокировок по IP до проведени€ конкурентной разведки и автоматизации процессов.
¬ этой статье мы рассмотрим, как работают резидентские прокси, почему они необходимы дл€ электронной коммерции и как их можно использовать дл€ улучшени€ операций вашего онлайн-бизнеса.
1. „то такое резидентские прокси (Residential Proxies)?
–езидентские прокси — это IP-адреса, предоставл€емые интернет-провайдерами (ISP) владельцам жилых домов. ¬ отличие от дата-центровых прокси, которые происход€т из централизованных центров обработки данных, резидентские прокси прив€заны к реальным жилым адресам. Ёто делает их гораздо более трудными дл€ обнаружени€, поскольку они выгл€д€т как обычный трафик пользователей, а не автоматизированные запросы ботов.
ак они работают?
ѕри использовании резидентского прокси ваш бизнес в электронной коммерции направл€ет запросы через промежуточный сервер, который присваивает IP-адрес, соответствующий жилому адресу. Ёто позвол€ет вам просматривать веб-страницы или взаимодействовать с сайтами так, как если бы вы были обычным потребителем из этого региона.
2. лючевые преимущества резидентских прокси в электронной коммерции
A. ћониторинг цен конкурентов и отслеживание товаров
ƒл€ бизнеса в электронной коммерции критически важно знать, как конкуренты устанавливают цены на товары. Ќезависимо от того, продаете ли вы на таких платформах, как Amazon, eBay, или управл€ете собственным интернет-магазином, сбор данных о ценах конкурентов и уровне их запасов позвол€ет вам корректировать свою стратегию в режиме реального времени.
• ак помогают резидентские прокси: ¬еб-сайты могут обнаруживать повтор€ющийс€ трафик с одного и того же IP-адреса и блокировать его, лиша€ вас ценных данных о конкурентах. –езидентские прокси решают эту проблему путем ротации IP-адресов, создава€ впечатление, что сайт посещают разные пользователи.
•ѕочему это важно: Ќепрерывный доступ к данным конкурентов необходим дл€ корректировки вашего ценообразовани€, запуска новых продуктов и улучшени€ описаний ваших товаров. –езидентские прокси позвол€ют собирать данные без риска блокировки, гарантиру€ получение точной и актуальной информации.
B. »збегание IP-блокировок и CAPTCHA
омпании электронной коммерции, использующие автоматизацию дл€ таких задач, как мониторинг товаров, отслеживание запасов или сравнение цен, часто сталкиваютс€ с блокировками IP или запросами CAPTCHA. ¬еб-сайты внедр€ют эти меры безопасности, чтобы предотвратить перегрузку серверов ботами или автоматизированный сбор данных.
• ак помогают резидентские прокси: »спользу€ пул резидентских IP-адресов, вы можете легко переключатьс€ между разными IP и регионами, избега€ обнаружени€. ƒаже если один IP будет помечен, запрос будет перенаправлен через другой, свод€ к минимуму шансы на блокировку.
•ѕочему это важно: »спользование резидентских прокси обеспечивает бесперебойную автоматизацию, котора€ ключева€ дл€ масштабировани€ операций без перерывов из-за CAPTCHA или блокировок IP.
C. √еолокаци€ дл€ региональных предложений
ћногие интернет-магазины предлагают региональные акции, уровни запасов или цены. Ќапример, товар может быть дешевле в одной стране или доступен в ограниченном количестве в другой.
• ак помогают резидентские прокси: –езидентские прокси могут направл€ть трафик через IP-адреса в различных географических местоположени€х, позвол€€ вам получать доступ к контенту, специфичному дл€ региона. Ќапример, вы можете просматривать цены или акции, доступные только покупател€м в определенной стране.
•ѕочему это важно: Ёто важно дл€ разработки глобальных ценовых стратегий, понимани€ рыночных различий и адаптации ваших предложений к разным локаци€м. Ёто также помогает избежать блокировки контента географическими ограничени€ми.
D. ”правление несколькими аккаунтами без блокировки
ћногим компани€м электронной коммерции необходимо управл€ть несколькими аккаунтами: дл€ покупки товаров оптом, продажи на разных платформах или отслеживани€ отзывов клиентов. ¬ход в несколько аккаунтов с одного и того же IP-адреса может вызвать подозрени€ и привести к бану аккаунтов или ограничени€м.
• ак помогают резидентские прокси: –езидентские прокси позвол€ют использовать разные IP дл€ каждого аккаунта, создава€ впечатление, что каждый вход выполн€етс€ отдельным пользователем. Ёто предотвращает помечание вашей активности системами платформ как подозрительной.
•ѕочему это важно: ”правление несколькими аккаунтами распространено в электронной коммерции, особенно при ведении бизнеса на нескольких платформах. –езидентские прокси обеспечивают сохранность аккаунтов и их незаметность.
3. ѕрименение резидентских прокси в электронной коммерции
A. ѕокупка лимитированных товаров (Sneaker Bots)
ƒл€ бизнеса или частных лиц, которые хот€т приобрести лимитированные продукты (например, кроссовки, одежду или технические гаджеты), важна скорость. "—никер-боты" (Sneaker bots) автоматизируют процесс покупки высоко востребованных товаров до того, как они распродадутс€.
• ак помогают резидентские прокси: –езидентские прокси помогают избежать обнаружени€, имитиру€ реальных пользователей, что снижает риск блокировки во врем€ меропри€тий с высоким трафиком. –отаци€ IP позвол€ет совершать несколько успешных покупок, не активиру€ системы безопасности.
•ѕочему это важно: омпании электронной коммерции, стрем€щиес€ перепродавать попул€рные товары (кроссовки, билеты на концерты и т. д.), могут воспользоватьс€ эксклюзивными релизами, использу€ резидентские прокси дл€ гарантированного приобретени€ лимитированных товаров в нужном масштабе.
B. ¬ерификаци€ рекламы
«апуск рекламы на таких платформах, как Google, Facebook или других рекламных сет€х, €вл€етс€ распространенной стратегией дл€ привлечени€ трафика на ваш сайт электронной коммерции. ќднако крайне важно убедитьс€, что ваша реклама отображаетс€ правильно и нужной аудитории.
• ак помогают резидентские прокси: –езидентские прокси позвол€ют провер€ть показы рекламы из разных географических местоположений, гарантиру€, что ваши кампании работают корректно в различных регионах и на разных устройствах.
•ѕочему это важно: ¬ерификаци€ рекламы гарантирует не только лучшую окупаемость инвестиций (ROI), но и то, что ваши объ€влени€ не подвержены манипул€ци€м или перенаправлению из-за мошенничества или ошибок на платформе.
C. —бор данных дл€ маркетинговых исследований
—бор данных часто используетс€ в электронной коммерции дл€ получени€ информации о поведении клиентов, тенденци€х, спросе на продукты и многом другом. ƒоступ к страницам товаров конкурентов, их отзывам или истории цен может помочь вам принимать более эффективные бизнес-решени€.
• ак помогают резидентские прокси: –езидентские прокси позвол€ют собирать большие объемы данных с сайтов конкурентов, не опаса€сь блокировки или ограничени€ скорости (rate-limiting).
•ѕочему это важно: —бор данных помогает вы€вл€ть новые тенденции, понимать стратегии конкурентов и собирать информацию о пробелах на рынке или возникающих нишах, что в конечном итоге способствует улучшению вашей бизнес-стратегии.
4. лючевые аспекты при использовании резидентских прокси
’от€ резидентские прокси предлагают значительные преимущества, важно учитывать следующие аспекты:
•A. —тоимость: –езидентские прокси, как правило, дороже дата-центровых из-за использовани€ реальных жилых IP-адресов. ќб€зательно соизмер€йте стоимость с преимуществами, исход€ из ваших потребностей.
•B. ачество поставщика прокси: Ќе все поставщики прокси одинаковы. ¬ыбирайте надежного поставщика с качественным и разнообразным пулом резидентских IP. ачественные провайдеры часто предлагают функцию ротации прокси, поддержку множества локаций и высокую доступность (uptime).
•C. Ётичное использование: ¬сегда убеждайтесь, что ваше использование прокси-серверов соответствует правилам использовани€ веб-сайтов, с которыми вы взаимодействуете. —бор данных, автоматизаци€ или обход ограничений без авторизации могут привести к санкци€м, бану аккаунтов или судебным искам.
«аключение
¬ современном мире электронной коммерции дл€ опережени€ конкурентов требуютс€ эффективна€ автоматизаци€, интеллектуальный мониторинг цен и безопасна€ работа в нескольких аккаунтах и регионах. –езидентские прокси-серверы позвол€ют обходить распространенные преп€тстви€, такие как блокировка IP, ограничение скорости (rate limiting) и CAPTCHA, сохран€€ при этом анонимность и незаметность вашего бизнеса. ¬ы можете попробовать с нашим Bitbrowser.
|
|
¬торжение »» против конфиденциальности |
Ѕыстрое развитие искусственного интеллекта (»») вызывает во всем мире одновременно и энтузиазм, и обеспокоенность. “акие технологии, как ChatGPT, стремительно эволюционируют, стимулиру€ инновации во многочисленных област€х. ќднако по мере того, как »» продолжает совершенствоватьс€, возникает одна критически важна€ проблема: вторжение в приватность.
