ѕроблемы безопасности Android-приложений: классификаци€ и анализ |

»зображение: etnyk, CC BY-NC-ND 2.0
»спользование смартфонов в повседневной жизни не ограничиваетс€ голосовыми звонками и —ћ—. ¬озможность загружать и выполн€ть программы, а также мобильный доступ в »нтернет привели к по€влению громадного числа мобильных приложений. ‘ункциональность современного смартфона составл€ют браузеры, клиентские программы социальных сетей, офисные приложени€ и всевозможные сервисы, работающие в —ети. Android-устройства зан€ли б'oльшую часть рынка смартфонов за счет открытой архитектуры платформы Android и удобного API разработчика. Ќа данный момент Android €вл€етс€ наиболее попул€рной мобильной ќ— с долей рынка более 75%. оличество приложений, загруженных из магазина Google Play, в 2016 году составило 65 миллиардов [1].
ѕараллельно наблюдаетс€ и бурный рост числа вредоносных приложений: в 2015 году их было обнаружено 2,3 миллиона [3]. роме того, около 60% Android-устройств работают на верси€х ќ— с известными у€звимост€ми, и они потенциально могут быть атакованы злоумышленниками [6]. Ёти угрозы, в свою очередь, привели к развитию средств защиты. ќфициальный магазин Google Play ввел фильтрацию приложений с помощью песочницы Google Bouncer. јнтивирусные компании стали выпускать свои продукты под Android (хот€, как показано в [8], многие из них сами по себе содержат опасные у€звимости). „исло научных публикаций по данной теме также возросло: одна из обзорных работ 2015 года о решени€х безопасности дл€ Android [2] насчитывает более 40 проектов и упоминает далеко не все известные на данный момент исследовани€. ¬ св€зи с тем, что мобильные устройства €вл€ютс€ источником и хранилищем большого количества конфиденциальных данных, проблема безопасности ќ— Android и ее приложений стоит особо остро.
ѕлатформа Android €вл€етс€ свободным ѕќ, база ее исходных кодов полностью открыта. ѕроизводители устройств самосто€тельно развивают кодовую базу, создава€ специализированные прошивки с целью достижени€ большей функциональности и лучшей производительности. ѕобочным результатом такой де€тельности станов€тс€ у€звимости и слабости в реализации алгоритмов, отсутствующие в основной кодовой базе, но существующие на множестве реальных устройств. ¬редоносное ѕќ использует эти у€звимости дл€ повышени€ прав и преодолени€ защитных механизмов. ¬ы€вление у€звимостей в прошивках при отсутствии исходных кодов крайне затруднено. ѕервоочередной проблемой становитс€ отсутствие среды контролируемого выполнени€, котора€ необходима дл€ проведени€ динамического анализа.
“аким образом, полноценный анализ безопасности устройства требует изучени€ свойств системного и прикладного ѕќ в совокупности. ¬ данной статье представлена собственна€ классификаци€ проблем безопасности Android, а также список требований к системе полносистемного анализа платформы Android.
1. ”стройство ќ— Android
¬ основе ќ— Android лежит €дро Linux с некоторыми архитектурными изменени€ми, которые были сделаны инженерами Google. ѕриложени€ дл€ операционной системы Android разрабатываютс€ на €зыке Java. Ќачина€ с версии Android 1.5 был представлен набор инструментов Android NDK, который позвол€ет разрабатывать модули приложений на €зыках — и —++ и компилировать их в машинный код [4]. ѕриложени€ поставл€ютс€ в виде файлов специального формата APK, который €вл€етс€ ZIP-архивом с определенной структурой каталогов и файлов. APK-файл приложени€ содержит:
- манифест;
- модули, скомпилированные в машинный код (раздел€емые библиотеки .so);
- различные ресурсы приложени€;
- DEX-файл;
- прочие необходимые файлы.
Ќачина€ с версии Android 4.4 поддерживаютс€ две среды выполнени€ приложений: Dalvik VM и ART. —ледует отметить, что процесс подготовки APK-файла не изменилс€, изменилс€ только процесс установки приложений в новой среде выполнени€ ART. Ќачина€ с версии 5.0 среда выполнени€ ART стала использоватьс€ по умолчанию вместо Dalvik VM.
—реда выполнени€ Java-программ Dalvik VM на Android сильно отличаетс€ от Ђобычнойї Java VM. ¬о-первых, при компил€ции Java-программы она компилируетс€ в байт-код виртуальной машины Dalvik, который сильно отличаетс€ от байт-кода виртуальной машины HotSpot. ¬иртуальна€ машина Dalvik €вл€етс€ регистровой, что делает ее выполнение на RISC-архитектурах, часто используемых в мобильных устройствах, более эффективным. “акже при разработке Dalvik учитывались ограничени€ пам€ти в мобильных устройствах. Ќачина€ с версии Android 2.2 среда выполнени€ Dalvik содержит JIT-компил€тор, который компилирует Ђгор€чиеї куски кода Java-программ в машинный код [5]. —тандартные библиотеки Java были либо заменены на доработанные библиотеки из пакета Apache Harmony либо написаны заново. ѕри компил€ции Java-программы получаетс€ файл формата DEX (Dalvik Executable), который содержит байт-код дл€ виртуальной машины Dalvik. ‘ормат файла был разработан с целью сокращени€ объема занимаемой пам€ти и существенно отличаетс€ от стандартного формата JAR. ƒл€ вызова модулей, реализованных в машинном коде, из Java-программ используетс€ интерфейс JNI. —тоит отметить, что имеетс€ возможность подгружать машинные модули динамически по сети с помощью компонента DexClassLoader.
