ћаги€ SSH |
— SSH многие знакомы давно, но, как и €, не все подозревают о том, какие возможности та€тс€ за этими магическими трем€ буквами. ’отел бы поделитьс€ своим небольшим опытом использовани€ SSH дл€ решени€ различных административных задач.
ќглавление:
1) Local TCP forwarding
2) Remote TCP forwarding
3) TCP forwarding chain через несколько узлов
4) TCP forwarding ssh-соединени€
5) SSH VPN Tunnel
6) оротко о беспарольном доступе
7) —пасибо (ссылки)
Ќачнем с простого Ч local TCP forwarding:
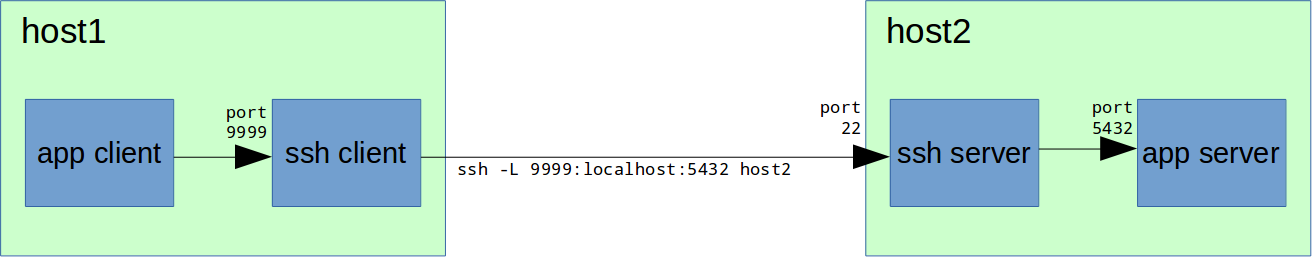
»меем удаленный сервер Ђhost2ї с неким приложением, допустим, PostgreSQL server, которое принимает TCP-соединени€ на порту 5432. ѕри этом вполне логично, что на этом сервере стоит файрвол, который пр€мых соединений извне на порт 5432 не разрешает, но при этом есть доступ по SSH (по-умолчанию порт 22, рекомендую его изменить). “ребуетс€ подключитьс€ с нашего рабочего места Ђhost1ї клиентским приложением к серверу PostgreSQL на Ђhost2ї.
ƒл€ этого на Ђhost1ї в консоли набираем:
“еперь на Ђhost1ї мы можем соедин€тьс€ с PostgreSQL сервером через локальный порт 9999:
ћы также можем соедин€тьс€ с приложением не на самом Ђhost2ї, а на любой доступной ему машине:
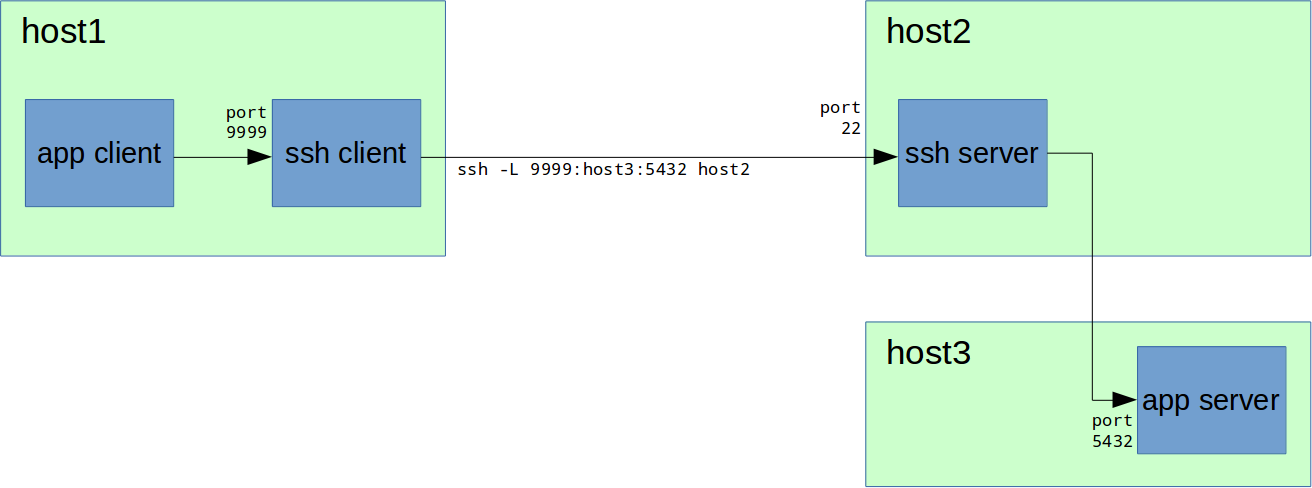
ƒл€ этого при пробросе портов вместо Ђlocalhostї указываем им€ хоста, например Ђhost3ї:
“ут важно заметить, что Ђhost3ї должен быть известен (если это им€, а не IP-адрес) и доступен дл€ машины Ђhost2ї.
“акже можно через Ђhost1ї предоставить доступ любому другому узлу (назовем его Ђhost1Aї) к сервису на Ђhost3ї:

ƒл€ этого нужно вставить в команду соединени€ ssh IP-адрес интерфейса, на котором будет подн€т локальный порт 9999:
¬ данном примере порт 9999 будет открыт на всех доступных на Ђhost1ї IPv4 интерфейсах.
Ќо что делать, если, например, Ђhost2ї не имеет белого IP-адреса, находитс€ за NAT или вообще все вход€щие соединени€ к нему закрыты? »ли, например, на Ђhost2ї стоит Windows и нет возможности поставить SSH-сервер?