¬ этой статье мы исследуем, как »» вли€ет на конфиденциальность данных и безопасность в интернете дл€ частных лиц, корпораций и предпри€тий. ћы углубимс€ в преимущества и риски, св€занные с этой революцией »».
„то такое »»?
»скусственный интеллект (»») — это способность машин обрабатывать, синтезировать и интерпретировать информацию способами, схожими с человеческим интеллектом. ќн включает такие технологии, как машинное обучение, глубокое обучение, обработка естественного €зыка, робототехника и компьютерное зрение. ¬месте они позвол€ют машинам обучатьс€ на основе данных, вы€вл€ть закономерности и принимать решени€ без €вного программировани€.
ћашинное обучение: ќснова »»
ћашинное обучение лежит в основе »». ќно позвол€ет машинам учитьс€ на данных, распознава€ шаблоны, дела€ прогнозы и получа€ полезную информацию. »нтеграци€ машинного обучени€ произвела революцию в бизнес-операци€х, автоматизировав процессы и позволив принимать решени€ на основе данных. ќднако эта технологическа€ мощь привносит и этические соображени€, особенно когда системы »» работают с конфиденциальными персональными данными.
ѕриватность и безопасность в интернете в цифровую эпоху
ѕриватность в интернете означает защиту персональной информации, которой дел€тс€ в сети, такой как имена, данные кредитных карт или медицинские записи. »нтернет-безопасность, с другой стороны, защищает наши цифровые данные от киберугроз, таких как взломы, вредоносное ѕќ и кража личных данных. ѕоскольку все больше сторон нашей жизни переходит в цифровую сферу, защита этой информации становитс€ как никогда важной.
ѕочему важна приватность в интернете
–иски, св€занные с недостаточной приватностью и безопасностью, включают:
1.«ащита от неправомерного использовани€ личной информации: Ѕез надлежащих мер защиты конфиденциальные данные могут быть использованы дл€ преступной де€тельности или кражи личных данных.
2.–ост киберугроз: ибератаки, такие как фишинг и социальна€ инженери€, усиливаютс€, дела€ защиту конфиденциальных данных об€зательной.
3.«ащита фундаментальных прав: ѕриватность €вл€етс€ основополагающим правом, а неправомерное использование персональных данных может нарушать свободы, особенно при наблюдении со стороны правительств или корпораций.
’от€ новые регулирующие нормы направлены на защиту персональной информации, »» продолжает стремительно развиватьс€ и создает новые вызовы.
–иски приватности и безопасности в »»
ѕо мере интеграции »» в нашу повседневную жизнь его вли€ние на приватность и безопасность становитс€ все более значительным. ¬от ключевые проблемы:
1.Ќарушени€ конфиденциальности данных:
•—истемы »» дл€ повышени€ точности полагаютс€ на огромные объемы данных.
•ќднако эти данные часто содержат конфиденциальную личную информацию.
•≈сли они используютс€ неправомерно или получаютс€ без согласи€, это может привести к нарушени€м приватности.
•—истемы »» могут собирать данные из социальных сетей, поисковых систем и онлайн-платформ, создава€ подробные профили людей без их ведома.
2.–иски кибербезопасности:
•—истемы »» у€звимы дл€ кибератак.
•’акеры могут использовать »» дл€ запуска более изощренных и автоматизированных атак.
•‘ишинг и социальна€ инженери€ на основе »» могут упростить дл€ злоумышленников обман пользователей и кражу данных.
3.«лоупотребление данными:
•—истемам »» дл€ эффективной работы требуютс€ большие наборы данных, которые могут эксплуатироватьс€ в коммерческих цел€х, например дл€ таргетированной рекламы или продажи сторонним брокерам данных.
•ѕерсональные данные могут подвергатьс€ незаконному использованию в цел€х извлечени€ прибыли, часто без согласи€ или ведома пользовател€.
акие ваши онлайн-данные подвержены риску?
¬аши онлайн-данные посто€нно собираютс€ и могут быть у€звимы в нескольких аспектах:
•ћестоположение: —ервисы, отслеживающие ваше местоположение, могут быть использованы дл€ таргетированной рекламы или злоумышленниками дл€ определени€ вашего местонахождени€.
•ѕароли и конфиденциальные документы: »» можно использовать дл€ подбора слабых паролей или дл€ целевых фишинговых атак с целью кражи конфиденциальной информации.
•‘айлы на жестком диске: ак только устройство скомпрометировано, злоумышленники могут получить доступ к файлам на вашем жестком диске и манипулировать ими.
•»стори€ браузера: ¬ашу историю просмотров могут отследить хакеры и использовать в злонамеренных цел€х, включа€ распространение вредоносного ѕќ.
ак BitBrowser может защитить вашу приватность в интернете?
BitBrowser — это передовой антидетективный браузер, повышающий приватность и безопасность в интернете. ќн использует передовые технологии цифрового отпечатка, чтобы гарантировать анонимность ваших действий, затрудн€€ дл€ третьих сторон отслеживание вашего поведени€ в сети.
лючевые особенности BitBrowser:
•Ќеограниченное количество профилей браузера: Ќесколько профилей с уникальными цифровыми отпечатками браузера обеспечивают безопасность и анонимность.
•“ехнологи€ цифрового отпечатка: BitBrowser посто€нно обновл€ет и измен€ет ваш цифровой отпечаток дл€ защиты вашей личности.
•”правление куки: онтроль над куки гарантирует, что данные вашего браузера защищены и не эксплуатируютс€ злоумышленниками.
•’ранение данных: онфиденциальные данные, такие как пароли и истори€ браузера, хран€тс€ безопасно, защища€ вашу личную информацию.
«аключение
’от€ »» обладает огромным потенциалом дл€ прогресса, он также представл€ет собой значительные проблемы дл€ приватности и безопасности. ќт нарушений конфиденциальности данных до рисков кибербезопасности — эволюци€ »» требует от нас прин€ти€ мер предосторожности дл€ защиты нашей цифровой жизни.
»нструменты, такие как BitBrowser, обеспечивают повышенную защиту от онлайн-угроз, позвол€€ вам пользоватьс€ преимуществами »», не жертву€ своей приватностью. —охран€€ баланс между мощью »» и практиками, ориентированными на приватность, мы можем безопасно ориентироватьс€ в этой цифровой эпохе, защища€ наши фундаментальные права.
|
|
ак мне иметь несколько аккаунтов Warpcast? |
Warpcast, самый попул€рный клиент дл€ децентрализованного социального протокола Farcaster, быстро становитс€ центральным узлом дл€ Web3-социализации. ќт создателей и креаторов до бизнесов и сообществ — многие пользователи быстро обнаруживают, что им нужно более одной учетной записи Warpcast.
¬опрос в следующем: как эффективно управл€ть несколькими учетными запис€ми Warpcast?
ороткий ответ: да, это возможно — и самый простой способ масштабировани€ — использование BitBrowser.
1. Ќесколько аккаунтов через разные кошельки
ажда€ учетна€ запись Warpcast прив€зана к уникальному адресу кошелька и идентификатору Farcaster (FID). „тобы открыть дополнительную учетную запись, вам понадобитс€:
- Ќовый кошелек (MetaMask, Rainbow, Privy и т.д.).
- «арегистрировать этот кошелек в Warpcast.
- ќплатить единовременный сбор за регистрацию FID (обычно от $5 до $10 в криптовалюте).
Ёто официальный метод, но управление несколькими кошельками может стать cumbersome (неудобным) без правильных инструментов.
2. “радиционные обходные пути (”стройства и браузеры)
≈сли вам нужно только две учетные записи, вы можете управл€ть ими с помощью:
- ћобильное приложение + Ѕраузер: »спользуйте одну учетную запись в мобильном приложении Warpcast, другую — в Safari или Chrome.
- Ќесколько десктопных браузеров: ¬ойдите в Chrome под одной учетной записью, в Firefox под другой или используйте режим инкогнито.
Ёто работает в краткосрочной перспективе, но становитс€ беспор€дочным и неэффективным, как только вы добавл€ете более двух учетных записей.
3. »спользуйте BitBrowser дл€ effortless (легкого) управлени€ несколькими аккаунтами
≈сли вы серьезно настроены управл€ть несколькими учетными запис€ми Warpcast — будь то дл€ роста бизнеса, управлени€ сообществом или присутстви€ бренда — то BitBrowser €вл€етс€ ultimate (идеальным) решением.
„то такое BitBrowser?
BitBrowser — это браузер дл€ multi-account (многопользовательской работы) и anti-detect (противодействи€ обнаружению), созданный дл€ безопасного управлени€ несколькими цифровыми идентичност€ми. ќн создает полностью изолированные среды браузера, гарантиру€, что ваши куки, сессии и логины никогда не пересекаютс€.
ѕочему пользователи Warpcast люб€т BitBrowser:
- ✅ «апускайте неограниченное количество учетных записей Warpcast параллельно.
- ✅ Ѕольше не нужно посто€нно входить и выходить.
- ✅ ƒержите бизнес-, личные и общественные идентичности полностью разделенными.
- ✅ ¬строенна€ RPA-автоматизаци€ и API-интеграции дл€ advanced (продвинутых) рабочих процессов.
