What Is the Most Secure Phone? iPhone vs Android |
The attacker can also utilize this approach to call paid services, resulting in a charge to the owner of the mobile phone. It is likewise really unsafe because the smartphone might call emergency situation services and hence interfere with those solutions; A jeopardized smartphone can videotape discussions in between the customer as well as others and also send them to a 3rd celebration.
This raises protection worries in nations where smart devices can be used to location orders, view financial institution accounts or are made use of as an identity card; The opponent can minimize the energy of the smart device, by releasing the battery. They can launch an application that will run continuously on the smartphone cpu, calling for a great deal of power as well as draining the battery.
Frank Stajano and Ross Anderson first described this kind of assault, calling it an assault of "battery exhaustion" or "rest starvation torment"; The assaulter can protect against the procedure and/or be beginning of the mobile phone by making it unusable., or change certain documents to make it unusable (e.
a script that launches at introduces that forces the requires to smart device) reactivate even embed also installed application start-up would empty the clear; The attacker can opponent the personal (individual, music, videos, etc) or professional data Expertinformation, calls, notes) of the user.
Secure Call
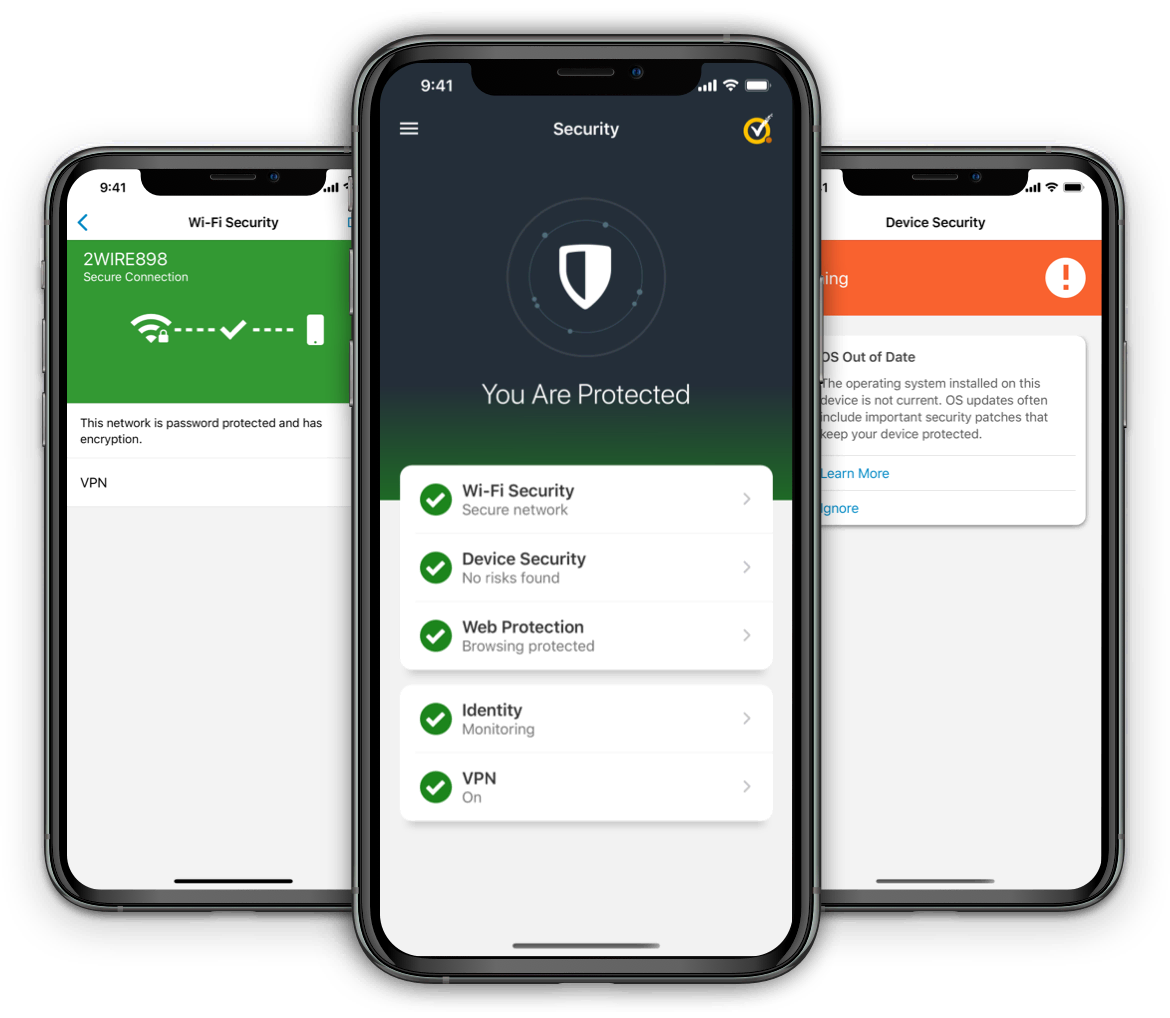 The 11 Best Privacy and Security Apps for Android
The 11 Best Privacy and Security Apps for AndroidIt is possible, by sending an ill-formed block, to cause the phone to reactivate, bring about the denial of service attacks. If a customer with a Siemens S55 got a text message including a Chinese personality, it would bring about a denial of solution. In another situation, while the requirement requires that the optimum dimension of a Nokia Mail address is 32 characters, some Nokia phones did not validate this criterion, so if a customer goes into an email address over 32 personalities, that causes complete dysfunction of the e-mail handler as well as puts it out of order.
