Ќастройка основного и двух резервных операторов на Linux-роутере с NetGWM |
«адача резервировани€ основного шлюза Ч одна из самых попул€рных в сетевом администрировании. ” нее есть целый р€д решений, которые реализуют механизмы приоритезации или балансировки исход€щих каналов дл€ абсолютного большинства современных маршрутизаторов, в том числе и маршрутизаторов на базе Linux.
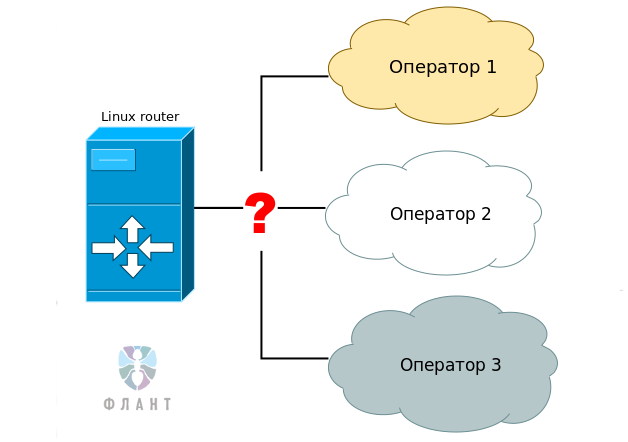
¬ статье об отказоустойчивом роутере мы вскользь упоминали свой корпоративный стандарт дл€ решени€ этой задачи Ч Open Source-продукт NetGWM Ч и обещали рассказать об этой утилите подробнее. »з этой статьи вы узнаете, как устроена утилита, какие Ђфишкиї можно использовать в работе с ней и почему мы решили отказатьс€ от использовани€ альтернативных решений.
лассическа€ схема резервировани€ основного шлюза в Linux, реализуема€ средствами iproute2, выгл€дит практически во всех источниках примерно одинаково:
ѕодробности этой схемы легко гугл€тс€ по запросу Ђlinux policy routingї. Ќа наш взгл€д, схема имеет р€д очевидных недостатков, которые и стали основным мотиватором создани€ утилиты NetGWM:
ћы посмотрели, что поможет нам решить все 4 проблемы: простое и управл€емое средство с поддержкой 2 и более шлюзов по умолчанию, умеющее диагностировать доступность канала и тестировать его на стабильность. » не нашли такого варианта. »менно так и по€вилс€ NetGWM.
NetGWM (Network GateWay Manager) Ч это небольша€ утилита приоритезации основного шлюза, написанна€ на Python и распростран€ема€ под свободной лицензией GNU GPL v3. јвтор первоначальной версии Ч driusha (јндрей ѕоловов).
»сходный код и документаци€ на английском €зыке доступны на GitHub, а кратка€ документаци€ и описание на русском €зыке Ч здесь.
”становка из GitHub:
роме того, готовый DEB-пакет с NetGWM можно установить из репозитори€ дл€ Ubuntu компании Ђ‘лантї. ”становка дл€ Ubuntu 14.04 LTS выгл€дит так:
ƒобавл€ть служебную таблицу маршрутизации и настраивать cron в Ubuntu не потребуетс€. “аблица автоматически добавитс€ при установке пакета. роме того, при установке будет зарегистрирована служба
¬ основе работы NetGWM также лежит policy-роутинг, и нам придетс€ предварительно настроить таблицы маршрутизации дл€ каждого оператора.
ƒопустим, есть 3 оператора, и необходимо сделать так, чтобы основным оператором был оператор 1, в случае отказа Ч использовалс€ оператор 2, а в случае отказа из обоих Ч оператор 3.
ѕусть первый оператор у нас подключен к интерфейсу eth1, второй Ч к eth2, третий Ч к eth3. ѕервый оператор имеет шлюз 88.88.88.88, второй оператор Ч шлюз 99.99.99.99, третий Ч 100.100.100.100.
ћы почти всегда при настройке сети с несколькими основными шлюзами используем маркировку пакетов и модуль conntrack из NetFilter. Ёто хороша€ практика, помогающа€ распредел€ть пакеты по таблицам маршрутизации с учетом состо€ни€, но не €вл€юща€с€ об€зательной.
Ќастроим маркинг пакетов и conntrack:
2. ƒобавим правила маршрутизации дл€ промаркированных пакетов. ћы это делаем с помощью скрипта, который вызываетс€ из
3. ќбъ€вим таблицы маршрутизации в
4. Ќастроим NetGWM. ѕо умолчанию,
5. Ќастроим действи€ при переключении.