- ✅ Ѕезопасно делитесь аккаунтами с членами команды с помощью функций командного collaboration (сотрудничества).
ƒл€ пользователей Web3 это означает, что вы можете масштабировать использование Warpcast как профессиональный менеджер социальных сетей — без риска перекрестного загр€знени€ аккаунтов.
4. јльтернативные клиенты Farcaster
’от€ Warpcast €вл€етс€ самым попул€рным, это не единственный клиент Farcaster. ¬ы также можете попробовать:
- Jam – минималистичный и чистый интерфейс.
- AlfaFrens – разработан дл€ вовлечени€ сообщества.
- Nook – сфокусирован на нативных дл€ Web3 обсуждени€х.
- Supercast – создан дл€ креаторов.
¬ сочетании с BitBrowser эти клиенты предлагают еще большую гибкость дл€ управлени€ несколькими идентичност€ми под одной крышей.
—оответствие правилам
ƒа, Warpcast разрешает несколько учетных записей, но всегда используйте их responsibly (ответственно). —пам, использование ботов или злоупотребление протоколом могут привести к ограничени€м. BitBrowser предназначен дл€ этичного, профессионального управлени€ аккаунтами, а не дл€ злоупотреблений.
«аключение
»так, можно ли иметь несколько учетных записей Warpcast? јбсолютно.
- ќбычные пользователи могут просто создать другой кошелек и использовать разные браузеры или устройства.
- ѕродвинутые пользователи и профессионалы должны выбрать BitBrowser, который делает управление несколькими идентичност€ми Warpcast безопасным, масштабируемым и effortless (легким).
— BitBrowser + Farcaster у вас есть свобода строить, развивать и управл€ть вашей экосистемой идентичностей в Web3 так, как вы хотите.
|
|
Ѕудут ли работать cookie-боты в 2025 году? ћоделирование реальных пользовательских стратегий |
|
|
акую информацию можно получить из IP-адреса в 2025 году с помощью BitBrowser? |

ƒл€ многих пользователей »нтернета термин «IP» звучит загадочно. „то он на самом деле означает? акую роль играет в нашей онлайн-жизни? ƒавайте разберемс€.
IP-адрес (сокращение от Internet Protocol address) работает как цифровое удостоверение личности или почтовый индекс дл€ вашего устройства. ќн гарантирует, что вс€ информаци€, которую вы отправл€ете и получаете в сети, достигает правильного пункта назначени€. Ѕез него устройства в »нтернете не смогли бы распознавать друг друга или общатьс€ между собой.
¬ этой статье мы объ€сним:
- „то такое IP-адрес
- „ем отличаютс€ IPv4 и IPv6
- «начение публичных и частных IP
- —татические и динамические IP
- акую информацию можно раскрыть по вашему IP
- ак скрыть или защитить свой IP-адрес
„то такое IP-адрес?
IP-адрес — это уникальный номер, назначаемый вашему устройству при подключении к »нтернету. —читайте его онлайн-домашним адресом вашего устройства.
—истема IP-адресов была стандартизирована в 1983 году, когда јдминистраци€ адресного пространства »нтернет (IANA) начала управл€ть распределением адресов по всему миру. IANA распредел€ет большие блоки IP среди региональных интернет-регистраторов, которые, в свою очередь, назначают меньшие блоки интернет-провайдерам (ISP). Ќаконец, ваш интернет-провайдер выдает вашему устройству его уникальный IP.
IPv4 против IPv6
Ѕольшинство устройств сегодн€ все еще используют IPv4, который выгл€дит так: 192.43.228.12. IPv4 основан на 32-битной системе и позвол€ет использовать около 4,3 миллиарда уникальных адресов. ќднако с миллиардами устройств, теперь наход€щихс€ в сети, IPv4-адреса заканчиваютс€.
»менно поэтому был введен IPv6. ќн использует 128-битные шестнадцатеричные числа (например: 5879:4a9d:f68c:64f1:7bf1:6aa2:3dc2:2d43), что позвол€ет получить 340 ундециллионов адресов — практически неограниченное количество. IPv6 также делает подключени€ более быстрыми и пр€мыми, поскольку каждое устройство может получить свой собственный уникальный IP.
¬ насто€щее врем€ около 30–35% пользователей »нтернета используют IPv6, и это число продолжает расти.
ѕубличный и частный IP
аждое устройство, подключенное к »нтернету, имеет либо публичный IP, либо частный IP:
- ѕубличный IP: виден в »нтернете, используетс€ вашим провайдером дл€ подключени€ вашей домашней или офисной сети.
- „астный IP: используетс€ только внутри локальных сетей (как ваш домашний Wi-Fi) и скрыт от посторонних.
Ќапример, ваш маршрутизатор использует публичный IP дл€ подключени€ к вебу, но ваш телефон или ноутбук внутри дома имеют только частный IP.
—татический и динамический IP
- —татический IP: остаетс€ неизменным и настраиваетс€ вручную.
- ƒинамический IP: регул€рно мен€етс€ и автоматически назначаетс€ DHCP-сервером вашего провайдера.
Ѕольшинство людей используют динамические IP, так как их проще управл€ть провайдерам, и они добавл€ют уровень конфиденциальности.
„то может раскрыть ваш IP-адрес?
¬аш IP-адрес содержит больше информации, чем вы могли бы подумать. ѕо нему другие часто могут оценить ваше:
- ѕримерное географическое местоположение
- ¬еб-сайты и сервисы, которые вы используете
- ¬озможные интересы и привычки
- ќрганизацию или компанию, к которой вы подключены
¬еб-сайты, рекламодатели, правоохранительные органы и даже киберпреступники могут отслеживать данные IP. Ќапример:
- ’акеры могут обманом заставить вас раскрыть ваш IP, а затем попытатьс€ использовать его.
- –екламодатели используют ваш IP, чтобы адаптировать рекламу под ваше поведение в сети.
- –аботодатели могут отслеживать активность сотрудников через IP, назначенные компанией.
- ѕравоохранительные органы используют данные IP дл€ отслеживани€ преступников при сотрудничестве с интернет-провайдерами.
ћожет ли кто-то узнать ваш IP-адрес?
ƒа. Ћюбой, имеющий доступ к вашему устройству, может его увидеть, а целеустремленные злоумышленники иногда могут раскрыть его через онлайн-взаимодействи€. ¬от почему защита вашего IP важна дл€ сохранени€ конфиденциальности.
ак скрыть свой IP-адрес
≈сли вы хотите большей анонимности в сети, скрытие вашего IP — один из первых шагов. ¬от наиболее распространенные методы:
- VPN (¬иртуальна€ частна€ сеть): ћаскирует ваш IP другим, но все еще может быть у€звима к утечкам или ведению логов.
- ѕрокси: Ќаправл€ет ваш трафик через другой сервер, чтобы скрыть ваш реальный IP.
- јнтидетект-браузеры: »нструменты, такие как BitBrowser, идут дальше, маскиру€ не только ваш IP, но и ваш цифровой отпечаток. Ёто помогает избежать обнаружени€ платформами и защищает вашу личность в сети.
’от€ ни один метод не гарантирует 100% анонимности, комбинаци€ инструментов, таких как VPN, прокси и антидетект-браузеры, обеспечивает более сильную защиту от отслеживани€ и профилировани€.
«аключительные мысли
¬аш IP-адрес — это ключ к вашей онлайн-идентичности: он соедин€ет вас с »нтернетом, но также раскрывает информацию о вас. ’от€ вы не можете полностью его скрыть, вы можете замаскировать его с помощью инструментов, таких как VPN, прокси и антидетект-браузеры, например BitBrowser.
ѕрин€тие этих мер предосторожности поможет вам сохранить лучшую конфиденциальность, безопасность и контроль над вашим цифровым следом.
|
|
BitBrowser против DlCloak: почему BitBrowser Ч лучший браузер дл€ защиты от обнаружени€ в 2025 году |
ќбзор
BitBrowser — это браузер с антидетектом, базирующийс€ в √онконге, разработанный дл€ того, чтобы помочь пользовател€м безопасно управл€ть несколькими аккаунтами и избежать обнаружени€ веб-сайтами. ќн особенно удобен дл€ таких задач, как электронна€ коммерци€, управление социальными сет€ми и интернет-маркетинг.
DlCloak (DICloak) — это более новый браузер с антидетектом, разработанный компанией DICloak Technology Limited, зарегистрированной в —ингапуре. ¬ыпущенный в 2024 году, он направлен на предоставление продвинутых возможностей подделки отпечатков браузера и управлени€ несколькими аккаунтами.
—равнение ключевых функций
÷ены
- BitBrowser: ѕредлагает бесплатный тариф с 10 профил€ми и платный тариф, стартующий примерно от 9 долларов в мес€ц дл€ до 50 профилей.
- DlCloak: ѕредлагает пробный период с 5 профил€ми и до 15 запусков в день; платные тарифы стартуют от 6,8 долларов в мес€ц.