ƒл€ этого случа€ есть Remote TCP forwarding:

“еперь нужно устанавливать ssh-соединение в обратном направлении Ч от Ђhost2ї к Ђhost1ї. “.е. наша административна€ рабоча€ станци€ будет SSH-сервером и будет доступна по SSH с Ђhost2ї, а на Ђhost2ї нужно будет выполнить подключение SSH-клиентом:
“акже у вас возникнут дополнительные сложности с обеспечением безопасности на Ђhost1ї, если вы не довер€ете узлу Ђhost2ї. ќднако это выходит за рамки данной статьи.
», конечно, вы каким-то образом (сами или с посторонней помощью) должны инициировать ssh-соединение со стороны Ђhost2ї вводом приведенной выше команды, а Ђhost1ї должен иметь белый IP-адрес и открытый порт SSH.
ѕосле установки ssh-соединени€ все работает аналогично предыдущей главе.
¬ закрытых сет€х часто бывает, что нужный нам узел напр€мую недоступен. “.е. мы можем зайти на нужный хост только по цепочке, например host1 -> host2 -> host3 -> host4:
Ёто может происходить например если эти узлы €вл€ютс€ шлюзами, либо если на них доступны шлюзы только в соседние подсети.
¬ таком случае мы также можем делать TCP forwarding по цепочке:
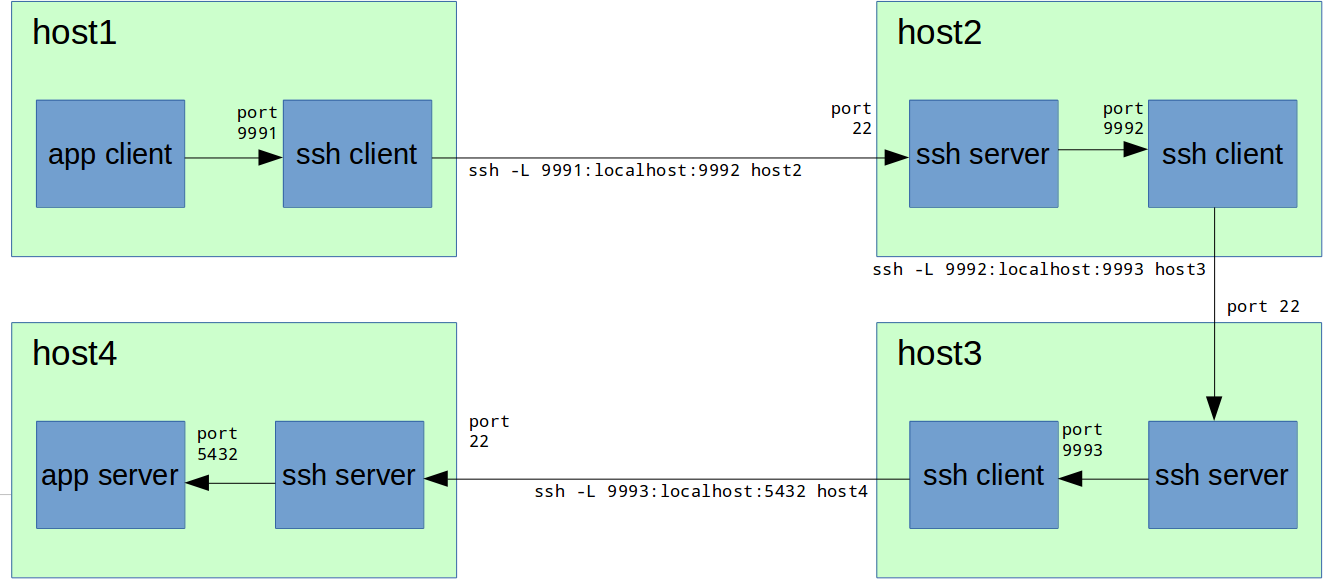
«десь порты 9991, 9992, 9993 выбраны дл€ нагл€дности, на практике можно использовать один и тот же порт (например, 9999), если он свободен на всех узлах.
»того нужно выполнить следующую цепочку команд:
»ногда бывает нужно соединитьс€ по ssh с сервером, который напр€мую недоступен, а доступ возможен только по цепочке ssh-серверов (см. предыдущую главу).