2. ѕроблемы безопасности
–одительским процессом дл€ всех приложений в ќ— Android €вл€етс€ процесс Zygote. ƒанный процесс представл€ет собой каркас Android-приложени€, в котором уже загружены все необходимые библиотеки окружени€ Android, но отсутствует код самого приложени€. «апуск приложени€ Android с точки зрени€ операционной системы происходит следующим образом:
- ¬начале происходит системный вызов fork дл€ создани€ потомка от процесса Zygote (см. рис. 1).
- ¬ этом новом процессе открываетс€ файл запускаемого приложени€ (системный вызов open).
- ѕроисходит чтение информации о файлах классов (classes.dex) и ресурсов из файла приложени€. ѕроисходит открытие сокетов дл€ IPC.
- ¬ыполн€етс€ системный вызов mmap дл€ отображени€ файлов приложени€ в пам€ть.
- —реда выполнени€ производит настройку необходимого окружени€ и выполн€ет приложение (интерпретирует байт-код Dalvik или передает управление функци€м в исполн€емом коде в случае ART [7]).
Ќа уровне €дра ќ— Android каждое приложение €вл€етс€ отдельным процессом с уникальными значени€ми user/group ID, которые даютс€ ему при установке. “аким образом, кажда€ программа работает в своей песочнице. Ќачина€ с версии 4.3 в дополнение к этой политике безопасности добавилось использование компонента мандатного контрол€ доступа SELinux [10].
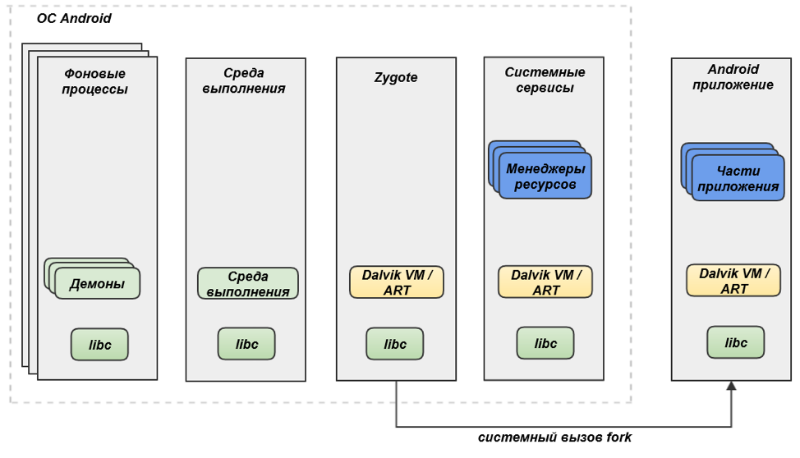
–ис. 1. «апуск нового приложени€ в ќ— Android
ѕо умолчанию приложение ограничено в своих возможност€х и не может сделать ничего, чтобы негативно повли€ть на другое приложение или пользовател€: ни прочитать пользовательские данные, ни модифицировать системные приложени€; отсутствует доступ к сети. ƒл€ получени€ доступа к различным ресурсам приложение обращаетс€ к сервисам ќ— Android. –азрешени€ на доступ задаютс€ статически в файле манифеста приложени€ и выдаютс€ приложению во врем€ его работы по мере необходимости. —истема запрашивает у пользовател€ согласие на выдачу этих разрешений во врем€ установки или во врем€ обновлени€ приложени€. ќтветственность за выдачу доступа приложению лежит на пользователе, он самосто€тельно решает, какому приложению давать разрешени€ на определенные действи€, а какому не давать, Ч во врем€ его установки. »спользование такого подхода, при котором все разрешени€ выдаютс€ разом при установке приложени€, привело к тому, что пользователи стали раздавать полномочи€ приложени€м, не задумыва€сь о последстви€х. ¬ свою очередь, приложени€ стали запрашивать все больше разрешений по мере расширени€ их функциональности. ¬ Android 6 Marshmallow данна€ система заменена на другую: приложение запрашивает доступ к ресурсам у пользовател€ во врем€ его работы, а пользователь может либо разрешить доступ, либо запретить его [11].
Android-приложение состоит из четырех видов компонентов и не содержит функции main() или какой-то другой единой точки входа. омпоненты приложений взаимодействуют друг с другом с помощью специальных сообщений, называемых Intent.
омпоненты под названием Activity определ€ют пользовательский интерфейс. ак правило, используетс€ один компонент Activity дл€ описани€ одного экрана приложени€. Activity может запустить другое Activity, передав параметры с помощью механизма Intent. ¬о врем€ работы только одно Activity может работать и обрабатывать пользовательский ввод, остальные на это врем€ остаютс€ замороженными или уничтожаютс€, в зависимости от выбранного режима работы приложени€.
омпоненты под названием Service [9] производ€т фоновую обработку. огда Activity нужно выполнить какую-то операцию, например загрузку файла или проигрывание музыки, и продолжить работу, когда пользователь перешел в другое приложение или свернул текущее, приложение запускает сервис, цель которого Ч выполнение этой операции. –азработчики могут использовать Service в качестве приложени€-демона, стартующего во врем€ загрузки системы. омпонент Service, как правило, поддерживает RPC (Remote Procedure Call), поэтому другие компоненты системы могут обращатьс€ к нему.