»тоговый вердикт
-
’от€ DlCloak предлагает продвинутые функции и гибкость, BitBrowser €вно лидирует среди большинства пользователей. ≈го сочетание удобного дизайна, надежной интеграции прокси, поддержки автоматизации и инструментов совместной работы в команде делает его лучшим выбором дл€ начинающих, небольших команд и профессионалов, которые хот€т надежный контроль над несколькими аккаунтами без лишних сложностей.
|
|
ћобильный счет Sulhu faida'a kada'a wuzəna suro saa 2025 иен - Cloud Phone |

—егодн€, в услови€х быстрого развити€ цифрового бизнеса, всЄ больше студий и индивидуальных пользователей сталкиваютс€ с трудност€ми управлени€ несколькими аккаунтами, особенно в сферах трансграничной электронной коммерции и управлени€ социальными сет€ми. „астые операции с несколькими аккаунтами не только снижают эффективность, но и несут риск их взаимосв€зи, что может привести к блокировке. “ехнологи€ облачных телефонов постепенно становитс€ ключевым инструментом дл€ решени€ этих проблем.
„то такое облачный телефон?
ѕроще говор€, облачный телефон — это не физическое устройство, а виртуальна€ среда мобильного телефона, созданна€ на базе облачного сервера. ¬се его вычислительные ресурсы наход€тс€ на удалЄнном облачном сервере, а локальное устройство отвечает только за отображение и передачу команд управлени€. Ёто означает, что пользовател€м не нужно вкладывать большие средства в аппаратное обеспечение, чтобы получить высокопроизводительный мобильный компьютерный опыт.
„то могут облачные телефоны?
ћощные облачные вычислительные ресурсы облачного телефона позвол€ют выполн€ть такие высоконагруженные задачи, как одновременный запуск нескольких сложных приложений и обработка данных искусственным интеллектом, при этом пользователь может управл€ть ими в режиме реального времени через интернет-соединение. —тоит отметить, что фактический опыт использовани€ облачного телефона тесно св€зан с качеством сети. ¬ сет€х 5G или оптоволоконных сет€х (с задержкой менее 20 мс) пользователи почти не ощущают задержки, что позвол€ет достичь «воспринимаемого облачного вычислени€»; в услови€х плохой сети, даже при мощных облачных ресурсах, могут возникать задержки или ухудшение качества изображени€.
ѕочему стоит выбрать облачный телефон Bit Cloud Phone?
—реди множества решений дл€ облачных телефонов выдел€етс€ Bit Cloud Phone. ќснованный на мощных возможност€х управлени€ средой Bit Browser, он позвол€ет пользовател€м гибко настраивать параметры облачного телефона и поддерживает системы Android 12 и Android 15, что значительно повышает производительность и возможности защиты от взаимосв€зи нескольких аккаунтов.
ѕользователи могут быстро создавать несколько независимых сред облачного телефона через Bit Browser, кажда€ из которых может быть настроена с отдельным прокси, что эффективно предотвращает риск взаимосв€зи аккаунтов. Ѕудь то массовое управление аккаунтами в социальных сет€х, ведение магазинов трансграничной электронной коммерции или проведение зарубежных маркетинговых кампаний, Bit Cloud Phone может предоставить стабильную и надЄжную поддержку.
роме того, Bit Cloud Phone поддерживает загрузку приложений из Google Play Store, что позвол€ет пользовател€м беспреп€тственно запускать различные приложени€ Android в облачном телефоне. ‘ункци€ «Ќовый телефон в один клик» позвол€ет быстро создавать новую телефонную среду, а синхронизатор поддерживает пакетное управление несколькими облачными телефонами, что значительно повышает эффективность работы.
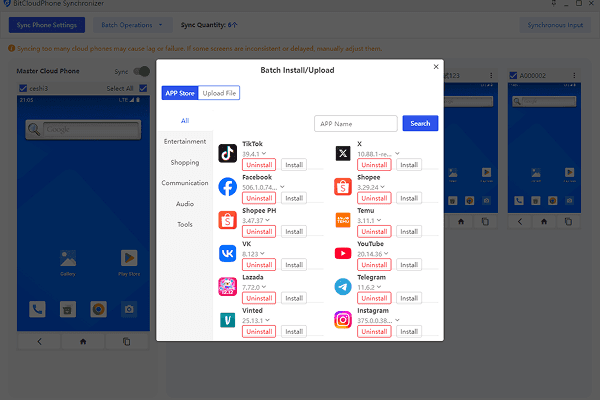
—тоит отметить, что Bit Cloud Phone предлагает гибкие способы контрол€ затрат: пользователи могут выбрать оплату по факту использовани€ или пакетный режим, что эффективно снижает порог входа. Ёта особенность особенно удобна дл€ стартапов и индивидуальных пользователей.
¬ывод:
¬ычислительные ресурсы телефона определ€ютс€ облачным сервером, а сетева€ среда €вл€етс€ ключевым фактором, вли€ющим на опыт использовани€. Bit Cloud Phone, как отличное решение дл€ облачного телефона, благодар€ своей мощной вычислительной поддержке и возможност€м управлени€ несколькими аккаунтами, предоставл€ет пользовател€м удобный и эффективный облачный опыт. ≈сли вы сталкиваетесь с трудност€ми управлени€ несколькими аккаунтами, попробуйте Bit Cloud Phone — возможно, он принесЄт новый прорыв в ваш бизнес.
|
|
„то такое Cloud Phone ADB? „то он может делать? ак его включить? |

¬ цифровом мире мы ежедневно взаимодействуем с различными устройствами, и как наш самый близкий спутник, технические принципы, лежащие в основе мобильных телефонов, привлекают все больше внимани€. огда речь идет о глубоких операци€х с телефонами на Android, часто упоминаетс€ инструмент под названием ADB.
„то такое ADB и что он может делать?
ADB (Android Debug Bridge — портативный отладчик Android) — это мощный командный инструмент, предоставленный Google дл€ разработчиков Android. ѕроще говор€, он выступает в роли моста, соедин€ющего ваш компьютер с устройством на Android, позвол€€ вам выполн€ть более глубокое управление и контроль над телефоном через компьютер.
— помощью ADB мы можем выполн€ть множество действий:
-”становка и управление приложени€ми: помимо обычной установки через магазины приложений, ADB позвол€ет пакетно устанавливать или удал€ть приложени€ в тихом режиме, что очень эффективно дл€ разработчиков или пользователей, которым нужно тестировать большое количество приложений.
-ѕередача файлов: быстро передавать файлы между компьютером и телефоном, особенно системные файлы, к которым нельз€ получить доступ обычными способами.
-¬ыполнение команд Shell: ADB предоставл€ет доступ к Shell системы Android, что означает, что вы можете выполн€ть различные команды на уровне €дра Linux, например, просматривать системные журналы, получать подробную информацию об устройстве и даже измен€ть сетевые настройки.
-јвтоматизированные операции: в сочетании с определенными сценари€ми и инструментами ADB позвол€ет выполн€ть автоматизированное тестирование, например, имитировать клики пользовател€, прокрутки и другие операции, что очень полезно в игровых студи€х или сфере тестировани€ приложений.
ѕоддерживает ли Ѕит-ќблачный “елефон ADB?
—егодн€ с ростом технологий облачных телефонов все больше людей начинают использовать виртуальные телефоны в облаке. ак ведущий провайдер услуг облачных телефонов, Ѕит-ќблачный “елефон также прекрасно понимает ценность ADB дл€ пользователей. „тобы удовлетворить потребности в разработке, тестировании и других расширенных операци€х, Ѕит-ќблачный “елефон полностью поддерживает функцию ADB.
Ёто означает, что даже если телефон не в ваших руках, вы можете подключитьс€ к Ѕит-ќблачному “елефону в облаке через сеть и использовать ADB дл€ выполнени€ различных операций отладки, при этом функциональность така€ же, как у локального телефона. Ётот метод виртуализации не только делает операции более гибкими, но и облегчает управление несколькими устройствами. Ќапример, вы можете использовать ADB дл€ пакетного контрол€ нескольких Ѕит-ќблачных “елефонов, реализу€ групповой контроль, что значительно повышает эффективность работы.