A research study on the safety of the SMS infrastructure revealed that SMS messages sent out from the Net can be used to perform a dispersed denial of service (DDo, S) assault versus the mobile telecom infrastructure of a huge city. The assault makes use of the hold-ups in the delivery of messages to overload the network.
This add-on is infected with a virus. Upon invoice of the MMS, the customer can pick to open up the accessory. If it is opened up, the phone is infected, and also the infection sends out an MMS with an infected accessory to all the calls in the address book. There is a real-world instance of this assault: the virus Commwarrior uses the address book and sends MMS messages including a contaminated data to recipients.
Then, the infection started to send out messages to recipients taken from the address publication. Attacks based on communication networks [edit] Attacks based on the GSM networks [modify] The enemy might try to break the security of the mobile network. The GSM network encryption formulas belong to the family of formulas called A5.
If the network does not support A5/1, or any other A5 algorithm carried out by the phone, then the base terminal can specify A5/0 which is the void formula, whereby the radio website traffic is sent unencrypted.
What is the Secure Folder and how do I use it? - Samsung UK
This is the basis for eavesdropping strikes on mobile radio networks making use of a fake base station typically called an IMSI catcher. On top of that, mapping of mobile terminals is challenging since each time the mobile terminal is accessing or being accessed by the network, a brand-new short-term identity (TMSI) is designated to the mobile terminal - secure phone app.
The TMSI is sent out to the mobile terminal in encrypted messages. When the encryption algorithm of GSM is broken, the enemy can intercept all unencrypted interactions made by the sufferer's mobile phone. Assaults based on Wi-Fi [modify] An enemy can attempt to eavesdrop on Wi-Fi interactions to obtain info (e. g. username, password).
The safety and security of wireless networks (WLAN) is thus a vital subject. The weak point of WEP is a short security key which is the same for all connected customers.
(TKIP)" which was developed to allow movement from WEP to WPA on the tools currently deployed. The major renovations in security are the dynamic encryption tricks.
With minimal opportunities for input (i. e. just the numerical keypad), smart phone users could specify brief security keys which contain just numbers. This increases the probability that an opponent succeeds with a brute-force assault. The successor to WPA, called WPA2, is meant to be risk-free enough to withstand a brute pressure assault.
Get HIPAA Compliant Secure Text Messaging & Calling - iPlum
In enhancement to investing more time on the properties, Wi-Fi gain access to assists them to remain effective. It's most likely they'll wind up spending even more money if they invest even more time on the facilities. similar apps like skype monitoring is one more factor. A great deal of dining establishments as well as coffee bar assemble information regarding their consumers so they can target promotions straight to their gadgets.
Generally, people filter organization premises based on Internet links as one more factor to acquire an one-upmanship. The ability to accessibility cost-free and also rapid Wi-Fi provides a service an edge over those who do not. Network security is the obligation of the organizations. There are many risks connected with their unprotected Wi-Fi networks, however (secure phone app).