≈сли произойдет переключение, то после смены основного шлюза будут выполнены все исполн€емые файлы из каталога
¬ скрипте можно на основании этих переменных описать логику действий в зависимости от подключаемого оператора (добавить или удалить маршруты, отправить уведомлени€, настроить шейпинг и т.п.). ƒл€ примера приведу скрипт на shell, отправл€ющий уведомлени€:
6. —тартуем сервис
≈сли вы получили NetGWM из GitHub, то установленное ранее задание в cron уже и так провер€ет доступность вашего основного шлюза, дополнительных действий не требуетс€.
—обыти€ по переключению NetGWM регистрирует в журнале
—охраненна€ истори€ переключений помогает произвести анализ инцидента и определить причины перерыва в св€зи.
”же около 4 лет NetGWM используетс€ в нашей компании на 30+ маршрутизаторах Linux разных масштабов. Ќадежность утилиты многократно проверена в работе. ƒл€ примера, на одной из инсталл€ций, с ма€ 2014 года NetGWM обработал 137 переключений операторов без каких-либо проблем.
—табильность, покрытие всех наших потребностей и отсутствие проблем в эксплуатации в течение длительного времени привели к тому, что мы практически не занимаемс€ развитием проекта. од NetGWM написан на Python, поэтому отсутствует и необходимость в адаптации утилиты к новым верси€м операционных систем. “ем не менее, мы будем очень рады, если вы решите прин€ть участие в развитии NetGWM, отправив свои патчи в GitHub или просто написав feature request в комментари€х.
— NetGWM мы имеем стабильную, гибкую и расшир€емую (с помощью скриптов) утилиту, котора€ полностью закрывает наши потребности в управлении приоритетом основного шлюза.
Ћюбые вопросы по использованию NetGWM также приветствуютс€ Ч можно пр€мо здесь в комментари€х.
P.S. „итайте также в нашем блоге: ЂЌаш рецепт отказоустойчивого Linux-роутераї Ч и подписывайтесь на него, чтобы не пропускать новые материалы!
ћетки:
author gserge
системное администрирование
сетевые технологии
настройка linux
*nix
блог компании флант
netgwm
роутеры
iptables
conntrack
linux
флант

¬ статье об отказоустойчивом роутере мы вскользь упоминали свой корпоративный стандарт дл€ решени€ этой задачи Ч Open Source-продукт NetGWM Ч и обещали рассказать об этой утилите подробнее. »з этой статьи вы узнаете, как устроена утилита, какие Ђфишкиї можно использовать в работе с ней и почему мы решили отказатьс€ от использовани€ альтернативных решений.
ѕочему NetGWM?
лассическа€ схема резервировани€ основного шлюза в Linux, реализуема€ средствами iproute2, выгл€дит практически во всех источниках примерно одинаково:
- ƒано: 2 провайдера.
- —оздаем дл€ каждого оператора свою таблицу маршрутизации.
- —оздаем правила (
ip rule), по которым трафик попадает в ту или иную таблицу маршрутизации (например, по источнику и/или по метке из iptables). - ћетриками или ifupdown-скриптами определ€ем приоритет основного шлюза.
ѕодробности этой схемы легко гугл€тс€ по запросу Ђlinux policy routingї. Ќа наш взгл€д, схема имеет р€д очевидных недостатков, которые и стали основным мотиватором создани€ утилиты NetGWM:
- —ложность внесени€ изменений в схему, плоха€ управл€емость.
- ≈сли количество шлюзов 3 и более, логика скриптов усложн€етс€, как и реализаци€ выбора шлюза на основе метрик.
- ѕроблема обнаружени€ пропадани€ канала. «ачастую, физический линк и даже шлюз оператора могут быть доступны, при этом из-за проблем внутри инфраструктуры оператора или у его вышесто€щего поставщика услуг реально сеть оказываетс€ недоступной. –ешение этой проблемы требует добавление дополнительной логики в ifupdown-скрипты, а в маршрутизации на основе метрик она нерешаема в принципе.
- ѕроблема Ђшалтай-болтайї. “ака€ проблема про€вл€етс€, если на высокоприоритетном канале наблюдаютс€ кратковременные частые перерывы в св€зи. ѕри этом шлюз успешно переключаетс€ на резервный. ќткуда здесь, казалось бы, может вз€тьс€ проблема? ƒело в том, что р€д сервисов, таких как телефони€, видеосв€зь, VPN-туннели и другие, требуют некоторого таймаута дл€ определени€ факта обрыва и установлени€ нового сеанса. ¬ зависимости от частоты обрывов это приводит к резкому снижению качества сервиса или его полной недоступности. –ешение этой проблемы также требует усложнени€ логики скриптов и тоже совершенно нерешаема метриками.