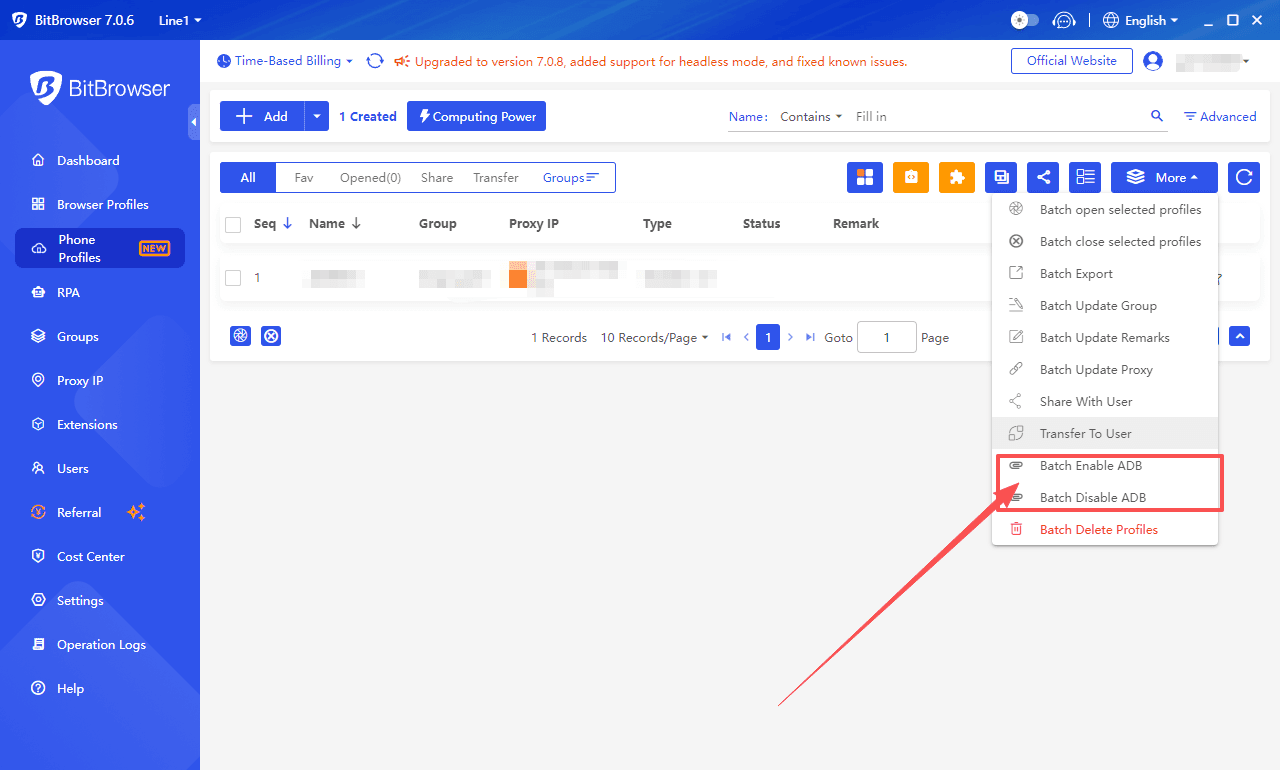
ак включить ADB на Ѕит-ќблачном “елефоне?
¬ключение функции ADB на Ѕит-ќблачном “елефоне очень просто и включает в себ€ в основном следующие шаги:
1. ¬ключение функции ADB:
—начала в интерфейсе управлени€ Ѕит-ќблачным “елефоном найдите экземпл€р облачного телефона, с которым вы хотите работать. ѕосле выбора нажмите «ƒополнительные операции» или аналогичную опцию, затем выберите «¬ключить ADB», чтобы активировать режим отладки. ≈сли вам нужно одновременно работать с несколькими облачными телефонами, вы также можете использовать функцию «ѕакетное включение ADB», чтобы сделать это за один раз.
2. ѕолучение информации дл€ подключени€:
ѕосле включени€ ADB вам нужно получить адрес и код проверки, необходимые дл€ подключени€. ¬ интерфейсе управлени€ наведите курсор мыши на статус ADB облачного телефона — будет отображен IP-адрес, порт и код проверки подключени€. Ёта информаци€ €вл€етс€ ключом к подключению к облачному телефону.
3. Ћокальное подключение и отладка:
Ќа вашем компьютере откройте терминал или командную строку и введите `adb connect
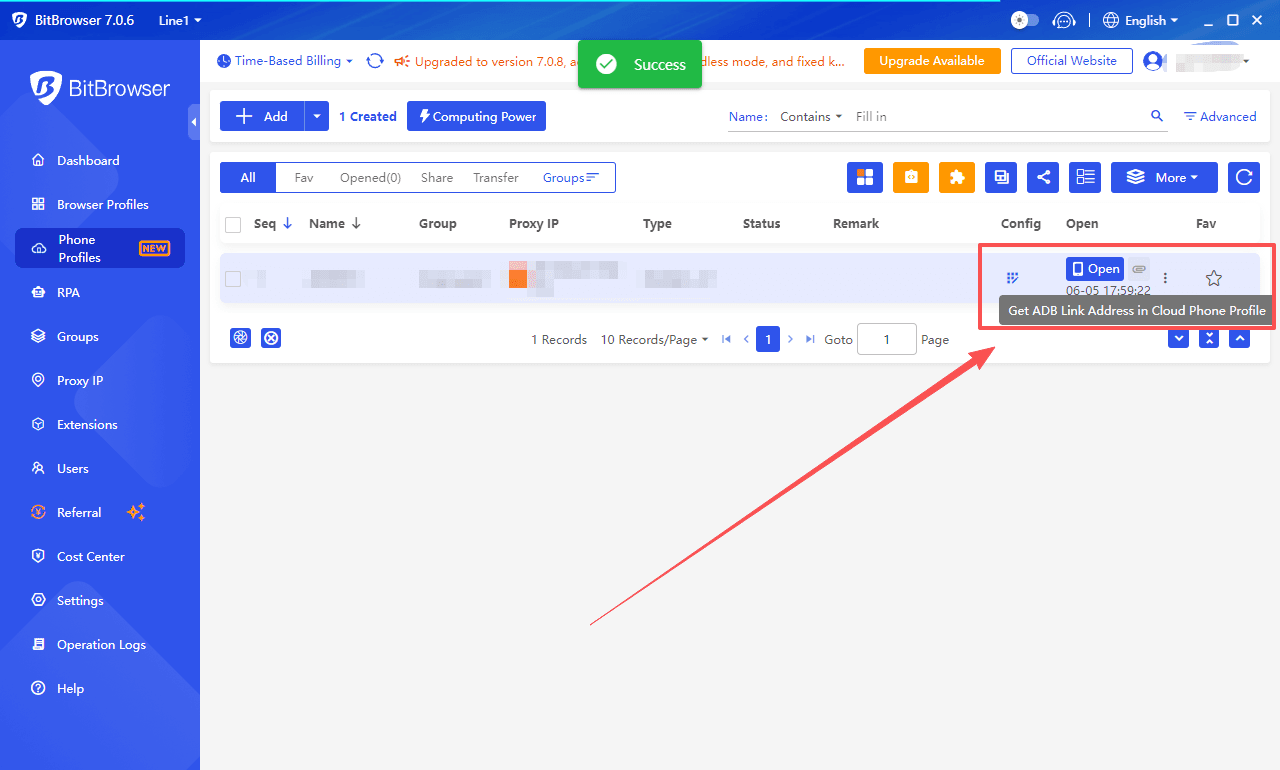
»тог:
“аким образом, Ѕит-ќблачный “елефон делает сложные облачные операции проще и более эффективными, предоставл€€ пользовател€м мощный инструмент дл€ удовлетворени€ различных профессиональных и непрофессиональных потребностей. — продолжающимс€ технологическим прогрессом можно уверенно сказать, что в будущем в облачные телефоны будут интегрированы еще более эффективные и практичные функции, делающие нашу цифровую жизнь удобнее.
|
|
—инхронна€ работа нескольких аккаунтов мобильных телефонов |

¬ цифровую эпоху, будь то кросс-бордерный электронный коммерци€, управление социальными сет€ми или многоэкземпл€рное тестирование игр, часто возникает необходимость одновременно управл€ть несколькими аккаунтами или приложени€ми. “радиционно пользовател€м приходилось готовить несколько физических мобильных телефонов, подключать их к компьютеру через кабели данных и использовать программное обеспечение дл€ централизованного управлени€. Ётот метод работает, когда количество устройств невелико, но при расширении масштабов стоимость оборудовани€, управление кабел€ми и сложность эксплуатации значительно возрастают. —уществует ли более легкий и гибкий способ? ќтвет положительный. Ѕлагодар€ облачной технологии теперь возможно реализовать виртуализированное управление несколькими устройствами посредством «облачных телефонов» и в сочетании с функцией синхронизатора значительно повысить эффективность работы.
1. „то такое синхронизатор облачных телефонов?
—инхронизатор облачных телефонов — не сложный концепт; это инструмент, который обеспечивает реалтайм-синхронизацию операций между несколькими симулированными мобильными телефонами, размещенными в облаке (то есть облачными телефонами). ≈го основна€ иде€ очень интуитивна: вам нужно управл€ть только одним облачным телефоном в качестве главного окна управлени€, и все действи€, такие как клики, ввод данных и свайпы, автоматически и бесшовно дублируютс€ во всех подключенных подчиненных окнах.
ѕредставьте себе управление несколькими аккаунтами интернет-магазинов, матрицами социальных сетей или игровыми задачами — раньше вам приходилось повтор€ть одни и те же операции сотни раз. Ќо с синхронизатором эти повтор€ющиес€ задачи упрощаютс€ до одного клика. Ќапример, когда вы массово публикуете маркетинговый текст на главном телефоне, другие облачные телефоны одновременно завершают ввод и отправку текста, значительно повыша€ эффективность массовых операций.
2. Bit Cloud Phone: —оздание эффективной облачной рабочей станции дл€ вас
¬ услови€х такого эффективного взаимодействи€ Bit Cloud Phone, как инновационный продукт на рынке, предоставл€ет стабильную и надежную облачную среду Android. ќн позвол€ет гибко создавать любое количество виртуальных телефонов в соответствии с бизнес-требовани€ми, без необходимости покупать и обслуживать большое количество физических устройств. аждый Bit Cloud Phone имеет независимую идентичность и среду, что гарантирует безопасность работы с несколькими аккаунтами и их изол€цию.
‘ункци€ синхронизатора Bit Cloud Phone正是 €вл€етс€ ключом к реализации «управление одним, а несколько сред реагируют одновременно».