Additionally, malware can be dispersed through the complimentary Wi-Fi network and hackers can make use of software application vulnerabilities to smuggle malware onto linked devices. It is additionally possible to be all ears and smell Wifi signals using unique software and tools, recording login qualifications and also pirating accounts. Similar to GSM, if the assailant is successful in damaging the recognition trick, it will certainly be feasible to attack not only the phone but also the entire network it is connected to.
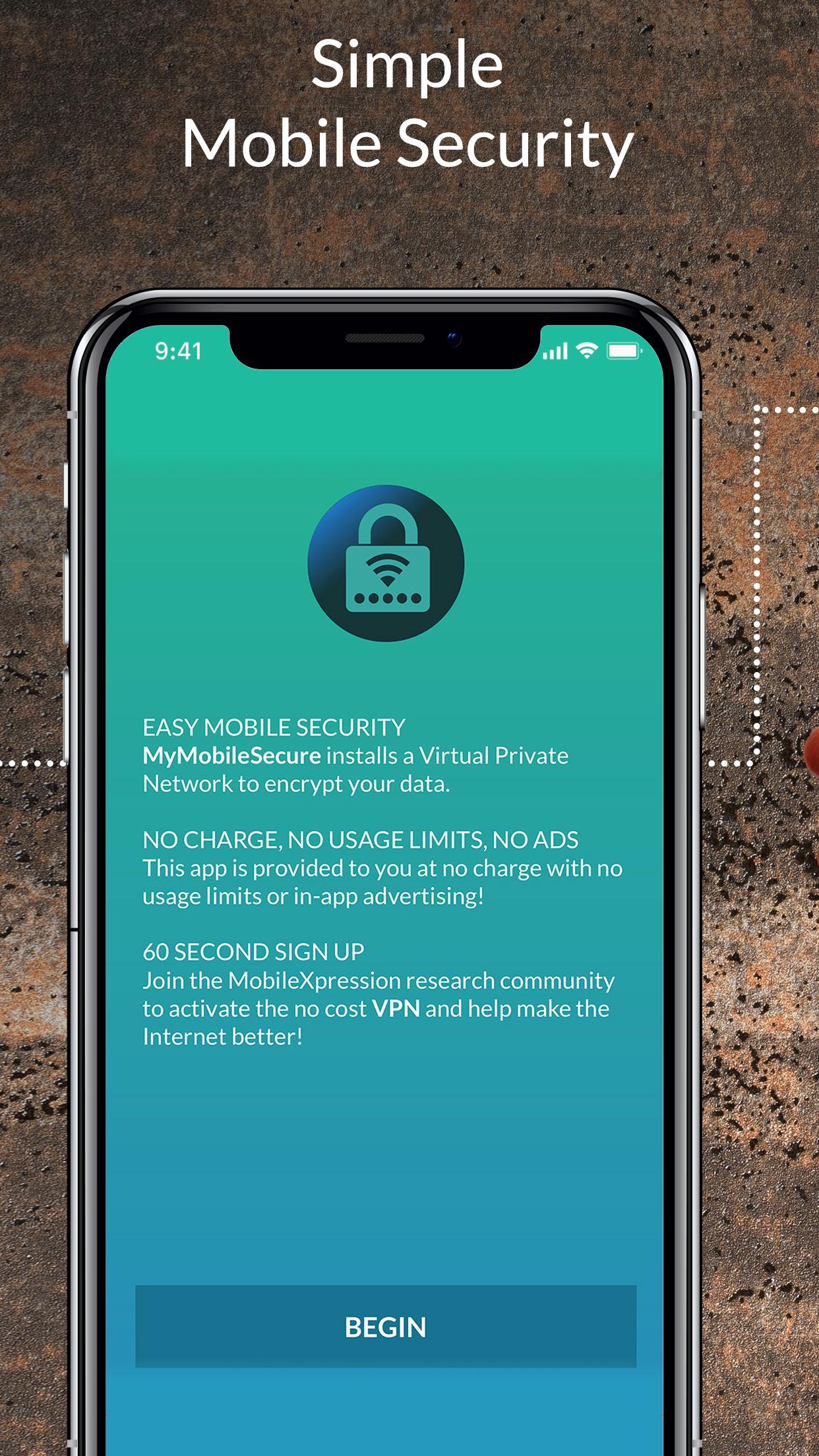 My Mobile Secure - Fast, Reliable, Unlimited VPN for Android - APK Download
My Mobile Secure - Fast, Reliable, Unlimited VPN for Android - APK Download Secure Phone App Library Highly Vulnerable
Secure Phone App Library Highly VulnerableAn aggressor could create a Wi-fi accessibility factor double with the same parameters and also attributes as the real network. Utilizing the reality that some mobile phones keep in mind the networks, they might confuse the two networks and also attach to the network of the aggressor who can intercept information if it does not transfer its data in encrypted type.