ћы посмотрели, что поможет нам решить все 4 проблемы: простое и управл€емое средство с поддержкой 2 и более шлюзов по умолчанию, умеющее диагностировать доступность канала и тестировать его на стабильность. » не нашли такого варианта. »менно так и по€вилс€ NetGWM.
”становка из GitHub и репозитори€ Ђ‘лантї
NetGWM (Network GateWay Manager) Ч это небольша€ утилита приоритезации основного шлюза, написанна€ на Python и распростран€ема€ под свободной лицензией GNU GPL v3. јвтор первоначальной версии Ч driusha (јндрей ѕоловов).
»сходный код и документаци€ на английском €зыке доступны на GitHub, а кратка€ документаци€ и описание на русском €зыке Ч здесь.
”становка из GitHub:
## ѕредварительно в системе требуетс€ установить:
## iproute2, conntrack, модуль python-yaml
## ѕосле этого клонируем репозиторий:
$ git clone git://github.com/flant/netgwm.git netgwm
## » устанавливаем (понадоб€тс€ права суперпользовател€):
$ cd netgwm && sudo make install
## ƒобавим служебную таблицу маршрутизации, котора€ будет использоватьс€ NetGWM
$ sudo sh -c "echo '100 netgwm_check' >> /etc/iproute2/rt_tables"
## ƒобавл€ем в cron пользовател€ root вызов netgwm с той частотой,
## с которой вам бы хотелось провер€ть доступность основного шлюза
## (например, раз в минуту):
$ sudo crontab -e
*/1 * * * * /usr/lib/netgwm/newtgwm.pyроме того, готовый DEB-пакет с NetGWM можно установить из репозитори€ дл€ Ubuntu компании Ђ‘лантї. ”становка дл€ Ubuntu 14.04 LTS выгл€дит так:
## ”становим репозиторий:
$ sudo wget https://apt.flant.ru/apt/flant.trusty.common.list \
-O /etc/apt/sources.list.d/flant.common.list
## »мпортируем ключ:
$ wget https://apt.flant.ru/apt/archive.key -O- | sudo apt-key add -
## ѕонадобитс€ HTTPS-транспорт Ч установите его, если не сделали это раньше:
$ sudo apt-get install apt-transport-https
## ќбновим пакетную базу и установим netgwm:
$ sudo apt-get update && sudo apt-get install netgwmƒобавл€ть служебную таблицу маршрутизации и настраивать cron в Ubuntu не потребуетс€. “аблица автоматически добавитс€ при установке пакета. роме того, при установке будет зарегистрирована служба
netgwm, init-скрипт которой стартует в качестве демона небольшой shell-скрипт /usr/bin/netgwm, который, в свою очередь, читает из файла /etc/default/netgwm значение параметра INTERVAL (в секундах) и с указанной периодичностью сам вызывает netgwm.py. Ќастройка
¬ основе работы NetGWM также лежит policy-роутинг, и нам придетс€ предварительно настроить таблицы маршрутизации дл€ каждого оператора.
ƒопустим, есть 3 оператора, и необходимо сделать так, чтобы основным оператором был оператор 1, в случае отказа Ч использовалс€ оператор 2, а в случае отказа из обоих Ч оператор 3.
ѕусть первый оператор у нас подключен к интерфейсу eth1, второй Ч к eth2, третий Ч к eth3. ѕервый оператор имеет шлюз 88.88.88.88, второй оператор Ч шлюз 99.99.99.99, третий Ч 100.100.100.100.
ћы почти всегда при настройке сети с несколькими основными шлюзами используем маркировку пакетов и модуль conntrack из NetFilter. Ёто хороша€ практика, помогающа€ распредел€ть пакеты по таблицам маршрутизации с учетом состо€ни€, но не €вл€юща€с€ об€зательной.