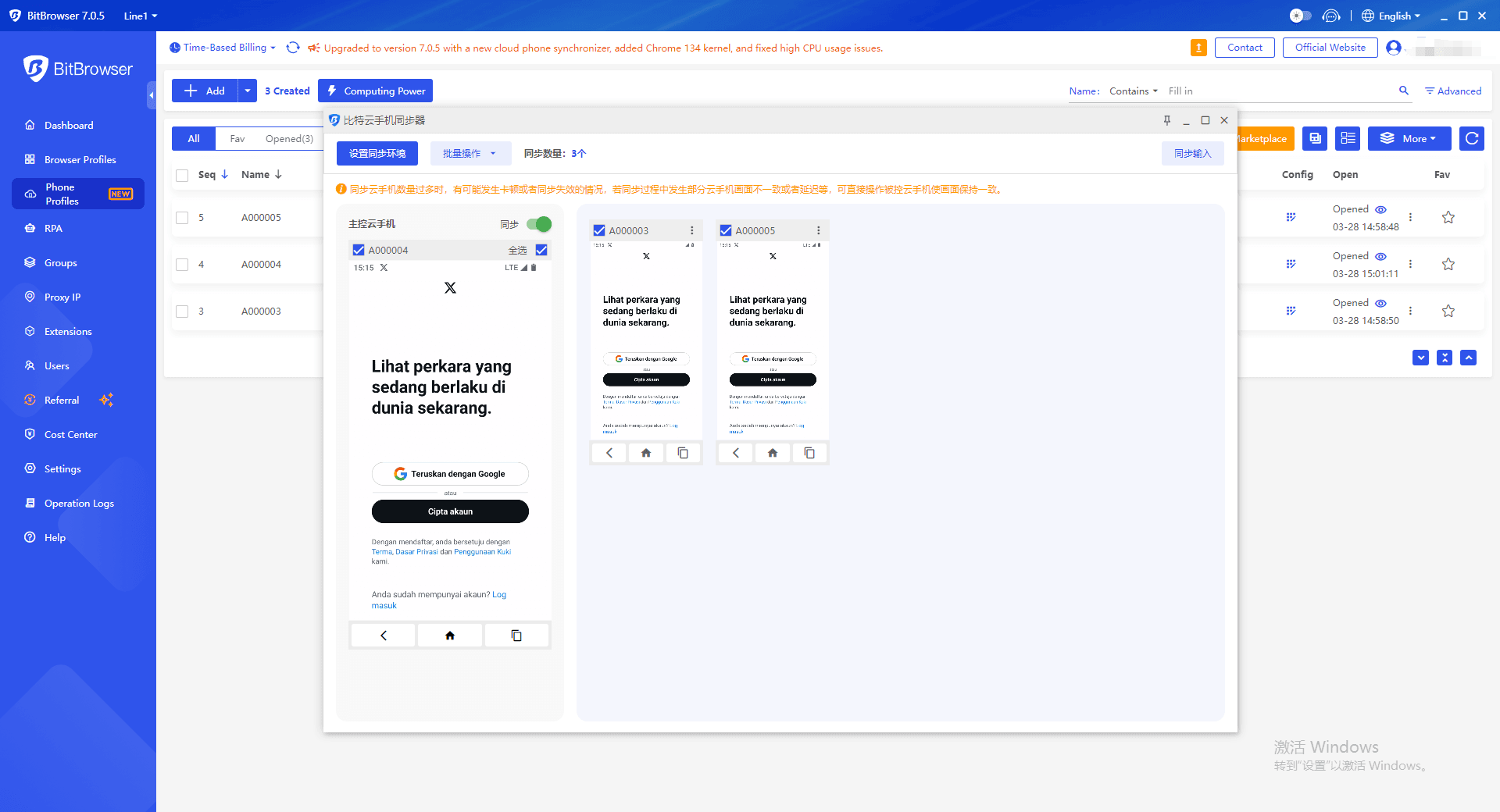
ќбзор основных функций:
1. √лобальна€ синхронизированна€ операци€: ѕолна€ совместимость с мышью и клавиатурой, обеспечивающа€ точную синхронизацию действий от главного терминала управлени€ ко всем подчиненным терминалами без задержек.
2. ћассовое управление: ѕоддержка массового запуска, установки или удалени€ приложений, упрощающа€ работу по управлению приложени€ми.
3. √ибкий ввод текста: ѕоддержка массового ввода одинакового или разного текста, что имеет решающее значение дл€ массовой регистрации нескольких аккаунтов, входа в систему или выполнени€ конкретных поисковых задач.
4. Ѕыстра€ передача файлов: ѕредоставление функции массовой загрузки файлов, позвол€ющей быстро распростран€ть как видеоматериалы, так и конфигурационные сценарии на все устройства.
5. ћассовые операции: Ќапример, массова€ установка приложений, едина€ загрузка файлов, одновременное включение/выключение звука и т.д.
ѕеред использованием синхронизатора пользовател€м сначала необходимо создать как минимум две облачные телефонные среды одного типа. ѕосле входа в консоль нажмите на функцию «—инхронизатор», отметьте окна, которые нужно синхронизировать, и назначьте одно из них главным терминалом управлени€. ѕосле подтверждени€ все отмеченные облачные телефоны переход€т в состо€ние синхронизации. ¬ это врем€ операции, выполн€емые на главном терминале управлени€ — такие как запуск приложений, ввод текста, просмотр контента — одновременно дублируютс€ на других облачных телефонах. роме того, синхронизатор Bit Cloud Phone позвол€ет пользовател€м динамически регулировать главные и подчиненные среды, а также даже устанавливать задержки кликов дл€ имитации более реалистичных действий пользовател€, помога€ повысить эффективность бизнеса и сэкономить средства.
ѕримечание: ƒл€ обеспечени€ эффективности синхронизации все облачные телефоны, участвующие в синхронизации, должны быть одного типа по вычислительной мощности. –екомендуетс€ подобрать стабильную сеть и независимый IP-адрес, чтобы избежать неполадок в работе, вызванных различи€ми сред или колебани€ми сети.
3. ому нужен синхронизатор облачных телефонов?
«начение синхронизатора облачных телефонов заключаетс€ в том, что он позвол€ет снизить издержки и повысить эффективность. ќн стал ключевым инструментом в нескольких отрасл€х:
росс-бордерное управление несколькими магазинами: ≈диное управление дес€тками магазинов на платформах вроде Amazon и Shopee, массовое обновление информации и избегание рисков св€зывани€ аккаунтов.
ћаркетинг в матрице социальных сетей: ћассова€ публикаци€ контента на платформах вроде TikTok и Instagram, быстрое охват глобальной аудитории и достижение матричного привлечени€ трафика.
»гровые студии: ќдновременный запуск нескольких игровых аккаунтов, синхронное выполнение задач, прохождение подземелий или автоматические действи€ (AFK, away from keyboard), значительно повыша€ эффективность получени€ ресурсов.
»тог:
ƒл€ сценариев, таких как управление несколькими магазинами в кросс-бордерном электронном коммерции, управление матрицей социальных сетей и автоматизированное тестирование, синхронизатор облачных телефонов не только экономит много времени, затрачиваемого на повтор€ющиес€ операции, но и снижает затраты на обслуживание оборудовани€ дл€ нескольких устройств. ≈сли вы ищете способ повысить эффективность работы с несколькими аккаунтами, рекомендуем попробовать функцию синхронизатора Bit Cloud Phone — она может открыть дл€ вас новые возможности дл€ эффективного управлени€ и эксплуатации.
|
|
„то такое функци€ ЂЌовый телефон одним кликомї на BitCloud Phone? „то она может делать? |

¬ отличие от физических телефонов, облачные телефоны предоставл€ют пользовател€м беспрецедентную удобство благодар€ уникальной функции «ќдин клик — новое устройство». “ак называемое «одно клик — новое устройство» позвол€ет быстро создать совершенно новую виртуальную телефонную среду в облаке с помощью одного простого действи€. »нформаци€ о оборудовании, така€ как отпечаток устройства, модель и серийный номер, полностью сбрасываютс€. Ёто означает, что пользователи могут получить «новый» телефон в любое врем€, не покупа€ новый физический аппарат и не выполн€€ сложных операций по перепрошивке, что значительно снижает затраты и повышает эффективность.
ѕочему облачные телефоны нуждаютс€ в функции «ќдин клик — новое устройство»?
¬о многих деловых сценари€х, например, при работе с аккаунтами и тестировании рекламы, часто необходимо мен€ть устройства, чтобы избежать детектировани€ системой контрол€ рисков платформы. “радиционный подход заключаетс€ в покупке большого количества телефонов или изменении информации о устройстве через перепрошивку, но этот метод не только дорог и громоздкий, но и неэффективен.
‘ункци€ Bit Cloud Phone «ќдин клик — новое устройство» идеально решает эти проблемы. ќна использует переданную виртуализационную технологию дл€ восстановлени€ совершенно новой виртуальной среды за чрезвычайно короткое врем€. Ётот метод не только дешевле, но и позвол€ет создавать новые среды устройств неограниченное количество раз, помога€ пользовател€м легко управл€ть большим количеством аккаунтов или выполн€ть несколько раундов тестировани€.
„то может сделать функци€ Bit Cloud Phone «ќдин клик — новое устройство»?