омпонент Content provider сохран€ет и обмениваетс€ данными, использу€ интерфейс рел€ционных баз данных. аждый Content provider содержит уникальный URI дл€ данных и обрабатывает запросы к нему в виде очередей SQL (Select, Insert, Delete).
омпоненты Broadcast receiver выступают в роли €щиков дл€ сообщений от других приложений.
ѕроблемы безопасности, возникающие в ќ— Android, рассматривались в работах [2, 12, 13], но классификаци€ проблем по категори€м дана только в статье [2]. Ёта классификаци€ достаточно подробна€ и охватывает многие проблемы безопасности, но у нее есть р€д существенных недостатков: некоторые категории охватывают широкую область у€звимостей, в то врем€ как другие достаточно специализированы; приведенные категории у€звимостей никак не соотнос€тс€ с программными уровн€ми архитектуры ќ— Android; не охвачены у€звимости из интернет-источников, а также слабо охвачены у€звимости в протоколах и аппаратуре (п. 2.7 и 2.8 в нашей классификации). ѕредлагаема€ ниже классификаци€ у€звимостей устран€ет эти недочеты.
2.1. ”€звимости €дра Linux и его модулей
данной категории проблем относ€тс€ у€звимости, которые присущи всем ќ—, основанным на той же версии €дра Linux, что и ќ— Android. Ёксплойты, использующие у€звимости в €дре, могут получить данные пользовател€ или права администратора системы. ѕовысив привилегии процесса до прав администратора системы, вредоносна€ программа может отключить систему безопасности Android, вставить в существующие программы вредоносный код и установить руткит. тому же производители различных устройств добавл€ют в €дро модули дл€ своих устройств; в этих модул€х также могут быть у€звимости. ѕримеры у€звимостей повышени€ привилегий описаны в [14, 15, 16, 64]. “акже стоит отметить, что совсем недавно была обнаружена у€звимость в компоненте ashmem дл€ межпроцессного взаимодействи€ в Android [62].
2.2. ”€звимости модификаций и компонентов производителей устройств
¬ последнее врем€ производители различных мобильных устройств стали выпускать свои модифицированные прошивки Android. Ёти прошивки могут содержать различные приложени€ и сервисы, разработанные производителем устройства, которые чаще всего нельз€ удалить. Ќапример, в окт€бре 2016 года был обнаружен скрытый бэкдор в прошивках Foxconn [63]. јнализ этих сервисов, приведенный в стать€х [17], показывает, что в них содержитс€ от 65 до 85% у€звимостей, обнаруженных во всей системе. тому же стоит отметить, что у€звимости, которые были обнаружены и исправлены в основной ветке Android, могут долгое врем€ оставатьс€ в ветках производителей устройств [18, 19].
2.3. ”€звимости модулей в машинных кодах
Android-приложени€ поддерживают запуск машинного кода через интерфейс JNI. Ёто порождает еще одну категорию у€звимостей, св€занную с широко известными у€звимост€ми утечек пам€ти в низкоуровневых €зыках (например, в — и —++ ) [20]. ѕоскольку на уровне процессов ќ— Android нет никаких ограничений, кроме накладываемых €дром Linux, сторонние библиотеки в машинных кодах могут использовать разрешени€, выданные всему приложению, дл€ совершени€ вредоносной активности (см. также следующую категорию у€звимостей, п. 2.4). “акже модули приложени€ в машинных кодах используютс€ авторами вредоносных приложений, чтобы обойти инструменты анализа и мониторинга уровн€ Android. Ёти модули также могут использовать техники противодействи€ анализу, используемые в обычных программах.
2.4. ”€звимости механизмов межкомпонентного взаимодействи€
данной категории относ€тс€ у€звимости, св€занные с взаимодействием между различными компонентами приложений. “ак как на уровне операционной системы приложение ограничено песочницей процесса, ему необходим механизм доступа к компонентам ќ— Android дл€ взаимодействи€ с ними. Ёто происходит через устройство /dev/Binder и различные другие сервисы ќ— Android. ак уже говорилось выше, параметры этого доступа задаютс€ в файле манифеста, в виде XML-файла с разрешени€ми. јнализ, приведенный в стать€х [12, 21, 22, 23, 24, 25], указывает на недочеты этой системы ограничений и показывает пути их обхода. “ак, например, приложение может воспользоватьс€ правами доступа другого приложени€ и получить с помощью него данные через ICC. “акже могут быть у€звимости, св€занные со сторонними библиотеками. —торонние библиотеки, используемые в приложении, получают тот же набор ограничений, что и само приложение. ѕоэтому сторонние библиотеки могут использовать разрешени€, выданные всему приложению, дл€ совершени€ вредоносной активности. ѕриложени€ к тому же могут перехватывать системные событи€, пересылаемые через широковещательный запрос, и сохран€ть информацию о вход€щих звонках и —ћ—.
2.5. ”€звимости в самих приложени€х
аждое приложение сохран€ет какие-то данные о пользователе. Ёти данные должны быть защищены должным образом, чтобы к ним не могли получить доступ другие приложени€, Ч но така€ защита предусмотрена не всегда. Ќапример, Skype в одной из версий приложени€ сохран€л базу данных контактов в открытом виде на диске. “аким образом, контакты можно было прочитать любым другим приложением, у которого есть доступ к диску [26]. “акже приложени€ могут использовать криптографические библиотеки с ошибками [27] или же какие-то собственные реализации. тому же не все приложени€ производ€т хорошую аутентификацию и авторизацию пользовател€. роме этого, приложени€ могут позвол€ть SQL-инъекции и подвержены атакам XSS. “акже стоит отметить, что большинство разрабатываемых приложений написаны на Java без использовани€ какой-либо защиты дл€ бинарного кода, а байт-код Java, как известно, легко поддаетс€ дизассемблированию и анализу. —тоит отметить, что к этой категории у€звимостей относитс€ также известный список Mobile OWASP-10. ћногие подобные у€звимости описаны в [28, 29].