“еперь мы обладаем нужными знани€ми чтобы сделать следующее:
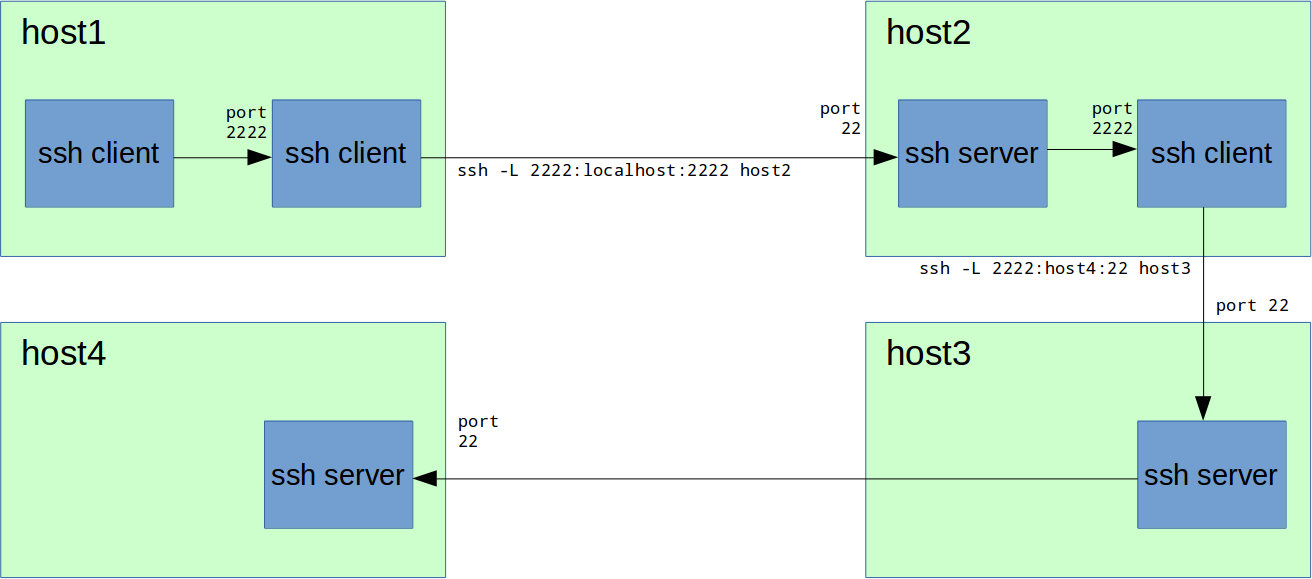
“аким образом, на порту 2222 на Ђhost1ї у нас теперь есть форвардинг на порт SSH (22) на Ђhost4ї. ћожем соединитьс€:
азалось бы, зачем это нужно? Ќапример, вот зачем:
Ќу и вообще, здорово что теперь Ђhost4ї так близко :)
¬ывод: можно делать TCP forwarding большого уровн€ вложенности.
TCP port forwarding Ч это отлична€ возможность. Ќо что если нам нужно больше? ƒоступ по UDP, доступ к множеству портов и хостов, доступ к динамическим портам? ќтвет очевиден Ч VPN. » всемогущий SSH начина€ с версии 4.3 и здесь придет нам на помощь.
«абега€ вперед скажу: этот функционал SSH хорошо работает если вам нужно временное решение дл€ каких-то административных задач. ƒл€ построени€ посто€нных VPN этот вариант далеко не самый подход€щий, т.†к. он предполагает TCP-over-TCP, что плохо скажетс€ на скорости соединени€.
Ќастройка SSH-сервера:
PermitTunnel в настройках sshd по-умолчанию выключен, его нужно включить в /etc/ssh/sshd_config:
или
¬ј∆Ќќ: дл€ подн€ти€ нового сетевого интерфейса туннел€ и на ssh-клиенте, и на ssh-сервере необходимы права суперпользовател€. ћожно долго спорить о том, насколько это небезопасно, но в большинстве случаев на ssh-сервере достаточно настройки:
“аким образом вы запрещаете вход root по паролю, а разрешаете только другими средствами, например, по ключу RSA, что гораздо безопаснее.
ѕерезапускаем sshd:
или
“уннель поднимаетс€ при использовании магического ключа -w:
√де 5:5 Ч номер интерфейса на локальной машине и на удаленной соответственно.
«десь вас может смутить, что ifconfig не выдаст в списке интерфейса Ђtun5ї. Ёто потому что он в состо€нии Ђdownї, а вот если вызвать Ђifconfig -aї или Ђifconfig tun5ї, то интерфейс будет виден:
Ќазначаем интерфейсам IP-адреса и поднимаем их:
≈сли есть файрвол, не забываем разрешить соединени€ с интерфейса tun5:
Ќа host1 это делать необ€зательно, здесь это сделано лишь дл€ того чтобы ping работал в обе стороны.
Ќаслаждаемс€ пингом:
≈сли рассмотреть более ранний пример с PostgreSQL, то теперь схема будет така€:
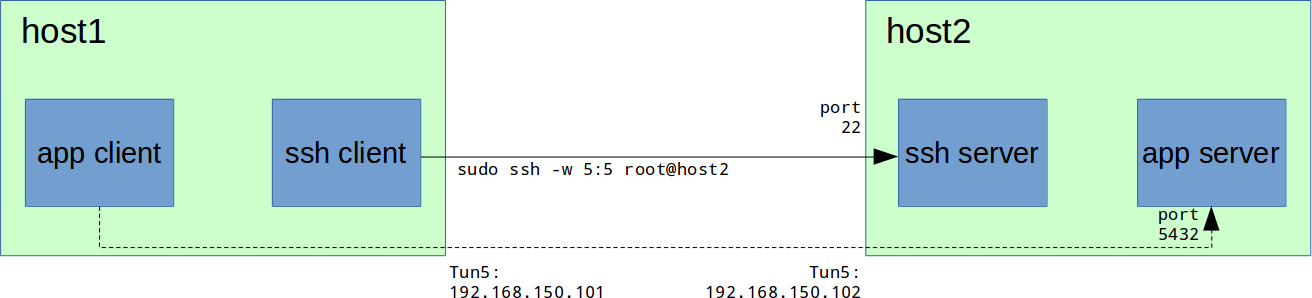
ј команда дл€ подключени€ к серверу PostgreSQL будет выгл€деть так:
Ќу а далее можно делать какой-либо из этих узлов шлюзом, если нужно обеспечить доступ не к одному узлу, а к сети. Ќапример:
ѕосле окончани€ работы не забываем вернуть net.ipv4.ip_forward и файрвол в исходное состо€ние.