‘ункци€ «один клик — новое устройство»远远超出 этого, и функци€ Bit Cloud Phone «ќдин клик — новое устройство» имеет важную прикладную ценность «ќдин клик — новое устройство» в многих отрасл€х:
1. Ѕорьба с ассоциацией дл€ нескольких аккаунтов
ћногие платформы, такие как Amazon и Shopify, строго ограничивают вход нескольких аккаунтов на одном устройстве. — помощью функции «один клик — новое устройство» пользователи могут назначить отдельный отпечаток устройства каждому магазину или аккаунту, физически разорвав св€зь и эффективно снизив риск блокировки.
2. A/B-тестирование дл€ размещени€ рекламы
–екламодатели необходимо тестировать эффективность конверсии рекламных материалов на разных модел€х устройств. — помощью функции «один клик — новое устройство» они могут быстро генерировать различные виртуальные среды (например, iPhone, Samsung и т.д.) дл€ точного A/B-тестировани€ и оптимизации стратегии размещени€.
3. ѕакетное управление матрицей аккаунтов
ƒл€ пользователей, которые необходимо управл€ть большим количеством аккаунтов социальных сетей (например, TikTok, Instagram), функци€ «один клик — новое устройство» позвол€ет быстро регистрировать новые аккаунты и предоставл€ть каждому аккаунту отдельную рабочую среду. ¬ сочетании с автоматизированными скриптами они могут выполн€ть пакетные операции, такие как развитие аккаунтов и публикаци€ контента, повыша€ эффективность.
4. ћногократный запуск игр и автоигра (AFK)
ћногие игры детектируют поведение пользователей, св€занное с многократным запуском игры на одном устройстве. — помощью функции «один клик — новое устройство» пользователи могут запускать несколько экземпл€ров игры на одном устройстве, при этом каждый экземпл€р имеет отдельную рабочую среду, эффективно избега€ детектировани€ производител€ми игр.
ак начать использовать функцию Bit Cloud Phone «ќдин клик — новое устройство»?
„тобы опробовать функцию Bit Cloud Phone «ќдин клик — новое устройство», пользовател€м只需 найти кнопку «один клик — новое устройство» в приложении Bit Cloud Phone и выбрать режим случайного или пользовательского создани€, чтобы быстро генерировать новую среду устройства. Ёто устран€ет громоздкий процесс замены устройств и позвол€ет пользовател€м сосредоточитьс€ больше на самом бизнесе.
»тог:
‘ункци€ «один клик — новое устройство» в Bit Cloud Phone поддерживает пользовательскую смену нескольких брендов, позвол€€ пользовател€м маскировать облачный телефон под любую указанную модель бренда в соответствии с их потребност€ми. –ежим работы делитс€ на случайное создание нового устройства (автоматическа€ генераци€ новых данных) и пользовательское создание нового устройства (ручной ввод параметров). ¬се операции выполн€ютс€ в облаке, и информаци€ о устройстве может быть полностью изменена за один клик, чтобы обеспечить бесперебойное проведение бизнеса.
оротко говор€, функци€ «один клик — новое устройство» в Bit Cloud Phone предоставл€ет пользовател€м эффективную и экономичную возможность смены среды устройства за счет восстановлени€ ключевых параметров устройства, и стала неотъемлемым инструментом в сценари€х, таких как работа с аккаунтами и тестирование рекламы. —ледует отметить, что в насто€щее врем€ эта функци€ доступна только дл€ тарифов с вычислительной мощностью по пакету, а дл€ временной вычислительной мощности еще не предусмотрена.
¬ы ищете более эффективный и экономичный способ управлени€ вашим бизнесом с несколькими аккаунтами? Bit Cloud Phone может быть лучшим выбором дл€ вашего бизнеса.
|
|
ћобильный счет Sulhu faida'a kada'a wuzəna suro saa 2025 иен - Cloud Phone |

—егодн€, в услови€х быстрого развити€ цифрового бизнеса, всЄ больше студий и индивидуальных пользователей сталкиваютс€ с трудност€ми управлени€ несколькими аккаунтами, особенно в сферах трансграничной электронной коммерции и управлени€ социальными сет€ми. „астые операции с несколькими аккаунтами не только снижают эффективность, но и несут риск их взаимосв€зи, что может привести к блокировке. “ехнологи€ облачных телефонов постепенно становитс€ ключевым инструментом дл€ решени€ этих проблем.
„то такое облачный телефон?
ѕроще говор€, облачный телефон — это не физическое устройство, а виртуальна€ среда мобильного телефона, созданна€ на базе облачного сервера. ¬се его вычислительные ресурсы наход€тс€ на удалЄнном облачном сервере, а локальное устройство отвечает только за отображение и передачу команд управлени€. Ёто означает, что пользовател€м не нужно вкладывать большие средства в аппаратное обеспечение, чтобы получить высокопроизводительный мобильный компьютерный опыт.
„то могут облачные телефоны?
ћощные облачные вычислительные ресурсы облачного телефона позвол€ют выполн€ть такие высоконагруженные задачи, как одновременный запуск нескольких сложных приложений и обработка данных искусственным интеллектом, при этом пользователь может управл€ть ими в режиме реального времени через интернет-соединение. —тоит отметить, что фактический опыт использовани€ облачного телефона тесно св€зан с качеством сети. ¬ сет€х 5G или оптоволоконных сет€х (с задержкой менее 20 мс) пользователи почти не ощущают задержки, что позвол€ет достичь «воспринимаемого облачного вычислени€»; в услови€х плохой сети, даже при мощных облачных ресурсах, могут возникать задержки или ухудшение качества изображени€.
ѕочему стоит выбрать облачный телефон Bit Cloud Phone?
—реди множества решений дл€ облачных телефонов выдел€етс€ Bit Cloud Phone. ќснованный на мощных возможност€х управлени€ средой Bit Browser, он позвол€ет пользовател€м гибко настраивать параметры облачного телефона и поддерживает системы Android 12 и Android 15, что значительно повышает производительность и возможности защиты от взаимосв€зи нескольких аккаунтов.
ѕользователи могут быстро создавать несколько независимых сред облачного телефона через Bit Browser, кажда€ из которых может быть настроена с отдельным прокси, что эффективно предотвращает риск взаимосв€зи аккаунтов. Ѕудь то массовое управление аккаунтами в социальных сет€х, ведение магазинов трансграничной электронной коммерции или проведение зарубежных маркетинговых кампаний, Bit Cloud Phone может предоставить стабильную и надЄжную поддержку.
роме того, Bit Cloud Phone поддерживает загрузку приложений из Google Play Store, что позвол€ет пользовател€м беспреп€тственно запускать различные приложени€ Android в облачном телефоне. ‘ункци€ «Ќовый телефон в один клик» позвол€ет быстро создавать новую телефонную среду, а синхронизатор поддерживает пакетное управление несколькими облачными телефонами, что значительно повышает эффективность работы.

—тоит отметить, что Bit Cloud Phone предлагает гибкие способы контрол€ затрат: пользователи могут выбрать оплату по факту использовани€ или пакетный режим, что эффективно снижает порог входа. Ёта особенность особенно удобна дл€ стартапов и индивидуальных пользователей.
¬ывод:
¬ычислительные ресурсы телефона определ€ютс€ облачным сервером, а сетева€ среда €вл€етс€ ключевым фактором, вли€ющим на опыт использовани€. Bit Cloud Phone, как отличное решение дл€ облачного телефона, благодар€ своей мощной вычислительной поддержке и возможност€м управлени€ несколькими аккаунтами, предоставл€ет пользовател€м удобный и эффективный облачный опыт. ≈сли вы сталкиваетесь с трудност€ми управлени€ несколькими аккаунтами, попробуйте Bit Cloud Phone — возможно, он принесЄт новый прорыв в ваш бизнес.
|
|
Ёмул€ци€ ввода браузера: основна€ технологи€, лежаща€ в основе обнаружени€ антибраузеров |

¬ сценари€х, требующих управлени€ несколькими аккаунтами (например, трансгранична€ электронна€ коммерци€ или маркетинг в соцсет€х), антифрод-системы платформ посто€нно отслеживают поведение пользователей. ѕаттерны ввода с клавиатуры — ключевой показатель дл€ вы€влени€ автоматизированных операций. ѕр€ма€ вставка текста через Ctrl+V легко определ€етс€ как механическое поведение, что ведЄт к блокировкам аккаунтов. ’от€ ручной ввод выгл€дит естественно, он неэффективен и раскрывает уникальные ритмы печати (например, врем€ нажати€ клавиш), создава€ риски кросс-аккаунтной ассоциации.
“ехнологи€ »митации ¬вода (например, Human-Like Input HLI) стала решением. ќна воспроизводит последовательности событий клавиатуры реальных пользователей (keydown, keyup) и состо€ни€ модификаторов (Shift, Ctrl), воссоздава€ случайность и ритм человеческого ввода при вставке текста. ѕримеры:
• “очное срабатывание событий: ¬вод заглавной "T" требует одновременной активации событи€ нажати€ Shift с корректным event.key ("T" вместо "t").
• ћаскировка типа ввода: «амена тегов "insert from paste" генерацией событий "insertText", чтобы платформы воспринимали действи€ как ручной ввод.