2.6. ”€звимости во встроенных сервисах и библиотеках
—тандартный набор библиотек и сервисов, работающих в Android, также содержит у€звимости. Ќапример, недавно была обнаружена у€звимость Stagefright в библиотеке дл€ отображени€ видео в MMS-сообщени€х, которой были подвержены все версии Android, начина€ с 2.2 [30]. ѕозже была обнаружена у€звимость в компоненте MediaServer, которой подвержены все версии Android c 2.3 до 5.1 [31]. ¬ статье [13] показаны у€звимости рантайма Dalvik: запустив большое количество процессов в системе, можно добитьс€, что последующий процесс запуститс€ с правами администратора.
2.7. »нтернет-источники
Android-приложени€ распростран€ютс€ через широкое количество источников помимо официального магазина приложений. ѕоскольку Android-приложени€ написаны в основном на Java, то они легко поддаютс€ обратной разработке и переупаковке с использованием вредоносного кода [32, 33]. роме того, как было показано в статье [34], песочницу анализа приложений Bouncer, используемую в официальном каталоге, легко обойти. ѕоэтому и в самом официальном магазине содержитс€ большое количество вредоносных программ. роме этого, Android поддерживает удаленную установку приложений через Google Play на устройства, св€занные с Google-аккаунтом. “аким образом, если взломать учетную запись Google дл€ устройства, можно установить из Google Play вредоносное приложение, которое туда предварительно загрузил злоумышленник. ѕри этом на экране мобильного телефона не требуетс€ каких-либо подтверждений этих действий, поскольку они запрашиваютс€ в окне браузера и приложение устанавливаетс€ на телефон в фоновом режиме при получении доступа к »нтернету. “акже к этой категории у€звимостей относитс€ использование социальной инженерии, когда дл€ продолжени€ работы предлагают установить приложение из неавторизованного источника [35].
2.8. ”€звимости аппаратуры и св€занных с ней модулей и протоколов
ћобильные устройства, работающие под управлением ќ— Android, имеют широкий набор аппаратуры дл€ взаимодействи€ с внешним миром. —оответствующие у€звимости можно эксплуатировать при непосредственной близости к устройству или при наличии физического доступа к устройству. ѕримерами таких атак служат атака типа Ђотказ в обслуживанииї на технологию Wi-Fi Direct [36], кража данных кредитных карт с помощью NFC [37], исполнение удаленного кода через Bluetooth [38], установка вредоносного приложени€ без ведома пользовател€ через adb с помощью механизма бэкапов [39]. ¬ работе [13] показаны у€звимости, с помощью которых можно повысить привилегии приложени€, использу€ ошибки в реализации протокола adb.
3. »нструменты дл€ анализа Android-приложений
— того момента, как были выпущены первые Android-телефоны, было написано большое количество инструментов дл€ анализа Android-приложений. Ќаиболее полный обзор этих инструментов содержитс€ в стать€х [40, 41, 42, 2]. ¬ первых трех источниках инструменты классифицированы по видам анализа: статический, динамический и их объединение (смешанный). ¬ статье [2] используетс€ классификаци€ инструментов по стади€м развертывани€ приложени€ на Android-устройстве. ¬ нашей работе используетс€ классификаци€ по видам анализа.
—татический анализ
»нструменты статического анализа можно разделить на следующие категории:
- »нструменты, извлекающие метаинформацию из манифеста приложени€ и предоставл€ющие информацию о запрашиваемых разрешени€х, компонентах Activity, сервисах и зарегистрированных Broadcast receivers. ћетаинформаци€ часто используетс€ позже в динамическом анализе дл€ запуска функций приложени€.
- »нструменты дл€ модификации существующего байт-кода приложени€ с использованием техники инструментировани€. Ёто позвол€ет, например, добавл€ть трассирование функциональности в существующие приложени€.
- »нструменты, которые реализуют декомпил€тор или дизассемблер байт-кода Dalvik.
ќдним из наиболее попул€рных инструментов обратной разработки €вл€етс€ Apktool [43]. ќн имеет возможности декодировани€ ресурсов приложени€ приблизительно в оригинальную форму, переупаковки приложений обратно в APK/JAR-файлы, отладку байт-кода smali. ƒл€ декомпилировани€ и компилировани€ в apktool байт-кода Dalvik используетс€ другой широко известный проект smali/backsmali [44]. “акже дл€ дизассемблировани€ байт-кода Dalvik часто примен€етс€ инструмент Dedexer [45].
Radare2 [46] Ч инструмент с открытым исходным кодом дл€ дизассемблировани€, анализа, отладки и изменени€ бинарных файлов Android-приложени€.
ќдин из самых разносторонних инструментов дл€ статического анализа Ч Androguard [47]. ќн может дизассемблировать и декомпилировать приложение обратно в исходный код Java. ѕолучив два APK-файла, он может посчитать коэффициент их похожести дл€ детектировани€ переупакованных приложений или известных вредоносных приложений. Ѕлагодар€ своей гибкости он используетс€ в некоторых инструментах смешанного анализа.