Ќастроим маркинг пакетов и conntrack:
iptables -t mangle -A PREROUTING -i eth1 -m conntrack --ctstate NEW,RELATED -j CONNMARK --set-xmark 0x1/0x3
iptables -t mangle -A PREROUTING -i eth2 -m conntrack --ctstate NEW,RELATED -j CONNMARK --set-xmark 0x2/0x3
iptables -t mangle -A PREROUTING -i eth3 -m conntrack --ctstate NEW,RELATED -j CONNMARK --set-xmark 0x3/0x3
iptables -t mangle -A PREROUTING -j CONNMARK --restore-mark --nfmask 0xffffffff --ctmask 0xffffffff
iptables -t mangle -A OUTPUT -o eth1 -m conntrack --ctstate NEW,RELATED -j CONNMARK --set-xmark 0x1/0x3
iptables -t mangle -A OUTPUT -o eth2 -m conntrack --ctstate NEW,RELATED -j CONNMARK --set-xmark 0x2/0x3
iptables -t mangle -A OUTPUT -o eth3 -m conntrack --ctstate NEW,RELATED -j CONNMARK --set-xmark 0x3/0x3
iptables -t mangle -A OUTPUT -j CONNMARK --restore-mark --nfmask 0xffffffff --ctmask 0xffffffff
iptables -t mangle -A POSTROUTING -o eth1 -m conntrack --ctstate NEW,RELATED -j CONNMARK --set-xmark 0x1/0x3
iptables -t mangle -A POSTROUTING -o eth2 -m conntrack --ctstate NEW,RELATED -j CONNMARK --set-xmark 0x2/0x3
iptables -t mangle -A POSTROUTING -o eth3 -m conntrack --ctstate NEW,RELATED -j CONNMARK --set-xmark 0x3/0x3
iptables -t mangle -A POSTROUTING -j CONNMARK --restore-mark --nfmask 0xffffffff --ctmask 0xffffffff2. ƒобавим правила маршрутизации дл€ промаркированных пакетов. ћы это делаем с помощью скрипта, который вызываетс€ из
/etc/network/interfaces при событии post-up на интерфейсе lo:#!/bin/bash
/sbin/ip rule flush
# operator 1
/sbin/ip rule add priority 8001 iif eth1 lookup main
/sbin/ip rule add priority 10001 fwmark 0x1/0x3 lookup operator1
/sbin/ip rule add from 88.88.88.88 lookup operator1
# operator 2
/sbin/ip rule add priority 8002 iif eth2 lookup main
/sbin/ip rule add priority 10002 fwmark 0x2/0x3 lookup operator2
/sbin/ip rule add from 99.99.99.99 lookup operator2
# operator 3
/sbin/ip rule add priority 8002 iif eth3 lookup main
/sbin/ip rule add priority 10002 fwmark 0x3/0x3 lookup operator3
/sbin/ip rule add from 100.100.100.100 lookup operator33. ќбъ€вим таблицы маршрутизации в
/etc/iproute2/rt_tables:# «арезервированные значени€:
255 local
254 main
253 default
0 unspec
# —лужебна€ таблица, которую мы (или dpkg) добавили ранее:
100 netgwm_check
# “аблицы дл€ операторов, которые мы должны добавить сейчас:
101 operator1
102 operator2
103 operator34. Ќастроим NetGWM. ѕо умолчанию,
netgwm.py будет искать конфигурационный файл по адресу /etc/netgwm/netgwm.yml, однако вы можете переопределить это с помощью ключа -c. Ќастроим работу утилиты:# ќписываем маршруты по умолчанию дл€ каждого оператора и приоритеты
# ћеньшее значение (число) имеет больший приоритет. 1 - самый высокий приоритет
# ќбратите внимание, что дл€ смены шлюза по умолчанию на другой достаточно просто
# изменить значени€ приоритетов в этом файле. » уже при следующем запуске (через
# минуту в нашем случае) шлюз изменитс€ на более приоритетный (если он доступен).
# Ќаименование оператора должно совпадать с именем таблицы маршрутизации из
# /etc/iproute2/rt_tables
gateways:
operator1: {ip: 88.88.88.88, priority: 1}
operator2: {ip: 99.99.99.99, priority: 2}
operator3: {ip: 100.100.100.100, priority: 3}
# Ётот параметр решает проблему Ђшалтай-болтайї, когда приоритетного
# оператора (из доступных) Ђштормитї.
# ѕараметр определ€ет врем€ посто€нной доступности (в секундах),
# после которого netgwm будет считать, что св€зь стабильна
min_uptime: 900
# ћассив удаленных хостов, которые будут использоватьс€ netgwm дл€
# проверки работоспособности каждого оператора. «десь стоит указать либо важные
# дл€ вас хосты в интернете, либо общедоступные и стабильно работающие ресурсы,
# как сделано в примере. Ўлюз считаетс€ недоступным, если netgwm Ќ≈ —ћќ√
# установить через него св€зь до ¬—≈’ (условие AND) указанных хостов
check_sites:
- 8.8.8.8 # Google public DNS
- 4.2.2.2 # Verizon public DNS
# ѕо умолчанию netgwm провер€ет доступность только дл€ самого
# приоритетного шлюза. ≈сли тот недоступен Ч до второго по приоритетности и т.д.
# ƒанна€ опци€, будучи установленной в true, заставит netgwm провер€ть
# доступность всех шлюзов при каждом запуске
check_all_gateways: false5. Ќастроим действи€ при переключении.