ƒумаю, все уже знают что авторизаци€ по паролю это не про нас. Ќо на вс€кий случай впихну сюда краткую инструкцию по настройке аутентификации по ключу RSA:
1. Ќа клиентских машинах генерируем пользователю свой ключ RSA:
ѕо-умолчанию приватный ключ сохран€етс€ в ~/.ssh/id_rsa, а открытый Ч в ~/.ssh/id_rsa.pub. ѕриватный ключ храните как зеницу ока и никому не давайте, никуда не копируйте.
ѕри создании ключа можно задать пароль (passphrase), которым ключ будет зашифрован.
2. лиентские открытые ключи нужно сохранить на ssh-сервере в файле ~/.ssh/authorized_keys (~ это домашн€€ директори€ того пользовател€, которым будете логинитьс€), каждый на отдельной строке. ƒл€ того чтобы это не делать вручную, на каждом клиенте можно воспользоватьс€ командой:
√де user Ч им€ пользовател€ на сервере, sshserver Ч им€ или IP-адрес ssh-сервера.
3. ѕроверьте, что можете зайти на сервер по ключу, без ввода парол€ (не путать с passphrase):
–екомендую не закрывать хот€ бы одну активную ssh-сессию с сервером до тех пор, пока окончательно не закончите настройку и не убедитесь что все работает.
4. ќтключите на SSH-сервере возможность входа по паролю в файле /etc/ssh/sshd_config:
¬озможность входа по открытому ключу обычно уже включена по-умолчанию:
я обычно также отключаю две следующие опции:
¬ некоторых случа€х это позвол€ет ускорить процесс соединени€ (например, когда на сервере нет доступа в »нтернет).
5. ѕерезапустите sshd:

ћетки:
author nitro2005
системное администрирование
серверное администрирование
настройка linux
*nix
ssh
ssh tunnel
ssh-2
vpn
port forwarding
ќглавление:
1) Local TCP forwarding
2) Remote TCP forwarding
3) TCP forwarding chain через несколько узлов
4) TCP forwarding ssh-соединени€
5) SSH VPN Tunnel
6) оротко о беспарольном доступе
7) —пасибо (ссылки)
1) Local TCP forwarding
Ќачнем с простого Ч local TCP forwarding:

»меем удаленный сервер Ђhost2ї с неким приложением, допустим, PostgreSQL server, которое принимает TCP-соединени€ на порту 5432. ѕри этом вполне логично, что на этом сервере стоит файрвол, который пр€мых соединений извне на порт 5432 не разрешает, но при этом есть доступ по SSH (по-умолчанию порт 22, рекомендую его изменить). “ребуетс€ подключитьс€ с нашего рабочего места Ђhost1ї клиентским приложением к серверу PostgreSQL на Ђhost2ї.
ƒл€ этого на Ђhost1ї в консоли набираем:
host1# ssh -L 9999:localhost:5432 host2“еперь на Ђhost1ї мы можем соедин€тьс€ с PostgreSQL сервером через локальный порт 9999:
host1# psql -h localhost -p 9999 -U postgres≈сли на Ђhost1ї Windows
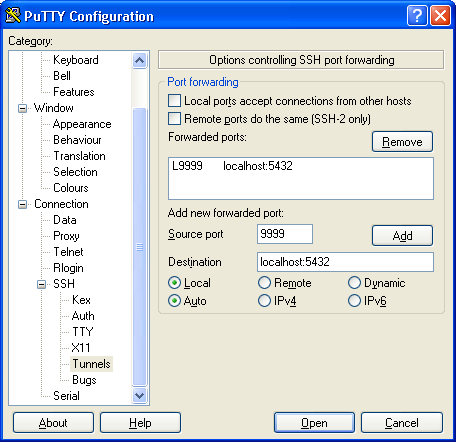
Ќапример, в PuTTy это делаетс€ так:
»дем по дереву настроек: Connection -> SSH -> Tunnels.
ƒалее в поле ЂSource portї вбиваем 9999, в ЂDestinationї Ч localhost:5432, и нажимаем Add.
Ќе забываем после этого сохранить настройки сессии, если требуетс€.
»дем по дереву настроек: Connection -> SSH -> Tunnels.
ƒалее в поле ЂSource portї вбиваем 9999, в ЂDestinationї Ч localhost:5432, и нажимаем Add.
Ќе забываем после этого сохранить настройки сессии, если требуетс€.

ак это работает
ѕосле успешного подключени€ к SSH-серверу на Ђhost2ї, на Ђhost1ї SSH-клиент начинает слушать порт 9999. ѕри подключении к порту 9999 на Ђhost1ї, SSH-сервер на Ђhost2ї устанавливает соединение с localhost (коим и €вл€етс€ дл€ себ€ самого Ђhost2ї) на порт 5432 и передает по этому соединению данные, прин€тые ssh-клиентом на Ђhost1ї на порт 9999.
¬ј∆Ќќ! ¬се указанные на схемах стрелками соединени€ €вл€ютс€ отдельными TCP-соединени€ми (сесси€ми).
¬ј∆Ќќ! ¬се указанные на схемах стрелками соединени€ €вл€ютс€ отдельными TCP-соединени€ми (сесси€ми).
Ќастройка SSH-сервера
Port forwarding, как правило, уже включен в настройках sshd по-умолчанию.
/etc/ssh/sshd_config:
/etc/ssh/sshd_config:
AllowTcpForwarding yesћы также можем соедин€тьс€ с приложением не на самом Ђhost2ї, а на любой доступной ему машине:

ƒл€ этого при пробросе портов вместо Ђlocalhostї указываем им€ хоста, например Ђhost3ї:
host1# ssh -L 9999:host3:5432 host2“ут важно заметить, что Ђhost3ї должен быть известен (если это им€, а не IP-адрес) и доступен дл€ машины Ђhost2ї.