Ѕолее полный список инструментов статического анализа можно найти в стать€х, указанных выше. —ледует отметить, что статический анализ имеет р€д существенных ограничений, св€занных с тем, что имеетс€ лишь абстрактное представление о программе. Ќапример, статический анализ становитс€ намного сложнее, если к программе применены обфусцирующие преобразовани€. ¬ зависимости от сложности обфускации некоторые (а может, и все) статические подходы могут стать абсолютно бесполезными. ≈сли вызов каждого метода делаетс€ только косвенно, вр€д ли удастс€ построить граф вызовов программы. ¬ Android такое преобразование можно сделать, использу€ Java Reflection API дл€ вызова методов и создани€ объектов вместо использовани€ обычных вызовов и инструкций создани€ нового объекта. Ќа рынке решений по защите исходного кода уже представлено несколько продуктов дл€ обфускации файлов Android-приложений, которые могут свести на нет все преимущества статического анализа [48, 49]. Ѕолее подробно о техниках противодействи€ статическому анализу можно почитать в 50.
ƒинамические и смешанные инструменты анализа
»нструменты динамического анализа отслеживают поведение неизвестного приложени€ во врем€ выполнени€ при запуске его в контролируемой песочнице дл€ получени€ поведенческого следа. ƒл€ этого производитс€ инструментирование песочницы на различных уровн€х архитектуры участками кода, которые отслеживают поведение приложени€ и ќ— Android.
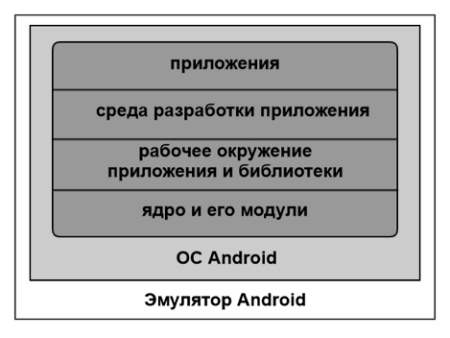
–ис. 2. ”ровни архитектуры песочницы Android
јрхитектура песочницы Android представл€ет из себ€ эмул€тор Android (чаще всего QEMU), внутри которого работает ќ— Android. »нструментирование производитс€ либо на уровне эмул€тора, либо на уровне ќ— Android, либо и там и там. ”ровень ќ— Android также делитс€ на четыре подуровн€:
- приложени€,
- среда разработки приложени€,
- рабочее окружение приложени€ и библиотеки,
- €дро и его модули.
“ехники, используемые в динамическом анализе приложени€:
- ќтслеживание помеченных данных. “акие инструменты используютс€, чтобы отслеживать потенциальные утечки конфиденциальной информации.
- ћониторинг системных вызовов. »нструменты могут записывать системные вызовы с помощью инструментировани€ виртуальных машин, strace или модул€ €дра. Ёто позвол€ет производить трассировку машинного кода.
- “рассировка методов (функций). »нструменты могут отслеживать вызовы Java-методов приложени€ в виртуальной машине Dalvik, вызовы функций в машинных кодах через JNI, системные вызовы и прерывани€.
инструментам смешанного анализа относ€тс€ инструменты, которые сочетают в себе техники динамического и статического анализа.
4. »деальна€ система полносистемного анализа платформы Android
—татьи [40, 41, 42, 2] насчитывают более 40 различных инструментов как дл€ анализа Android-приложений, так и дл€ анализа ќ— Android в целом. ак было замечено в стать€х [34, 60, 61], существующие инструменты динамического анализа обладают р€дом серьезных недостатков. ƒанные недостатки присущи и стандартному инструменту анализа приложений в магазине Google Play Ч Google Bouncer, вследствие чего вредоносные приложени€ могут распростран€тьс€ через официальный магазин, не будучи обнаруженными.
—опоставление возможностей подходов и систем в рассмотренных публикаци€х позвол€ет сформулировать требовани€ к идеальной системе анализа платформы Android, котора€ способна анализировать в совокупности приложени€ и все слои системного ѕќ. —истема заимствует некоторые эффективные приемы из рассмотренных работ, комбиниру€ их с целью преодолени€ недостатков в существующих решени€х.
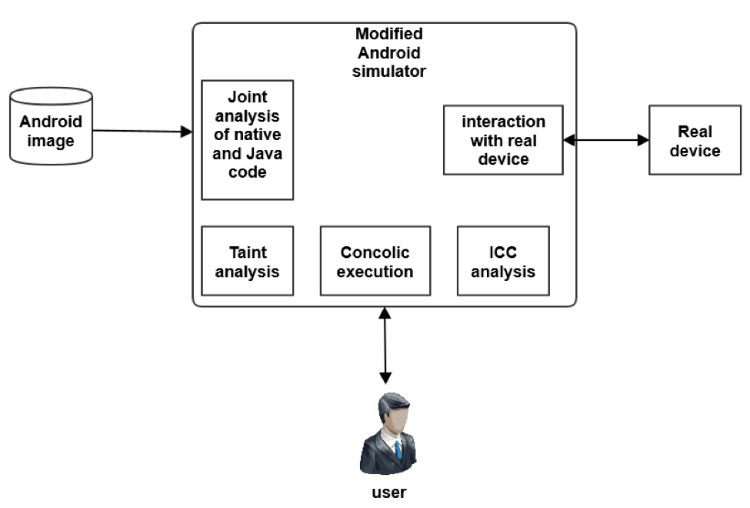
јрхитектура системы представлена на рис. 3. ќсновным компонентом €вл€етс€ полносистемный эмул€тор, который может загружать как прошивки ќ— Android с реальных устройств, так и официальный образ Android дл€ эмул€тора. Ёмул€тор поддерживает проброс датчиков от реального устройства, а также исполнение отдельных участков кода на реальных устройствах. ¬нутри эмул€тора работают модули, которые обеспечивают:
- поддержку смешанного исполнени€,
- трассировку приложений,
- анализ помеченных данных,
- анализ межкомпонентного взаимодействи€,
- склейку машинного и Java-кода приложени€,
- взаимодействие с реальным оборудованием.