≈сли произойдет переключение, то после смены основного шлюза будут выполнены все исполн€емые файлы из каталога
/etc/netgwm/post-replace.d/*. ѕри этом каждому файлу будут переданы 6 параметров командной строки:-
$1Ч наименование нового оператора; -
$2Ч IP вновь установленного шлюзе или NaN, если новый шлюз установить не удалось; -
$3Ч им€ устройства нового шлюза или NaN, если шлюз установить не удалось; -
$4Ч наименование старого оператора или NaN, если шлюз устанавливаетс€ впервые; -
$5Ч IP старого оператора или NaN, если шлюз устанавливаетс€ впервые; -
$6Ч им€ устройства старого оператора или NaN, если шлюз устанавливаетс€ впервые.
¬ скрипте можно на основании этих переменных описать логику действий в зависимости от подключаемого оператора (добавить или удалить маршруты, отправить уведомлени€, настроить шейпинг и т.п.). ƒл€ примера приведу скрипт на shell, отправл€ющий уведомлени€:
#!/bin/bash
# ќпредел€ем, что произошло: переключение или старт netgwm
if [ "$4" = 'NaN' ] && [ "$5" = 'NaN' ]
then
STATE='start'
else
STATE='switch'
fi
# ќтправл€ем уведомление дежурным инженерам о произошедшем
case $STATE in
'start')
/usr/bin/flant-integration --sms-send="NetGWM on ${HOSTNAME} has been started and now use gw: $1 - $2"
;;
'switch')
/usr/bin/flant-integration --sms-send="NetGWM on ${HOSTNAME} has switched to new gw: $1 - $2 from gw: $4 - $5"
;;
*)
/usr/bin/logger -t netgwm "Unknown NetGWM state. Try restarting service fo fix it."
;;
esac
exit6. —тартуем сервис
netgwm в Ubuntu, если вы установили DEB-пакет:$ sudo service netgwm start≈сли вы получили NetGWM из GitHub, то установленное ранее задание в cron уже и так провер€ет доступность вашего основного шлюза, дополнительных действий не требуетс€.
∆урналирование
—обыти€ по переключению NetGWM регистрирует в журнале
/var/log/netgwm:$ tail -n 3 /var/log/netgwm.log
2017-07-14 06:25:41,554 route replaced to: via 88.88.88.88
2017-07-14 06:27:09,551 route replaced to: via 99.99.99.99
2017-07-14 07:28:48,573 route replaced to: via 88.88.88.88—охраненна€ истори€ переключений помогает произвести анализ инцидента и определить причины перерыва в св€зи.
ѕроверено в production
”же около 4 лет NetGWM используетс€ в нашей компании на 30+ маршрутизаторах Linux разных масштабов. Ќадежность утилиты многократно проверена в работе. ƒл€ примера, на одной из инсталл€ций, с ма€ 2014 года NetGWM обработал 137 переключений операторов без каких-либо проблем.
—табильность, покрытие всех наших потребностей и отсутствие проблем в эксплуатации в течение длительного времени привели к тому, что мы практически не занимаемс€ развитием проекта. од NetGWM написан на Python, поэтому отсутствует и необходимость в адаптации утилиты к новым верси€м операционных систем. “ем не менее, мы будем очень рады, если вы решите прин€ть участие в развитии NetGWM, отправив свои патчи в GitHub или просто написав feature request в комментари€х.
«аключение
— NetGWM мы имеем стабильную, гибкую и расшир€емую (с помощью скриптов) утилиту, котора€ полностью закрывает наши потребности в управлении приоритетом основного шлюза.
Ћюбые вопросы по использованию NetGWM также приветствуютс€ Ч можно пр€мо здесь в комментари€х.
P.S. „итайте также в нашем блоге: ЂЌаш рецепт отказоустойчивого Linux-роутераї Ч и подписывайтесь на него, чтобы не пропускать новые материалы!
| омментировать | « ѕред. запись — дневнику — —лед. запись » | —траницы: [1] [Ќовые] |