SIS documents style (Software program Installment Script) is a script documents that can be executed by the system without individual interaction. The mobile phone therefore believes the documents ahead from a relied on resource as well as downloads it, infecting the machine. Principle of Bluetooth-based attacks [modify] Safety and security issues connected to Bluetooth on mobile tools have been studied and also have actually revealed countless issues on different phones.
5 Great Phone Apps For Keeping Your Passwords Secure
An aggressor only needed to attach to the port to take full control of the tool. One more example: a phone should be within reach and Bluetooth in exploration setting. The opponent sends out a documents by means of Bluetooth.
The individual needs to accept the inbound file as well as mount the program. After setting up, the worm infects the machine. Assaults based on susceptabilities in software applications [modify] Other strikes are based upon flaws in the OS or applications on the phone. Web web browser [modify] The mobile web browser is an arising attack vector for mobile phones.
Jailbreaking the i, Phone with firmware 1. 1.1 was based totally on susceptabilities on the internet browser. Consequently, the exploitation of the vulnerability defined right here underlines the value of the Web internet browser as a strike vector for mobile phones. In this situation, there was a vulnerability based upon a stack-based buffer overflow in a collection utilized by the internet browser (Libtiff).
, harmful internet sites, software application that run in the history, etc.
The internet uses countless interactive attributes that ensure a greater engagement price, capture more and pertinent data, and increase brand commitment. Blog sites, discussion forums, social networks, as well as wikis are a few of the most common interactive web sites. Due to the remarkable growth of the internet, there has actually been a fast rise in the variety of safety and security breaches experienced by individuals as well as businesses over the previous few years.
'Freedom Phone' Looks To Be A Cheap And ... - The Daily Dot
Reviewing computer protection on a regular basis and fixing, updating, and changing the required features are a few of the means to do this. Installation of anti-viruses and also anti-spyware programs is one of the most effective means of shielding the computer, and also they use defense against malware, spyware, and also infections. They utilize firewall programs, which are normally installed between the net and also the computer network in order to find a balance.
Sometimes it is feasible to conquer the safety safeguards by changing the operating system itself. These assaults are tough. In 2004, susceptabilities in online makers running on specific gadgets were revealed.
Platform Safety And Security Architecture (PSA) is based on a main configuration documents called SWIPolicy. In 2008 it was feasible to adjust the Nokia firmware before it is installed, as well as in truth in some downloadable versions of it, this data was human-readable, so it was feasible to change as well as alter the photo of the firmware.
Theoretically, smart devices have an advantage over hard drives given that the OS documents remain in ROM, and also can not be altered by malware. Nevertheless, in some systems it was possible to prevent this: in the Symbian OS it was feasible to overwrite a data with a data of the exact same name.
When an application is installed, the signing of this application is verified by a series of certificates. One can create a valid signature without using a legitimate certification and also include it to the list. In the Symbian OS all certifications are in the directory site: c: \ resource \ swicertstore \ dat. With firmware adjustments described above it is really simple to insert a relatively legitimate yet destructive certification.
Best Encrypted Messaging Apps You Should Use Today
The exploit benefited from antenna-properties of earphone cords while linked into the audio-output jacks of the susceptible mobile phones and properly spoofed audio input to infuse commands via the audio user interface. Juice Jacking [modify] Juice Jacking is a physical or hardware susceptability particular to mobile platforms. Utilizing the dual objective of the USB fee port, lots of devices have actually been at risk to having information exfiltrated from, or malware mounted onto a mobile device by utilizing destructive charging stands established in public places or concealed in typical fee adapters.
Mobile tool customers take control of their own gadget by jail-breaking it, and also tailor the user interface by setting up applications, modification system setups that are not enabled on the tools. Hence, permitting to fine-tune the mobile gadgets operating systems processes, run programs behind-the-scenes, therefore devices are being subject to variety of destructive attack that can bring about jeopardize vital personal information.
| Комментировать | « Пред. запись — К дневнику — След. запись » | Страницы: [1] [Новые] |