—писок требований к данной системе:
1. ѕоддержка загрузки прошивок от производителей различных устройств
—ущественным недостатком всех существующих инструментов анализа ќ— Android и ее приложений €вл€етс€ невозможность запуска прошивок от производителей устройств в доступных эмул€торах. ак было показано в п. 2.2, модифицированные прошивки от производителей устройств содержат от 65 до 85% у€звимостей, обнаруженных во всей системе. Ќа данный момент не существует инструментов дл€ анализа, которые позвол€ли бы запускать прошивки от производителей. ¬се существующие решени€ работают на специальной сборке Android дл€ виртуальной платформы GoldFish.
2. ¬озможность исполнени€ отдельных кусков машинного кода на реальном устройстве
ѕо информации из статей [34, 61], существуют способы вы€влени€ работы внутри эмул€тора. ак правило, вы€вл€етс€ выполнение в эмул€торе QEMU в режиме бинарной трансл€ции, поскольку именно на нем основано большинство песочниц. —пособы основаны на разном поведении определенных участков машинного кода в эмул€торе и на реальном устройстве. “ак как изменение механизма бинарной трансл€ции представл€етс€ сложной задачей, исполнение отдельных кусков машинного кода на реальном устройстве было бы хорошим подходом дл€ противосто€ни€ данным способам обнаружени€ эмул€тора.
3. ѕроброс данных от датчиков оборудовани€ реальных устройств в эмул€тор
ак было описано в стать€х [34, 61], существуют способы определени€ эмул€тора, основанные на данных, получаемых от датчиков оборудовани€, таких как акселерометр, гироскоп, GPS, датчик света, силы т€жести. ¬ыходные значени€ этих датчиков основаны на информации, собранной из окружающей среды, и следовательно, реалистична€ их эмул€ци€ €вл€етс€ сложной задачей. ѕрисутствие такого рода датчиков Ч основное различие между смартфонами и настольными компьютерами. ”величивающеес€ число датчиков на смартфонах дает новые возможности дл€ идентификации мобильных устройств.
4. —овместный анализ на уровне Java-кода и машинного кода
«атруднением дл€ многих систем анализа Android-приложений €вл€етс€ то, что приложени€ содержат как модули в байт-коде Dalvik, так и модули в машинных кодах. »з существующих решений поддержка анализа всех модулей реализована только в DroidScope [57] и CopperDroid [58, 59]. »деальна€ система анализа должна позвол€ть отслеживать потоки данных и управлени€ на уровне пользовательского и системного кода. ƒл€ пользовательского кода, когда это возможно, следует поднимать уровень представлени€ до Java-кода, €вл€ющегос€ высокоуровневым €зыком разработки. “акже необходимо обеспечивать Ђсклейкуї потоков данных и управлени€ при переходе от машинного кода к Java и наоборот.
5. ѕоддержка анализа межкомпонентного взаимодействи€
¬ статье о CopperDroid [58] показана реализаци€ поддержки анализа межкомпонентного взаимодействи€ как внутри Android-приложени€, так и между различными приложени€ми. Ёто сделано с помощью перехвата данных, проход€щих через компонент €дра Binder, так как все взаимодействие проходит через него. ѕодход, реализованный в CopperDroid, позвол€ет не производить модификации исходного кода Android, что делает возможность его переноса на новые версии ќ— Android и новую среду запуска приложений ART с минимальными изменени€ми.
6. «ащита от статических эвристик обнаружени€
ак показано в стать€х [[57], 61], большинство песочниц дл€ анализа можно обнаружить, просто проверив значени€ IMEI, IMSI или номера сборки прошивки у устройства. “акже эмул€тор может быть обнаружен, если проверить на стандартные значени€ таблицу маршрутизации. »з существующих решений защита от обнаружени€ по статическим эвристикам реализована только в проекте ApkAnalyzer [65].
7. ћинимальные изменени€ прошивок Android
“акже стоит отметить, что многие решени€ динамического анализа основаны на инструментировании кода различных компонентов ќ— Android, в частности виртуальной машины Dalvik. Ёто осложн€ет их дальнейшую поддержку, а также миграцию в новую среду запуска приложений ART. ћногие песочницы ограничиваютс€ только анализом кода компонентов Java, тогда как все больше и больше приложений используют компоненты в машинных кодах.
8. ѕоддержка полносистемного анализа помеченных данных с отслеживанием потоков управлени€
—тоит отметить, что многие из инструментов динамического анализа используют анализ помеченных данных, использу€ дл€ этого инструмент TaintDroid [56]. ¬ статье [60] были показаны успешные способы обхода анализа данного инструмента. ѕричиной успешности данных атак €вл€ютс€ следующие факты: 1) TaintDroid отслеживает только потоки данных и не отслеживает потоки управлени€, 2) TaintDroid отслеживает потоки данных только на уровне виртуальной машины Dalvik и проход€щих через интерфейс JNI. ¬озможные пути разрешени€ данных недостатков описаны в [60] и дают направление дл€ дальнейших исследований.