“акже можно через Ђhost1ї предоставить доступ любому другому узлу (назовем его Ђhost1Aї) к сервису на Ђhost3ї:

ƒл€ этого нужно вставить в команду соединени€ ssh IP-адрес интерфейса, на котором будет подн€т локальный порт 9999:
ssh -L 0.0.0.0:9999:host3:5432 host2¬ данном примере порт 9999 будет открыт на всех доступных на Ђhost1ї IPv4 интерфейсах.
2) Remote TCP forwarding
Ќо что делать, если, например, Ђhost2ї не имеет белого IP-адреса, находитс€ за NAT или вообще все вход€щие соединени€ к нему закрыты? »ли, например, на Ђhost2ї стоит Windows и нет возможности поставить SSH-сервер?
ƒл€ этого случа€ есть Remote TCP forwarding:

“еперь нужно устанавливать ssh-соединение в обратном направлении Ч от Ђhost2ї к Ђhost1ї. “.е. наша административна€ рабоча€ станци€ будет SSH-сервером и будет доступна по SSH с Ђhost2ї, а на Ђhost2ї нужно будет выполнить подключение SSH-клиентом:
ssh -R 9999:localhost:5432 host1≈сли на Ђhost2ї Windows
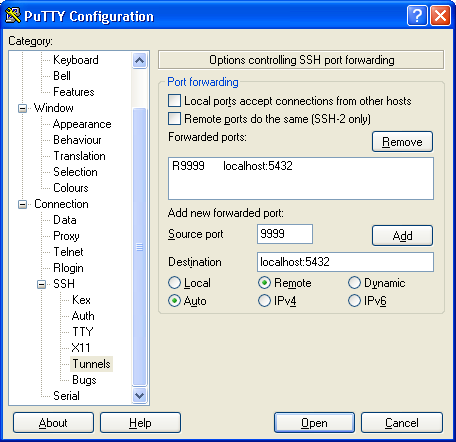
Ќапример, в PuTTy это делаетс€ так:
»дем по дереву настроек: Connection -> SSH -> Tunnels.
ƒалее в поле ЂSource portї вбиваем 9999, в ЂDestinationї Ч localhost:5432, а ниже выбираем ЂRemoteї, и нажимаем Add.
Ќе забываем после этого сохранить настройки сессии, если требуетс€.
»дем по дереву настроек: Connection -> SSH -> Tunnels.
ƒалее в поле ЂSource portї вбиваем 9999, в ЂDestinationї Ч localhost:5432, а ниже выбираем ЂRemoteї, и нажимаем Add.
Ќе забываем после этого сохранить настройки сессии, если требуетс€.

ак это работает
ѕосле успешного подключени€, на Ђhost1ї SSH-сервер начинает слушать порт 9999. ѕри подключении к порту 9999 на Ђhost1ї, SSH-клиент на Ђhost2ї устанавливает соединение с localhost (коим и €вл€етс€ дл€ себ€ самого Ђhost2ї) на порт 5432 и передает по этому соединению данные, прин€тые ssh-сервером на Ђhost1ї на порт 9999.
“акже у вас возникнут дополнительные сложности с обеспечением безопасности на Ђhost1ї, если вы не довер€ете узлу Ђhost2ї. ќднако это выходит за рамки данной статьи.
», конечно, вы каким-то образом (сами или с посторонней помощью) должны инициировать ssh-соединение со стороны Ђhost2ї вводом приведенной выше команды, а Ђhost1ї должен иметь белый IP-адрес и открытый порт SSH.
ѕосле установки ssh-соединени€ все работает аналогично предыдущей главе.
3) TCP forwarding chain через несколько узлов
¬ закрытых сет€х часто бывает, что нужный нам узел напр€мую недоступен. “.е. мы можем зайти на нужный хост только по цепочке, например host1 -> host2 -> host3 -> host4:
host1# ssh host2
host2# ssh host3
host3# ssh host4
host4# echo hello host4Ёто может происходить например если эти узлы €вл€ютс€ шлюзами, либо если на них доступны шлюзы только в соседние подсети.
¬ таком случае мы также можем делать TCP forwarding по цепочке:

«десь порты 9991, 9992, 9993 выбраны дл€ нагл€дности, на практике можно использовать один и тот же порт (например, 9999), если он свободен на всех узлах.
»того нужно выполнить следующую цепочку команд:
host1# ssh -L 9991:localhost:9992 host2
host2# ssh -L 9992:localhost:9993 host3
host3# ssh -L 9993:localhost:5432 host4 ак это работает
ѕосле успешного выполнени€ перечисленных выше команд, на узлах выполн€етс€ следующее:
“аким образом, при соединении на порт 9991 на Ђhost1ї, данные перенаправл€ютс€ по цепочке на Ђhost4ї на порт 5432.
¬ј∆Ќќ! ¬се указанные на схемах стрелками соединени€ €вл€ютс€ отдельными TCP-соединени€ми (сесси€ми).
- на Ђhost1ї: открываетс€ порт 9991, при подключении к которому данные перенаправл€ютс€ по ssh-соединению на порт 9992 на Ђhost2ї;
- на Ђhost2ї: открываетс€ порт 9992, при подключении к которому данные перенаправл€ютс€ по ssh-соединению на порт 9993 на Ђhost3ї;
- на Ђhost3ї: открываетс€ порт 9993, при подключении к которому данные перенаправл€ютс€ по ssh-соединению на порт 5432 на Ђhost4ї;
“аким образом, при соединении на порт 9991 на Ђhost1ї, данные перенаправл€ютс€ по цепочке на Ђhost4ї на порт 5432.