• ƒинамическа€ имитаци€ ритма: ”никальные временные интервалы между нажати€ми дл€ разных аккаунтов предотвращают ассоциацию через "ƒЌ печати".
Bit Browser совершенствует эту технологию. ≈го функци€ имитации глубоко воспроизводит базовую логику поведени€ реальных браузеров:
1. ѕоддержка ѕолного ÷ифрового ќтпечатка: јвтоматическое соответствие прокси-IP с временной зоной, €зыком и разрешением, гарантиру€ синхронизацию поведени€ ввода с географическими данными.
2. ќптимизаци€ на уровне событий: “очна€ обработка свойств событий (keyCode, inputType), исключающа€ типичные ошибки конкурентов (потер€ модификаторов или нарушение последовательности событий).
3. ћультисценарна€ совместимость: ”спешное тестирование на регистрацию/вход в системах вроде TypingDNA с стабильным ростом счЄтчиков, подтверждающим эффективность имитации.
ќтраслевые сравнени€ показывают: конкуренты ограничиваютс€ посимвольной вставкой (с триггером insertFromPaste) или игнорируют состо€ни€ Shift, что приводит к провалам в обходе детекции. Ћогика имитации BitBrowser максимально приближена к поведению Chrome, значительно снижа€ риски ассоциации.
ѕочему ¬ыбрать BitBrowser?
”правление магазинами Amazon, работа с аккаунтами TikTok или зарубежные рекламные кампании — BitBrowser предоставл€ет комплексное антидетект-решение:
• 10 Ѕесплатных —ред: «апуск мультиаккаунтного управлени€ без затрат с поддержкой Windows/macOS.
• »нтеграци€ с автоматизацией: Ѕесшовна€ работа с Selenium/Puppeteer при сохранении реалистичности имитации ввода в пакетных операци€х.
• —инхронизаци€ прокси: ¬строенный менеджер прокси (HTTP/SOCKS5) автоматически синхронизирует локацию IP с цифровыми отпечатками (временна€ зона, €зык).

ѕредставьте: пока конкуренты провоцируют блокировки грубой вставкой, вы используете имитацию BitBrowser дл€ безопасных пакетных входов, размещени€ товаров или ответов покупател€м в 10 изолированных средах — так технологическое превосходство создаЄт операционные барьеры.
—ейчас BitBrowser предлагает бесплатный пробный период. —качайте и зарегистрируйтесь дл€ получени€ 10 посто€нных бесплатных окон.
|
|
Ћучшие решени€ RPA 2025 года |

¬ 2025 году, с усложнением цифровых рабочих процессов, технологи€ автоматизации браузера (RPA) стала ключевым инструментом дл€ повышени€ эффективности. Ѕудь то сбор данных, управление несколькими учетными запис€ми или выполнение ежедневных повтор€ющихс€ задач, решени€ по автоматизации могут значительно сократить ручное вмешательство, снизить количество ошибок и высвободить ценные человеческие ресурсы.
I. «ачем вам нужна автоматизаци€ браузера (RPA)?
1. “ехнологи€ изол€ции среды дл€ нескольких учетных записей
»нструменты автоматизации должны создавать независимую рабочую среду дл€ каждой учетной записи, чтобы избежать св€зи данных через файлы cookie, кэш, отпечатки браузера и другие данные. Ќапример, Bitbrowser использует двухъ€дерную архитектуру (Chrome + Firefox), динамически генериру€ отпечатки Canvas/WebGL и назнача€ независимые IP-адреса и параметры устройства каждому профилю, полностью обход€ обнаружение св€зей на платформе. оманда трансграничной электронной коммерции использовала эту функцию дл€ одновременного управлени€ более чем 50 учетными запис€ми магазинов Amazon, снизив показатель приостановки учетных записей на 87%.
2. ¬озможность выполнени€ автоматизации RPA
¬изуальный дизайн сценариев €вл€етс€ основой повышени€ эффективности. Bitbrowser предоставл€ет конструктор рабочих процессов с возможностью перетаскивани€, позвол€€ пользовател€м быстро создавать задачи с полным циклом, такие как «вход в систему, просмотр и взаимодействие». Ќапример, команда по управлению социальными сет€ми, заранее настроив врем€ публикации и стратегии взвешивани€ взаимодействи€, смогла выполнить холодный старт более 100 учетных записей в течение 7 дней, эконом€ в среднем 6 часов ручного управлени€ в день. ≈го модуль RPA также поддерживает интеллектуальные настройки временной шкалы дл€ имитации циклов работы и отдыха человека, эффективно снижа€ веро€тность контрол€ рисков на платформе.
3. —истема безопасности и защиты данных
Ѕезопасна€ обработка файлов cookie €вл€етс€ основной задачей автоматизации. Bitbrowser использует технологию Cookie Sandbox дл€ автоматической блокировки сторонних сценариев отслеживани€, а также поддерживает массовый импорт и экспорт данных cookie в формате ZIP. –екламна€ команда использовала эту функцию дл€ синхронизации учетных данных дл€ входа дл€ более чем 100 рекламных учетных записей без ручного вмешательства и риска утечки информации. ≈го система ведени€ журнала может записывать метку времени и IP-след каждой операции, что соответствует требовани€м корпоративного аудита.
II. ¬ каких сценари€х используетс€ автоматизаци€ браузера (RPA)?
1. ѕроверка рекламы и оптимизаци€ кампаний
»нструменты автоматизации могут в пакетном режиме провер€ть достоверность рекламных ссылок и скорость загрузки целевых страниц. оманда онлайн-торговли использовала Bitbrowser дл€ выполнени€ проверки соответстви€ 200 рекламных мест за 1 час, что в 20 раз превысило эффективность ручных операций. ¬ сочетании с динамическим чередованием IP-адресов он может имитировать поведение пользователей из разных регионов дл€ точного тестировани€ эффективности рекламной кампании.
2. ”правление несколькими магазинами трансграничной электронной коммерции
“ехнологи€ изол€ции среды Bitbrowser создает уникальный отпечаток дл€ каждой учетной записи магазина, а в сочетании с пулом IP-ресурсов жилых прокси-серверов она может одновременно запускать сотни учетных записей без обнаружени€ платформами. ѕродавец трансграничной торговли сократил ежедневные эксплуатационные расходы одного магазина на 40% за счет автоматизированных процессов дл€ размещени€ товаров, корректировки цен и ответа на запросы клиентов.
3. —бор и анализ данных
¬ сценари€х сбора данных Bitbrowser поддерживает обход механизмов защиты от ботов, таких как Cloudflare. јгентство по исследованию рынка использовало свой модуль RPA дл€ ежедневного извлечени€ данных о ценах и запасах с более чем 50 веб-сайтов конкурентов и автоматического создани€ многомерных аналитических отчетов посредством интеграции API, что экономит 20 часов ручной обработки в неделю.
III. ак начать работу с автоматизацией браузера (RPA)? »нструменты и предложени€ по реализации
1. ”правление иерархическими разрешени€ми
”становите права доступа дл€ членов команды. Ќапример, младшие сотрудники могут выполн€ть только предустановленные задачи, в то врем€ как администраторы могут измен€ть сценарии и профили. јгентство цифрового маркетинга сократило количество сбоев задач, вызванных человеческим фактором, на 65% с помощью этой стратегии.
2. ћеханизм мониторинга аномалий
¬ключите журналы в реальном времени и уведомлени€ по электронной почте, чтобы автоматически приостанавливать задачи при возникновении аномалий, таких как запросы CAPTCHA или блокировки IP-адресов. »нтерфейс LocalAPI Bitbrowser может быть интегрирован с корпоративными системами CRM дл€ достижени€ автоматизации статусов заказов на основе триггеров.
3. ƒизайн операций, ориентированный на соответствие требовани€м
»збегайте частого доступа к одному и тому же веб-сайту, и рекомендуетс€ устанавливать интервалы задач (например, выполн€ть один раз в 30 минут). оманда партнерского маркетинга, имитиру€ реальные модели поведени€ пользователей, увеличила CTR рекламы на 32% без срабатывани€ систем защиты от мошенничества платформы.
«аключение:
¬ 2025 году автоматизаци€ браузеров (RPA) будет развиватьс€ в сторону «интеллекта + сценарных приложений». Ќапример, Bitbrowser добилс€ глубокой интеграции с системами обслуживани€ клиентов с искусственным интеллектом, автоматически анализиру€ комментарии пользователей и генериру€ содержимое ответов с помощью технологии NLP. — попул€ризацией технологии Web3.0 инструменты автоматизации также будут поддерживать новые сценарии, такие как операции с блокчейн-узлами и развертывание смарт-контрактов, предоставл€€ поддержку предпри€ти€м дл€ создани€ комплексной системы цифровых операций.
¬ыбор инструмента с трем€ основными возможност€ми: изол€ци€ среды, автоматизаци€ RPA и защита безопасности - €вл€етс€ ключевым дл€ предпри€тий, чтобы создать конкурентное преимущество в цифровом ландшафте. –екомендуетс€ начать с тестировани€ с помощью 10 бесплатных профилей Bit Fingerprint Browser и постепенно расшир€ть до сложных бизнес-сценариев, достига€ как эффективности, так и безопасности.
|
|