9. ѕоддержка символьного исполнени€ и частичного исполнени€ с конкретными значени€ми с использованием данных, полученных из статического анализа кода (concolic execution Ч смешанное исполнение)
¬ статье [51] описана среда анализа, реализующа€ данный подход. Ёта среда сочетает в себе техники статического анализа графа потока управлени€ программы, символьного исполнени€ программы и исполнени€ программы с конкретными значени€ми. ѕодходы, сочетающие техники символьного исполнени€ и исполнени€ программы с конкретными значени€ми, описаны в стать€х [52, 53, 54, 55]. ÷елью данного метода €вл€етс€ наблюдение путей исполнени€, которые привод€т к секци€м программы, содержащим Ђинтересныйї код. ѕод Ђинтереснымї кодом понимают такой код, выполнение которого зависит от каких-либо произошедших внешних событий или настроек окружени€ системы. Ќапример, код классов в Android, динамически подгружаемый с помощью компонента DexClassLoader или вызов Ђмашинныхї методов через интерфейс JNI.
«аключение
ѕроблемы безопасности мобильной ќ— Android существуют на всех уровн€х платформы и требуют более комплексного подхода, чем те меры защиты, которые можно наблюдать сейчас. ѕри разработке классификации у€звимостей, представленной в данной статье, было замечено, что одна из главных проблем Ч значительна€ фрагментаци€ рынка, котора€ не позвол€ет организовать своевременную поставку обновлений безопасности всем устройствам, как это реализовано в iOS.
ѕри этом ныне существующие средства защиты, включа€ антивирусы и песочницы, имеют множество недостатков и не могут полностью защитить пользовател€. ’от€ создать песочницу дл€ полносистемного анализа ќ— Android без описанных недостатков можно, если руководствоватьс€ списком требований, представленных в данной статье.
Ќесмотр€ на такую пессимистичную картину, в последнее врем€ наблюдаетс€ р€д позитивных движений в сторону улучшени€ безопасности Android. ¬ частности, компани€ Google запустила программу выпуска обновлений безопасности: они выход€т каждый мес€ц и некоторые вендоры все же добавл€ют их в свои версии прошивки (устройства, поддерживаемые Google, получают эти обновлени€ первыми). роме того, пользователи могут самосто€тельно установить на свои устройства версию ќ— Android CyanogenMod (ныне LineageOS), котора€ поддерживает эти обновлени€ безопасности. “акже пользователь может снизить риски, если ограничитс€ набором попул€рных приложений только из официального магазина Google Play. ”€звимости типа RCE (удаленное выполнение кода) встречаютс€ все реже, поэтому доставка вредоносных приложений на телефоны чаще происходит через фишинговые сайты, неофициальные магазины приложений или с помощью социальной инженерии. —реднестатистический пользователь ќ— Android, соблюда€ определенную технику безопасности, может быть спокоен за свой смартфон.
јвтор: ћихаил –оманеев (@melon)
—сылки и использованные материалы:
- statista.com/statistics/281106/number-of-android-app-downloads-from-google-play
- Tan D. J. J. et al. Securing Android: A Survey, Taxonomy, and Challenges // ACM Computing Surveys (CSUR). 2015. Vol. 47. є 4. P. 58.
- file.gdatasoftware.com/web/en/documents/whitepaper/G_DATA_Mobile_Malware_Report_H1_2016_EN.pdf
- developer.android.com/ndk/guides/stable_apis.html
- Dalvik VM Internals // sites.google.com/site/io/dalvik-vm-internals
- securityweek.com/overwhelming-majority-android-devices-dont-have-latest-security-patches
- Google I/O 2014 Ч The ART runtime // youtube.com/watch?v=EBlTzQsUoOw
- media.defcon.org/DEF%20CON%2024/DEF%20CON%2024%20presentations/DEFCON-24-Huber-Rasthofer-Smartphone-Antivirus-And-Security-Applications-Under-Fire.pdf
- developer.android.com/guide/components/services.html
- source.android.com/devices/tech/security/selinux
- developer.android.com/preview/features/runtime-permissions.html
- Enck W., Ongtang M., McDaniel P. Understanding android security // IEEE security & privacy. 2009. є 1. P. 50Ч57.
- Shabtai A., Mimran D., Elovici Y. Evaluation of Security Solutions for Android Systems // arXiv preprint arXiv:1502.04870. Ч 2015.
- Hei X., Du X., Lin S. Two vulnerabilities in Android OS kernel // Communications (ICC), 2013 IEEE International Conference on. IEEE, 2013. P. 6123Ч6127.
- forum.xda-developers.com/showthread.php?t=2048511
- Zhou X. et al. Identity, location, disease and more: Inferring your secrets from android public resources // Proceedings of the 2013 ACM SIGSAC conference on Computer & communications security. ACM, 2013. P. 1017Ч1028.
- Wu L. et al. The impact of vendor customizations on android security // Proceedings of the 2013 ACM SIGSAC conference on Computer & communications security. ACM, 2013. P. 623Ч634.
- en.wikipedia.org/wiki/Stagefright_(bug)
- Zhou X. et al. The peril of fragmentation: Security hazards in android device driver customizations // Security and Privacy (SP), 2014 IEEE Symposium on. IEEE, 2014. P. 409Ч423.