¬ј∆Ќќ! ¬се указанные на схемах стрелками соединени€ €вл€ютс€ отдельными TCP-соединени€ми (сесси€ми).
4) TCP forwarding ssh-соединени€
»ногда бывает нужно соединитьс€ по ssh с сервером, который напр€мую недоступен, а доступ возможен только по цепочке ssh-серверов (см. предыдущую главу).
“еперь мы обладаем нужными знани€ми чтобы сделать следующее:

host1# ssh -L 2222:localhost:2222 host2
host2# ssh -L 2222:host4:22 host3“аким образом, на порту 2222 на Ђhost1ї у нас теперь есть форвардинг на порт SSH (22) на Ђhost4ї. ћожем соединитьс€:
host1# ssh -p 2222 localhost
host4# echo hello host4азалось бы, зачем это нужно? Ќапример, вот зачем:
# копируем файл на host4
host1# scp -P 2222 /local/path/to/some/file localhost:/path/on/host4
# копируем файл с host4
host1# scp -P 2222 localhost:/path/on/host4 /local/path/to/some/file
# делаем еще один замечательный TCP forwarding на host4
host1# ssh -p 2222 -L 9999:localhost:5432 localhost
host1# psql -h localhost -p 9999 -U postgres
# обратите внимание, что порт дл€ команды ssh задаетс€ ключем -p в нижнем регистре,
# а дл€ команды scp -P в верхнем регистреЌу и вообще, здорово что теперь Ђhost4ї так близко :)
¬ывод: можно делать TCP forwarding большого уровн€ вложенности.
«амечани€ про RSA fingerprint
¬ некоторых случа€х scp не отработает, пока не зайдете сначала через ssh -p 2222 localhost и не примете RSA fingerprint удаленного сервера.
≈сли пользуетесь одним и тем же портом (2222) дл€ доступа к разным удаленным серверам, то будут ошибки RSA fingerprint, который осталс€ от предыдущего сервера. ≈го нужно будет удалить из ~/.ssh/known_hosts.
≈сли пользуетесь одним и тем же портом (2222) дл€ доступа к разным удаленным серверам, то будут ошибки RSA fingerprint, который осталс€ от предыдущего сервера. ≈го нужно будет удалить из ~/.ssh/known_hosts.
5) SSH VPN Tunnel
TCP port forwarding Ч это отлична€ возможность. Ќо что если нам нужно больше? ƒоступ по UDP, доступ к множеству портов и хостов, доступ к динамическим портам? ќтвет очевиден Ч VPN. » всемогущий SSH начина€ с версии 4.3 и здесь придет нам на помощь.
«абега€ вперед скажу: этот функционал SSH хорошо работает если вам нужно временное решение дл€ каких-то административных задач. ƒл€ построени€ посто€нных VPN этот вариант далеко не самый подход€щий, т.†к. он предполагает TCP-over-TCP, что плохо скажетс€ на скорости соединени€.
≈ще про TCP forwarding
ј вот TCP port forwarding с помощью SSH, если его достаточно, во многих случа€х выиграет по производительности у VPN, т.†к. при TCP port forwarding передаютс€ только данные приложени€, а не исходные пакеты целиком вместе с заголовками, см. ссылку: http://blog.backslasher.net/ssh-openvpn-tunneling.html
Ќастройка SSH-сервера:
PermitTunnel в настройках sshd по-умолчанию выключен, его нужно включить в /etc/ssh/sshd_config:
PermitTunnel yesили
PermitTunnel point-to-point¬ј∆Ќќ: дл€ подн€ти€ нового сетевого интерфейса туннел€ и на ssh-клиенте, и на ssh-сервере необходимы права суперпользовател€. ћожно долго спорить о том, насколько это небезопасно, но в большинстве случаев на ssh-сервере достаточно настройки:
PermitRootLogin without-password“аким образом вы запрещаете вход root по паролю, а разрешаете только другими средствами, например, по ключу RSA, что гораздо безопаснее.
ѕерезапускаем sshd:
sudo service sshd restart # centosили
/etc/init.d/ssh restart # (debian/ubuntu)“уннель поднимаетс€ при использовании магического ключа -w:
host1# sudo ssh -w 5:5 root@host2√де 5:5 Ч номер интерфейса на локальной машине и на удаленной соответственно.
«десь вас может смутить, что ifconfig не выдаст в списке интерфейса Ђtun5ї. Ёто потому что он в состо€нии Ђdownї, а вот если вызвать Ђifconfig -aї или Ђifconfig tun5ї, то интерфейс будет виден:
host1# ifconfig tun5
tun5 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
POINTOPOINT NOARP MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:500
RX bytes:0 (0.0 b) TX bytes:0 (0.0 b)Ќазначаем интерфейсам IP-адреса и поднимаем их:
host1# sudo ifconfig tun5 192.168.150.101/24 pointopoint 192.168.150.102
host2# sudo ifconfig tun5 192.168.150.102/24 pointopoint 192.168.150.101≈сли есть файрвол, не забываем разрешить соединени€ с интерфейса tun5:
host1# # сохран€ем исходные правила файрвола
host1# sudo iptables-save > /tmp/iptables.rules.orig
host1# sudo iptables -I INPUT 1 -i tun5 -j ACCEPT
host2# # сохран€ем исходные правила файрвола
host2# sudo iptables-save > /tmp/iptables.rules.orig
host2# sudo iptables -I INPUT 1 -i tun5 -j ACCEPTЌа host1 это делать необ€зательно, здесь это сделано лишь дл€ того чтобы ping работал в обе стороны.
Ќаслаждаемс€ пингом:
host1# ping 192.168.150.102
host2# ping 192.168.150.101≈сли рассмотреть более ранний пример с PostgreSQL, то теперь схема будет така€:

ј команда дл€ подключени€ к серверу PostgreSQL будет выгл€деть так:
host1# psql -h 192.168.150.102 -U postgresЌу а далее можно делать какой-либо из этих узлов шлюзом, если нужно обеспечить доступ не к одному узлу, а к сети. Ќапример:
host2# # разрешаем IP forwarding
host2# sudo sysctl -w net.ipv4.ip_forward=1
host2# # разрешаем IP forwarding с host1
host2# sudo iptables -I FORWARD 1 -s 192.168.150.101 -j ACCEPT
host2# # разрешаем IP forwarding на host1
host2# sudo iptables -I FORWARD 1 -d 192.168.150.101 -j ACCEPT
host2# # маскируем IP адрес host1
host2# sudo iptables -t nat -A POSTROUTING -s 192.168.150.101 -j MASQUERADEhost1# # ѕредположим, у host2 есть доступ к сети 192.168.2.x, куда нам нужно попасть с host1
host1# # ѕрописываем host2 как шлюз в сеть 192.168.2.x
host1# sudo ip route add 192.168.2.0/24 via 192.168.150.2
host1# # Ќаслаждаемс€ доступом в сеть с host1
host1# ping 192.168.2.1ѕосле окончани€ работы не забываем вернуть net.ipv4.ip_forward и файрвол в исходное состо€ние.
host1# sudo iptables-restore < /tmp/iptables.rules.orig
host2# sudo iptables-restore < /tmp/iptables.rules.origѕод спойлером более интересный случай с временным расшариванием »нтернета
ƒопустим, нужно настроить сервер в закрытой сети, где доступ в »нтернет запрещен, но тем не менее у вас туда есть лазейка Ч доступ через один ssh-сервер или цепочку ssh-серверов. ѕредположим, дл€ настройки сервера вам нужен на нем доступ в »нтернет. “огда проще самосто€тельно настроить временный доступ в »нтернет на требующем настройки сервере, чем просить это сделать обслуживающий персонал.
ƒопустим, есть доступ по ssh с вашей рабочей машины host1 на сервер host2, с него Ч на host3, а уже оттуда Ч на нужный вам host4. “огда делаем TCP forwarding дл€ ssh (если с host1 вы сразу можете соединитьс€ с host4, пропустите этот шаг):
ƒалее, соедин€емс€ с host4 и поднимаем интерфейс tun5:
—мотрим таблицу маршрутизации на host4, допустим видим следующее:
¬ј∆Ќќ! ƒалее нам скорее всего захочетс€ сделать маршрутом по-умолчанию интерфейс tun5 со шлюзом 192.168.150.101, через который будет доступен »нтернет. ѕоэтому на данном этапе важно точно знать, какие маршруты нужно дописать, чтобы заменить маршрут по-умолчанию. Ёто важно, поскольку довольно часто маршруты на отдельные сети не прописывают отдельно, а просто задают маршрут по-умолчанию (0.0.0.0/0) со шлюзом, через который и идет весь межсетевой трафик. Ѕолее того, вполне веро€тно что ваше ssh-соединение с сервером также использует исходный шлюз по-умолчанию.
ƒл€ простоты в данном примере предположим, что никаких маршрутов кроме 192.168.56.0/24 серверу дл€ нормального функционировани€ не нужно и что предыдущий ssh-хост host3 имеет IP-адрес из этой же сети.
«апоминаем и записываем куда-нибудь исходную маршрутную таблицу со шлюзом по-умолчанию:
Ќастраиваем наш host1 дл€ работы в качестве шлюза в »нтернет дл€ host4:
»змен€ем маршрут по-умолчанию на host4 (ќ—“ќ–ќ∆Ќќ, см. предупреждение выше!):
ѕровер€ем, что есть »нтернет:
ќтлично. ќсталось настроить DNS. ≈сть множество способов это сделать, проще всего отредактировать файл /etc/resolv.conf и добавить туда строчки:
ѕосле этого »нтернет должен быть полностью доступен:
ѕосле окончани€ работы не забываем вернуть все в исходное состо€ние:
ƒопустим, есть доступ по ssh с вашей рабочей машины host1 на сервер host2, с него Ч на host3, а уже оттуда Ч на нужный вам host4. “огда делаем TCP forwarding дл€ ssh (если с host1 вы сразу можете соединитьс€ с host4, пропустите этот шаг):
host1# ssh -L 2222:localhost:2222 host2
host2# ssh -L 2222:host4:22 host3ƒалее, соедин€емс€ с host4 и поднимаем интерфейс tun5:
host1# sudo ssh -p 2222 -w 5:5 root@localhost
host1# # или если host4 доступен сразу: sudo ssh -w 5:5 root@host4
host1# sudo ifconfig tun5 192.168.150.101/24 pointopoint 192.168.150.102
host4# sudo ifconfig tun5 192.168.150.102/24 pointopoint 192.168.150.101—мотрим таблицу маршрутизации на host4, допустим видим следующее:
host4# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.150.0 0.0.0.0 255.255.255.0 U 0 0 0 tun5
192.168.56.0 0.0.0.0 255.255.255.0 U 1 0 0 eth0
0.0.0.0 192.168.56.254 0.0.0.0 UG 0 0 0 eth0¬ј∆Ќќ! ƒалее нам скорее всего захочетс€ сделать маршрутом по-умолчанию интерфейс tun5 со шлюзом 192.168.150.101, через который будет доступен »нтернет. ѕоэтому на данном этапе важно точно знать, какие маршруты нужно дописать, чтобы заменить маршрут по-умолчанию. Ёто важно, поскольку довольно часто маршруты на отдельные сети не прописывают отдельно, а просто задают маршрут по-умолчанию (0.0.0.0/0) со шлюзом, через который и идет весь межсетевой трафик. Ѕолее того, вполне веро€тно что ваше ssh-соединение с сервером также использует исходный шлюз по-умолчанию.