- Sun M., Tan G. NativeGuard: Protecting android applications from third-party native libraries // Proceedings of the 2014 ACM conference on Security and privacy in wireless & mobile networks. ACM, 2014. P. 165Ч176.
- Octeau D. et al. Effective inter-component communication mapping in android with epicc: An essential step towards holistic security analysis // USENIX Security 2013.
- Chin E. et al. Analyzing inter-application communication in Android // Proceedings of the 9th international conference on Mobile systems, applications, and services. ACM, 2011.
- Felt A. P. et al. Permission Re-Delegation: Attacks and Defenses // USENIX Security Symposium. 2011.
- Bugiel S. et al. Xmandroid: A new android evolution to mitigate privilege escalation attacks // Technische Universit"at Darmstadt, Technical Report TR-2011-04.
- Bugiel S. et al. Towards Taming Privilege-Escalation Attacks on Android // NDSS. 2012.
- cvedetails.com/cve/CVE-2011-1717
- Fahl S. et al. Why Eve and Mallory love Android: An analysis of Android SSL (in) security // Proceedings of the 2012 ACM conference on Computer and communications security. ACM, 2012. P. 50Ч61.
- owasp.org/index.php/Projects/OWASP_Mobile_Security_Project_-_Top_Ten_Mobile_Risks
- Lu L. et al. Chex: statically vetting android apps for component hijacking vulnerabilities //Proceedings of the 2012 ACM conference on Computer and communications security. ACM, 2012. P. 229Ч240.
- kb.cert.org/vuls/id/924951
- CVE-2015-3842 // cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3842
- Zhou Y. et al. Hey, You, Get Off of My Market: Detecting Malicious Apps in Official and Alternative Android Markets // NDSS. 2012.
- Nolan G. Decompiling android. Ц Apress, 2012.
- Petsas T. et al. Rage against the virtual machine: hindering dynamic analysis of android malware // Proceedings of the Seventh European Workshop on System Security. ACM, 2014. P. 5.
- Android Security Underpinnings // youtube.com/watch?v=NS46492qyJ8
- coresecurity.com/advisories/android-wifi-direct-denial-service
- securityaffairs.co/wordpress/37667/hacking/nfc-attack-credit-card.html
- zerodayinitiative.com/advisories/ZDI-15-092/
- securityfocus.com/archive/1/535980/30/150/threaded
- Neuner S. et al. Enter sandbox: Android sandbox comparison // arXiv preprint arXiv:1410.7749. 2014.
- Hoffmann J. From Mobile to Security: Towards Secure Smartphones: дис. Ц 2014.
- Faruki P. et al. Android Security: A Survey of Issues, Malware Penetration and Defenses.
- ibotpeaches.github.io/Apktool
- github.com/JesusFreke/smali
- dedexer.sourceforge.net
- radare.org/r
- github.com/androguard/androguard
- dexprotector.com
- guardsquare.com/dexguard
- PANDORA applies non-deterministic obfuscation randomly to Android, Schulz P. Code protection in android // Insititute of Computer Science, Rheinische Friedrich-Wilhelms-Universit"at Bonn, Germany. 2012.
- Sch"utte J., Fedler R., Titze D. Condroid: Targeted dynamic analysis of android applications // in review. 2014.
- Sen K. DART: Directed Automated Random Testing // Haifa Verification Conference. 2009. Vol. 6405. P. 4.
- Sen K., Marinov D., Agha G. CUTE: a concolic unit testing engine for C. ACM, 2005. Vol. 30. є 5. P. 263Ч272.
- Godefroid P. Random testing for security: blackbox vs. whitebox fuzzing // Proceedings of the 2nd international workshop on Random testing: co-located with the 22nd IEEE/ACM International Conference on Automated Software Engineering (ASE 2007). ACM, 2007. P. 1.
- Jayaraman K. et al. jFuzz: A Concolic Whitebox Fuzzer for Java // NASA Formal Methods. 2009. P. 121Ч125.
- Enck W. et al. TaintDroid: an information-flow tracking system for realtime privacy monitoring in smartphones // ACM Transactions on Computer Systems (TOCS). 2014. Vol. 32. є 2. P. 5.
- Yan L. K., Yin H. DroidScope: Seamlessly Reconstructing the OS and Dalvik Semantic Views for Dynamic Android Malware Analysis // USENIX Security Symposium. 2012. P. 569Ч584.
- Tam K. et al. CopperDroid: Automatic Reconstruction of Android Malware Behaviors // Proc. of the Symposium on Network and Distributed System Security (NDSS). 2015.
- copperdroid.isg.rhul.ac.uk/copperdroid
- Sarwar G. et al. On the Effectiveness of Dynamic Taint Analysis for Protecting against Private Information Leaks on Android-based Devices // SECRYPT. 2013. P. 461Ч468.
- Jing Y. et al. Morpheus: automatically generating heuristics to detect Android emulators // Proceedings of the 30th Annual Computer Security Applications Conference. ACM, 2014. P. 216Ч225.
- googleprojectzero.blogspot.ru/2016/12/bitunmap-attacking-android-ashmem.html
- bbqand0days.com/Pork-Explosion-Unleashed
- powerofcommunity.net/poc2016/x82.pdf
- apk-analyzer.net
- www.phdays.ru/program/fast-track/45984
| омментировать | « ѕред. запись — дневнику — —лед. запись » | —траницы: [1] [Ќовые] |