ƒл€ простоты в данном примере предположим, что никаких маршрутов кроме 192.168.56.0/24 серверу дл€ нормального функционировани€ не нужно и что предыдущий ssh-хост host3 имеет IP-адрес из этой же сети.
«апоминаем и записываем куда-нибудь исходную маршрутную таблицу со шлюзом по-умолчанию:
host4# route -n > routes.origЌастраиваем наш host1 дл€ работы в качестве шлюза в »нтернет дл€ host4:
host1# # разрешаем IP forwarding
host1# sudo sysctl -w net.ipv4.ip_forward=1
host1# # сохран€ем исходные правила файрвола
host1# sudo iptables-save > /tmp/iptables.rules.orig
host1# # разрешаем IP forwarding с host4
host1# sudo iptables -I FORWARD 1 -s 192.168.150.102 -j ACCEPT
host1# # разрешаем IP forwarding на host4
host1# sudo iptables -I FORWARD 1 -d 192.168.150.102 -j ACCEPT
host1# # маскируем IP адрес host4
host1# sudo iptables -t nat -A POSTROUTING -s 192.168.150.102 -j MASQUERADE»змен€ем маршрут по-умолчанию на host4 (ќ—“ќ–ќ∆Ќќ, см. предупреждение выше!):
host4# sudo ip route replace default via 192.168.150.101
host4# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.150.0 0.0.0.0 255.255.255.0 U 0 0 0 tun5
192.168.56.0 0.0.0.0 255.255.255.0 U 1 0 0 eth0
0.0.0.0 192.168.150.101 0.0.0.0 UG 0 0 0 tun5ѕровер€ем, что есть »нтернет:
host4# ping 8.8.8.8ќтлично. ќсталось настроить DNS. ≈сть множество способов это сделать, проще всего отредактировать файл /etc/resolv.conf и добавить туда строчки:
nameserver 8.8.8.8
nameserver 8.8.4.4ѕосле этого »нтернет должен быть полностью доступен:
host4# ping ya.ruѕосле окончани€ работы не забываем вернуть все в исходное состо€ние:
host1# # восстанавливаем правила файрвола на host1
host1# sudo iptables-restore < /tmp/iptables.rules.orig
host1# # не забудьте восстановить также значение net.ipv4.ip_forwardhost2# # восстановите маршрут по-умолчанию на host4:
host2# sudo ip route replace default via 192.168.56.254
host2# # и уберите добавленные ранее DNS-сервера из /etc/resolv.conf6) оротко о беспарольном доступе
ƒумаю, все уже знают что авторизаци€ по паролю это не про нас. Ќо на вс€кий случай впихну сюда краткую инструкцию по настройке аутентификации по ключу RSA:
1. Ќа клиентских машинах генерируем пользователю свой ключ RSA:
client1# ssh-keygen -t rsaѕо-умолчанию приватный ключ сохран€етс€ в ~/.ssh/id_rsa, а открытый Ч в ~/.ssh/id_rsa.pub. ѕриватный ключ храните как зеницу ока и никому не давайте, никуда не копируйте.
ѕри создании ключа можно задать пароль (passphrase), которым ключ будет зашифрован.
2. лиентские открытые ключи нужно сохранить на ssh-сервере в файле ~/.ssh/authorized_keys (~ это домашн€€ директори€ того пользовател€, которым будете логинитьс€), каждый на отдельной строке. ƒл€ того чтобы это не делать вручную, на каждом клиенте можно воспользоватьс€ командой:
ssh-copy-id user@sshserver√де user Ч им€ пользовател€ на сервере, sshserver Ч им€ или IP-адрес ssh-сервера.
3. ѕроверьте, что можете зайти на сервер по ключу, без ввода парол€ (не путать с passphrase):
ssh user@sshserver–екомендую не закрывать хот€ бы одну активную ssh-сессию с сервером до тех пор, пока окончательно не закончите настройку и не убедитесь что все работает.
4. ќтключите на SSH-сервере возможность входа по паролю в файле /etc/ssh/sshd_config:
PasswordAuthentication no¬озможность входа по открытому ключу обычно уже включена по-умолчанию:
PubkeyAuthentication yesя обычно также отключаю две следующие опции:
GSSAPIAuthentication no
UseDNS no¬ некоторых случа€х это позвол€ет ускорить процесс соединени€ (например, когда на сервере нет доступа в »нтернет).
5. ѕерезапустите sshd:
service sshd restart>
или
/etc/init.d/ssh restart
7) —пасибо (ссылки)
help.ubuntu.com/community/SSH_VPN
habrahabr.ru/post/87197
blog.backslasher.net/ssh-openvpn-tunneling.html| омментировать | « ѕред. запись — дневнику — —лед. запись » | —траницы: [1] [Ќовые] |






